Remember to Encrypt Your Connection
[This article was contributed by the SQL Azure team.]
SQL Azure doesn’t support unencrypted connections. If you try to request a connection via SQL Server Management Studio that is unencrypted, SQL Azure signals SQL Server Management Studio to establish an encrypted connection. Likewise, you need to specify in your connection strings that you want to encrypt the connection. If you copy and paste your connection string from the SQL Azure portal this is done for you.
- For ADO.NET you add: Encrypt=True
- For ODBC you add: Encrypt=yes
This handshake for encryption is done in the PRELOGIN stream of the Tabular Data Stream(TDS) Protocol which is required by any client communicating with SQL Server and SQL Azure including: SQL Server Management Studio and SQL Client and ADO.Net. You can read more about how the client and server handle encryption negotiation here.
Man-In-The-Middle Attack
However, there is a potential for a Man-In-The-Middle attack when requesting the connection. “A Man-In-The-Middle attack is the type of attack where attackers intrude into an existing connection to intercept the exchanged data and inject false information. It involves eavesdropping on a connection and intercepting messages.” -Toolbox for IT.
If an attacker simulates the PRELOGIN stream response from SQL Azure (using a Proxy) and that response doesn’t request an encrypted connection from your client you could be sending your data to the attacker.
Always Encrypt Your Connection
For this reason always important to make your client request encryption, instead of negotiating encryption with the server. It is easy to enable encryption to SQL Azure. You just need to remember to do it.
Here is how:
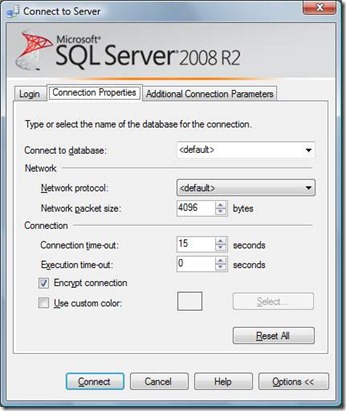
1) When you open a connection to the SQL Azure or start a new Query click on the Options button in the Connect to Server Dialog.
2) On the Connection Properties tab click the Encrypt connection checkbox.
You can lean about securely connecting to SQL Azure here.
Do you have questions, concerns, comments? Post them below and we will try to address them.