Internet Feature Controls (M..R)
This article describes feature controls with names that begin with the letter M, N, O, P, Q, or R. For links to other feature controls, see Feature Controls.
- MIME Type Determination
- MIME Type Handling
- MK Protocol Support
- Named Window Isolation
- Navigation Sound Support
- Protocol Lockdown
- Resource Protocol Restriction
- Restrict JScript at a System Level
- Restrict JScript at a Process Level
- Related topics
MIME Type Determination
Allow the process to determine a file's type by examining its bit signature. Windows Internet Explorer uses this information to determine how to render the file. The FEATURE_MIME_SNIFFING feature, when enabled, allows to be set differently for each security zone by using the URLACTION_FEATURE_MIME_SNIFFING URL action flag.
By default, this feature is enabled for Windows Internet Explorer and for applications hosting the WebBrowser Control. To disable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_MIME_SNIFFING
contoso.exe = (DWORD) 00000000
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
MIME Type Handling
Microsoft Internet Explorer 6 for Windows XP Service Pack 2 (SP2) and later. When the FEATURE_MIME_HANDLING feature control is enabled, Internet Explorer handles MIME types more securely:
The file extension given to a download file is based on the user's configuration, the values of the Content-Type and Content Disposition headers (if any), and the URL.
Internet Explorer will not automatically open downloaded files if the file extension is different from the file extensions supported by the registered application.
For more information, Handling MIME Types in Internet Explorer.
By default, this feature is enabled for Internet Explorer and disabled for applications hosting the WebBrowser Control. To enable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_MIME_HANDLING
contoso.exe = (DWORD) 00000001
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
MK Protocol Support
The FEATURE_DISABLE_MK_PROTOCOL feature blocks resources hosted on the "MK:" protocol, which is an obsolete mechanism for linking Windows Help files to webpages. When this feature control is disabled, the "MK:" protocol is enabled.
By default, this feature is enabled for Internet Explorer and for applications hosting the WebBrowser Control. To disable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_DISABLE_MK_PROTOCOL
contoso.exe = (DWORD) 00000000
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
Named Window Isolation
Windows Internet Explorer 8 and later. The FEATURE_ISOLATE_NAMED_WINDOWS feature prevents webpages hosted on one domain from manipulating named windows opened by webpages hosted on other domains. When this feature is disabled, named windows can be manipulated by other webpages, regardless of the domain they are hosted on.
By default, this feature is enabled for Internet Explorer and for applications hosting the WebBrowser Control. To disable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_ISOLATE_NAMED_WINDOWS
contoso.exe = (DWORD) 00000000
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
Note Because this feature reverses a change designed to improve the security of Internet Explorer, disabling this feature is strongly discouraged.
Navigation Sound Support
Internet Explorer 8 and later. When enabled, the FEATURE_DISABLE_NAVIGATION_SOUNDS feature disables the sounds played when you open a link in a webpage.
By default, this feature is disabled for Internet Explorer and for applications hosting the WebBrowser Control. To enable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_DISABLE_NAVIGATION_SOUNDS
contoso.exe = (DWORD) 00000001
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
Protocol Lockdown
The FEATURE_PROTOCOL_LOCKDOWN feature applies the restrictions of the FEATURE_LOCALMACHINE_LOCKDOWN feature to specific protocols used in other zone contexts. For example, you can restrict HTML content from being loaded by the "shell:" protocol in the Internet zone. Because the shell protocol is designed primarily for the Local Machine zone, you can reduce the risk of malicious attacks from other zones. For more information, please see Security Considerations: URL Security Zones API.
By default, this feature is disabled for Internet Explorer and for applications hosting the WebBrowser Control. To enable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_PROTOCOL_LOCKDOWN
contoso.exe = (DWORD) 00000001
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
Resource Protocol Restriction
Internet Explorer 6 for Windows XP SP2 and later. When enabled, the FEATURE_RESTRICT_RES_TO_LMZ feature restricts the res: protocol to the Local Machine Zone.
By default, this feature is enabled for Internet Explorer and disabled for applications hosting the WebBrowser Control. To enable this feature by using the registry, add the name of your executable file to the following setting.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
FEATURE_RESTRICT_ACTIVEXINSTALL
contoso.exe = (DWORD) 00000001
The feature is enabled when the value is set to (DWORD) 00000001 and disabled when the value is (DWORD) 00000000.
Restrict JScript at a System Level
When the FEATURE_ACTIVATE_URLACTION_ALLOW_JSCRIPT_IE feature is enabled, an admin will be able to configure Internet Explorer to restrict JScript execution per security zone in IE.
There are two parts to restrict JScript from being loaded at a system level. First, the feature has to be enabled and then secondly configured per security zone. This feature is enabled by default for RS4 and later platforms, please skip the “enabling the feature” and go to Option to disable JScript execution in Internet Explorer (microsoft.com) for further instructions.“ This feature is disabled by default for RS3 and earlier platforms – the following are instructions on how to enable this feature.
Enabling this feature
Follow the below steps to enable this feature for RS3 and earlier:
Step 1: Navigate to the below registry path
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
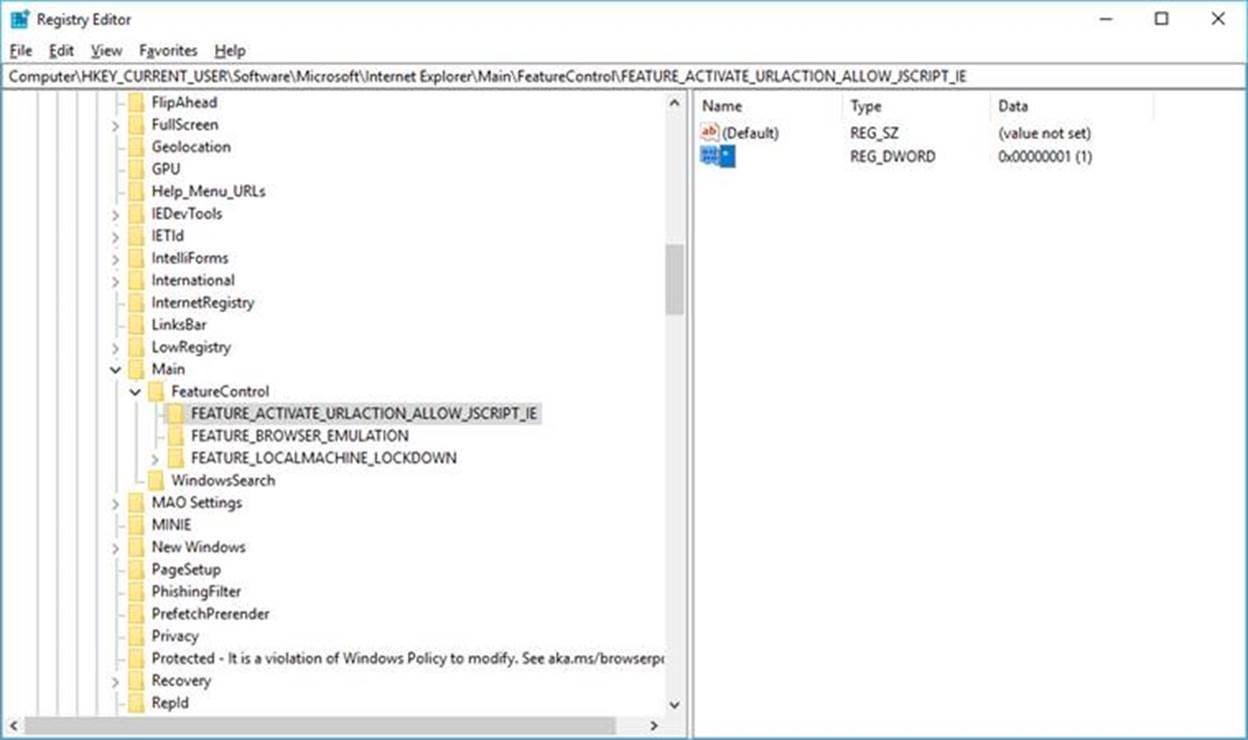
Step 2: Create a new key with the following name: FEATURE_ACTIVATE_URLACTION_ALLOW_JSCRIPT_IE
Step 3: Create a new DWORD (32-bit) Value with * as the name and set the data value to 1
The feature is now enabled. This is only needed for RS3 and older platforms. Setting this key on RS4 and newer platforms will not do anything.
See Option to disable JScript execution in Internet Explorer (microsoft.com) for instructions on how to configure this feature.
When enabling this feature, please be aware of the order of precedence as documented in the Introduction to Feature Control Key page and configure accordingly. The order of precedence is as below.
- HKEY_LOCAL_MACHINE policy hive (administrative overrides)
- HKEY_CURRENT_USER policy hive
- HKEY_CURRENT_USER preference hive
- HKEY_LOCAL_MACHINE preference hive (system default settings)
Restrict JScript at a Process Level
When the FEATURE_ACTIVATE_PROCESS_POLICY_FOR_JSCRIPT feature is enabled, an admin will be able to configure Internet Explorer to restrict JScript execution per application and per security zone.
There are two parts to restrict JScript from being loaded by a specific process. First, the feature has to be enabled and then secondly configured to block the desired process. This feature is enabled by default for RS4 and later platforms, please skip the “enabling the feature” and look at “configuring this feature” for further instructions. This feature is disabled by default for RS3 and earlier platforms – the following are instructions on how to enable this feature.
Enabling this feature
The following steps describes how to enable this feature by using the registry editor.
Step 1: Navigate to the following registry path using the registry editor.
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
Step 2: Create a new key with the following name: FEATURE_ACTIVATE_PROCESS_POLICY_FOR_JSCRIPT
Step 3: Create a new DWORD (32-bit) Value with * as the name and set the data value to 1.
This enables the feature and allows it to be configured to block the desired process. This is only needed for RS3 and older platforms. Setting this key on RS4 and newer platforms will not do anything.
Configuring this feature
The following steps describes how to configure this feature.
Step 1:
Navigate to the below registry path
HKEY_LOCAL_MACHINE (or HKEY_CURRENT_USER)
SOFTWARE
Microsoft
Internet Explorer
Main
FeatureControl
Step 2:
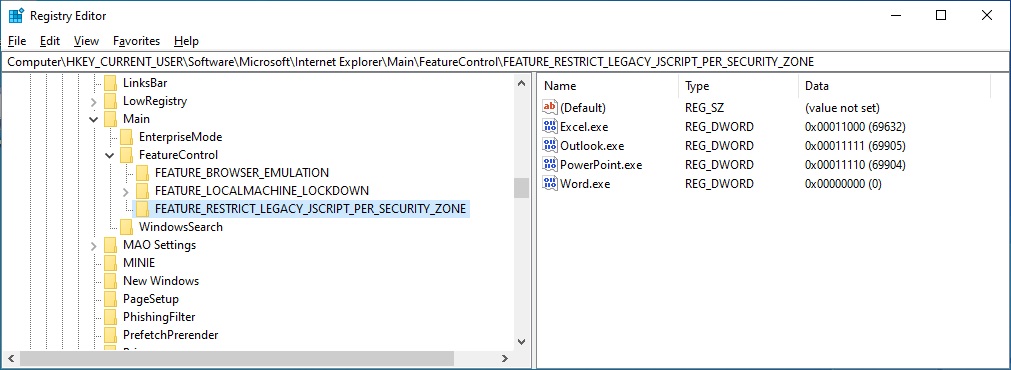
Create the following key FEATURE_RESTRICT_LEGACY_JSCRIPT_PER_SECURITY_ZONE
Step 3:
Define the value per process according to the desired configuration.
- Restrictions:
- 0x00000001 My Computer disallowed
- 0x00000010 Local Intranet disallowed
- 0x00000100 Trusted Sites disallowed
- 0x00001000 Internet disallowed
- 0x00010000 Restricted Sites disallowed
- Examples:
- 0x00011000 Internet and Restricted Sites combined lockdown
- 0x00011010 Local Intranet, Internet, and Restricted Sites combined lockdown
To block a specific process, specify the process name as a new DWORD (32 Bit) name and change the data based on the above to block JScript from being loaded in each security zone. For example, in the below screenshot,
- Word.exe does not restrict access to jscript.dll at the process level. Therefore, its corresponding process-level registry key set to the bit-wise mask of 0x00000000 in hexadecimal).
- Excel.exe allows loading jscript.dll for My Computer, Local Intranet and Trusted security zones, while it disallows loading it for both Internet (3) and Restricted Sites (4) security zones. Therefore, its registry key is set to the combined bit-wise mask of 0x00011000 in hexadecimal.
- PowerPoint.exe allows loading jscript.dll for My Computer only, and disallows loading it Local Intranet (1), Trusted Sites (2), Internet (3) and Restricted Sites (4) security zones. Therefore, its registry key is set to the combined bit-wise mask of 0x00011110 in hexadecimal.
- Outlook.exe disallows loading jscript.dll at all security zones. Therefore, its registry key is set to the combined bit-wise mask of 0x00011111 in hexadecimal.
When enabling this feature, please be aware of the order of precedence as documented in the Introduction to Feature Control Key page and configure accordingly. The order of precedence is as below.
- HKEY_LOCAL_MACHINE policy hive (administrative overrides)
- HKEY_CURRENT_USER policy hive
- HKEY_CURRENT_USER preference hive
- HKEY_LOCAL_MACHINE preference hive (system default settings)
Note that by default, JScript functions without any restrictions.
Related topics
Conceptual
Internet Feature Controls (B..C)
Internet Feature Controls (D..H)
Internet Feature Controls (I..L)
Internet Feature Controls (S..T)