Proteggere il recapito webhook con l’utente di Microsoft Entra in Griglia di eventi di Azure
Questo script fornisce la configurazione per recapitare gli eventi agli endpoint HTTPS protetti dall'utente di Microsoft Entra usando Griglia di eventi di Azure.
Ecco i passaggi generali dello script:
- Creare un'entità servizio per Microsoft.EventGrid , se non esiste già.
- Creare un ruolo denominato AzureEventGridSecureWebhookSubscriber nell'app Microsoft Entra per il webhook.
- Aggiungere l'entità servizio dell'utente che crea la sottoscrizione al ruolo AzureEventGridSecureWebhookSubscriber.
- Aggiungere l'entità servizio di Microsoft.EventGrid ad AzureEventGridSecureWebhookSubscriber.
Ottenere l'ID applicazione Microsoft.EventGrid
Passare al portale di Azure.
Nella barra di ricerca digitare
Microsoft.EventGride quindi selezionare Microsoft.EventGrid (entità servizio) nell'elenco a discesa.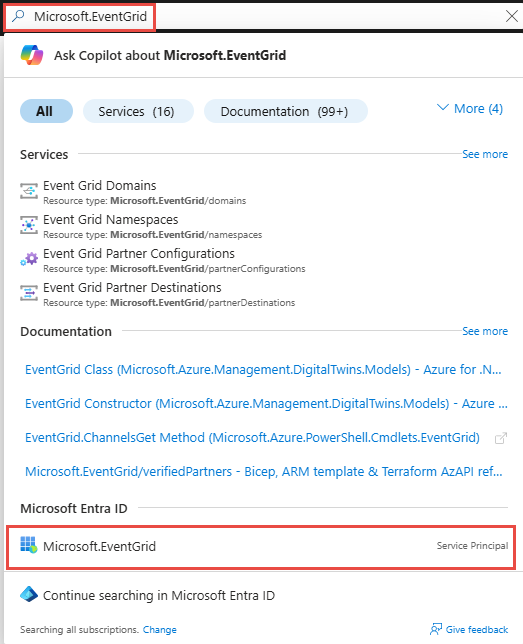
Nella pagina Microsoft.EventGrid annotare o copiare l'ID applicazione negli Appunti.
Nello script seguente impostare la
$eventGridAppIdvariabile su questo valore prima di eseguirla.
Script di esempio
# NOTE: Before run this script ensure you are logged in Azure by using "az login" command.
$eventGridAppId = "[REPLACE_WITH_EVENT_GRID_APP_ID]"
$webhookAppObjectId = "[REPLACE_WITH_YOUR_ID]"
$eventSubscriptionWriterUserPrincipalName = "[REPLACE_WITH_USER_PRINCIPAL_NAME_OF_THE_USER_WHO_WILL_CREATE_THE_SUBSCRIPTION]"
# Start execution
try {
# Creates an application role of given name and description
Function CreateAppRole([string] $Name, [string] $Description)
{
$appRole = New-Object Microsoft.Graph.PowerShell.Models.MicrosoftGraphAppRole
$appRole.AllowedMemberTypes = New-Object System.Collections.Generic.List[string]
$appRole.AllowedMemberTypes += "Application";
$appRole.AllowedMemberTypes += "User";
$appRole.DisplayName = $Name
$appRole.Id = New-Guid
$appRole.IsEnabled = $true
$appRole.Description = $Description
$appRole.Value = $Name;
return $appRole
}
# Creates Azure Event Grid Microsoft Entra Application if not exists
# You don't need to modify this id
# But Azure Event Grid Microsoft Entra Application Id is different for different clouds
$eventGridSP = Get-MgServicePrincipal -Filter ("appId eq '" + $eventGridAppId + "'")
if ($eventGridSP.DisplayName -match "Microsoft.EventGrid")
{
Write-Host "The Event Grid Microsoft Entra Application is already defined.`n"
} else {
Write-Host "Creating the Azure Event Grid Microsoft Entra Application"
$eventGridSP = New-MgServicePrincipal -AppId $eventGridAppId
}
# Creates the Azure app role for the webhook Microsoft Entra application
$eventGridRoleName = "AzureEventGridSecureWebhookSubscriber" # You don't need to modify this role name
$app = Get-MgApplication -ApplicationId $webhookAppObjectId
$appRoles = $app.AppRoles
Write-Host "Microsoft Entra App roles before addition of the new role..."
Write-Host $appRoles.DisplayName
if ($appRoles.DisplayName -match $eventGridRoleName)
{
Write-Host "The Azure Event Grid role is already defined.`n"
} else {
Write-Host "Creating the Azure Event Grid role in Microsoft Entra Application: " $webhookAppObjectId
$newRole = CreateAppRole -Name $eventGridRoleName -Description "Azure Event Grid Role"
$appRoles += $newRole
Update-MgApplication -ApplicationId $webhookAppObjectId -AppRoles $appRoles
}
Write-Host "Microsoft Entra App roles after addition of the new role..."
Write-Host $appRoles.DisplayName
# Creates the user role assignment for the user who will create event subscription
$servicePrincipal = Get-MgServicePrincipal -Filter ("appId eq '" + $app.AppId + "'")
try
{
Write-Host "Creating the Microsoft Entra App Role assignment for user: " $eventSubscriptionWriterUserPrincipalName
$eventSubscriptionWriterUser = Get-MgUser -UserId $eventSubscriptionWriterUserPrincipalName
$eventGridAppRole = $app.AppRoles | Where-Object -Property "DisplayName" -eq -Value $eventGridRoleName
New-MgUserAppRoleAssignment -UserId $eventSubscriptionWriterUser.Id -PrincipalId $eventSubscriptionWriterUser.Id -ResourceId $servicePrincipal.Id -AppRoleId $eventGridAppRole.Id
}
catch
{
if( $_.Exception.Message -like '*Permission being assigned already exists on the object*')
{
Write-Host "The Microsoft Entra User Application role is already defined.`n"
}
else
{
Write-Error $_.Exception.Message
}
Break
}
# Creates the service app role assignment for Event Grid Microsoft Entra Application
$eventGridAppRole = $app.AppRoles | Where-Object -Property "DisplayName" -eq -Value $eventGridRoleName
New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $eventGridSP.Id -PrincipalId $eventGridSP.Id -ResourceId $servicePrincipal.Id -AppRoleId $eventGridAppRole.Id
# Print output references for backup
Write-Host ">> Webhook's Microsoft Entra Application Id: $($app.AppId)"
Write-Host ">> Webhook's Microsoft Entra Application Object Id: $($app.Id)"
}
catch {
Write-Host ">> Exception:"
Write-Host $_
Write-Host ">> StackTrace:"
Write-Host $_.ScriptStackTrace
}
Spiegazione dello script
Per altre informazioni, vedere Secure WebHook delivery with Microsoft Entra ID in Griglia di eventi di Azure( Secure WebHook delivery with Microsoft Entra ID in Griglia di eventi di Azure).