Monitorare Protezione DDoS di Azure
Monitoraggio di Azure raccoglie e aggrega metriche e log dal sistema per monitorare la disponibilità, le prestazioni e la resilienza e notificare eventuali problemi che interessano il sistema. È possibile usare il portale di Azure, PowerShell, l'interfaccia della riga di comando di Azure, l'API REST o le librerie client per configurare e visualizzare i dati di monitoraggio.
Sono disponibili metriche e log diversi per diversi tipi di risorse. Questo articolo descrive i tipi di dati di monitoraggio che è possibile raccogliere per questo servizio e i modi per analizzare tali dati.
Raccogliere dati con Monitoraggio di Azure
Questa tabella descrive come raccogliere i dati per monitorare il servizio e le operazioni che è possibile eseguire con i dati dopo la raccolta:
| Dati da raccogliere | Descrizione | Come raccogliere e instradare i dati | Dove visualizzare i dati | Dati supportati |
|---|---|---|---|---|
| Dati delle metriche | Le metriche sono valori numerici che descrivono determinati aspetti di un sistema in un particolare momento. Le metriche possono essere aggregate usando algoritmi, rispetto ad altre metriche e analizzate per individuare le tendenze nel tempo. | - Raccolto automaticamente a intervalli regolari. - È possibile instradare alcune metriche della piattaforma a un'area di lavoro Log Analytics per eseguire query con altri dati. Controllare l'impostazione di esportazione DS per ogni metrica per verificare se è possibile usare un'impostazione di diagnostica per instradare i dati delle metriche. |
Esplora metriche | Metriche di Protezione DDoS di Azure supportate da Monitoraggio di Azure |
| Dati del log delle risorse | I log vengono registrati eventi di sistema con un timestamp. I log possono contenere tipi diversi di dati e possono essere strutturati o in formato libero. È possibile instradare i dati del log delle risorse alle aree di lavoro Log Analytics per l'esecuzione di query e l'analisi. | Creare un'impostazione di diagnostica per raccogliere e instradare i dati del log delle risorse. | Log Analytics | Dati di log delle risorse di Protezione DDoS di Azure supportati da Monitoraggio di Azure |
| Dati del log attività | Il log attività di Monitoraggio di Azure fornisce informazioni dettagliate sugli eventi a livello di sottoscrizione. Il log attività include informazioni relative, ad esempio, alla modifica di una risorsa o all'avvio di una macchina virtuale. | - Raccolto automaticamente. - Creare un'impostazione di diagnostica per un'area di lavoro Log Analytics senza costi aggiuntivi. |
Log attività |
Per l'elenco di tutti i dati supportati da Monitoraggio di Azure, vedere:
Monitoraggio predefinito per la protezione DDoS di Azure
Protezione DDoS di Azure offre informazioni dettagliate e visualizzazioni dei modelli di attacco tramite Analisi degli attacchi DDoS. Offre ai clienti visibilità completa sul traffico di attacco e sulle azioni di mitigazione tramite report e log dei flussi. Durante un attacco DDoS, le metriche dettagliate sono disponibili tramite Monitoraggio di Azure, che consente anche le configurazioni degli avvisi in base a queste metriche.
È possibile visualizzare e configurare i dati di telemetria di protezione DDoS di Azure.
I dati di telemetria per un attacco vengono forniti da Monitoraggio di Azure in tempo reale. Mentre i trigger di mitigazione per TCP SYN, TCP & UDP sono disponibili durante il tempo di pace, altri dati di telemetria sono disponibili solo quando un indirizzo IP pubblico è stato sottoposto a mitigazione.
È possibile visualizzare i dati di telemetria DDoS per un indirizzo IP pubblico protetto tramite tre diversi tipi di risorse: piano di protezione DDoS, rete virtuale e indirizzo IP pubblico.
La registrazione può essere ulteriormente integrata con Microsoft Sentinel, Splunk (Hub eventi di Azure), OMS Log Analytics e Archiviazione di Azure per l'analisi avanzata tramite l'interfaccia diagnostica di Monitoraggio di Azure.
Per altre informazioni sulle metriche, vedere Monitoraggio di Protezione DDoS di Azure per informazioni dettagliate sui log di monitoraggio di Protezione DDoS.
Visualizzare le metriche dal piano di protezione DDoS
Accedere al portale di Azure e selezionare il piano di protezione DDoS.
Nel menu del portale di Azure selezionare o cercare e selezionare Piani di protezione DDoS quindi selezionare il piano di protezione DDoS.
In Monitoraggio selezionare Metrica.
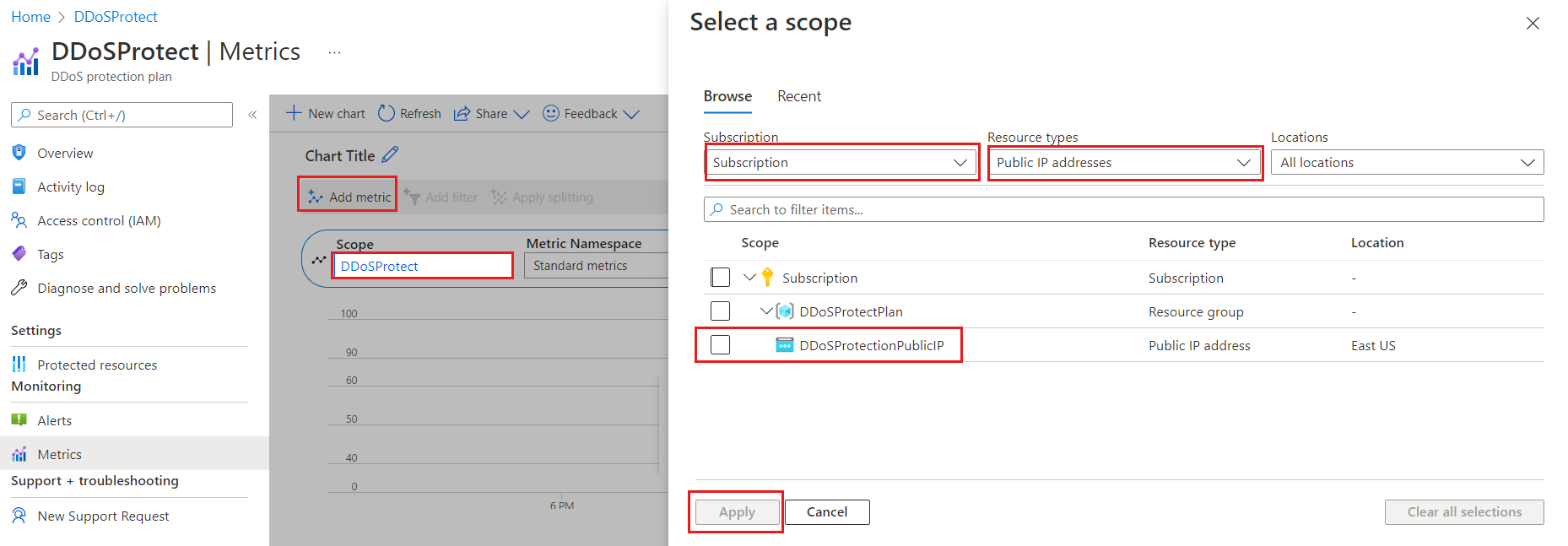
Selezionare Aggiungi metrica e quindi Ambito.
Nel menu Selezionare un ambito, selezionare la sottoscrizione contenente l'indirizzo IP pubblico che si vuole registrare.
Selezionare Indirizzo IP pubblico per Tipo di risorsa, quindi selezionare l'indirizzo IP pubblico specifico per il quale si vogliono registrare le metriche e scegliere Applica.
Per Metrica selezionare In caso di attacco DDoS o meno.
Impostare il tipo di aggregazione su Max.
Visualizzare le metriche dalla rete virtuale
Accedere al portale di Azure e passare alla rete virtuale con protezione DDoS abilitata.
In Monitoraggio selezionare Metrica.
Selezionare Aggiungi metrica e quindi Ambito.
Nel menu Selezionare un ambito, selezionare la sottoscrizione contenente l'indirizzo IP pubblico che si vuole registrare.
Selezionare Indirizzo IP pubblico per Tipo di risorsa, quindi selezionare l'indirizzo IP pubblico specifico per il quale si vogliono registrare le metriche e scegliere Applica.
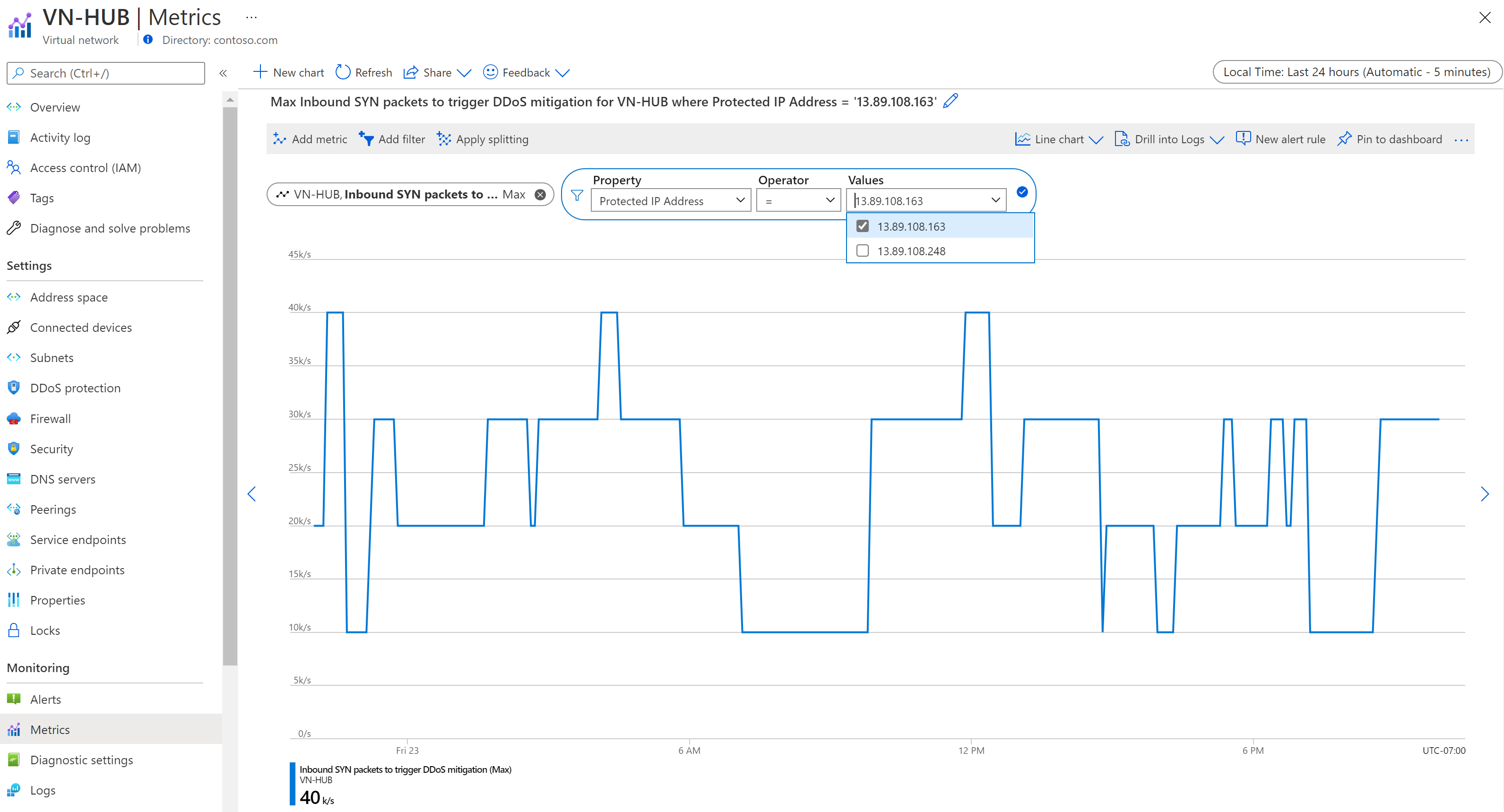
In Metrica selezionare la metrica scelta e quindi in Aggregazione selezionare tipo come Max.
Nota
Per filtrare gli indirizzi IP, selezionare Aggiungi filtro. In Proprietà, selezionare Indirizzo IP protetto e l'operatore deve essere impostato su =. In Valori viene visualizzato un elenco a discesa di indirizzi IP pubblici, associati alla rete virtuale, protetti da Protezione DDoS di Azure.
Visualizzare le metriche dall'indirizzo IP pubblico
- Accedere al portale di Azure e passare all'indirizzo IP pubblico.
- Nel menu del portale di Azure selezionare o cercare e selezionare indirizzi IP pubblici quindi selezionare l'indirizzo IP pubblico.
- In Monitoraggio selezionare Metrica.
- Selezionare Aggiungi metrica e quindi Ambito.
- Nel menu Selezionare un ambito, selezionare la sottoscrizione contenente l'indirizzo IP pubblico che si vuole registrare.
- Selezionare Indirizzo IP pubblico per Tipo di risorsa, quindi selezionare l'indirizzo IP pubblico specifico per il quale si vogliono registrare le metriche e scegliere Applica.
- In Metrica selezionare la metrica scelta e quindi in Aggregazione selezionare tipo come Max.
Nota
Quando si modifica la protezione IP DDoS da abilitata a disabilitata, i dati di telemetria per la risorsa IP pubblica non sono disponibili.
Visualizzare i criteri di mitigazione della protezione DDoS
Protezione DDoS di Azure usa tre criteri di mitigazione modificati automaticamente (TCP SYN, TCP e UDP) per ogni indirizzo IP pubblico della risorsa protetta. Questo approccio si applica a qualsiasi rete virtuale con protezione DDoS abilitata.
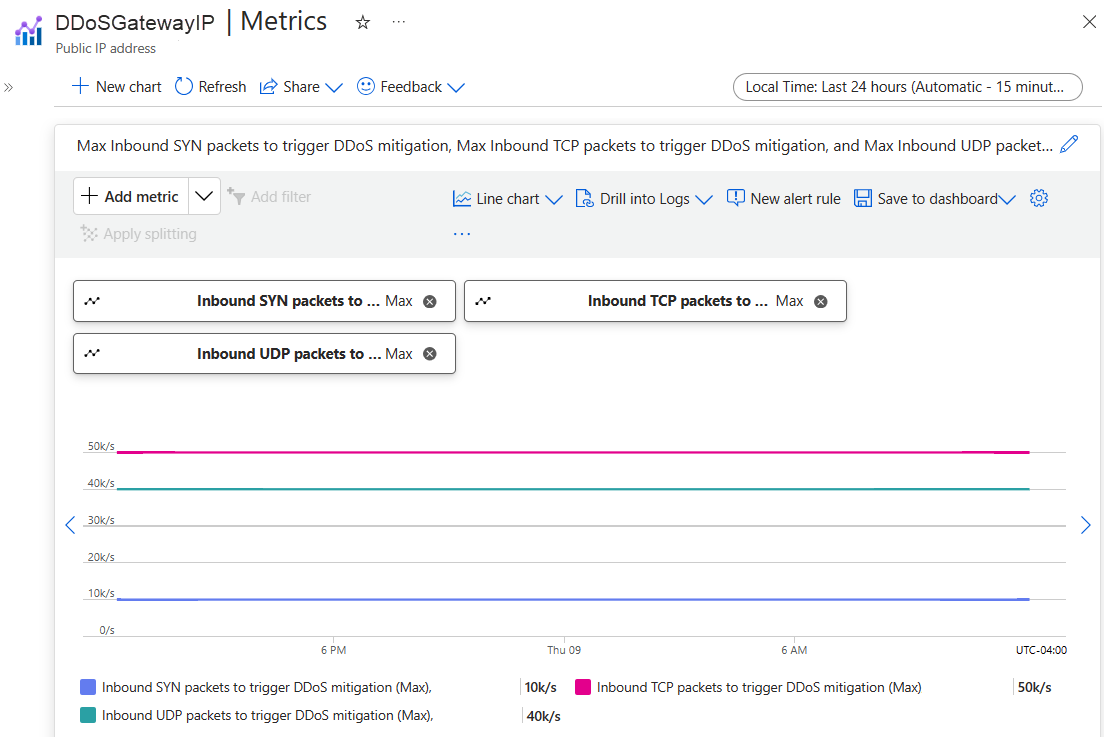
È possibile visualizzare i limiti dei criteri nelle metriche degli indirizzi IP pubblici scegliendo i pacchetti SYN in ingresso per attivare la mitigazione DDoS, i pacchetti TCP in ingresso per attivare la mitigazione DDoS e i pacchetti UDP in ingresso per attivare le metriche di mitigazione DDoS. Assicurarsi di impostare il tipo di aggregazione su Max.
Visualizzare i dati di telemetria del traffico in tempo di pace
È importante tenere d'occhio le metriche per i trigger di rilevamento TCP SYN, UDP e TCP. Queste metriche consentono di sapere all'avvio della protezione DDoS. Assicurarsi che questi trigger riflettano i normali livelli di traffico quando non è presente alcun attacco.
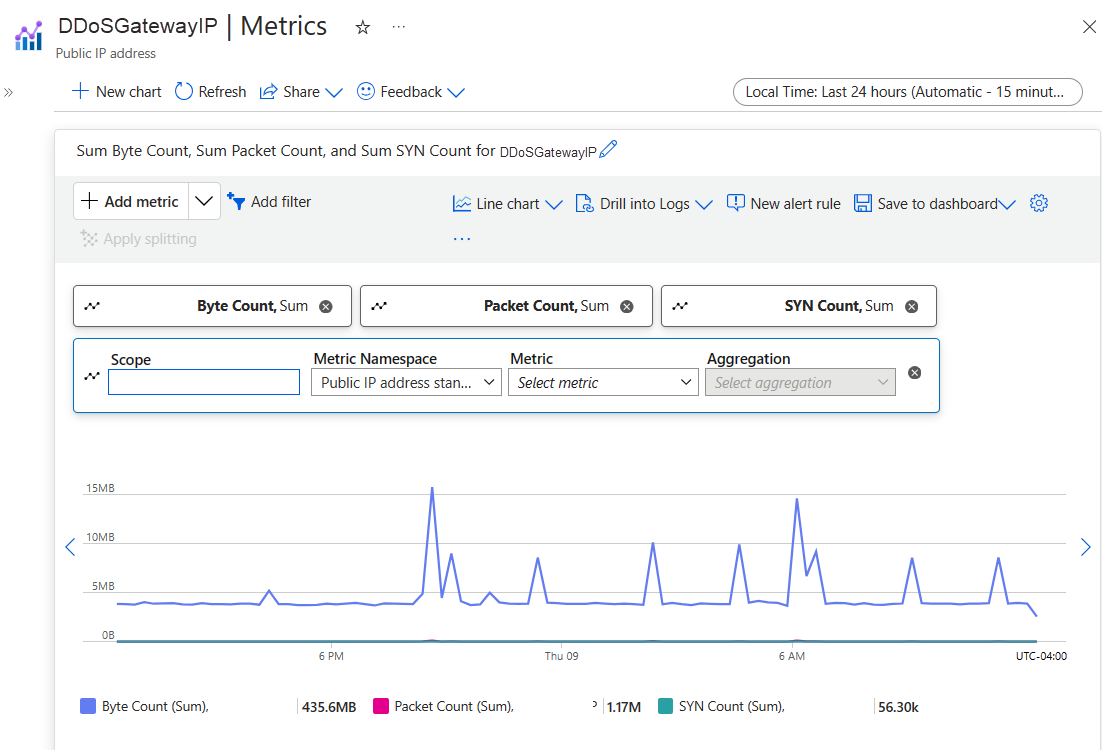
È possibile creare un grafico per la risorsa indirizzo IP pubblico. In questo grafico includere le metriche Conteggio pacchetti e Conteggio SYN. Il conteggio pacchetti include pacchetti TCP e UDP. Viene visualizzata la somma del traffico.
Nota
Per eseguire un confronto equo, è necessario convertire i dati in pacchetti al secondo. È possibile eseguire questa conversione dividendo il numero visualizzato per 60, perché i dati rappresentano il numero di pacchetti, byte o pacchetti SYN raccolti in più di 60 secondi. Ad esempio, se sono presenti 91.000 pacchetti raccolti oltre 60 secondi, dividere 91.000 per 60 per ottenere circa 1.500 pacchetti al secondo (pps).
Convalidare e testare
Per simulare un attacco DDoS per convalidare i dati di telemetria della protezione DDoS, vedere Convalidare il rilevamento DDoS.
Usare gli strumenti di Monitoraggio di Azure per analizzare i dati
Questi strumenti di Monitoraggio di Azure sono disponibili nella portale di Azure per analizzare i dati di monitoraggio:
Alcuni servizi di Azure hanno un dashboard di monitoraggio predefinito nella portale di Azure. Questi dashboard sono denominati informazioni dettagliate ed è possibile trovarli nella sezione Insights di Monitoraggio di Azure nella portale di Azure.
Esplora metriche consente di visualizzare e analizzare le metriche per le risorse di Azure. Per altre informazioni, vedere Analizzare le metriche con Esplora metriche di Monitoraggio di Azure.
Log Analytics consente di eseguire query e analizzare i dati di log usando il linguaggio di query Kusto (KQL). Per altre informazioni, vedere Introduzione alle query dei log del Monitoraggio di Azure.
Il portale di Azure dispone di un'interfaccia utente per la visualizzazione e le ricerche di base del log attività. Per eseguire analisi più approfondite, indirizzare i dati ai log di Monitoraggio di Azure ed eseguire query più complesse in Log Analytics.
Application Insights monitora la disponibilità, le prestazioni e l'utilizzo delle applicazioni Web, in modo da poter identificare e diagnosticare gli errori senza attendere che un utente li segnala.
Application Insights include punti di connessione a vari strumenti di sviluppo e si integra con Visual Studio per supportare i processi DevOps. Per altre informazioni, vedere Monitoraggio delle applicazioni per il Servizio app.
Gli strumenti che consentono una visualizzazione più complessa includono:
- I dashboard che consentono di combinare tipi di dati diversi in un singolo riquadro nel portale di Azure.
- Cartelle di lavoro, report personalizzabili che è possibile creare nel portale di Azure. Le cartelle di lavoro possono includere testo, metriche e query di log.
- Grafana è una piattaforma aperta, ideale per i dashboard operativi. È possibile usare Grafana per creare dashboard che includano dati da più origini diverse dal Monitoraggio di Azure.
- Power BI, un servizio di analisi aziendale che fornisce visualizzazioni interattive per un'ampia varietà di origini dati. È possibile configurare per Power BI per importare automaticamente i dati di log da Monitoraggio di Azure per sfruttare i vantaggi di queste visualizzazioni.
Esportare i dati di Monitoraggio di Azure
È possibile esportare i dati da Monitoraggio di Azure in altri strumenti usando:
Metriche: usare l'API REST per le metriche per estrarre i dati delle metriche dal database delle metriche del Monitoraggio di Azure. Per altre informazioni, vedere Informazioni di riferimento sull'API REST del Monitoraggio di Azure.
Log: usare l'API REST o le librerie client associate.
Esportazione dei dati dell'area di lavoro Log Analytics.
Per iniziare a usare l'API REST di Monitoraggio di Azure, vedere Procedura dettagliata per l'API REST di monitoraggio di Azure.
Usare query Kusto per analizzare i dati di log
È possibile analizzare i dati dei log di Monitoraggio di Azure usando il linguaggio di query Kusto (KQL). Per altre informazioni, vedere Log di query in Monitoraggio di Azure.
Usare gli avvisi di Monitoraggio di Azure per notificare i problemi
Gli avvisi di Monitoraggio di Azure consentono di identificare e risolvere i problemi nel sistema e inviare notifiche proattive quando vengono rilevate condizioni specifiche nei dati di monitoraggio prima che i clienti li notino. È possibile creare avvisi su qualsiasi metrica o fonte di dati di log nella piattaforma di dati di Monitoraggio di Azure. Esistono diversi tipi di avvisi di Monitoraggio di Azure a seconda dei servizi monitorati e dei dati di monitoraggio raccolti. Vedere Scelta del tipo di regola di avviso corretto.
Regole di avviso consigliate di Monitoraggio di Azure per protezione DDoS di Azure
Per altre informazioni sugli avvisi in Protezione DDoS di Azure, vedere Configurare gli avvisi delle metriche di Protezione DDoS di Azure tramite il portale e Configurare gli avvisi di registrazione diagnostica di Protezione DDoS di Azure.
Per esempi di avvisi comuni per le risorse di Azure, vedere Query di avviso di log di esempio.
Implementazione di avvisi su larga scala
Per alcuni servizi, è possibile effettuare un monitoraggio su larga scala applicando la stessa regola di avviso delle metriche a più risorse dello stesso tipo presenti nella stessa area di Azure. Gli avvisi di base di Monitoraggio di Azure (AMBA) offrono un metodo semi-automatizzato per implementare importanti avvisi, dashboard e linee guida per le metriche della piattaforma su larga scala.