Exporting Computers that are not Compliant with Security Baseline Recommendations in Azure Security Center
To enhance your security posture you must ensure that your computers are using the appropriate secure configuration, which may vary according to its role, for example: Web Servers will have a different security baseline compare to File Servers. In Security Center you can see the current security state of your computers by using the Security configurations mismatch (formerly known as Remediate OS vulnerabilities) in Compute’s recommendation, as shown below: 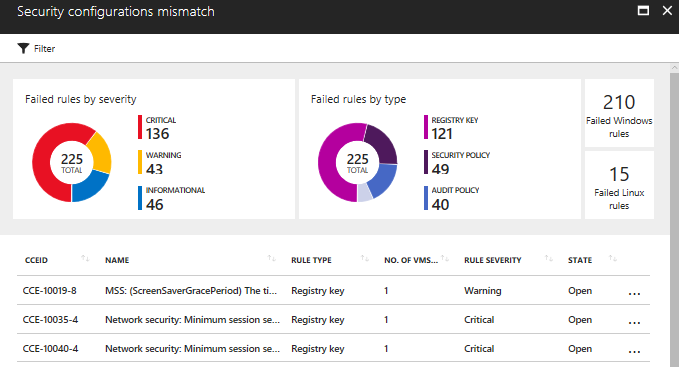
As you can see, these recommendations are based on CCE (Common Configuration Enumeration), and all rules that are tested are documented here. When you select one of those CCE rule, Security Center will open a blade to show the details about this particular rule, as shown below: 
If you click the Search button on top of this blade, Security Center opens Log Analytics and automatically search for all computers that are not compliant with this security baseline rule. While this is very cool, the question that I received recently was: how can I export all this list to know which computers are not compliant with these listed rules? The answer is: you can use the following Log Analytics query to export all computers that are not compliant with these rules:
SecurityBaseline | where (BaselineType =~ "WindowsOS" or BaselineType =~ "Linux" or (isempty(BaselineType) and isnotempty(TimeGenerated))) and AnalyzeResult == "Failed" and CceId contains "CCE"
The result of this query will be a table with all computers, and within each line, you can expand and find many more info, including:
SourceSystem: OpsManager
TimeGenerated [UTC]: 2017-12-06T07:19:06.863Z
SubscriptionId: XXXX
ResourceGroup: ascdemorg
ResourceProvider: microsoft.compute
Resource: vm3
ResourceId: XXXX
ResourceType: virtualmachines
ComputerEnvironment: Azure
Computer: vm3
BaselineId: 6ba1ce80-e4e5-4b8a-bc88-257612e72185
BaselineType: WindowsOS
OSName: Windows Server 2012 R2 Datacenter
AssessmentId: XXXX
TimeAnalyzed [UTC]: 2017-12-06T07:18:58.672Z
CceId: CCE-37853-9
RuleSeverity: Informational
BaselineRuleType: Audit Policy
Description: Audit Policy: System: IPsec Driver
RuleSetting: 0cce9213-69ae-11d9-bed3-505054503030
ExpectedResult: Success and Failure
ActualResult: No Auditing
AnalyzeResult: Failed
BaselineRuleId: 107b8424-7ee8-4b6a-a859-b5256aa6596e
Type: SecurityBaseline
While there are lots of information in here, the fields Description, Vulnerability, Potential Impact, and Countermeasure are not available via this search. One way to correlate the CCID with these fields is by using the Security Compliance Manager (SCM), which although was retired this year still have the templates for Windows Server 2012. Here how you can find these fields from the CCID and export to an Excel file:
1. Select the template that you want from the list:
2. Export to Excel
3. Open the Excel file and click Customize Fields button.
4. Select CCE-ID 5.0 and click the >> button
5. Filter for the CCE that you want:
Stay safe!
@yuridiogenes

