What’s different about Kerberos Authentication on IIS 7.0
On IIS 6.0 if your web application ran under a custom user account you would have to setup Service Principal Names (SPNs) for that account. This detail is something that most users miss and as a result the authentication falls back to NTLM. The need for the custom SPNs arises because the authentication happens in the user mode.
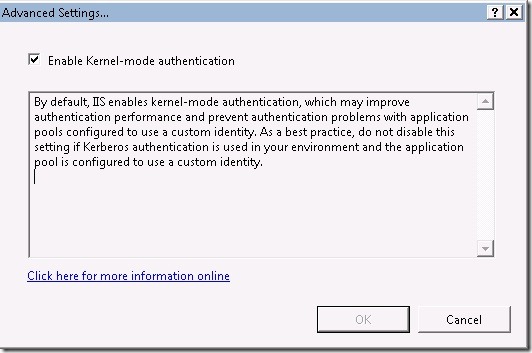
In IIS 7.0 by default the authentication is moved into the kernel. This eliminates the need for setting up SPNs when you change the application pool user account as the authentication is happening in the context of the machine and every machine already has a default HOST/machine SPN in the Active Directory(AD).
IIS Manager > Global Level(MachineName) > Authentication > Windows Authentication > Advanced Settings…
For folks who are accustomed with IIS 6.0 this change may seem disturbing. Especially if your are migrating from an IIS 6.0 environment to IIS 7.0 this could lead to duplicate SPNs. Since you would have configured SPNs to the custom account in IIS 6.0 while moving to IIS 7.0 you need to ensure that you remove those. You can use this command to figure out which accounts have a particular SPN.
ldifde -f spn.txt -d"dc=contoso, dc=com" -l serviceprincipalname -r "(serviceprincipalname=http/www.contoso.com)" -p subtree
assuming your domain is contoso.com and your url for the web application is https://www.contoso.com/
Its a nifty command to figure out duplicate SPNs. The spn.txt file that is created will have a list of user accounts that have a particular SPN. Always ensure there is only one.
You can turn off this feature and make IIS 7.0 behave similar to IIS 6.0. However I strongly do not recommend it as the Kernel-mode authentication also increases performance.
If you have a history of setting up Kerberos authentication on websites by now you should be wondering how Kernel-mode can work in a load balanced(webfarm) scenario. In load balanced scenarios also you do not have to disable Kernel-mode authentication. Instead you can set the useAppPoolCredentials property to true . You do this in your configuration file under the system.webServer / security / authentication / windowsauthentication section.
<windowsAuthentication enabled="true" useKernelMode="true" useAppPoolCredentials="true" />
With Win7 you will see a new option in the above screen called Extended Protection which can be set to Off / Accept / Required. This basically will support Channel Binding Token and helps in preventing Kerberos authentication forwarding attacks by a man in the middle.
Comments
Anonymous
January 06, 2009
PingBack from http://www.codedstyle.com/what%e2%80%99s-different-about-kerberos-authentication-on-iis-70/Anonymous
November 05, 2009
The comment has been removed