Creating and Managing Security and Compliance Filters in the Real World [Part 1]
Diving deeper into the Security & Compliance Center, I decided to embark on trying to scope eDiscovery permissions to meet a certain set of requirements that we see when multiple business units want or need to maintain independence from a content search and discovery perspective.
Here is the scenario and requirements that we're going to try to accomplish:
- Single Office 365 Tenant
- Multiple agencies or business units synchronized into the environment
- A representative from the security department for "Users whose names start with D" needs to be able to perform eDiscovery searches on the mailboxes of persons whose first names start with the letter D. The representative's user name will be SearchUserStartsWithD, because I'm just that creative.
- A representative from the security department for the Marketing group needs to be able to perform eDiscovery searches on the mailboxes of persons whose Department attribute is populated with Marketing. The representative's user name will be SearchUserMarketing, just to keep it simple.
- A representative from the compliance department for the Customer Service group needs to be able to perform eDiscovery searches on the mailboxes of persons whose Department attribute is populated with CustomerService. Additionally, they should only be able to search for Instant messages or Contacts inside those mailboxes.
- Some of the users may appear in more than one search scope (for example, we may have someone who belongs to the Marketing department whose first name starts with D. As you may have guessed from my complex naming scheme, I'm going to call this user SearchUserCustServ.
We'll walk through the administrator configuration, as well as what it looks from the perspective of the search users. The three main references for performing this configuration are:
- Configure permissions filtering for Content Search
- Filterable properties for the -RecipientFilter parameter.
- Keyword queries and search conditions for Content Search
Since all of the configuration is performed from PowerShell, the first thing we need to do is connect to PowerShell for both the Security & Compliance Center as well as Exchange Online. It's important to note that the Security & Compliance Center does have some cmdlets that overlap the Exchange Online cmdlets. In my normal configuration, I use "-Prefix SCC" to differentiate the commands exported by the Security & Compliance Center so I know which ones I'm executing. For the purposes of this session, we're going to rely on the -DisableNameChecking and -AllowClobber parameters to allow the Security & Compliance cmdlets to take precedence over the Exchange cmdlets with the same names.
To do this, I'm just using a simple connect script. You can add this as a function to your PowerShell profile if that makes your life better. I just saved this code as EXOSCC.PS1, saved a credential object, and then ran it.
param(
[System.Management.Automation.PSCredential]$UserCredential = (Get-Credential)
)
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.outlook.com/powershell-liveid -Credential $UserCredential -Authentication Basic -AllowRedirection
Import-PSSession $Session -DisableNameChecking
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.compliance.protection.outlook.com/powershell-liveid -Credential $UserCredential -Authentication Basic -AllowRedirection
Import-PSSession $Session -AllowClobber -DisableNameChecking
$Host.UI.RawUI.WindowTitle = $UserCredential.UserName + " (Exchange Online + Compliance Center)"
Here it is in action:
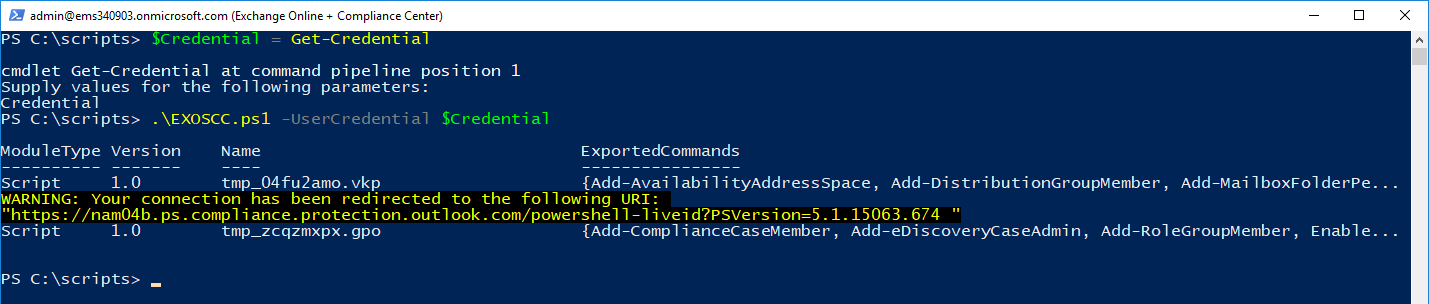
Once you're connected, verify that you have the cmdlets for both endpoints available to you. You can try something like Get-Mailbox to verify Exchange Online connectivity and Install-UnifiedCompliancePrerequisite to verify connectivity to the Security & Compliance Center:
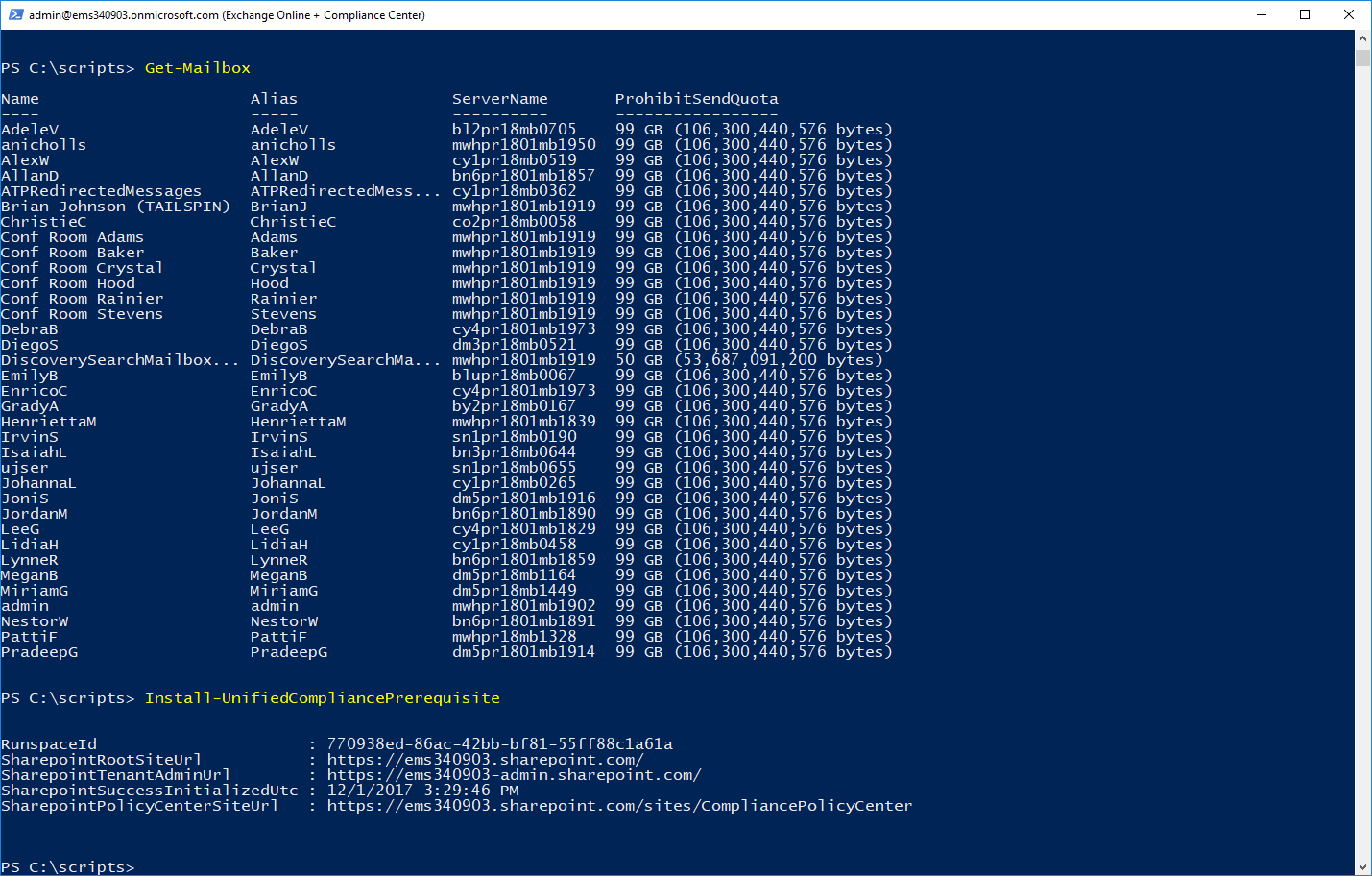
Before we get started with setting the filters, we need to create our Security Users and assign them the basic permissions that they're going to need to perform eDiscovery.
Create the users:
New-MsolUser -UserPrincipalName SearchUserStartsWithD@ems340903.onmicrosoft.com -FirstName SearchUser -LastName StartsWithD -DisplayName SearchUserStartsWithD -ForceChangePassword $False
New-MsolUser -UserPrincipalName SearchUserMarketing@ems340903.onmicrosoft.com -FirstName SearchUser -LastName Marketing -DisplayName SearchUserMarketing -ForceChangePassword $False
New-MsolUser -UserPrincipalName SearchUserCustServ@ems340903.onmicrosoft.com -FirstName SearchUser -LastName CustServ -DisplayName SearchUserCustServ -ForceChangePassword $False
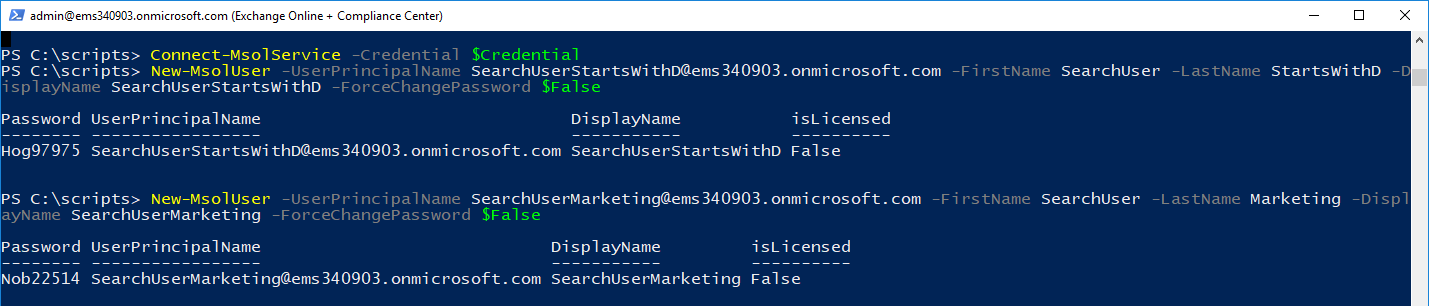
Don't worry--I changed the passwords. ;-)
And add them to the eDiscoveryManager role group:
Add-RoleGroupMember -Identity eDiscoveryManager -Member SearchUserStartsWithD@ems340903.onmicrosoft.com
Add-RoleGroupMember -Identity eDiscoveryManager -Member SearchUserMarketing@ems340903.onmicrosoft.com
Add-RoleGroupMember -Identity eDiscoveryManager -Member SearchUserCustServ@ems340903.onmicrosoft.com
Get-RoleGroupMember -Identity eDiscoveryManager
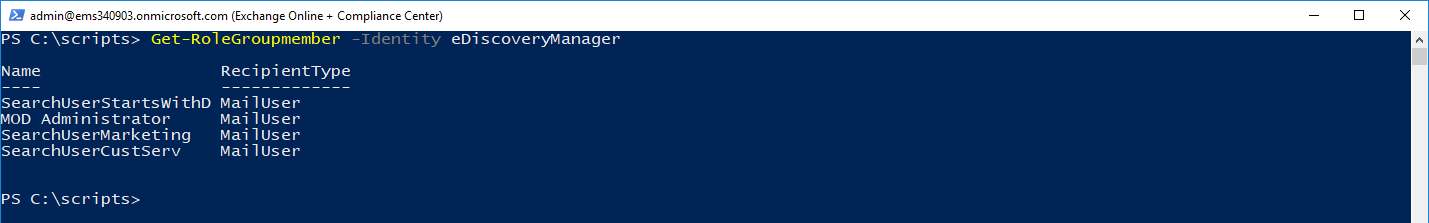
Note: You don't have to create the users or add them to the Role Groups inside PowerShell. I was already here, so it was easy (plus I'm lazy). You can create users via the Admin Center, and then navigate to the Security & Compliance Center | Permissions area and add the users to the eDiscovery Managers role group or any custom role group you've created if you're limiting the actions that can be performed. Additionally, if you want to be able to manage more easily via the Security & Compliance Center, you'll need to create Role Group inside the Security & Compliance Center and then use the Name of the Role Group for the -Users parameter when creating the filter.
Now, we're ready to really get started.
Creating the Search Filters
If you'll recall, we had three requirements, which will manifest themselves in three separate compliance security filters:
- SearchUserStartsWithD can only search mailboxes of users whose names start with D.
- SearchUserMarketing can only search mailboxes whose department is Marketing.
- SearchUserCustServ can only search for Instant Messaging and Contacts inside mailboxes whose department is CustomerService.
When we create the compliance filters, we're going to be using the Filters parameter with special keywords that indicate what parameters we're using. These keywords are "Mailbox_" and "MailboxContent_". We then use the values in the above articles for RecipientFilter parameters or Keyword content filters.
SearchUserStartsWithD
To create this filter, we're going to look in the FirstName and DisplayName properties of a user's mailbox. In these examples, we're just going to use the -Actions All parameter to allow the eDiscovery manager users to perform all relevant eDiscovery functions (search, hold, preview, export). You can specify a more limited set of actions if necessary. Available actions include Export, Preview, Purge, Search, and All.
New-ComplianceSecurityFilter -FilterName "Users that Start with D" -Users SearchUserStartsWithD@ems340903.onmicrosoft.com -Filters "Mailbox_FirstName -like 'D*' -or Mailbox_DisplayName -like 'D*'" -Action All
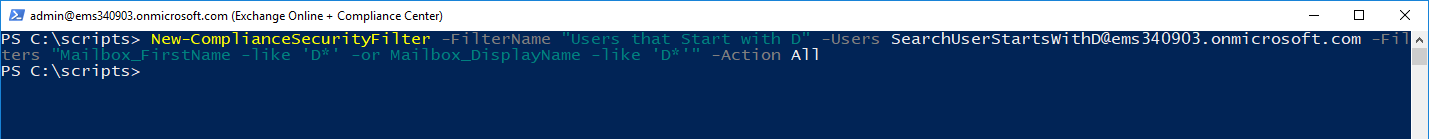
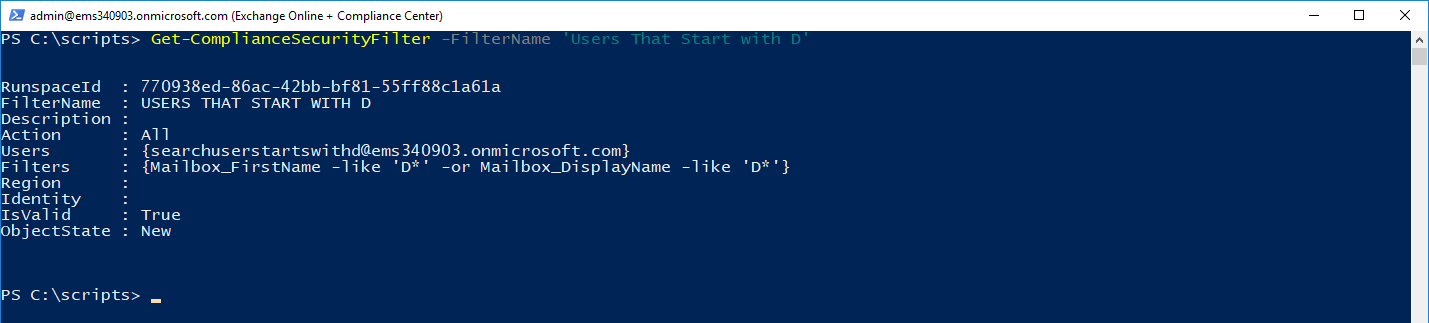
Verify that the filter has been created successfully by running the Get-ComplianceSecurityFilter cmdlet:
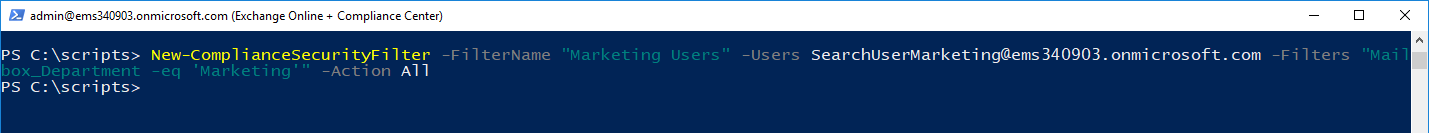
SearchUserMarketing
In this case, we're still going to use the Mailbox_ filter keyword, but use the Department property:
New-ComplianceSecurityFilter -FilterName "Marketing Users" -Users SearchUserMarketing@ems340903.onmicrosoft.com -Filters "Mailbox_Department -eq 'Marketing'" -Action All
SearchUserCustServ
The final search filter that we're going to create is for Customer Service. In this filter, we're going to specify both a Department (using the Mailbox_Department keyword construct) as well as the MailboxContent_ keyword. Per the documentation, you can't mix types of filters (Mailbox_<attribute> and MailboxContent_<type>), so I ended up creating two filters:
New-ComplianceSecurityFilter -FilterName "Customer Service Users - User Scope" -Users SearchUserCustServ@ems340903.onmicrosoft.com -Filters "Mailbox_Department -eq 'CustomerService'" -Action All
New-ComplianceSecurityFilter -FilterName "Customer Service Users - Instant Message and Contact Scope" -Users SearchUserCustServ@ems340903.onmicrosoft.com -Filters "MailboxContent_Kind -eq 'im' -or MailboxContent_Kind -eq 'contacts" -Action All
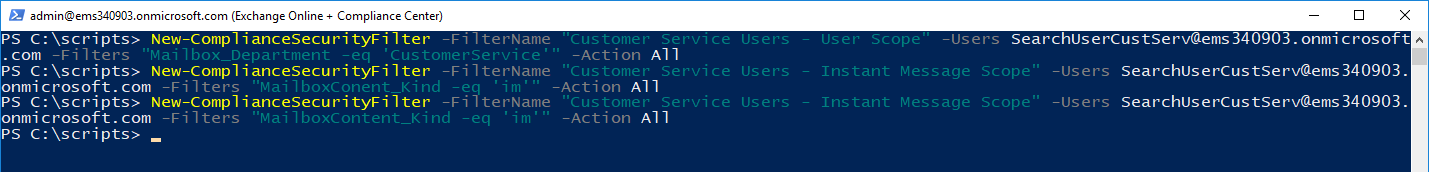
To verify that both filters exist:
Get-ComplianceSecurityFilter | ? { $_.FilterName -like "Customer*" }
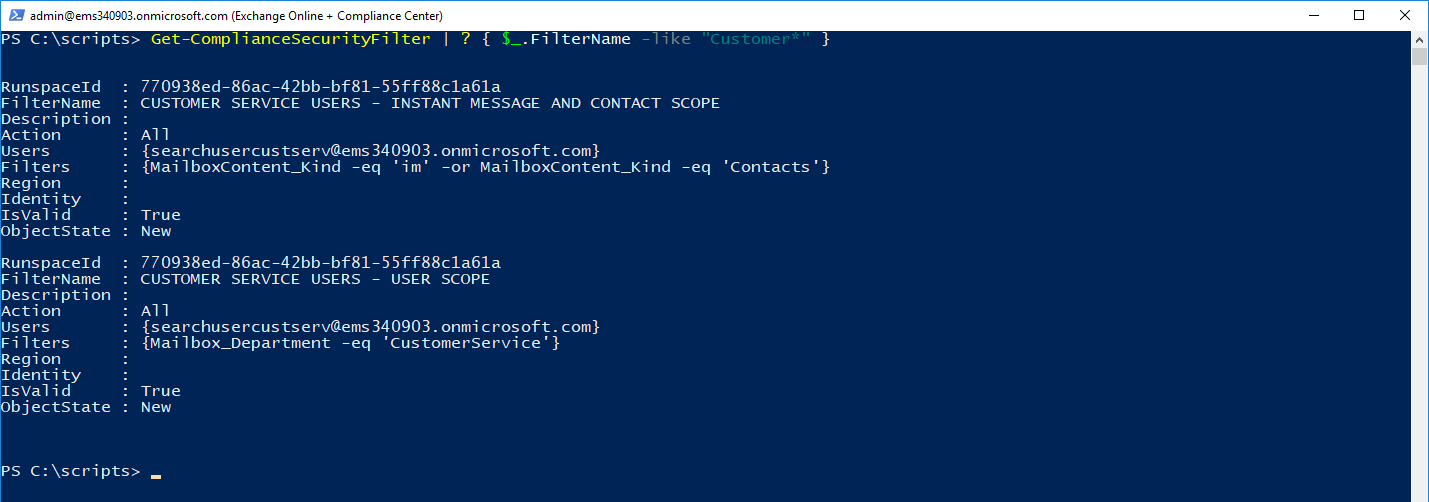
Now, we can get down to the business of searching.
Conducting the Searches
To really see the filters in action, we're going to log in as each of our search users and then create some test searches. However, we want to make sure that we're going to actually have mailboxes to search. As you recall, we should be searching 3 distinct sets of mailboxes:
- Mailboxes for users starting with D

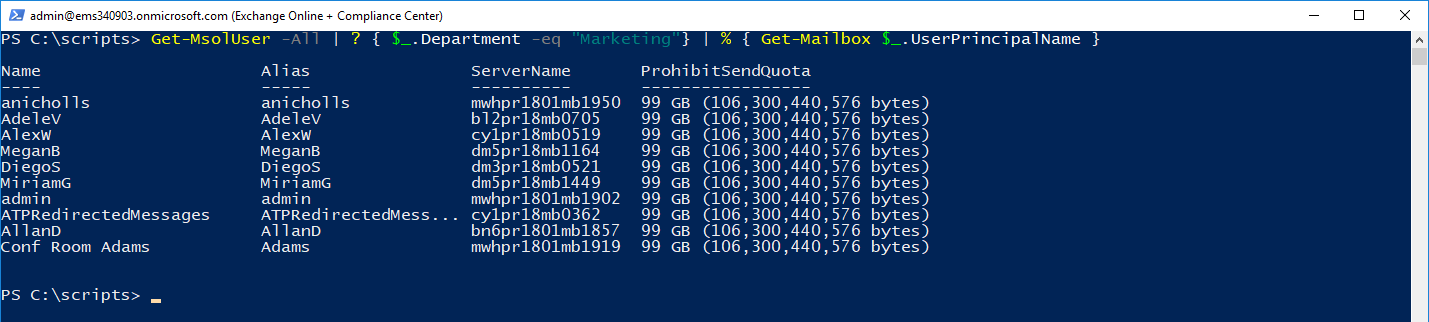
- Mailboxes for users with Department Marketing
- Mailboxes for users with Department CustomerService
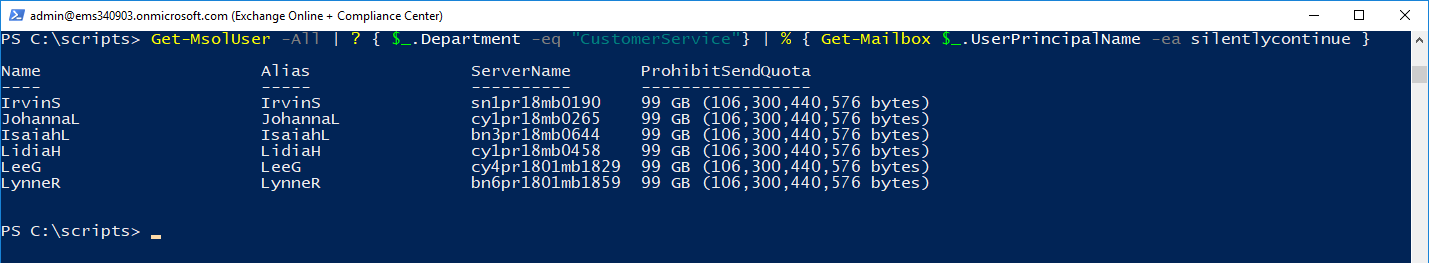
Notice we have one user whose name starts with D who is a member of the Marketing department, indicating results from that mailbox should show up in both the StartsWithD filter and the Marketing department filter.
Now, let's try out some searches!
SearchUserStartsWithD
To begin our adventure, I'm logging into the Security & Compliance Center with my user SearchUserstartsWithD@ems340903.onmicrosoft.com.
- Navigate to Search & Investigation | eDiscovery and click + Create a new case. Provide a name and description, and click Save.
- Open the case.
- Navigate to the Search tab, and click the + to start a new search.
- Add a few mailboxes. In this example, I want to test to make sure the compliance filter works, so I'm going to add mailboxes that DO NOT meet the criteria. To do so, select the "Custom location selection" radio button, then the "Choose specific mailboxes to search" radio button, and then click the + sign. Select AdeleV and PradeepG and add their mailboxes to the search list. Then, click Next.
- In order to make sure we're not getting any data back that doesn't meet the security filter, just leave the keyword and conditions blank and click Search.
- As the search completes, it should return 0 items (since the compliance security filter indicates this user is unable to search mailbox unless the names begin with "D").
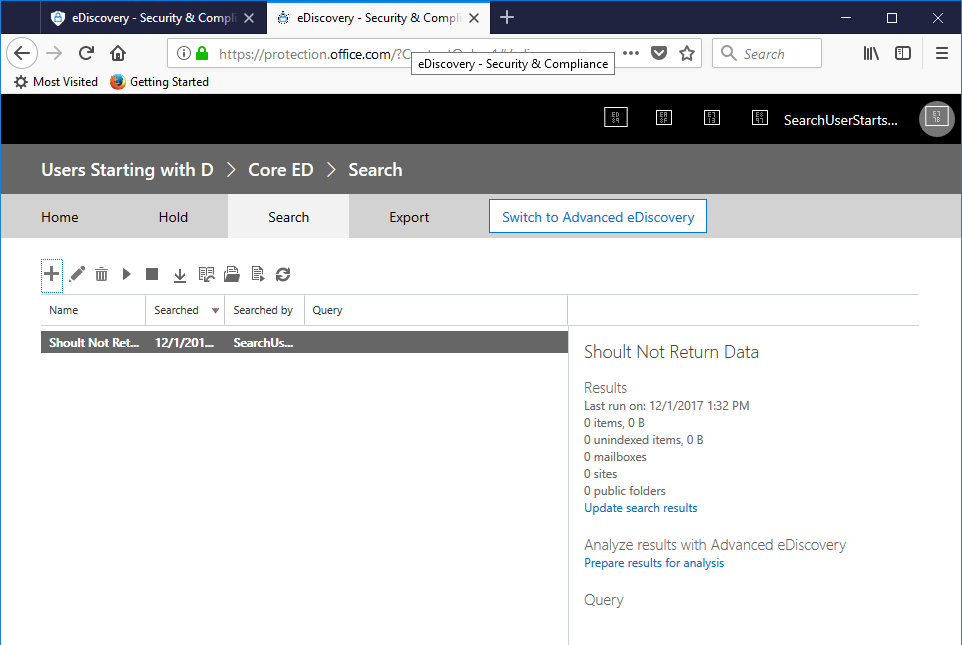
- Now, to create a search that has mailboxes matching our security filter. Click the + again, but this time, add mailboxes for Diego and Debra and then click Next.
- After configuring the search (no keyword or condition filters again, just to make this an easy search and verify that the filtering works), the search should return results for data in the selected mailboxes.
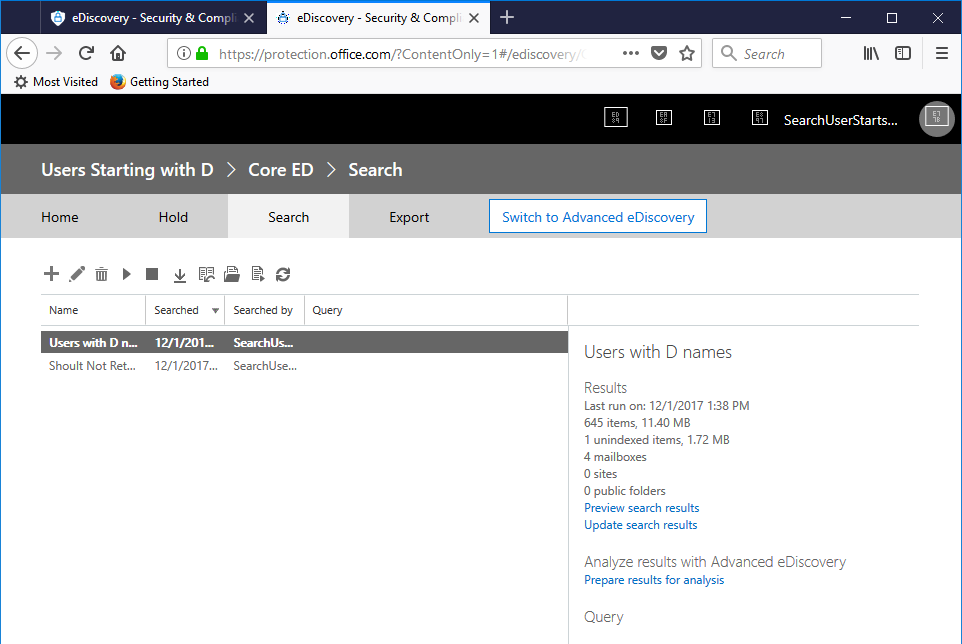
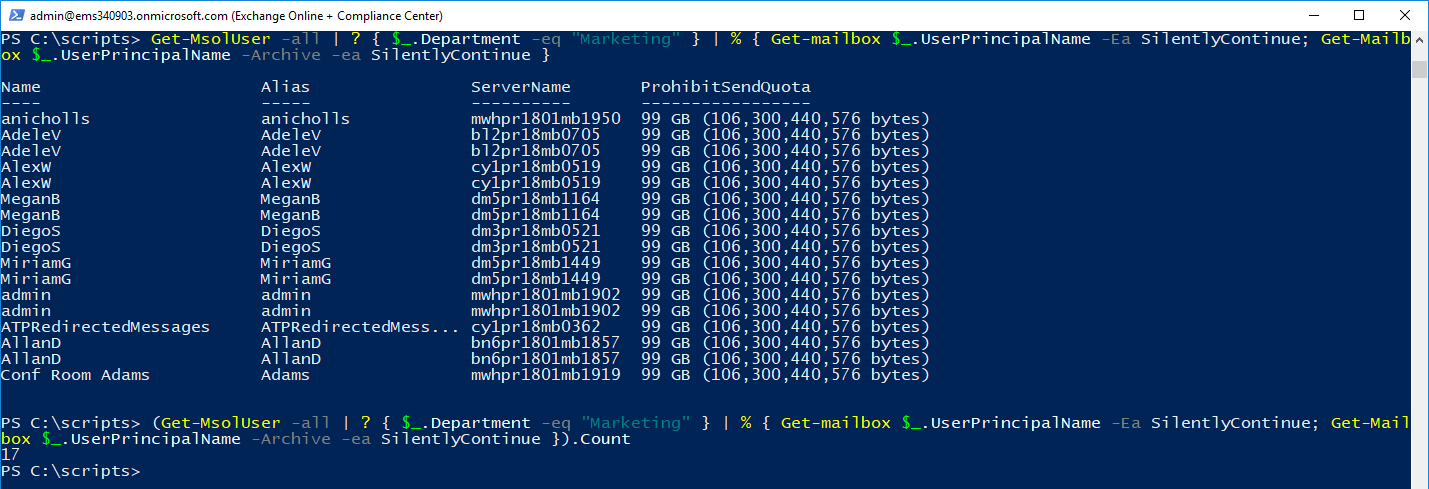
Note: In this example, there are 4 mailboxes listed in the detail pane. Each of these users have Archive mailboxes enabled, so they are being searched as well. - Click Preview Search Results to see the content in the mailboxes.
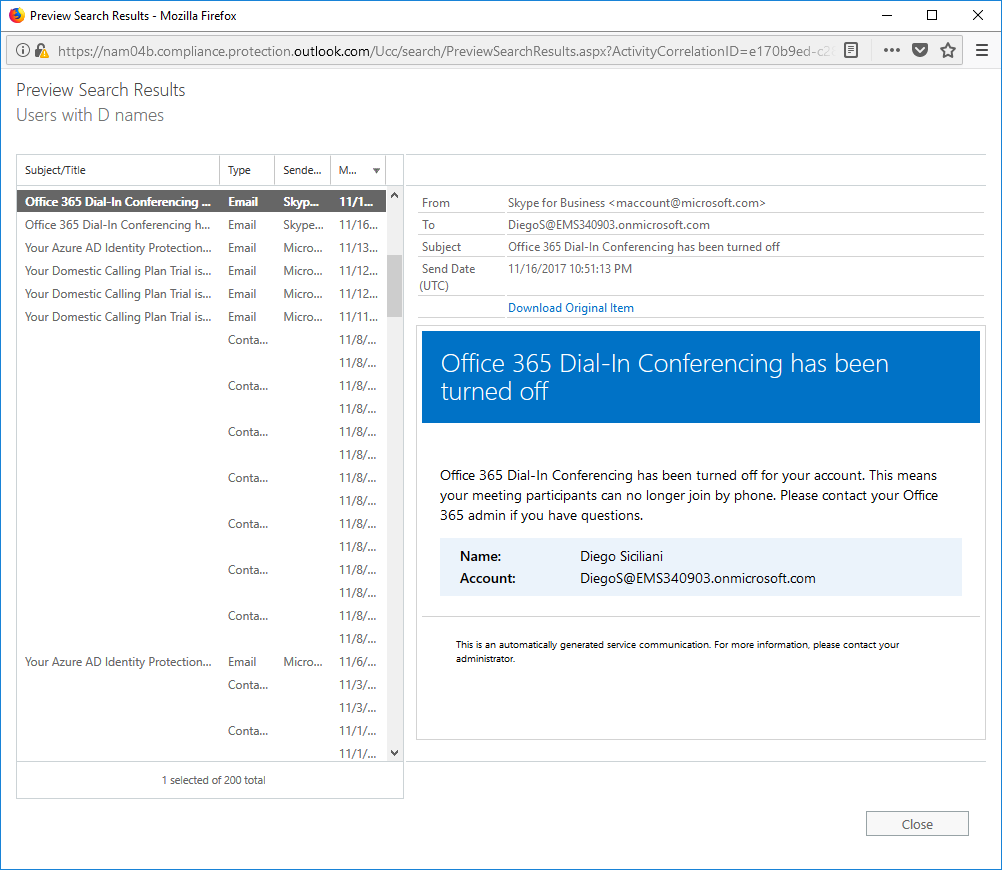
- After you're satisfied with the results, click Close. You can then choose to hold or export the data. For the purposes of the demo, we're going to just move on to the next case (Marketing mailbox search). Log out of the Security & Compliance Center.
SearchUserMarketing
- For the second test, I'm going to log into the Security & Compliance center as SearchUserMarketing@ems340903.onmicrosoft.com.
- Navigate to Search & Investigation | eDiscovery, and click + Create a case to create a new eDiscovery case. Provide a name and description, and click Save.
- Click the Search tab.
- Click + to start a new search. As with the previous test, we first want to select something that should be excluded to make sure we're not returning content.
- Select a few users that don't have the Department value set to Marketing.
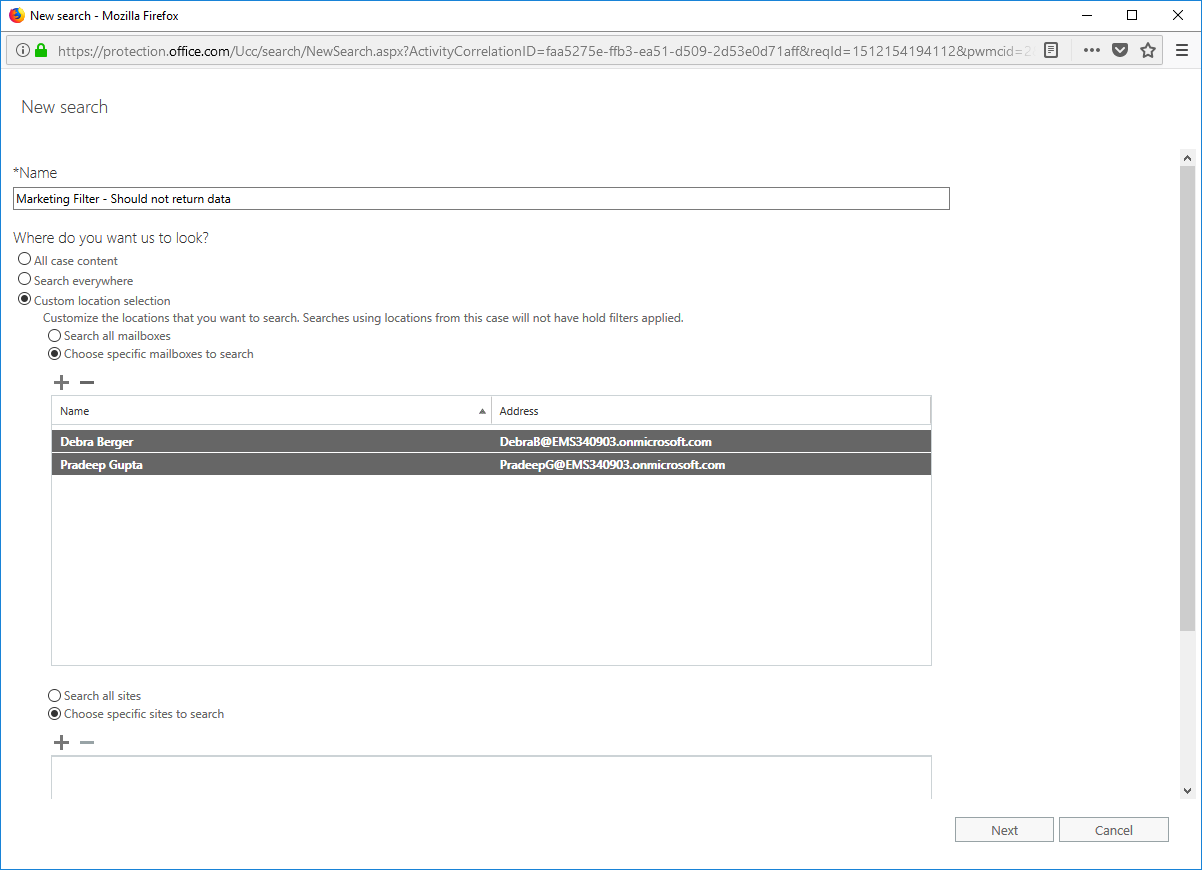
- Click Next to advance the page.
- Complete the search configuration without any conditions or keywords, and click Search.
- Verify that no results are returned.
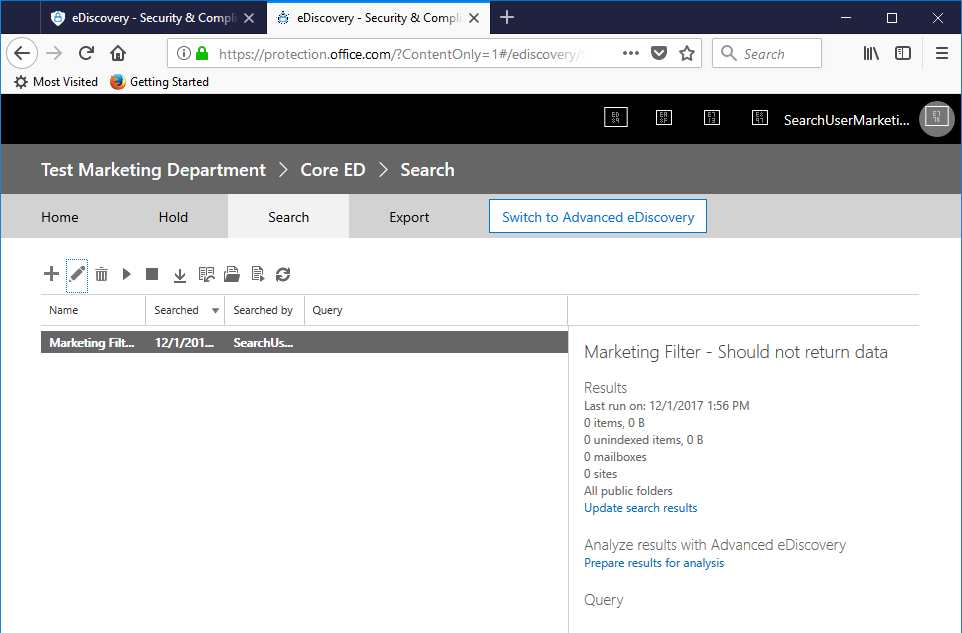
- Create a new search, but this time, instead of selecting individual mailboxes, select the radio button for "All Mailboxes."
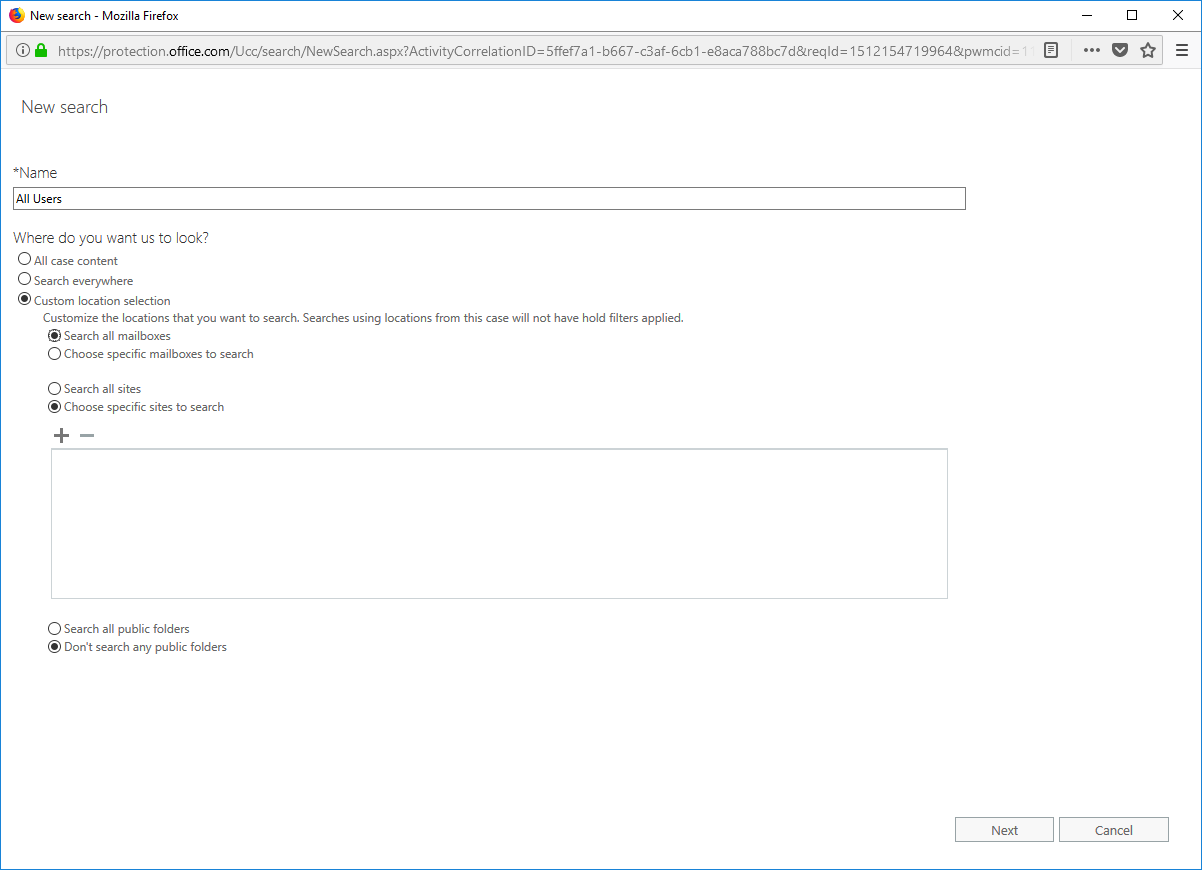
- Click Next, and then click Search with no keywords or conditions specified to search all mailboxes.
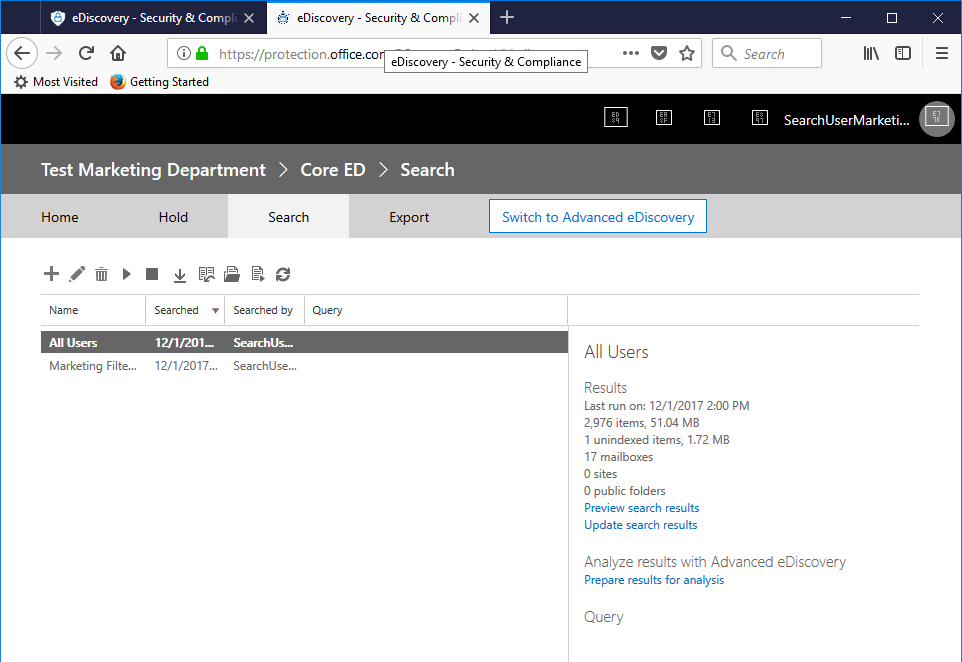
Again, notice that the mailbox number includes archive mailboxes:
In this case, you can see that even though we used the "All mailboxes" radio button, the results are limited to the scope of only the mailboxes (including archives) meeting the Compliance Security Filter parameter (Mailbox_Department -eq 'Marketing'). - Log out of the Security & Compliance Center.
SearchUserCustServ
In the final test, we're going to search the mailboxes for the users in the CustomerService department. Per our filter, we should only see IM and Contact object types.
- Log into the Security & Compliance center as SearchUserCustServ@ems340903.onmicrosoft.com.
- Navigate to Search & Investigation | eDiscovery, and click + Create a case to create a new eDiscovery case. Provide a name and description, and click Save.
- Click the Search tab.
- Click + to start a new search. As with the previous test, we first want to select something that should be excluded to make sure we're not returning content.
- Select a few users that don't have CustomerService as their Department value (such as Marketing users returned in the previous results).
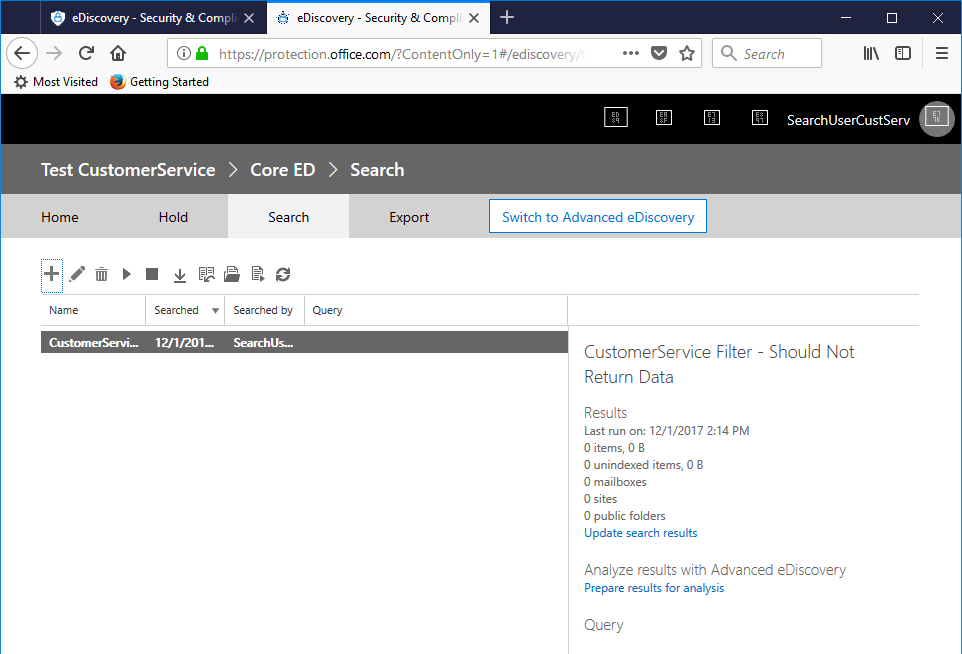
- Click Next, and then click Search without entering any search conditions or content keywords.
- Verify the results.
- Create a new search, only this time select a user that you know has the correct department value and click Next.
- On the Keyword and Conditions page, leave both areas blank and click search. Per our Compliance Security filter, we should only receive search results for instant messages (MailboxContent_Kind -eq 'im') and contacts (MailboxContent_Kind -eq 'contacts').
- After the search completes, you should see results.
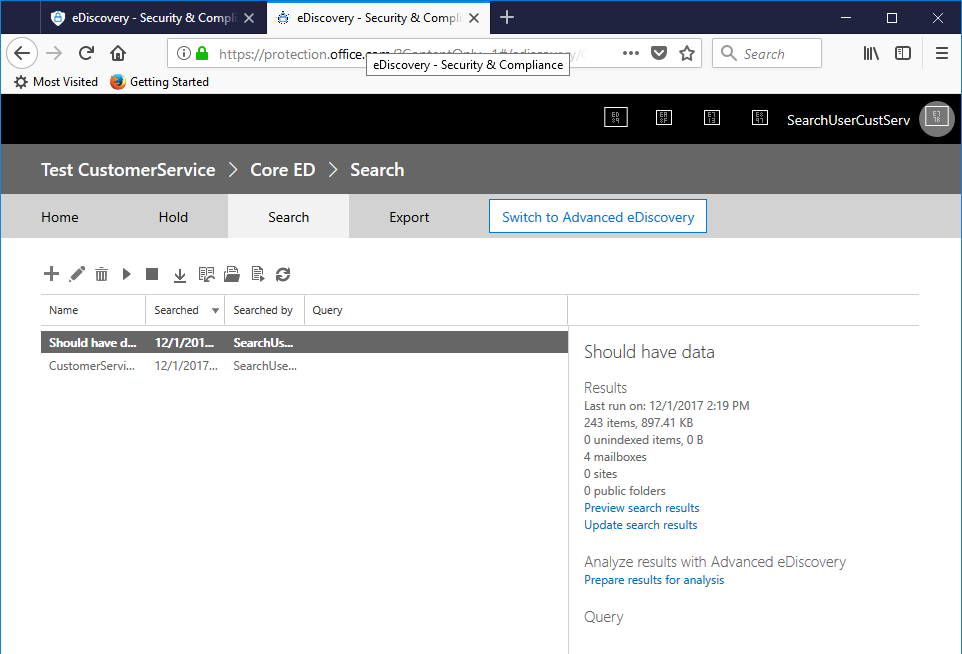
- Now, for the moment of truth--click Preview Search Results and check what types of items were returned.
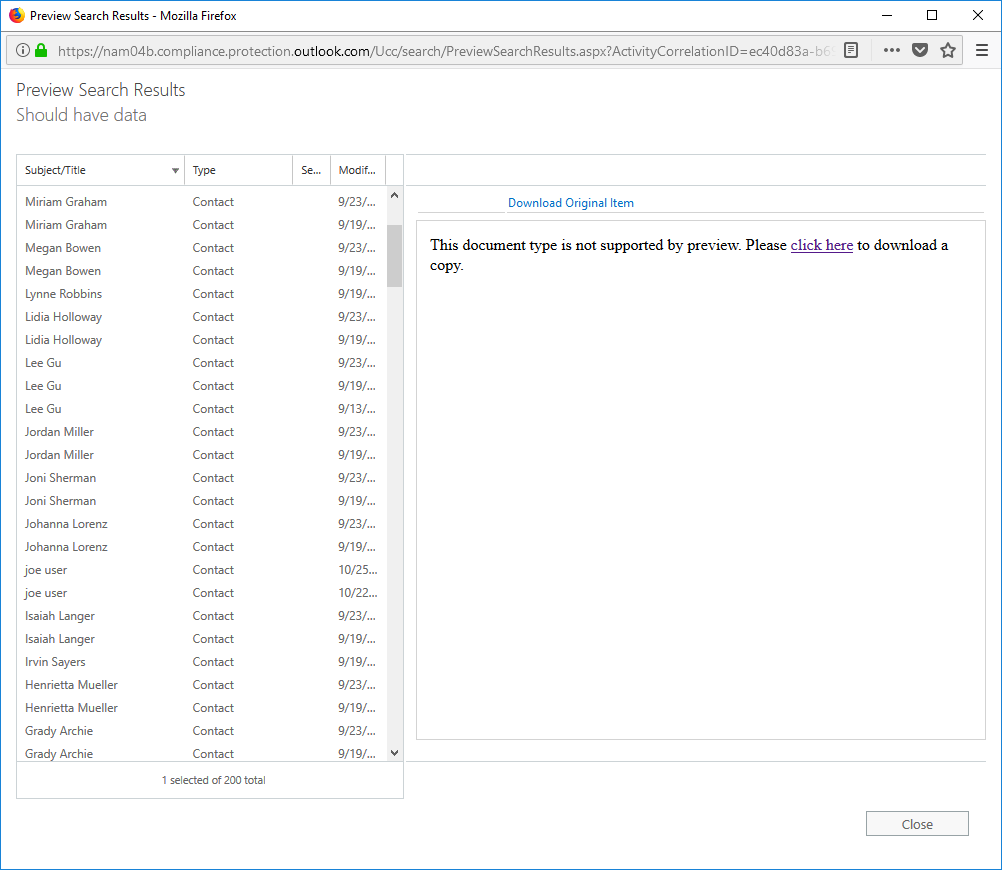
This is exactly the result we're looking for.
Some important takeaways:
- Even if you have have created compliance filters that restrict the mailboxes that can be searched by a user, a user can still add them to a search via the Add Mailbox interface. They just won't return data.
- When searching mailboxes, archive mailboxes are included. That accounts for the mailbox count not necessarily matching what you think it should.
- At this time, some compound compliance filters will not work (such as "Mailbox_Department -eq 'Marketing' -and MailboxContent_Kind -eq 'im'"). To work around that, you need to create two separate compliance filters. They are joined together so that the most restrictive set of content applies.
Be sure to check out part 2 of this post, where we create a custom role group for our search users!
Happy searching!
Comments
- Anonymous
December 02, 2017
Awesome stuffi seen this requirement many times but didn't know it was possible to achieve it Thanks- Anonymous
December 03, 2017
Our documentation has some good examples on cmdlets that can be run, but doesn't always have a lot of context around why they might be useful. Sometimes juxtaposing the capabilities with some real requirements helps you see some of the potential. I also learned that some of the cmdlets don't work as expected and had to figure out some workarounds, which I have feed back to our internal folks.
- Anonymous
- Anonymous
December 05, 2017
How does this work if a user separates employment that was on Litigation Hold that the Compliance Search user had access to? Will the filterable properties still apply to the separated employees old mailbox? Will that data that is on Lit Hold applied to still show up in a Discovery search?- Anonymous
December 05, 2017
When a mailbox is on-hold (either via the Litigation Hold applied to the mailbox, a content search hold, an eDiscovery case hold, or a Retention Policy), the mailbox is preserved even in the event that the user is removed. Depending on the filterable properties that you use, the mailbox may fall out of scope when you update a search (like if you reassign the SMTP address to reclaim it and have a filter based on SMTP suffix). I'll run a few tests and let you know what I see.
- Anonymous