Azure PIM - initial walkthrough and links aka.ms/Azure/PIM
In this post, I am taking another shortcut out of the aka.ms/Azure/Shortcuts page and expanding it out a little more. The Azure PIM documentation is pretty detailed on azure.microsoft.com. But as I was setting up my lab to demonstrate this, I wanted to capture the setup of this for others as I was doing this. For those old enough to remember, we'll call it "The Readers' Digest Condensed" version of the many resources out there. Or for you Chemists out there, "The Distilled Version". This distillation simply does a visual walkthrough of getting Azure PIM up and running, and then shares the many links at the end.
Azure Privileged Identity Management (PIM) summary
With administrative rights in Azure Active Directory (AD), these powers traverse many different parts of the cloud that mayt be owned by your organization in various Microsoft subscriptions and also SaaS applications. When you assign a user to an Azure AD administrative role, it is permanent. To reduce the potential intended or non-intentional damage from improper use of such accounts, we want to apply the concept of least privilege and for only the duration of time as needed. This is also known as JEA and JIT or "Just Enough Access" and "Just In Time".
To watch and learn about all of the related protections for Azure AD identities, make sure to watch the Ignite 2016 session on Respond to advanced threats before they start - identity protection at its best!
You may know this already, but just to be clear, Azure AD is a directory (tenant) that your company may own and should ideally be shared across any other Microsoft subscription services that you may have e.g. an Azure Subscription, Office 365, Intune or Dynamics CRM. As a common directory that provides authentication across these various services, these powers must be limited due to the scope of influence across those services/subscriptions.
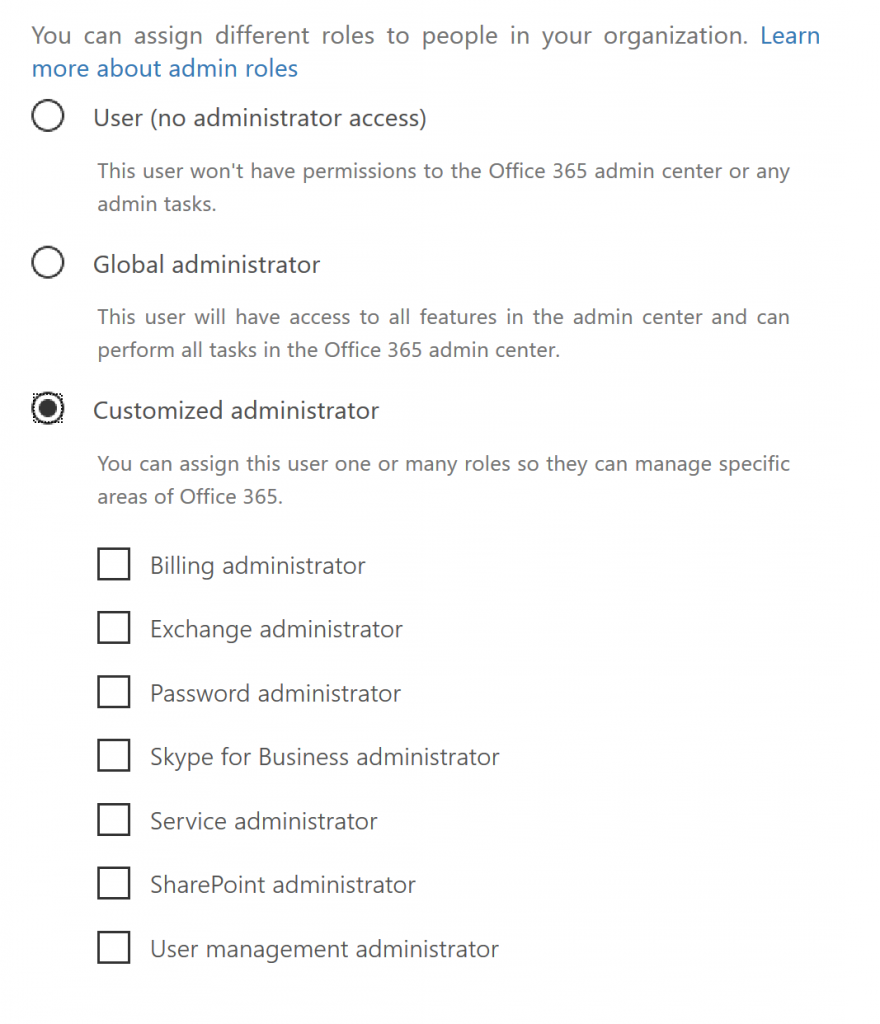
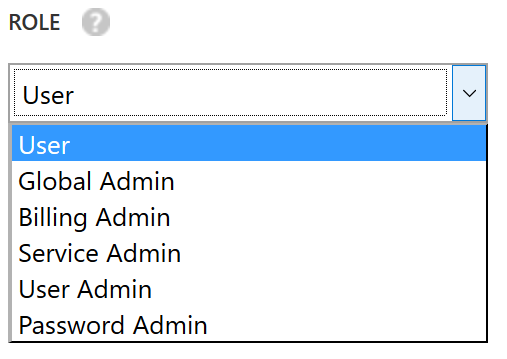
Azure AD roles are not to be confused with Administrative rights in an Azure Subscription (see aka.ms/Azure/Administration). But even the Azure AD roles can be a little confusing if you bounce around interfaces of the different services that you may subscribe to as noted above. So if you are looking at portal.office.com (left below) and then go to portal.azure.com (right below) you'll see different roles listed.
If you go into the Office Administration portal and select some of the "Customized administrator" roles that are not shown on the right side above e.g. Exchange, Skype or Exchange administrators, those roles will not be shown the same way when you select the same user accounts in the Azure AD portal. Instead of those office-specific roles, their roles will show up as a User role when looking at them in the azure active directory adminstration portal .
So what's the point of all that you ask? It has to do with what exact roles that Azure PIM will manage. If you look at the article Assigning administrator roles in Azure Active Directory, the list is even larger as it will account for specialized roles in Intune and CRM also. The list of roles managed by Azure PIM within an "Azure Subscription" include the following from Azure AD:
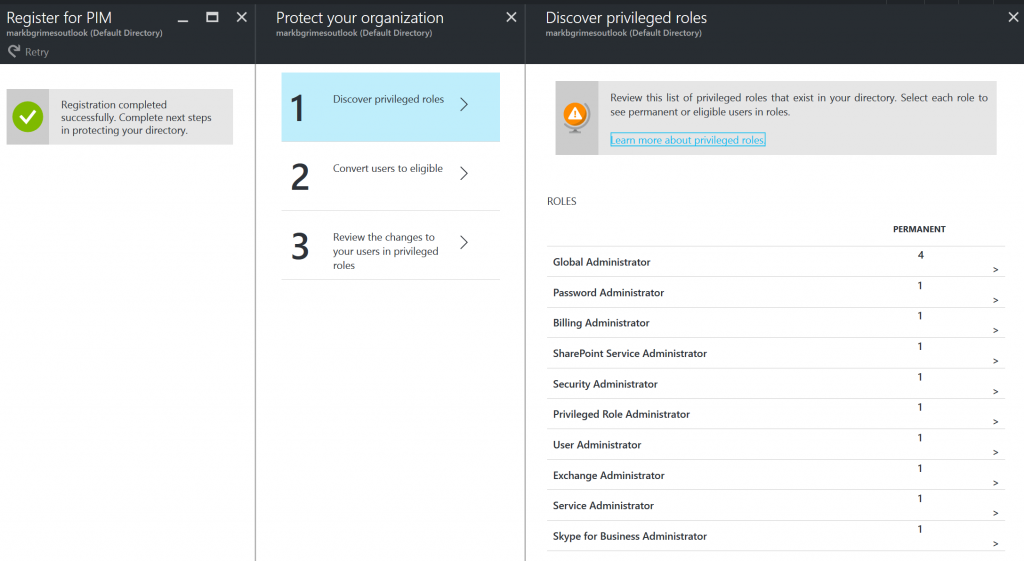
- Global Administrator
- Billing Administrator
- Service Administrator
- User Administrator
- Password Administrator
In consideration of the other administrative roles within Office 365, please be sure to read Roles in Azure AD Privileged Identity Management which explains exactly what will and will not be covered by Azure PIM. That list is larger than the five listed above and includes many others that show themselves up in Office 365, as I showed in the picture above from my Office 365 admin portal.
Prerequisites
We want to call these out first before you start the process of registration for this application.
- Requires Azure Active Directory Premium P2 version
- Here are the options to get that
- To enable this, you must be a Global Administrator with an organizational account (@company.com), and not a Microsoft account e.g. @outlook.com
- The organizational account must be enabled for Multi-Factor Authentication (MFA)
- Make a second backup Privileged role administrator...in case someone shows up missing!
- NOTE: you can only do this once you have Azure PIM all setup
Azure PIM Visual Walkthrough
As I used to do as a trainer, I like to make "mistakes" happen, so you can also see when things go wrong and why. At least that's my "excuse".
Once you have the prerequisites in place then getting Azure PIM moving ahead looks like this...
First login to https://portal.azure.com.
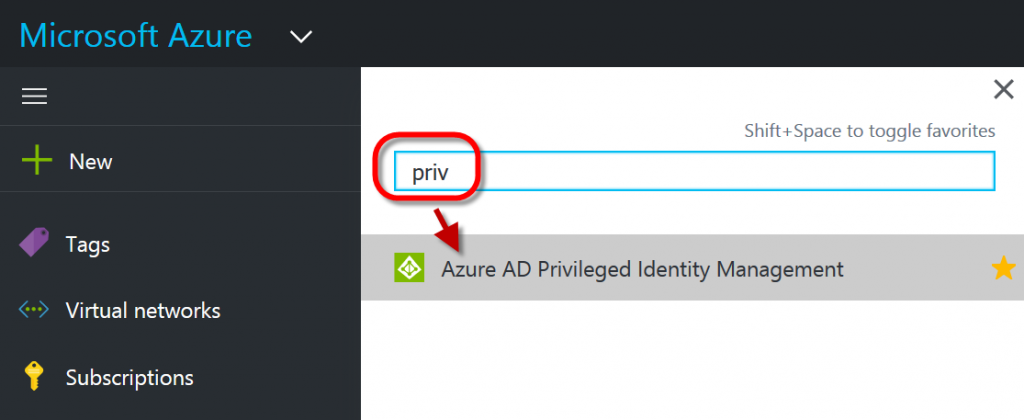
Once you have logged into your Azure portal, press the letter B and type priv. Then click on "Azure AD Privileged Identiy Management."
NOTE: "B" is a shortcut for Browse. Try pressing ? in the portal and you'll see ALL the portal shortcuts!
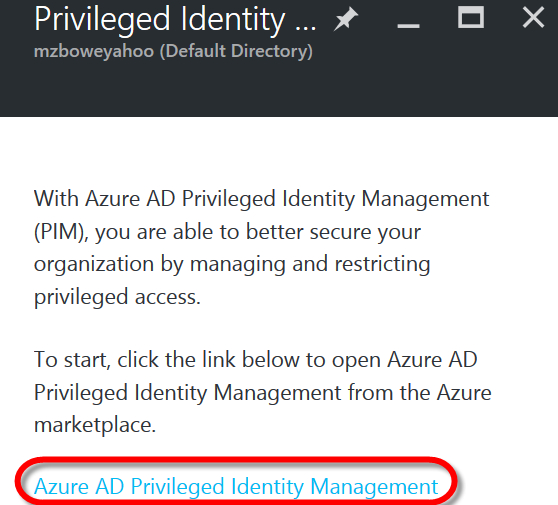
At the next dialog box that appears, click on the hyperlink at the bottom for "Azure AD Privileged Management"
The step above launched the option to pull this from the Azure Marketplace. So now you get to click it again :)
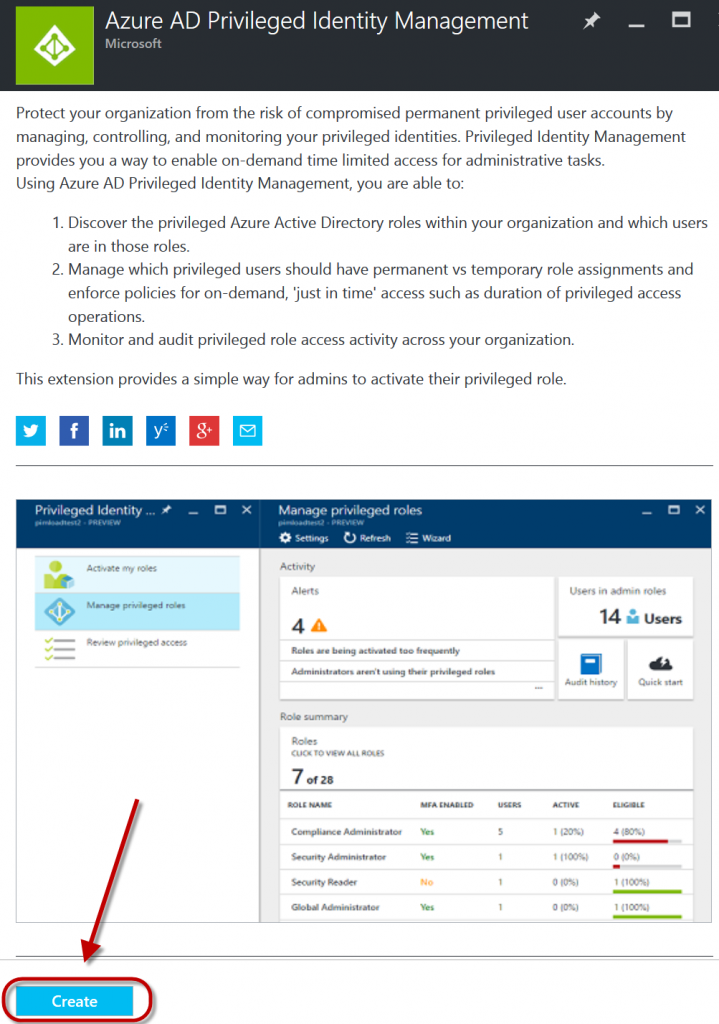
Now you will click Create at the bottom of the next dialog box to install this capability into your portal. This dialog box also describes the ability to Discover, Manage and Monitor your privileged role access for Azure AD.
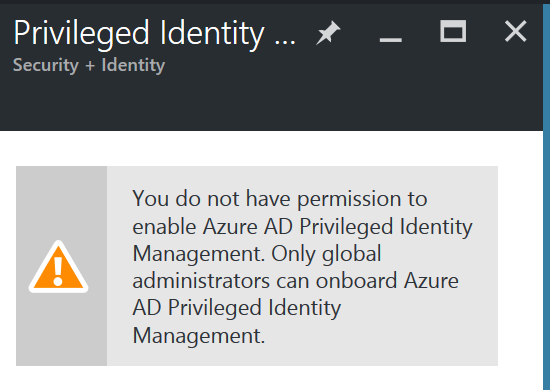
Well since I was in a hurry and did not follow my own prerequisites, I got this nice warning which tells me what I missed :) When I went back to Azure AD, I saw that my account was indeed a "Global Administrator". But, it was not an Organizational Account. So that is what I had to fix, even though the error said it was an issue with not being "Global Administrator".
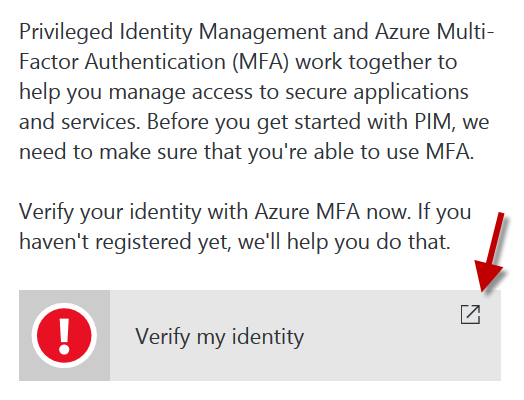
Assuming you didn't make that same mistake, or else you also corrected it, here is what happens next. And another error message. This one is good, as it reminds me of the other pre-requisite I missed. If you setup MFA for your account, skip ahead! after clicking on the box below in your portal.
Since I hadn't done the MFA setup, here is what that looks like...
Then after clicking Set it up now above...
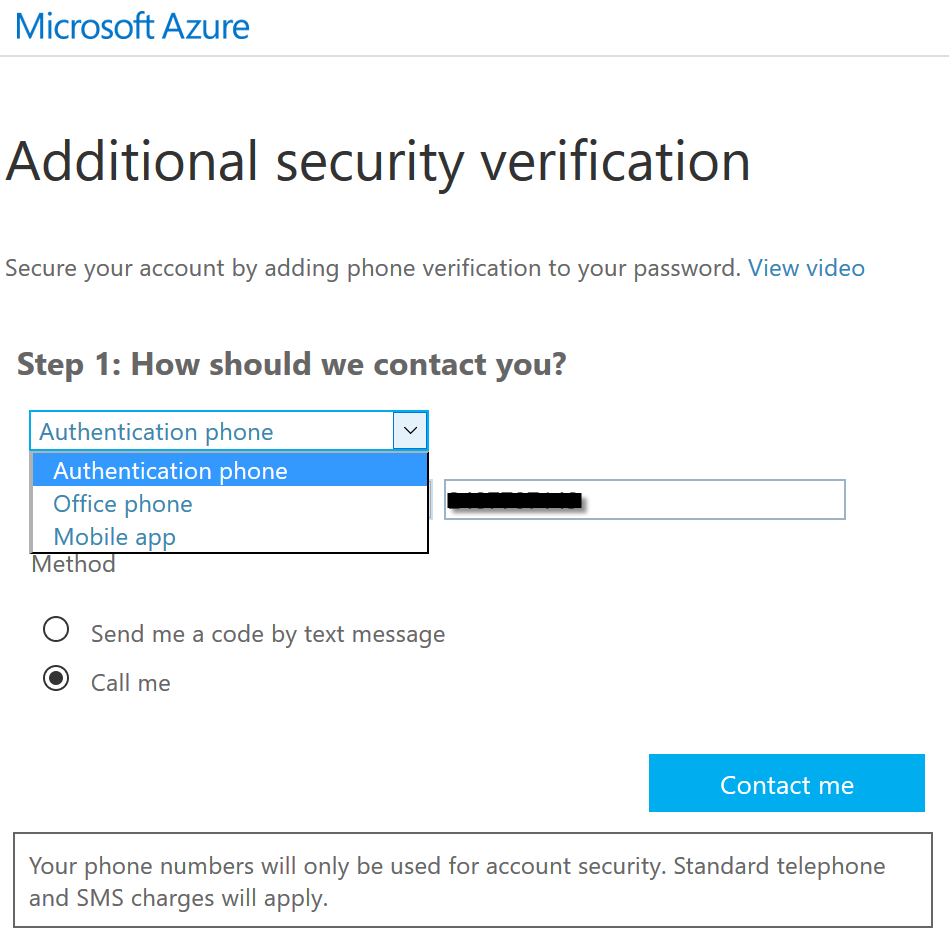
You can select the method of verification you choose, as shown in the drop-down box below
Then click Contact me
After you complete your verification, the window will say "Verification successful!" Then click Done
NOW, that all pre-requisites have been met, you can finally click Create for real!
As it sets it all up, it will scan Azure AD for all privileged role assignments
Now that Azure Privileged Identity Management has been properly registered with your Azure Subscription, the rest of the steps are well documented for using this service in the Reference Links below. There will be 3 remaining steps to get you there..
- Discover privileged roles.
- this is where you will review the list of privileged roles that exist in your directory.
- Then you will select each role to see permanent or eligible users in roles.
- Convert users to eligible.
- Review the changes to your users in privileged roles
After you have made changes, the wizard above will no longer show up. The next time you or another privileged role administrator use PIM, you will see the PIM dashboard.
NOTE: Once you walk through the wizard above, you will notice that the account the was used to set this up is locked in with three roles.
- Global Administrator - which you started with
- Privileged Role Administrator
- Only a privileged role administrator can access this application to manage the access for other administrators. The global admin account you used to start this has this role by default.
- Security Administrator
- I am seeking to confirm exactly what this covers, but wil update. For now I beleive it may be tied to the description for Security Administrator at Assigning administrator roles in Azure Active Directory
Azure PIM Administration Links
- Get started with Azure Privileged Identity Management
- Roles in Azure AD PIM
- The security wizard
- How to give other admins access to Privileged Identity Management
- How to add or remove a user role
- How to activate or deactivate a role
- How to change or view the default activation settings for a role
- How to configure security alerts
- How to start an access review
- How to perform an access review
- How to complete an access review
- How to require MFA
- How to use the audit log