New step-by-step deployment for Office 365 federated authentication in Azure
Inspired by CAAB member Trevor Seward’s presentation at the October 2016 CAAB webinar, there is a new Deploy high availability federated authentication for Office 365 in Azure set of articles that step you through a production deployment of the following:
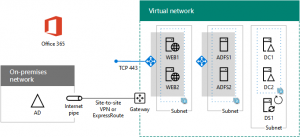
This configuration provides a highly-available and scalable infrastructure to support federated authentication with your on-premises Windows Server Active Directory (AD) for Office 365. You build this infrastructure in the following phases:
- Configure Azure infrastructure (resource groups, storage accounts, availability sets, and a cross-premises virtual network)
- Create and configure the Windows Server AD domain controllers
- Create and configure the AD FS servers
- Create and configure the web application proxy servers
- Use Azure AD Connect to configure federated authentication for Office 365
This configuration uses fill-in-the-blanks tables and PowerShell command blocks so that you can:
- Quickly create the needed set of Azure infrastructure elements with the correct settings.
- More easily customize the configuration, such as changing the numbers of servers in each tier or adding extra data disks to virtual machines.
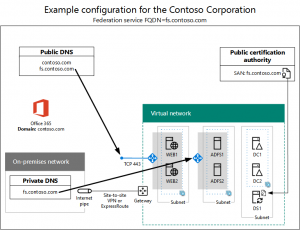
Here is an example configuration, including certificates and DNS settings, just prior to running the Azure AD Connect wizard:
Thanks to Trevor for his inspiration and review of the proposed configuration!
What do you think of this approach to deployment documentation? Let us know by leaving a comment below or sending a quick email to cloudadopt@microsoft.com.
To join the CAAB, become a member of the CAAB space in the Microsoft Tech Community and send a quick email to CAAB@microsoft.com to introduce yourself. Please feel free to include any information about your experience in creating cloud-based solutions with Microsoft products or areas of interest. Join now and add your voice to the cloud adoption discussion that is happening across Microsoft and the industry.