Manually Creating F5 Reverse Proxy for External Lync Web Services
In my previous position as a F5/Lync administrator, I was responsible for managing F5’s BIG-IP LTM and GTM as well as OCS/Lync infrastructure. Therefore, I like to fully understand what I’m implementing on my system. F5’s iApp is a great tool to use and it’s very helpful, however, in some cases, it’s necessary to set up things manually. In this posting, I’d like to share step-by-step instructions on how to manually configure F5 Reverse Proxy for the Lync External Web Services. This posting is intended for new F5 administrators or Lync administrators who are also tasked with configuring Lync Reverse Proxy on BIG-IP LTM.
These are the steps involved in configuring BIG-IP F5 LTM as a Lync Reverse Proxy:
- Creating a new TCP profile
- Exporting/Importing Lync Pool certificate
- Creating a new SSL Client profile
- Creating a new SSL Server profile
- Creating a new HTTPs Monitor
- Creating a new Lync Front End Pool
- Creating a new Virtual Server
Note: These instructions are based on:
- BIG-IP v11.x
- Single BIG-IP LTM deployment for all internal and external Lync Server services
- Lync Server 2013 only deployment
- No Lync Server 2013 Director roles deployed
1. Create a new TCP profile
1.1 From the main menu, navigate to Local Traffic – Virtual Servers – Profiles – Protocol – TCP
1.2 Click Create on the top right
1.3 Type in the name of the profile
1.4 Select tcp as the Parent Profile
Note: This will import all the values from the tcp baseline(parent) profile.
1.5 Check the Custom box on the top right
1.6 Change the Idle Timeout value from 300 to 1800 seconds
Note: BIG-IP LTM will reset the connection if the connection is idle for the configured Idle Timeout. This value can be modified as needed. In some cases, the firewall will terminate the idle connection before 1800 seconds.
1.7 Click Finished at the bottom of the screen
2. Export Lync Front End Pool certificate
2.1 From one of the Lync Front End servers, start the Certificates (Local Computer) console
2.2 Navigate to Personal – Certificates
2.3 Right-click on the Lync Front End Pool certificate and select All Tasks – Export
2.4 Click Next to continue
2.5 Select “Yes, export the private key” and click Next
2.6 Select “Include all certificates in the certification path if possible” and “Export all extended properties” and click Next
2.7 Select Password and enter the password for the private key and click Next
2.8 Select folder path and type in the file name and click Next
2.9 Click Finish to complete the exporting process
3. Import Lync Front End Pool certificate
3.1 From the main menu, navigate to System – File Management – SSL Certificate List
3.2 Click Import on the top right
3.3 Select PKCS 12 (IIS) as the Import Type
3.4 Type in the certificate name
3.5 Click Browse to locate the certificate (.pfk file) that you exported from the Lync Front End server
3.6 Enter the password
3.7 Click Import to complete the importing process
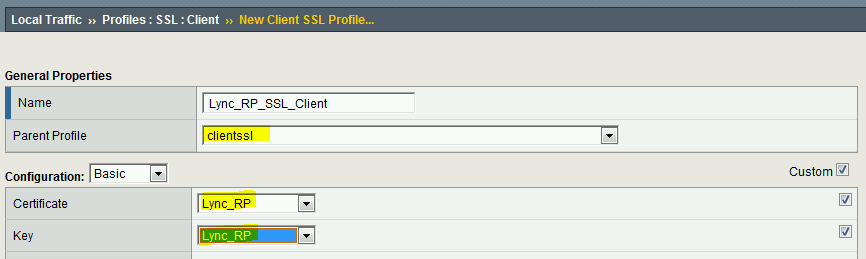
4. Create a new SSL Client profile
4.1 From the main menu, navigate to Local Traffic – Virtual Servers – Profiles – SSL – Client
4.2 Click Create on the top right
4.3 Type in the name of the profile
4.4. Select clientssl as the Parent Profile
Note: This will import/keep all the values from the clientssl baseline(parent) profile.
4.5 Check the Custom box on the top right
4.6 Select the certificate and key that you imported in the previous step
4.7 Click Finished at the bottom of the screen
5. Create a new SSL Server profile
5.1 From the main menu, navigate to Local Traffic – Virtual Servers – Profiles – SSL – Server
5.2. Click Create on the top right
5.3 Type in the name of the profile
5.4 Select serverssl as the Parent Profile
Note: This will import/keep all thevalues from the serverssl baseline(parent) profile.
5.5 Click Finished at the bottom of the screen
Note: You do not need to assign the certificate and the key.
6. Create a new HTTPS monitor
6.1 From the main menu, navigate to Local Traffic – Monitors
6.2. Click Create on the top right
6.3 Type in the name of the profile
6.4 Select HTTPS as the Type and https as the Parent Monitor
Note: This will import/keep all the values from the https baseline(parent) monitor.
6.5 Enter 4443 for the Alias Service Port
6.6 Click Finished at the bottom of the screen
Note: Jump to Step 8 if you already have a pool that load-balances Lync Front End servers on port 4443.
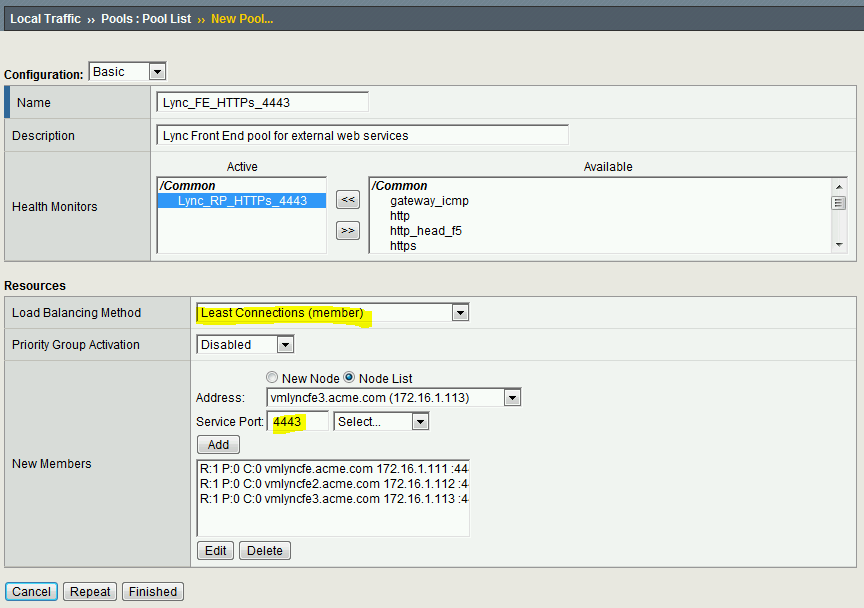
7. Create a new Pool
7.1 From the main menu, navigate to Local Traffic – Virtual Servers – Pools – Pool List
7.2 Click Create on the top right
7.3 Type in the name of the pool
7.4 Select the Health Monitor that you created in the previous step and move it over to Active
7.5 Select Least Connections (member) as the Load Balancing Method
Note: The Least Connections load balancing method determines the member/node with the least connections to pass the service request. Thus, the service requests are evenly distributed among poor members. This method is recommended for supporting long-lived connections.
7.6 Select Node List to see the list of available nodes (click New Node and enter the IP address of each Lync Front End server if you don’t see the from the list)
7.7 Select the IP address of each Lync Front End server
7.8 Enter 4443 as the Service Port and click Add
7.9 Click Finished at the bottom of the screen
8. Create a new Virtual Server
8.1 From the main menu, navigate to Local Traffic – Virtual Servers – Virtual Server List
8.2 Click Create on the top right
8.3 Type in the name of the virtual server
8.4 Select Host as the Destination Type
8.5 Enter the IP address of the Reverse Proxy (i.e. meet.domain.com and Lync External Web Services URL)
8.6 Enter 443 as the Service Port
8.7 From Configuration, select Advanced
8.8 Select the TCP client profile you created in Step 1 as the Protocol Profile (Client)
8.9 Select the SSL client profile you created in Step 4 as the SSL Profile (Client)
8.10 Select the SSL server profile you created in Step 5 as the SSL Profile (Server)
8.11 Select Auto Map for the Source Address Translation
Note: Auto Map is recommended if there are fewer than 64,000 simultaneous users. According to F5's documentation, one IP address is used for 64,000 users.
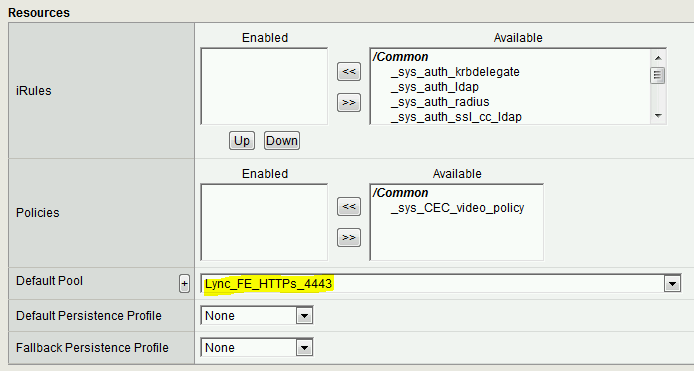
8.12 From the Resources section, select the pool you previously created as the Default Pool
Note: You can leave the Default Persistence Profile as Cookie persistent profile is not required with Lync Server 2013 only deployment. The Cookie persistent profile is required when Lync Server 2010 and Lync Server 2013 are both deployed.
8.13 Click Finished at the bottom of the screen
You are now all set to start testing your Lync External Web Services. Try to access https://meet.domain.com and see if you get this error:
This error was generated by a Lync Front End server. This tells me that the F5 Reverse Proxy is correctly passing the service request to the Lync External Web Services.
Comments
- Anonymous
August 11, 2014
The comment has been removed - Anonymous
October 29, 2015
I modify the program filesMicrosoft Lync Server 2013web componentsjoin launcherint (and ext) blank.html to have and internal or external piece of text, then test to meet.domain.com/.../blank.html and you will get the {internal][external] tag back so you can verify that your traffic is landing properly and the certs are chained up properly. -John http://tsoorad.blogspot.com