Invoke-Adversary – Simulating Adversary Operations
Invoke-Adversary is a PowerShell script that helps you to evaluate security products and monitoring solutions based on how well they detect advanced persistent threats. I was inspired to write this script after seeing APTSimulator excellent tool from Florian Roth.
Update 4/17/2018: The script is temporally removed while I resolve an issue. I will update as soon as I have update. Thanks for your patience and understanding!
Warning
Update 4/14/2018 - In the original script 3rd party tools were downloaded by the script automatically. I believe that the original disclaimers were enough, but decided to change it due to the feedback I got, and now the script ask the users to download the 3rd party tools by themselves - with additional warnings and hash file checking.
This script is provided AS IS without warranty of any kind.
The script should be used for authorized testing and/or educational purposes only with no exceptions. By using the script Windows system's security and stability (including but not limited to: passwords dump, disabling security features, etc.) may be affected so DON'T RUN IT ON PRODUCTION systems.
The script is my own, based on other researchers' public domain knowledge and not related to Microsoft in any form.
"Kill Chain", or What happens during a targeted cybersecurity attack?
Cybersecurity kill chain is a framework developed by Lockheed Martin for identification and prevention of cyber intrusions activity. As attacks may occur in stages, you as defender can put optics and controls to detect or disrupt the entire process.
The stages of the Kill Chain are:
- Reconnaissance – an attacker is probing for a weakness or bad configuration
- Weaponization – an attacker is building a payload that can be delivered to the victim (can be a PDF file or an Office document)
- Delivery- Sending the payload via e-mail, web link or removable media
- Exploit- The payload will execute on the victim's network
- Installation- The payload will download additional remote access tools and install them to maintain persistence
- Command and Control- A channel is created between the victim and the attacker
- Actions- The intended goal is executed (encrypt files, exfiltration of data, etc.)
On top of that model, Mitre, a not-for-profit organization, developed a enhanced model for cyber adversarial behavior, called "Adversarial Tactics, Techniques, and Common Knowledge" (ATT&CK™) Matrix.
Currently, the MITRE ATT&CK™ Matrix provides the most comprehensive framework for adversarial techniques and tactics that enterprises encounter daily.
| Technique | Description |
| Persistence | Techniques for persistent presence on compromised system |
| Privilege Escalation | Techniques for adversary to obtain a higher level of permissions |
| Defense Evasion | Techniques adversary may use to evade detection or avoid other defenses |
| Credential Access | Techniques resulting in access to or control over system, domain, or service credentials |
| Discovery | Techniques that allow the adversary to gain knowledge about the system and internal network |
| Lateral Movement | Techniques that enable an adversary to access and control remote systems on a network |
| Execution | Techniques that result in execution of adversary-controlled code on a local or remote system |
| Collection | Techniques used to identify and gather information |
| Exfiltration | Techniques that result or aid in the adversary removing files and information from a target network |
| Command and Control | Techniques that represents how adversaries communicate with systems under their control within a target network |
Many companies are using Security Information and Event Management (SIEM), Endpoint Protection Platform (EPP) and Endpoint Detection & Response (EDR) products to monitor and protect their environments. What seems to be missing is a tool that can generate a real data that represents real-world targeted attacks.
Invoke-Adversary is a PowerShell script that uses a set of functions to simulate post-compromise adversarial behavior within Windows Enterprise networks.
By using Invoke-Adversary script you can:
- Assess your security monitoring tools and practices
- Evaluate Endpoint detection agents
Setup
Requirements for deploying:
- PowerShell version 3.0 and above
- Windows 7 (some test cases will work only on Windows 10) and above
- Download Invoke-Adversary.ps1 file from https://github.com/MotiBa/Invoke-Adversary/tree/master
Usage
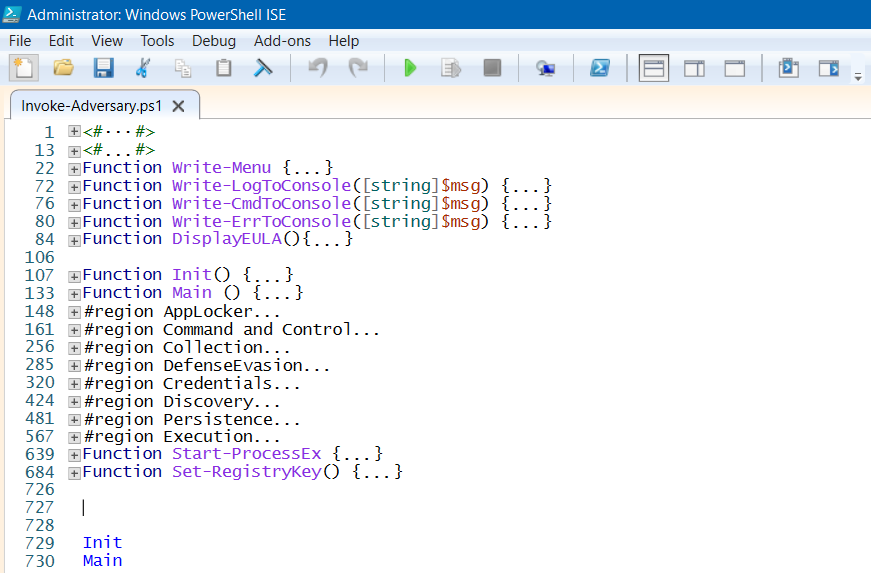
- The simplest way to run the script is to open an elevated (run as Administrator) PowerShell ISE window and press F5.
- The script will start and the first thing you need to do is to read the disclaimer and accept the terms by typing yes
- Now you can select any test case by choosing its number on the menu
- Choose which test you want to run by choosing its number on the menu
Screenshots
What are the tactics
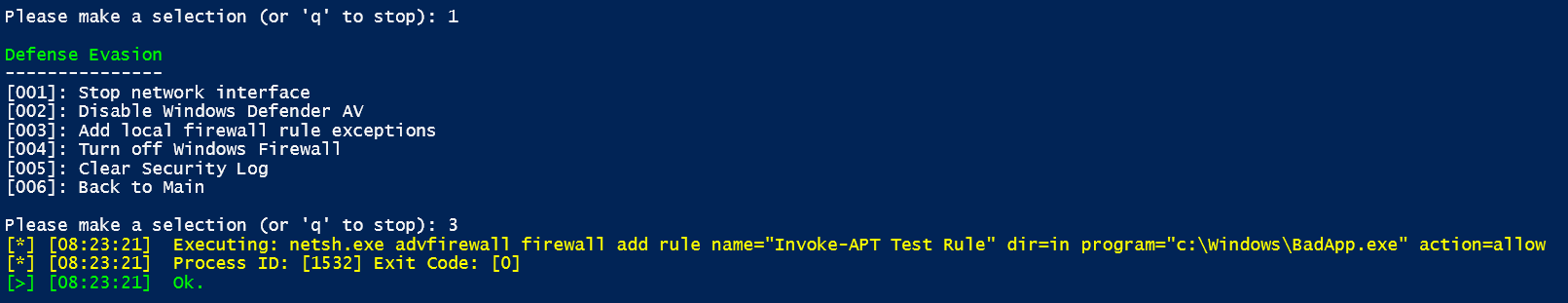
Defense Evasion
- Disable network interface - Disables a network adapter and causes loss of network connectivity
- Disable Windows Defender AV – Turn off real-time protection, scanning all downloaded files and attachments, behavior monitoring, network protection and privacy mode
- Add local firewall rule exceptions – Add fictitious rule "Invoke-APT Test Rule" to Windows Advanced Firewall
- Turn off Windows Firewall – Turn off Windows Advanced Firewall
- Clear Security Log - clears the security log using wevtutil command
Persistence Tactics
- Accessibility Features – "Hijack" sethc.exe with cmd.exe using "Image File Execution Options"
- AppInit DLLs – Adds entry for pserver32.dll under AppInit_DLLs
- Application Shimming – Create registry value under HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{842562ef-8d28-411d-a67d-ab75ef611fe8}.sdb
- Create local user – A new user (user name is: support_388945a0)
- Create local Administrator – A new user created (user name is: Lost_337fde69_81a9) and added to local Administrators group
- Create New Service – new service (WindowsHealth) is created
- Create New Service (Unquoted Path) – same as previous, just with unquoted path
- Registry Run Keys [HKLM] – New run key under HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
- Registry Run Keys [HKCU] - New run key under HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Scheduled tasks - new scheduled task (OfficeUpdaterA) is created
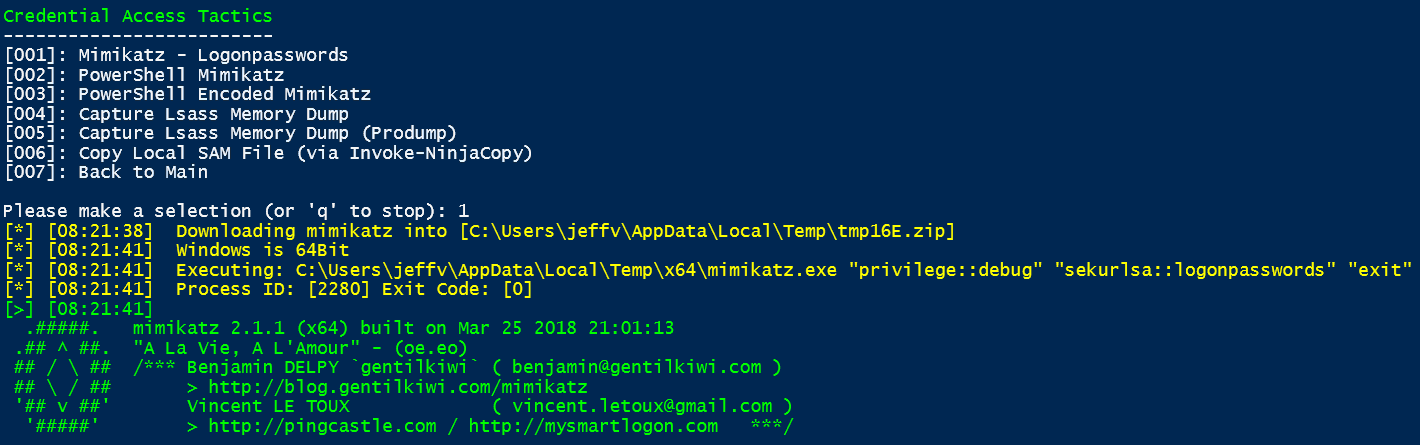
Credential Access
- Mimikatz – Logonpasswords – Download mimikatz to a random file name and execute it with the following arguments "privilege::debug" "sekurlsa::logonpasswords" "exit" (credit: https://twitter.com/gentilkiwi)
- PowerShell Mimikatz – Run Invoke-Mimikatz.ps1 (credit: https://twitter.com/josephbialek?lang=en)
- PowerShell Encoded Mimikatz - Run Invoke-Mimikatz.ps1 with encoded PowerShell command line
- Capture Lsass Memory Dump – Using Windows Error Reporting to capture lsass memory (credit: https://twitter.com/mattifestation)
- Capture Lsass Memory Dump (Prodump) - Download Prodump to a random file and capture lsass memory
- Copy Local SAM File (via Invoke-NinjaCopy) – Run Invoke-NinjaCopy to copy C:\Windows\System32\config\sam file (credit: https://twitter.com/josephbialek?lang=en)
Discovery Tactics
- Account Discovery – running net commands to discover local and domain users and groups
- Network Service Scanning – ports scan (1-1024) on user selected host
- System Owner Discovery – whoami command
- System Time Discovery – Running "net time" and "w32tm.exe /tz" commands
- Service Discovery – List of all services
- Network Connections Discovery – netstat
Command and Control
- Commonly used Ports – Trying to connect to user selected host
- Uncommonly used Ports - Trying to connect to user selected host using uncommon ports (credit: Florian Roth)
- Web Service – Create a new post at pastebin and upload BITS service information
- DNS - Well-Known Blacklisted IP Address – Resolving top 10 malicious IP addresses (credit: Florian Roth)
- Connect - Well-Known Blacklisted IP Address – Connecting to top 10 malicious IP addresses (credit: Florian Roth)
Execution
- PSExec (random file name) – Rename PSEec to random file name and execute it (credit: https://twitter.com/markrussinovich)
- PSExec (Remote) – Running psexec on user selected host
- PowerShell API call – Native API call from PowerShell
- Self Delete (batch file) – self deleting batch file
- WMI Process Execution - use the WMI command-line (WMIC) utility
Collection
- Screen Capture – screen capture (credit: https://www.pdq.com/blog/capturing-screenshots-with-powershell-and-net/)
AppLocker ByPasses
- Regsvr32 - Regsvr32 technique (credit: https://twitter.com/subTee)
Comments
- Anonymous
April 13, 2018
The comment has been removed- Anonymous
April 13, 2018
Oops, fixed! Thank you
- Anonymous
- Anonymous
April 16, 2018
GreatThe link to your Github project return a 404 not found- Anonymous
April 17, 2018
Hi, Please see the update I've added to the blog
- Anonymous