How to easily decode the userCertificate or caCertificate attribute in Active Directory (with only the tools built into Windows)
How many times have you needed to manipulate a certificate attribute in AD and been confronted with something that looks like this:
You know that you want to delete one of the certs, but which one is the one you want to delete? Or the one you want to keep?
The first time I ever had to deal with this was with a customer who had trouble with smartcard logon. They had 8 certificates in their NTAuth store and they only needed 2. I reached out to one of my colleagues on how to deal with this. She said that those certificates are too difficult to parse in AD. She added that the easiest way was to delete all the certificates from the store and just install the 2 we wanted. I figured there had to be an easier way, but did it just to get smartcard login working that day.
Later I ran into it again with a computer account which needed to have some old published certificates deleted from its object in AD. This time I vowed to find a better way and I did.
Clearly these are hexadecimal representations of the cert, but is the resulting output of the conversion readable? Besides, how do you convert without some special tools or going out to the internet?
It turns out that all you need is built into Windows.
First of all, let’s grab the hex. Edit a certificate and right-click in the attribute and Select All:

Now paste that into Notepad and save it as a file. I’ll call mine cert.hex.
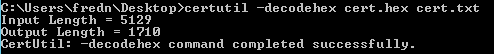
Next, run certutil –decodehex cert.hex cert.txt (because the resulting file will be text – well, at least some of it will be readable)
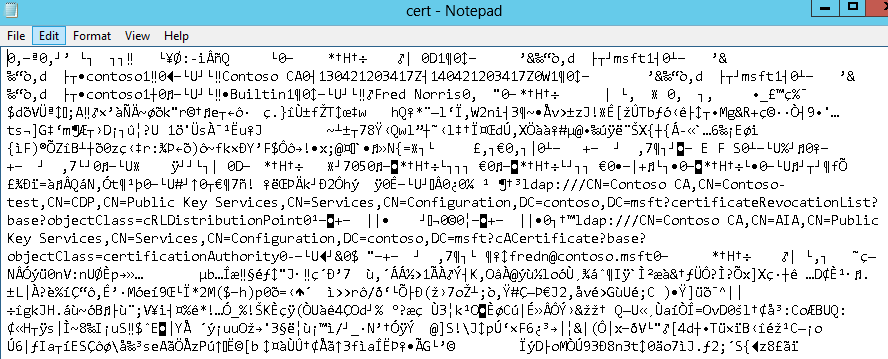
Open the resulting file in notepad. You should see some interesting items that are readable.
Specifically, you can read the Issuing CA, Subject, issued and expiration dates and times. If you look around you’ll see all sorts of other goodies that might meet your needs for ruling out or in the certificate.
The one item I’d like to also find is the certificate template. If anybody knows an easy way to identify this from the output, please share!
P. S. This also should work for the userSMIMECertificate attribute.
Comments
- Anonymous
January 30, 2014
What about just naming the output-file with a cer-extension...? And then just double-clicking it. - Anonymous
August 26, 2014
saving the output of decodehex as a .cer file works great - Anonymous
October 30, 2015
Probably can work with this via PowerShell: http://powershell.com/cs/blogs/tips/archive/2014/10/29/reading-in-pfx-certificate.aspx - Anonymous
November 11, 2015
Note that a .cer file would NOT result in a valid file when decoding the userSMIMEcertificate attribute!