| Installation Account |
miminstall |
| NOTE |
This is a recommended account, not a required account to make FIM/MIM work. |
The installation of the Identity Management software requires elevated privileges and special permissions on SQL Server. Many times, a standard user and/or a service account does not have all of the necessary permissions to execute an installation of the Microsoft Identity Management product and/or update. This is why we feel it is a good idea to have an installation account that can be utilized for the sole purpose of Product Installation, Service Pack Installation and/or Hotfix (Cumulative Update) Installation. Once the installation is completed, the recommendation would be to disable the account until you have another update installation to execute.This account will need the following permissions for the purpose of the installation.
| NOTE |
It is important to note that these permissions are required for the account executing the installation for the purpose of installation. Once the installation is complete, then these permissions can be removed if they are not needed for the account that is executing the installation. This is important to note in case you choose not to have an actual installation account, but to use a service account and/or another user account. |
- SQL SERVER: sysAdmin
- The account executing the installation must have sysAdmin permissions on the Microsoft SQL Server that is hosting the FIMSynchronizationService and FIMService Databases
- sysAdmin permissions are needed for several different creation and/or alter job that happen during the installation.
- Domain Admin Permissions
- The account executing the installation should have Domain Administrator permissions long enough for the installation of the product and/or update.
- By adding the account to the Domain Administrator, the account will most likely become a part of the Local Administrators group.
- SharePoint Permissions
| NOTE |
The SharePoint permissions are normally set during the installation process of SharePoint and is normally the account logged in executing the installation. |
- SharePoint Farm Administrator
- SharePoint Site Collection Administrator
Reasons to utilize an installation account
- It will always exist, even if the physical person executing the Identity Management Installation ends up leaving the company, then the installation account still resides.
- Installation account can have the elevated privileges where other accounts will not need to be granted this type access, even if it is for a short period of time.
It is not recommended to:
- Use Service Accounts to execute the installation, because the account executing the installation is required to have elevated privileges and permissions.
- Use Service Accounts because the installation of the Service and Portal adds it to the Administrators Set in the Portal.
|
|
|
|
| SharePoint Configuration Account |
spDBAccount |
- Domain User
- This account is specified/asked for during the SharePoint Configuration Wizard
- In SharePoint, this account is the SharePoint Farm Account which is utilized to talk to the SharePoint Databases.
|
|
|
|
| SharePoint Application Pool Account |
mimAppPool |
- Domain User
- This account is used during the SharePoint Installation and is the Application Pool Account for SharePoint and for the Identity Manager Product

- This account does require ServicePrincipalNames (SPN) for the purpose of kerberos authentication. The SPN will have the prefix of HTTP/
| SharePoint Application Pool - SPN Information |
If the address that the clients use to contact the FIM Portal is not the same as the server address, you have to establish an SPN for HTTP. That is, if you use a CNAME resource record in DNS, have a SharePoint farm, or use NLB, this address must be registered or Internet Explorer cannot use the Kerberos protocol when it contacts the portal. Run the following command:
- On a domain controller where the FIM Solution is installed, open an administrative command-prompt by right clicking on command prompt and selecting Run As Administrator
- Type:setspn -S HTTP/<FIMPortalAlias> <Domain Name>\<SharePoint Service Account>( e.g. setspn -s HTTP/myfimportalmachine DOMAINA\svcSharePointService )
- <FIMPortalAlias>: This is the address that is used to navigate to the FIM Portal ( e.g.http://myfimportalserver/ )
- <Domain Name>: NETBIOS name of the domain that the FIM Solution has been installed
- <SharePoint Service Account>: sAMAccountName of the SharePoint Service Account ( e.g. The account specified on the SharePoint - 80 Application Pool in IIS.
| NOTE |
If the account running the SharePoint Application Pool is Network Service, then the SharePoint Service Account should be the computer account that SharePoint Services and the FIM Portal are running. |
If, in your solution, you are using a Load Balancer, DNS, Fully Qualified Domain Names (FQDN), you will need to ensure that you have an SPN for each of them.
| SPN EXAMPLES |
| HTTP/myfimservicemachineHTTP/myfimservicemachine.contoso.comHTTP/myfimserviceDNSAlias |
ADDITIONAL INFORMATION ON SPNS
| NOTE |
This page will be the same for MIM 2016 |
|
- This account must be trusted for Kerberos delegation, which is done on the Active Directory account on the Delegation Tab. In the below snapshot, we utilize the 2nd radio button. In a more locked down, secure environment one might choose to use the 3rd radio button. However, we do not recommend doing this, unless you are familiar with Kerberos Delegation settings.

|
|
|
|
| Synchronization Service Account |
mimsync |
- Domain User
- This is the account that you will see on the Forefront Identity Manager Synchronization Service item in Services MMC.
- This account is utilized to communicate between the Application Client (Synchronization Service Manager) and the backend SQL Server Database called FIMSynchronizationService
- This account should not be used for:
- Installation purposes
- A Management Agent Account
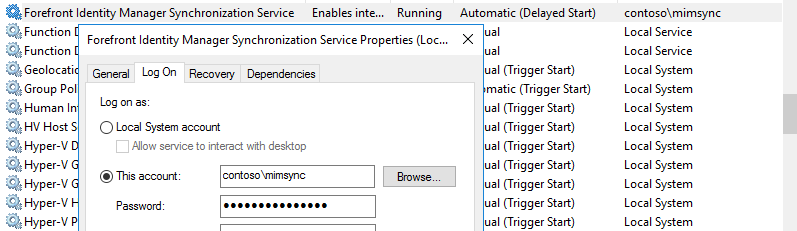
- Providing a bit more security to the FIM/MIM Service Account, add the FIM/MIM Service Account to the following Local Security Policies
- Deny Logon as Batch Job
- Deny Logon Locally
- Deny Access to this computer from the network
|
|
|
|
| Service Account |
mimservice |
- Domain User
- This is the account that is referenced on the Forefront Identity Manager Service item on the Services MMC
- The FIM/MIM Service is the account that helps connect the Synchronization Service to the FIMService Database for request processing
- This should be an email enabled service account, especially if you are going to utilize approvals which executes emails sent from the FIMService account
- This account should not be used for:
- Installation purposes
- A Management Agent Account
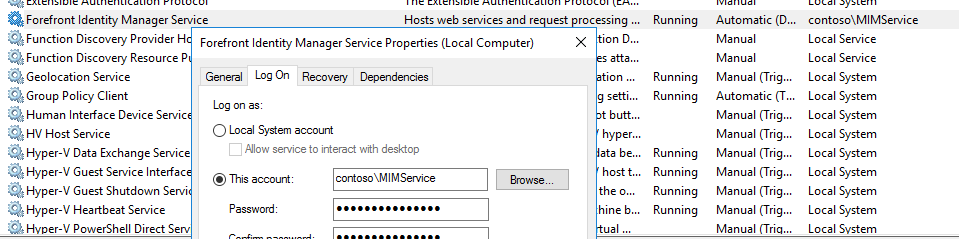
- This account does require ServicePrincipalNames (SPN) for the purpose of kerberos authentication. The SPN will have the prefix of HTTP/
| FIM/MIM Service - SPN Information |
If the address that the clients use to contact the FIM Portal is not the same as the server address, you have to establish an SPN for HTTP. That is, if you use a CNAME resource record in DNS, have a SharePoint farm, or use NLB, this address must be registered or Internet Explorer cannot use the Kerberos protocol when it contacts the portal. Run the following command:
- On a domain controller where the FIM Solution is installed, open an administrative command-prompt by right clicking on command prompt and selecting Run As Administrator
- Type:setspn -S HTTP/<FIMPortalAlias> <Domain Name>\<SharePoint Service Account>( e.g. setspn -s HTTP/myfimportalmachine DOMAINA\svcSharePointService )
- <FIMPortalAlias>: This is the address that is used to navigate to the FIM Portal ( e.g.http://myfimportalserver/ )
- <Domain Name>: NETBIOS name of the domain that the FIM Solution has been installed
- <SharePoint Service Account>: sAMAccountName of the SharePoint Service Account ( e.g. The account specified on the SharePoint - 80 Application Pool in IIS.
| NOTE |
If the account running the SharePoint Application Pool is Network Service, then the SharePoint Service Account should be the computer account that SharePoint Services and the FIM Portal are running. |
If, in your solution, you are using a Load Balancer, DNS, Fully Qualified Domain Names (FQDN), you will need to ensure that you have an SPN for each of them.
| SPN EXAMPLES |
| FIMService/myfimservicemachineFIMService/myfimservicemachine.contoso.comFIMService/myfimserviceDNSAlias |
ADDITIONAL INFORMATION ON SPNS
| NOTE |
This page will be the same for MIM 2016 |
|
- This account must be trusted for Kerberos delegation, which is done on the Active Directory account on the Delegation Tab. In the below snapshot, we utilize the 2nd radio button. In a more locked down, secure environment one might choose to use the 3rd radio button. However, we do not recommend doing this, unless you are familiar with Kerberos Delegation settings.
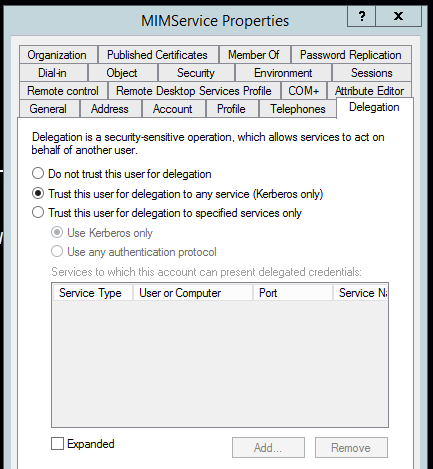
- Providing a bit more security to the FIM/MIM Service Account, add the FIM/MIM Service Account to the following Local Security Policies
- Deny Logon as Batch Job
- Deny Logon Locally
- Deny Access to this computer from the network
| NOTE |
If you are using Exchange Online, then do not have the FIMService in the "Deny Access to this computer from the network" |
- In a Privileged Access Management (PAM) Scenario
- The MIM Service Account must have the ability to create shadow principals or groups (depending on the mode PAM is running in)
|
|
|
|
| Self-Service Password Reset / Registration |
mimsspr |
- Domain User Account
- This account should be exclusive to the Self-Service Password Reset / Registration service
- This account is represented in the IIS Manager under the Application Pool
- This account does require ServicePrincipalNames (SPN) for the purpose of kerberos authentication. The SPN will have the prefix of HTTP/
| FIM/MIM Service - SPN Information |
If the address that the clients use to contact the FIM Portal is not the same as the server address, you have to establish an SPN for HTTP. That is, if you use a CNAME resource record in DNS, have a SharePoint farm, or use NLB, this address must be registered or Internet Explorer cannot use the Kerberos protocol when it contacts the portal. Run the following command:
- On a domain controller where the FIM Solution is installed, open an administrative command-prompt by right clicking on command prompt and selecting Run As Administrator
- Type:setspn -S HTTP/<FIMPortalAlias> <Domain Name>\<SharePoint Service Account>( e.g. setspn -s HTTP/myfimportalmachine DOMAINA\svcSharePointService )
- <FIMPortalAlias>: This is the address that is used to navigate to the FIM Portal ( e.g.http://myfimportalserver/ )
- <Domain Name>: NETBIOS name of the domain that the FIM Solution has been installed
- <SharePoint Service Account>: sAMAccountName of the SharePoint Service Account ( e.g. The account specified on the SharePoint - 80 Application Pool in IIS.
| NOTE |
If the account running the SharePoint Application Pool is Network Service, then the SharePoint Service Account should be the computer account that SharePoint Services and the FIM Portal are running. |
If, in your solution, you are using a Load Balancer, DNS, Fully Qualified Domain Names (FQDN), you will need to ensure that you have an SPN for each of them.
| SPN EXAMPLES |
| HTTP/myfimpasswordregistrationHTTP/myfimpasswordregistration.contoso.comHTTP/myfimpasswordregistrationDNSAlias |
ADDITIONAL INFORMATION ON SPNS
| NOTE |
This page will be the same for MIM 2016 |
|
- This account must be trusted for Kerberos delegation, which is done on the Active Directory account on the Delegation Tab. In the below snapshot, we utilize the 2nd radio button. In a more locked down, secure environment one might choose to use the 3rd radio button. However, we do not recommend doing this, unless you are familiar with Kerberos Delegation settings.
 |
|
|
|
| FIM Service Management Agent Account |
mimma |
- Domain User
- This account should be exclusive to the FIM Service Management Agent
- This account should not be a
- Local Administrator
- The Synchronization Service Account
- The FIM Service Account
- This account is utilized to communicate with the FIMService Database
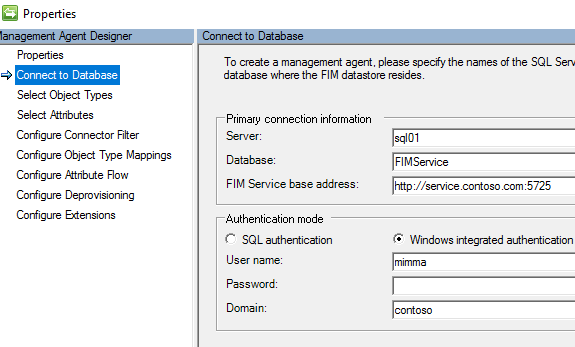
- This account should match the account that you specified during the Service and Portal Installation, which adds it to the Windows Registry under the key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\FIMService.
 LOCAL SECURITY POLICY LOCAL SECURITY POLICY
- The FIM Management Agent Account cannot have the "Deny access to this computer from the network"
INFORMATION / LINKS
|





 LOCAL SECURITY POLICY
LOCAL SECURITY POLICY
