New features recently implemented in HTTPREPLAY
I've recently implemented a couple of new features in HTTPREPLAY in order to ease report generation and troubleshooting:
- Ability to generate HTTPREPLAY report without starting "replay proxy"
- Minor fixes including STRACE log filename being now part of HTTPREPLAY report filename
- Conversion of HTTP or socket related data to PCAP format in order to take advantage of Wireshark parsers
Before digging a little bit more into this last feature, let me summarize how to open STRACE logs :
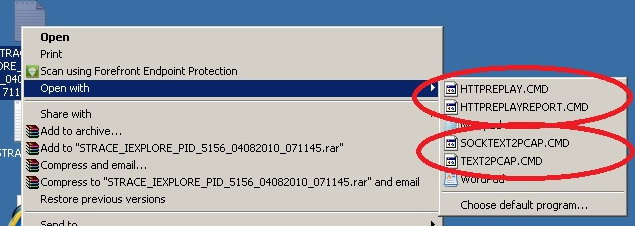
As you can see, outside the possibility of using NOTEPAD, there are now 4 different ways to parse/open STRACE logs in a readable manner:
- use HTTPREPLAY.CMD to generate HTTPREPLAY report on the user's desktop and start "replay proxy"
- use HTTPREPLAYREPORT to generate HTTPREPLAY report without starting "replay proxy"
- use TEXT2PCAP to convert STRACE HTTP related data (sent in clear or encrypted inside SSL session(s)) to PCAP file
- use SOCKTEXT2PCAP to convert STRACE TCP related data (sent using socket APIs) to PCAP file
The PCAP conversion is pretty helpful to troubleshoot authentication issues. Let's say that we are troubleshooting a Kerberos issue over SSL and we do have a STRACE log. Generating a HTTP report would allow us to see that Kerberos is used by looking at the request length. However, the Authorization blob remains opaque:

Now, let's convert the STRACE log to a PCAP file using TEXT2PCAP.CMD. The produced HTTPREPLAY.PCAP file will be automatically created on the desktop and opened:


We now clearly see the Kerberos ticket being sent, the SPN used…etc
Converting the same STRACE log using SOCKTEXT2PCAP.CMD allows us to see TCP related data. Since the STRACE log was created while connecting using HTTPS, we can see the SSL/TLS related data like the server's certificate …etc :


There are some limitations regarding the PCAP conversion mainly due to TEXT2PCAP.EXE limitations (TEXT2PCAP is the Wireshark tool used for the PCAP conversion) :
- source and destination addresses are faked addresses and sender/receiver information is lost
- port number information is lost
The attached ZIP file contains both STRACE and HTTPREPLAY as of 10/12/2011.
Happy tracing & analysis!
Emmanuel Boersma