Multiple MFA Prompts connecting to Office 365?
Customers using Active Directory Federation Services (AD FS) to authenticate users accessing Office 365, could be challenged by multiple prompts for Multi-Factor Authentication (MFA).
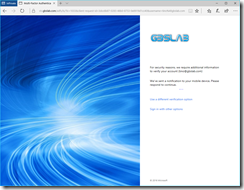
Here is an example of a user trying to access the Office 365 Portal at https://portal.office.com. First, the user gets directed to the Security Token Service (STS) the organization has configured. (In this case, it’s AD FS running on Windows Server 2016.) After authenticating using a username and password (since the user is accessing Office 365 from the ‘extranet’) the users gets a prompt for MFA:
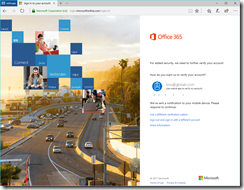
After successfully verifying the request, the user is redirected back to https://login.microsoftonline.com, the STS for Office 365. For Office 365, the customer has configured MFA to be required, and the STS for Office 365 requests MFA once more;
This can happen when (any form of) MFA is required on the “Microsoft Office 365 Identity Platform” Relying Party in AD FS, and it’s also required to access Office 365 (using conditional access rules or simply because the user is enabled for Azure MFA).
The cause of the double MFA prompt is that the AD FS farm, while issuing the token to the “Microsoft Office 365 Identity Platform”, did not ‘inform’ the recipient of the token about the fact that the user already did MFA. Part of the token that is sent from the AD FS farm to the “Microsoft Office 365 Identity Platform” is the way the user authenticated. It’s passed as a claim within the token. Whether the user did MFA or not, can be passed in another claim. This claim is not sent by default.
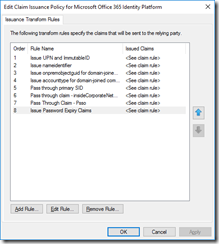
We can easily change this behavior by modifying the Claim Issuance Policy for the “Microsoft Office 365 Identity Platform” Relying Parting in AD FS.
In the AD FS Management Console, navigate to “Relying Party Trusts”, select the “Microsoft Office 365 Identity Platform” Relying Party Trust and click, on the right side, on “Edit Claim Issuance Policy… ”.
In the “Edit Claims Issuance Policy for Microsoft Office 365 Identity Platform” screen, click on the “Add Rule… ” button.
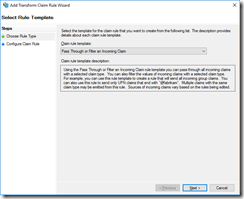
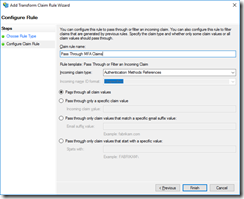
Under “Claim rule template: ”, select “Pass Through or Filter and Incoming Claim”.
Click “Next > ” to continue,
In the next screen, give the rule a friendly name, for example “Pass Through MFA Claims”, and next to “Incoming claim type: ” select “Authentication Methods References”.
Click “Finish” to add the rule.
After that, try it again!
The only MFA prompt the user will get is from AD FS, and no longer from the Office 365 STS! Should a user in your tenant authenticate with a non-federated account, so an account which is not ‘served’ by AD FS, the user will be challenged for MFA by the Office 365 STS.
(And this also works for any other applications that you have registered with your Azure Active Directory Tenant.)