Protecting the pre-OS environment with UEFI
There have been some comments about how Microsoft implemented secure boot and unfortunately these seemed to synthesize scenarios that are not the case so we are going to use this post as a chance to further describe how UEFI enables secure boot and the options available to PC manufacturers. The most important thing to understand is that we are introducing capabilities that provide a no-compromise approach to security to customers that seek this out while at the same time full and complete control over the PC continues to be available. Tony Mangefeste on our Ecosystem team authored this post. --Steven
Quick summary
- UEFI allows firmware to implement a security policy
- Secure boot is a UEFI protocol not a Windows 8 feature
- UEFI secure boot is part of Windows 8 secured boot architecture
- Windows 8 utilizes secure boot to ensure that the pre-OS environment is secure
- Secure boot doesn’t “lock out” operating system loaders, but is a policy that allows firmware to validate authenticity of components
- OEMs have the ability to customize their firmware to meet the needs of their customers by customizing the level of certificate and policy management on their platform
- Microsoft does not mandate or control the settings on PC firmware that control or enable secured boot from any operating system other than Windows
The big picture – no compromises on security
The UEFI secure boot protocol is the foundation of an architecturally neutral approach to platform and firmware security. Based on the Public Key Infrastructure (PKI) process to validate firmware images before they are allowed to execute, secure boot helps reduce the risk of boot loader attacks. Microsoft relies on this protocol in Windows 8 to improve platform security for our customers.
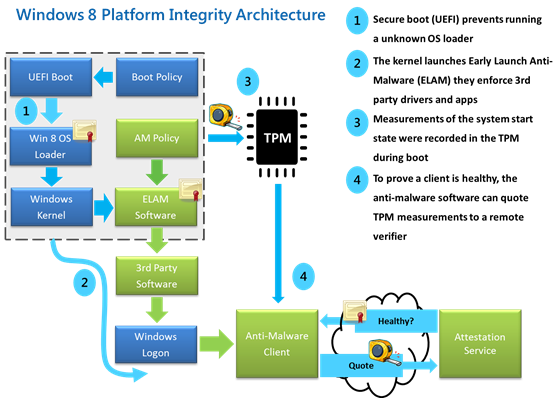
Figure 1 – Platform integrity architecture
Microsoft is working with our partners to ensure that secured boot delivers a great security experience for our customers. Microsoft supports OEMs having the flexibility to decide who manages security certificates and how to allow customers to import and manage those certificates, and manage secure boot. We believe it is important to support this flexibility to the OEMs and to allow our customers to decide how they want to manage their systems.
For Windows customers, Microsoft is using the Windows Certification program to ensure that systems shipping with Windows 8 have secure boot enabled by default, that firmware not allow programmatic control of secure boot (to prevent malware from disabling security policies in firmware), and that OEMs prevent unauthorized attempts at updating firmware that could compromise system integrity.
Most of these policies are not new to UEFI firmware, and most PCs today carry some form of firmware validation. Even the existing legacy support, such as BIOS password, is a form of secure boot that has been under OEM and end-user control for years. However, with secure boot & UEFI, the industry and Microsoft are raising the bar to create greater system integrity and health, and to provide customers with a strong level of protection against a growing class of threat.
What is UEFI?
UEFI (Unified Extensible Firmware Interface) is managed through the UEFI forum, a collection of chipset, hardware, system, firmware, and operating system vendors. The forum maintains specifications, test tools, and reference implementations that are used across many UEFI PCs. Microsoft is a board member of this forum, and the forum is open to any individual or company to join free of cost.
UEFI defines the next generation firmware interface for your personal computer. The Basic Input and Output System (BIOS) firmware, originally written in assembly and using software interrupts for I/O, has defined the PC ecosystem since its inception – but changes in the computing landscape have paved the way for a “modern firmware” definition to usher in the next generation of tablets and devices.
The intent of UEFI is to define a standard way for the operating system to communicate with the platform firmware during the boot process. Before UEFI, the primary mechanism to communicate with hardware during the boot process was software interrupts. Modern PCs are capable of performing faster, more efficient block I/O between hardware and software, and UEFI allows designs to utilize the full potential of their hardware.
UEFI allows for modular firmware design that enables hardware and system designers a greater flexibility in designing firmware for the more demanding modern computing environments. Whereas I/O was limited by software interrupts, UEFI promotes the concept of event-based, architecture-neutral coding standards.
What is secure boot?
UEFI has a firmware validation process, called secure boot, which is defined in Chapter 27 of the UEFI 2.3.1 specification. Secure boot defines how platform firmware manages security certificates, validation of firmware, and a definition of the interface (protocol) between firmware and the operating system.
Microsoft’s platform integrity architecture creates a root of trust with platform firmware using UEFI secure boot and certificates stored in firmware. A growing trend in the evolution of malware exploits is targeting the boot path as a preferred attack vector. This class of attack has been difficult to guard against, since antimalware products can be disabled by malicious software that prevents them from loading entirely. With Windows 8’s secured boot architecture and its establishment of a root of trust, the customer is protected from malicious code executing in the boot path by ensuring that only signed, certified “known good” code and boot loaders can execute before the operating system itself loads.
In most PCs today, the pre-operating system environment is vulnerable to attacks by redirecting the boot loader handoff to possible malicious loaders. These loaders would remain undetected to operating system security measures and antimalware software.

Figure 2 - Legacy BIOS boot path
Windows 8 addresses this vulnerability with UEFI secure boot, and using policy present in firmware along with certificates to ensure that only properly signed and authenticated components are allowed to execute.
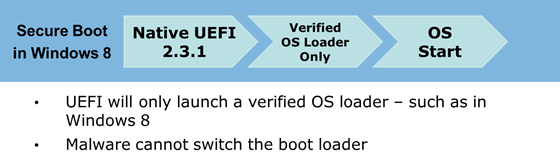
Figure 3 - Secure boot path with UEFI
Secure boot is only a part of the Windows 8 Platform Integrity story. Along with UEFI, Microsoft’s strategy is a holistic approach to other available hardware to further enhance the security of the platform.
Background: how does it work?
Powering on a PC starts the process of executing code that configures the processor, memory, and hardware peripherals in preparation for the operating system to execute. This process is consistent across all platforms, regardless of underlying silicon architectures (x86, ARM, etc.).
Shortly after the system is powered on, and before handoff to the OS loader occurs, the firmware will check the signature of firmware code that exists on hardware peripherals such as network cards, storage devices, or video cards. This device code, called Option ROMs, will continue the process of configuration by ensuring that the peripheral is prepared for handoff to the operating system.
During this part of the boot process firmware will check for an embedded signature inside of the firmware module, much like an application, and if that signature matches against a database of signatures in firmware, then that module is allowed to execute. These signatures are stored in databases in firmware. These databases are the “Allowed” and “Disallowed” lists that determine if the booting process can continue.
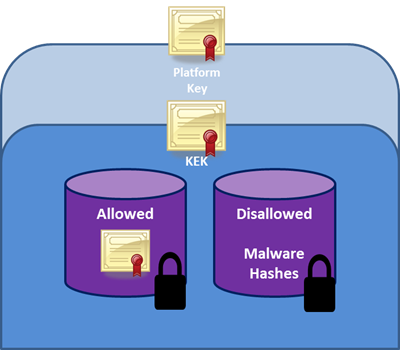
Figure 4 - Security databases for certificates
This figure represents the hierarchy of signatures and keys in a system with secure boot. The platform is secured through a platform key that the OEM installs in firmware during manufacturing. This is the process used today on most shipping systems, regardless of whether they are based on UEFI, or legacy BIOS. (Applications like firmware update utilities will use the platform key to protect the firmware image.) Other keys are used by secure boot to protect access to databases that store keys to allow or disallow execution of firmware.
The Allowed database contains keys that represent trusted firmware components and, more importantly, operating system loaders. Another database contains hashes of malware and firmware, and blocks execution of those malware components. The strength of these policies is based on signing firmware using Authenticode and Public Key Infrastructure (PKI). PKI is a well-established process for creating, managing, and revoking certificates that establish trust during information exchange. PKI is at the core of the security model for secure boot.
What is required for secure boot?
Secure boot requires firmware that meets or exceeds UEFI revision 2.3.1. The UEFI forum ratified the latest revision which updated the policies of Chapter 27 to improve upon the existing secure boot protocol to include time-authenticated variables, stronger keys for encryption, and clarification on how those certificates are stored.
The feature would be transparent to the consumer purchasing a PC. The benefit is that their system has an added measure of reliability from bootkit and rootkit attacks that target system vulnerabilities before the operating system itself even loads, as described above.
Who is in control?
At the end of the day, the customer is in control of their PC. Microsoft’s philosophy is to provide customers with the best experience first, and allow them to make decisions themselves. We work with our OEM ecosystem to provide customers with this flexibility. The security that UEFI has to offer with secure boot means that most customers will have their systems protected against boot loader attacks. For the enthusiast who wants to run older operating systems, the option is there to allow you to make that decision.
A demonstration of this control is found in the Samsung tablet with Windows 8 Developer Preview that was offered to //BUILD/ participants. In the screenshot below you will notice that we designed the firmware to allow the customer to disable secure boot. However, doing so comes at your own risk. OEMs are free to choose how to enable this support and can further customize the parameters as described above in an effort to deliver unique value propositions to their customers. Windows merely did work to provide great OS support for a scenario we believe many will find valuable across consumers and enterprise customers.
![Figure 5 - Samsung PC secured boot setting Image of a console with options for TPM Configuration: Enable virtualization [enabled], CSM Support [Disabled], Attempt Secure Boot [Enabled], Display Rev. Info - Intel UEFI...](https://msdntnarchive.z22.web.core.windows.net/media/MSDNBlogsFS/prod.evol.blogs.msdn.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/01/29/43/metablogapi/0624.Figure-5---Samsung-PC-secured-boot-setting_thumb_02016A69.jpg)
Figure 5 - Samsung PC secure boot setting
Tony Mangefeste
Ecosystem
Comments
Anonymous
September 22, 2011
Que bomAnonymous
September 22, 2011
Any OEM that won't let me turn this off or load my own certs won't get any business from me.Anonymous
September 22, 2011
Well done.Anonymous
September 22, 2011
Great to see the prompt and responsive Windows team keeping an eye on the blogosphere and current news. Keep working hard and pushing at Windows... Lets see Windows 8 in top quality before Ipad 3. Have your team work nights and weekends. :)Anonymous
September 22, 2011
@Steven, Do you have any plans to directly sell the Samsung PC to non //Build/ attendees like me. I would not mind paying to get my hands on it. Wouldnt it be actually beneficial to MS to do that?Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
@Trevor Sullivan thank you! @kevin -- exactly! We enable the technology so you can have this choice. @DotNetGeekAtLive -- sorry but we're all out. As many have noted, the Samsung Series 7 will have many of the same characteristics (but not all), and also include Samsung support for the hardware and a retail system load of Windows 7.Anonymous
September 22, 2011
@Steven, Can you elaborate on the boot requirements for ARM a bit? Will it require UEFI, will it be compatible with the built-on BIOS's, will it require ACPI, etc...? Basically, what I want to know, is there going to be any compatibility with existing devices, for the more technologically-inclined folk out there, or is it going to be strictly on new ARM devices?Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
Hahaha. Of course we knew that linux could dual boot with Windows. The linux fanbois just weren't getting enough attention with all of this recent positive Windows news. This is the year of the linux desktop, after all. Or wait... was that supposed to be next year?Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
How is malware prevented from just disabling secure boot?Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
Steven, Microsoft plans to have computers with the Microsoft brand?Anonymous
September 22, 2011
"Microsoft is using the Windows Certification program to ensure that systems shipping with Windows 8 have secure boot enabled by default, that firmware not allow programmatic control of secure boot (to prevent malware from disabling security policies in firmware), and that OEMs prevent unauthorized attempts at updating firmware that could compromise system integrity." Excellent. @Steven Sinofsky: "How secure boot works with any other operating systems is obviously a question for those OS products :-)" Agreed. It is up to other OS vendors to get their acts together regarding secure boot, and if this causes conflicts with their licensing models, that's their problem. The onus is not on Microsoft to compromise system security to be 'fair' to the GPL, or whatever. Other than in the diagram, the post does not contain the string 'TPM'. You need a TPM chip on your UEFI motherboard to run secure boot. TPM chips are on a minority of motherboards, even UEFI motherboards. The post is somewhat misleading in not mentioning all this explicitly. This is otherwise a quality post, except for the section 'Background: how does it work?'. The relationship between hardware platforms (x86,x64,ARM), firmware types (BIOS, UEFI), TPM vs. non-TPM systems, platform and osloader keys, is not quite clearly explained. Could you possibly add a truth-table to the end of the document that indicates what systems support what features and what hard/firmware is required per case? "The feature would be transparent to the consumer purchasing a PC." When Internet Explorer connects to a secure website (using https), is that "transparent to the consumer [using the] PC"? Windows boot menu should indicate the PKI status of each boot entry to the consumer (new term for 'user'?). Why hide the feature completely?Anonymous
September 22, 2011
There seems to be some concern that it will no longer be possible to load alternate OSes on Windows 8 computers. Just to clarify, will it be possible to install other operating systems such as Linux onto pre-built Windows 8 computers?Anonymous
September 22, 2011
@mt325000 the entire blog post was about clairying that :P pre-built win8 computers will only get the shiny sticker if they SUPPORT the new security feature. The new security feature will probably stop you installing many flavours of linux WHEN IT IS ENABLED. Whether or not you can disable this new feature is up to the PC manufacturer, but "probably" is a likely answerAnonymous
September 22, 2011
I suspected as much, but Sinofsky didn't specifically state anything about installing alternate operating systems. Besides, many system builders, such as Dell, only include the most basic BIOS/UEFI features. What if every major OEM decides to not let users disable the UEFI security features?Anonymous
September 22, 2011
mt325000, assuming the OEM has the option to disable secure boot then of course that will be possible right now. If the OEM does NOT provide that option but provides the option to disable UEFI completely then you can also do that to install Linux. Other wise no you would NOT be able to install Linux, in its current forum. But major Linux Distros could of course get their own certs and have OEMs add them to the allow list.Anonymous
September 22, 2011
At times people want to rebuild their OS from scratch..do a clean install and start installing apps and then restore data. I wonder how a clean rebuild will put TPM to believe that this OS is legitimateAnonymous
September 22, 2011
Thank you for clarifying this. The speculation about how it was going to work was getting a bit out of hand. Provided the OEMs don't do anything stupid, it sounds like all of this is sensible. Secure boot by default, but you can turn it off if you want to. Everyone should be happy with that.Anonymous
September 22, 2011
@Leo Davidson I think I have to agree with that.Anonymous
September 22, 2011
@Mohit: Good question. This should definitely be explained asap. What happens in the case of the retail SKUs? Can the consumer install the required certs into the UEFI-PKI, assuming they have a TPM?Anonymous
September 22, 2011
@Steven, how 'bout some ARM lovin'? Or at least a note that you heard my message?Anonymous
September 22, 2011
As long as the Windows 8 boot loader is going to restart to boot into another OS thereby delaying its boot, I will be replacing the new boot loader anyways with one that doesn't delay loading of other OSes. Why is the Windows 8 boot shell (bootim.exe) not capable of booting at least older Windows OSes without rebooting?Anonymous
September 22, 2011
I notice that in Windows 8, the F8 experience has been reworked. You have to hit Shift-F8 instead. Moreover, some BIOSes have an issue where Shift is not sent to Windows this early. Also, F8 worked with the Vista/Windows 7 bootloader, but it didn't work reliably in cases where the boot delay was set to less than 1-2 seconds (at least not on the PCs I used). The official key to show the boot screen/F8 options was Space bar which worked reliably or all cases. (blogs.msdn.com/.../the-space-bar-is-the-new-f8-when-it-comes-to-vista-and-server-2008-boot-options.aspx). Now not only is pressing Shift+F8 together at just the right time before the OS begins to boot not easy but Space or Shift+Space no longer works. Can't it be a single keystroke that works reliably even if the boot delay is set to 0 seconds and doesn't change constantly?Anonymous
September 22, 2011
@Drewfus, @Mohit: TPM is actually NOT required for secure boot. There are two separate features: secure boot and measured boot. The purpose of secure boot is to block unsigned code from the boot process unless there's an unforgable user action to allow it (e.g., flip a switch in the firmware settings). While the OS won't technically require secure boot, most systems that are designed for Windows 8 will ship with this feature enabled. Measured boot takes things a step further: using a TPM, the feature provides a thumbprint of all code that executed during boot. This thumbprint could be used to assure antivirus and other computers (e.g., a remote file share containing information confidential to your business) that the system has not been tampered with. Windows 8 will not require measured boot or a TPM. While a TPM is useful for businesses, most consumer systems will probably continue to ship without a TPM (to reduce costs). Measured boot isn't discussed in this article (except, confusingly, the first diagram), but you can learn more about it by watching this //BUILD video: channel9.msdn.com/.../HW-457T .Anonymous
September 22, 2011
My question is: what will happen with the Macs? All Intel-based Macs have EFI, but I don't know if Windows 8 will be able to be installed in a Mac without emulating a BIOS (Apple's Boot Camp).Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
This is a great read, but I can't almost guarantee this isn't going to stop a lot of the rumours. You need to speak in specifics. Show exactly what the case is for Linux, what scenarios if any can't you change the machine to boot to Linux.Anonymous
September 22, 2011
@Jeffrey Tippet [MSFT]: Thanks for making that clear. IMO the post should be updated to include info about this secure boot - measured boot distinction, especially considering the subject matter has aroused some controversy. I will view the Channel9 video asap...Anonymous
September 22, 2011
I notice that you're careful to avoid directly saying that customers will actually be able to manage UEFI certificates on non-developer hardware. For example: "Microsoft supports OEMs having the flexibility to decide who manages security certificates and how to allow customers to import and manage those certificates" So will customers be getting that access or won't they?Anonymous
September 22, 2011
if Microsoft put a feedback form in Windows 8, or build a specially feedback website for Windows (and support all languages).Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
UEFI Secure Boot offers me new opportunities to have a secure system. I don't want to miss that on my win8 system in the future and for those, who don't want to use that technologie, they can disable it.Anonymous
September 22, 2011
How do the certificate databases get updated?? Would new OS's have to wait for the numerous mobo manufactures to update the BIOS's?? I can see secure dual boot working for current OS's, but any new ones wouldn't be in the database. Also this will be open to non-OEM's too? So I can get a compatible motherboard and turn all this on myself and Windows 8 will be just as secure as if I bought an OEM PC?Anonymous
September 22, 2011
hi, can i know when the win8 beta will come?Anonymous
September 22, 2011
@cjb110 UEFI provides the protocol and interfaces to update the databases. Windows 8 supports these new protocols to update the databases in firmware. The action taken to update such databases are also done securely through PKI. All Windows 8 Certificated systems or motherboards will have support for Secured boot.Anonymous
September 22, 2011
you guys need to check out this concept video that suggests a few improvements for Windows 8. It's fantastic. www.youtube.com/watchAnonymous
September 22, 2011
First of all, hats off to you for responding so quickly to the mounting questions about the subject. You have might respect, and it is greatly appreciated. I guess the Windows 8 team cannot do much about the UEFI spec (which of course was nonetheless created with great input from Microsoft), but what you describe here is a lose-lose situation, unfortunately. Correct me please if I am wrong, but if secure boot is enabled, then legacy (non-signed) OSs can't boot, right? So then we have two possible scenarios:
- Secure boot is enabled on motherboards by default. This will make most other OSs (especially Linux for reasons you are probably well aware of) unbootable unless you turn it off. Average users will be unlikely to even understand the problem, so average users will be incapable of installing other OSs on their system. Cue anti-trust accusations, etc. etc.
- Secure boot is disabled on motherboards by default. Other OS install will be possible, but because the above issue, the average user will never benefit from the added security because the feature will likely be never turned on. That's not a very positive scenario either. (By the way, does the TPM spec. not state that the TPM module must always be enabled by hand by the end user? If so, the latter scenario is the only possible one.)
Anonymous
September 22, 2011
I use both Windows and Linux, and have been doing so since many years. There are a lot of users out there like me. I still consider Windows a bit smelly sometimes, but its ok since WIN 7. .3 things that would change my attitude against Windows 8 would be A) support other OS:es in Boot menu - ie dont destroy grub and stuff when installing windows. B) native support for att ext 2,3,4, filesystems!!! C) native UTF-8 in Windows. If these were there, Microsoft would be getting a lot more positive feedback out there from users like me.Anonymous
September 22, 2011
Ah, I should have read more of the comments. So the TPM is not needed for secure booting. My mistake.Anonymous
September 22, 2011
This has got to be one of the most disgusting "features" I've heard of in over 20 years of computing. What problem is this trying to solve?Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
@Matt E. So you don't think the GPL licensing which all (to the best of my knowledge) Linux distributions fall into specifically forbids withholding the keys required for such certification? Because so far, it looks like that if, let's say Red Hat wants to enable secure boot while satisfying the conditions of GPL, they must release the keys involved with the source code, which malware could then also employ. This would render the whole system just as vulnerable as it is now. (Perhaps a bit worse given the new false sense of security.)Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
As far as I understand it, OEMs will have to allow users to disable, if they want to sell in the EU.Anonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
If all drivers are required to be signed, what happens when I swap out my OEM-provided nVidia card (that overheated/failed) for an AMD one and the AMD keys aren't in the UEFI keystore? Am I unable to boot?Anonymous
September 22, 2011
Note to self: never buy a piece of hardware that uses UEFI instead of good ol' Linux-compatible BIOS. Either that, or become Amish. I'd rather not have a computer than have one running Windows.Anonymous
September 22, 2011
I don't get this whole "Average users will be unlikely to even understand the problem, so average users will be incapable of installing other OSs on their system" problem. Average users are average (as the name implies). They hardly ever install other operating systems. If they choose to they will found out how to disable secure boot using Goo... pardon my French, Bing.Anonymous
September 22, 2011
@pip25: The GPL does not require public signing keys. Since you've obviously never looked at the way security of repositories full of GPL-licenses software works, let me give you a hint: a GPG-signed list of hashes. That's how we verify that a package matches what the archive maintainers have released. This is asymmetric encryption. The public key is available, but the private key, in Ubuntu's case, is held solely by the build servers. Pushing updates to the build servers is done by developers who sign with their own personal private keys. The build server then has the public keys for the developers (to verify their signatures) and the private key for the archive-wide signatures. The user's systems have the public key for the archive-wide signatures. As an Ubuntu Developer, I have no access to the private archive signing key. It is, of course, PRIVATE.Anonymous
September 22, 2011
The problem with saying Red Hat, Ubuntu, Fedora, and so on could have their product certified, is that all these distributions allow the user to compile his own kernel to replace the distribution-provided one (and I have done so on occasion). Therefore, the certification would be able to only go as far as the bootloader - which can load anything (even Windows, via chain-loading). This is unlike Microsoft Windows, where only Microsoft can build a new kernel.Anonymous
September 22, 2011
@Mackenzie Thank you, then I was apparently misinformed. That's certainly a relief. Now I will only hope that major distributions will be able to get themselves keys the various OEM manufacturers will accept in their products.Anonymous
September 22, 2011
Please describe in detail which features of Windows 8 will get disabled if secure boot is turned off in order to allow a dual boot with another operating system.Anonymous
September 22, 2011
NOTE TO HARDWARE VENDORS: I am in charge of buying hardware at my (small) company. We buy several tens of thousands of dollars of PC hardware per year... not a lot in the big scheme of things, but a lot for a small company. We will UNDER NO CIRCUMSTANCES purchase any hardware that does not allow us to install Linux. So those hardware vendors who want to be Windows 8 compliant, think very carefully. If you don't provide a way to disable bootloader verification or allow end-users to insert their own verification keys, you will not get our business. I encourage anyone else in this position to post here.Anonymous
September 22, 2011
Mathew Garret responds to this post: mjg59.dreamwidth.org/5850.htmlAnonymous
September 22, 2011
The comment has been removedAnonymous
September 22, 2011
If the major OEM's fail to allow users to disable secure boot, we will do two things:
- Launch a class action lawsuit against them and Microsoft and
- ask the US congress and the EU to reopen the ant trust proceedings. This isn't something you can just blame on the OEM's it will come back to you a thousand fold. I would suggest requiring OEM's to allow a disable for secure boot. That is the only way for you, Microsoft, to ensure that class action and anti trust activity will not come of this.
Anonymous
September 22, 2011
I 100% agree with Jote, the average user really doesn't bother reïnstalling his pc with a new os. Let alone install Linux. And when they will attempt to reinstall windows they will indeed use google (the average user doesn't know what Bing is (if i tell my wife to use bing as a searchengine she looks @ me like a drunken sheep that just got a lecture from albert einstein)). And if this is some 'clever way' of Microsoft to reinforce their monopoly, i think it fails miserably. The average Linux, etc... user is clever enough to find/figure out how to disable this feature, so there is no "harm" done. Imho i think it's a very good feature and i'm happy to read it will be enabled by default.Anonymous
September 22, 2011
But can Windows 8 boot if I disable secure boot?Anonymous
September 22, 2011
Wow. Another layer of code to slow down our pc's. I wonder if this technology will be broken before the release of doze8 like the blue pill killed any idea of boot security in doze7...Anonymous
September 22, 2011
But why does it have to come down to BIOS checking? You're telling me you guys have no way of making the BIOS area read-only when Windows boots, staying read-only for as long as the PC is on? Banning pretty-poor Windows-based BIOS update tools would just stop unusers from bricking their own PCs...Anonymous
September 22, 2011
But why does it have to come down to BIOS checking? You're telling me you guys have no way of making the BIOS area read-only when Windows boots, staying read-only for as long as the PC is on? Banning pretty-poor Windows-based BIOS update tools would just stop unusers from bricking their own PCs...Anonymous
September 22, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The big issues is that microsoft will say it's up to the OEM to have a option to enable/disable uefi security policy, at the same time microsoft is offering lower win8 license costs to those who don't offer the option of disable the uefi security policy. You can self see what is more important to an OEM, a slightly higher profit on each sold unit or the customers freedom. We will quite soon see viruses which will get around the uefi security policy. as nothing will be stronger than the weakest link, in this case the microsoft products itself.Anonymous
September 23, 2011
Just be warned - if there's any chance of locking out other OS's - you'll get DOJ'd again for Monopolizing. And 3 strikes in Europe is not clever.Anonymous
September 23, 2011
What about Linux? Will it block users wanting to install/boot Linux?Anonymous
September 23, 2011
You should mandate that users have the ability to disable secure boot and add keys, else you leave it up to manufacturers whether a user would ultimately be allowed to boot anything other than windows. If you're willing to leverage your market share to ease the install of your system, you should take the simple steps to ensure you don't make things necessary difficult for other vendors in the process.Anonymous
September 23, 2011
but, will the user be able to sign his own loaders? if the vendor signs windows 8 loader but don't let the user sign a linux loader, then this protection is available only for windows. i just hope that by setting some jumper, or configuring something at the firmware, the user itself will be able to sign his trusted loaders, and not just the loaders the vendor trust.Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
I guess my biggest fear is that the decision to allow/disallow flipping the switch is left up to OEM, not the end users. Past tactics by Microsoft (like most businesses) show that they'll act in their own best interest and not so much for the consumer. While the OEM gets the decision, what sort of influence will Microsoft have in that decision? Will vendors prominently display (in reasonable terms) that they will or won't support the ability to disable this feature? While true that most consumers won't be concerned about it, there are plenty of people that do try alternative operating systems. When I next build a system, I'd like to make sure that it supports the user control over the setting. I'm also the family member that has to go and repair the computers with friends and family members and there have been times where oddly/surprisingly some have asked what I know about Linux . The topic is a bit lower level on the boot process than I'm familiar with, but could there be another option to the secured boot process? What if secured boot was enabled and simply reported if the selected boot loader was approved or not then reported in a standard method to the OS the result of that detection? Operating systems could display a status message about "Secure Boot" or "Non-Certified Boot" depending on the UEFI configuration.Anonymous
September 23, 2011
@pip25, from the developer's perspective I can tell the way Linux code is preserved and versioned in the secure repositories via GIT is done by using the pair of public and private keys. Otherwise those repositories would have compromised first. So the point is; there exists the private aspect when it comes to security. Moreover, Mackenzie elaborated it more explicitly. If there is anyone curious about Linux installation when security is enabled, I am pretty sure that the certified flavors (Ubuntu , fedora, RedHat and many more) would provide the certificate to pass through the UEFI level security. This is my optimistic guess. You can confirm it from Linux folks or ask Linus Torvalds if they are planning to implement this module. Also, for EU folks, you can wait the official words from the engineers of other OSes rather than rumoring something that is not confirmed yet as there are multiple stakeholders involve, OS manufacturers, OEMs and whole bunch of security conscious industry/people…Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
@John "I notice the nice screenshot of the samsung tablet did not have a menu which allows keys to be loaded" Suggestion: Know what you are talking about before you mouth off. You obviously are a master of knowing all with a single screen shot of an OS that is a year out and hardware that isn't finalized or configured for mass use. That is impressive.Anonymous
September 23, 2011
Can the UEFI be infected by malware?Anonymous
September 23, 2011
According to netmarketshare.com, Linux usage is at 1.1% whereas Windows is >92% So, why on earth bothering about giving its support in first place?Anonymous
September 23, 2011
Please - PLEASE - stop saying "no compromise". It's just embarrassing when you try to use meaningless market-speak when you're talking to technology professionals who know better. I'm begging you - stop embarrassing yourselves.Anonymous
September 23, 2011
@ChrisCollinsTheRadioGuy: "Here we are, with a wonderful solution to a growing problem that I have already encountered in my workplace and now the are complaining." Let's be clear here: UEFI and secure boot do NOTHING to stop malware. NOTHING AT ALL. If Windows has a flaw in it, malware will exploit it, secure-boot or no secure-boot.Anonymous
September 23, 2011
To @Jim_Maryland: "Don't you see anything good in terms of development?" I do. UEFI and Secure Boot are excellent features. But only if they let me use MY OWN signing key. I do not trust Microsoft. I do not trust VMWare. I do not trust Oracle, HP, or any other vendor. I do not trust anyone else to determine what is safe for MY computer. I trust only myself and I only want my computer to run software I approve, not what someone else does.Anonymous
September 23, 2011
Microsoft--do you REALLY think the OEMs are going to let end-users turn off secure boot? NO. They will lock it down, just like most OEMs who either hide the BIOS Setup entry prompts or put an administrative lock on the BIOS (or worse--make all but a handful of BIOS Setup options available). The only exception is DELL, who not only makes the BIOS Setup available, but also makes the setup options available! OEMs are not engineering companies--they are sales companies. They will do everything they can make sure support calls are kept to a minimum (ever try calling Acer, Asus, or Samsung? It's a nightmare and they are very quick to say "you changed something--warranty void. Goodbye." I like what I see with Windows 8 so far, but this is a huge turn-off for me and might make me stay with Windows 7 or even switch to Mac.Anonymous
September 23, 2011
@David F. Skoll, it'll work to stop exploits like blue pill ( en.wikipedia.org/.../Blue_Pill_(malware) ), which are becoming increasingly common. Something else it'll help stop is the bootloader attacks that were used to compromise the activation system in Vista/7, though since it can be disabled, will not be 100%.Anonymous
September 23, 2011
i have just lad my hands on the windows 8 developers preview build version ..it was superb ..i like each and every creative work you guys did in windows 8...its simply superb .... wish to see more in coming months...Anonymous
September 23, 2011
i have just lad my hands on the windows 8 developers preview build version ..it was superb ..i like each and every creative work you guys did in windows 8...its simply superb .... wish to see more in coming months...Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
If that's true I'm glad. Though in the past these kind of denials usually mean their long game is precisely what they're denying. They denied plenty of other anti-competitive practices too, but the courts saw it differently.Anonymous
September 23, 2011
@Nathan Ladwig: "Blue Pill" is esoteric compared to run-of-the-mill malware that arrives as a plain .EXE or .SCR. Users are either tricked into installing it or don't know they're installing malware (thank you, Sony.) This malware doesn't need to touch the boot sector. It doesn't even need to exploit Windows. It just sits quietly listening for commands and sending spam or running a DDoS. This malware spreads because of a brain-dead decision 25+ years ago to conflate file naming with "executableness". If Windows had a UNIX "x" bit instead of relying on filename extensions to mark executableness, the malware industry would be much smaller. The really effective way to slow down malware is to ditch Windows entirely. Patching a basically flawed design this late in the game is pointless.Anonymous
September 23, 2011
@Nathan Ladwig: "Blue Pill" is esoteric compared to run-of-the-mill malware that arrives as a plain .EXE or .SCR. Users are either tricked into installing it or don't know they're installing malware (thank you, Sony.) This malware doesn't need to touch the boot sector. It doesn't even need to exploit Windows. It just sits quietly listening for commands and sending spam or running a DDoS. This malware spreads because of a brain-dead decision 25+ years ago to conflate file naming with "executableness". If Windows had a UNIX "x" bit instead of relying on filename extensions to mark executableness, the malware industry would be much smaller. The really effective way to slow down malware is to ditch Windows entirely. Patching a basically flawed design this late in the game is pointless.Anonymous
September 23, 2011
In short this sounds like a proxy war tactic. MSFT has the "OEMs" lock down future BIOS to boot just Windows OS. Oh you wanna run Linux on your machine..? Too bad your OEM does not allow that...! Instead please keep staring at that shiny Windows sticker on your machine. Profit! //FWIW, I and my org will not be buying hardware locked down to a MSFT OS. Get a clue, if you want my $$.Anonymous
September 23, 2011
[Off-Topic] Could the msdn.com blog programmers please write blog software that detects and suppresses double-submissions? Now that you have a plan to destroy non-MSFT operating systems, surely you have some time on your hands? :)Anonymous
September 23, 2011
I am a loser and a folking troll. I'ts not my fault (That's what my mother told me). Please don't read my nonsense comments too much.Anonymous
September 23, 2011
@Prettysure: would you be so kind and return on topic? As if Microsoft would suddenly listen to your all-caps and change Windows 8 philosophy and release strategy. Get real? @Brendan: you are complaining about "locking down" and threatening to switch to a Mac at the same time. Seriously? ;)Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
UEFI off topic, but W8 related: www.zdnet.com/.../14917Anonymous
September 23, 2011
I think disabling Secure Boot functionality is a last resort solution and really shouldn't be required to boot other operating systems. The user should have control over the keys. How likely is it that some OEM gives its customers the possibility to upload public keys? Just like the existing trusted boot facilities which utilize a TPM it should work just fine with other operating systems. Sadly, I doubt that many vendors will give users those possibilities.Anonymous
September 23, 2011
What happens when a root sekret key is compromized?Anonymous
September 23, 2011
The "I am a loser and a folking troll." fake comment is clearly the best that a pitiful little Microsoft fanboi (or was it an employee?) could muster. How pathetic.Anonymous
September 23, 2011
So what if I am really a big time fuffing looser... so what? I don't have respect and all that? R u kidding me? I am a lowlife cockroach how can I earn some respect? I was born during daporn. So what people, so whaaaat?Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
So, in short, you've confirmed everything Garret was saying. The only way out of this fiasco is to mandate user-accessible control of UEFI checks in motherboard configuration.Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
@David F. Skoll, are you a sociopath? Seriously?Anonymous
September 23, 2011
If Microsoft continue follow this idea i will report it to the European Union. I will report it as You and the hardware manufacturers have a "secret" deal closing for alternative OS:es and so on. I don't trust Microsoft !Anonymous
September 23, 2011
I will sue them for not giving me free WINDOWS7!!!!! grrrrrrr!Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
Will it be possible to buy Windows 8 hardware that comes without UEFI secure boot in its entirety? I prefer generic, unspecialized hardware.Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
@"Let us change together" :-) Linux 1.1% vs Windows 92.8% after 17 years ??? Was it ever born?Anonymous
September 23, 2011
Linux accounts for more installations across ALL devices than Windows.Anonymous
September 23, 2011
@Iam Melab.. Yawn.. who cares? Btw, you are a troll. Just saying!Anonymous
September 23, 2011
@I am Melab, thus far I am using win8 in my PentiumD machine with Fedora10 and win7. You don't have to buy UEFI board if you don't want. Microsoft as always supporting multiple boards and architectures and so is Linux) as opposed to the iCrap. Lot of people trolling about enabling security in UEFI would make the machine Windows-only. Well that's not the case at all. You can dual boot with UEFI and other OSes (like Linux or Windows.old) with or without the UEFI security enable, in case they pass the UEFI certification phase. (and most Linux flavors shall employe those certificates) Which is in fact for your security. But. if you still don't like it just get rid of it. You can disable it. Also, you always have option to get BIOS-based board.Anonymous
September 23, 2011
Its not just about the security thing, which I don't see Microsoft doing to lockdown PCs, considering the DoJ still has their eye on them. I just prefer generic hardware. I'd rather the secure boot portion be implemented in software. Additionally, does anyone know if the ARM versions of Windows 8 will come with the capability to disable secure boot? And no StatsPerson, I am not a troll. Just a curious person.Anonymous
September 23, 2011
@Matt E. keep it simple. If you don't like it don't use it. Confused people like Iam Melab 1) use Windows 2) given any reason, they tend to participate in trolling against it.Anonymous
September 23, 2011
A note on comments and community standards. These comments are well below the level of dialog we hoped to have on this blog. If people cannot police themselves in their reactions to design discussions and to each other, then the mechanisms for comments will change. Respectfully, StevenAnonymous
September 23, 2011
@Steve, would you mind answering the questions I posted? (My apologies if this post comes off sounding rude.)Anonymous
September 23, 2011
@Steven Sinofsky I think this blog should be members only now. Anyone trolling should be banned from Windows Live.Anonymous
September 23, 2011
@Steven, yea, there've been numerous questions left unanswered here, care to shed some light on 'em?Anonymous
September 23, 2011
I am afraid this is not the good place to raise questions. As you might have observed, parsing 100+ comments and answering them is a cumbersome. To entertain your questions, windows-8 forums are designed and deployed (http://win8.ms/forums). Also, you can send your feedback using the feedback tool available on Connect website. Thanks you.Anonymous
September 23, 2011
Please raise your questions at http://win8.ms/forums.Anonymous
September 23, 2011
@Tony Mangefeste: Thanks for the info! I'll get up to speed with this stuff at the weekend, and ask questions when i know more about the subject. Regarding key presses, standardizing on those keys is good in itself, but now we have the situation that there is another way of accessing boot menus, depending on firmware and OS on the system in question. And of course, the answer to the question "what operating system are your running?" is "don't know" or "i think it's X". So trial and error will be necessary on the phone. Rather than restating my point, please refer to the comments in the //build/ video by Emily Wilson @57.08 (yes i did watch it all :) ) @cjb110: "How do the certificate databases get updated??" Windows UpdateAnonymous
September 23, 2011
Can you post the channel9 link for the video you mentioned? Thank you.Anonymous
September 23, 2011
@Steven Sinofsky: "These comments are well below the level of dialog we hoped to have on this blog." My two bits worth: When people feel they can be more virtuous than the next guy, just by saying something vaguely pro-social, their behaviour will deteriorate in other respects, to keep things in balance. Quality affects at work.Anonymous
September 23, 2011
Delivering a secure and fast boot experience with UEFI channel9.msdn.com/.../HW-457TAnonymous
September 23, 2011
perhaps ms is starting to cut pipes that made them money.Anonymous
September 23, 2011
@Steven Sinofsky I would suggest requiring a Live ID or OpenID to post. Not a big deal, but it could help with impersonations, for instance. About OEMs not including the disable option: I doubt that will be the case for a very simple reason: Doing so would mean that their computers would only run Win8. No Windows 7. No XP. Even if they don't care for OS alternatives like Linux, not everyone will want to upgrade to Winows 8 right away, and offering a motherboard which can run none of the previous Windows versions would be a very stupid decision generating unnecessary bad PR. I am more concerned about what Mathew Garret mentioned in his blog posts: The developers of other OSs will be simply unable to get their own keys added because they lack MSFT's resources, making every OS other than Win8 a second-class citizen on the PC, which STILL counts as an anti-competitive measure. The ability for users to add their keys via a secure, non-automated way through the UEFI would be the ideal solution.Anonymous
September 23, 2011
Imvho, pushing the same kindda comment over and over ain't gonna make them revert their decision. Linux tend to make Windows secondary so does Windows. But till date they never came across eachother. It is just the matter of bootloader where we can see Windows and Linux listed together (or on the Novell's website if you really care about moonlight). Otherwise people from Linux world don't have any respect for other worlds and vice versa. This is a blatant truth. Now about this OEM decision thing. If you take a closer look at this matter and think twice, it's really the OEM choice. You may get into the debate that its actually the company guy pressuring them to do so. But it doesn't matter for the end user like joe. You can expect something like: (just visualize) on dell's website, there are two rows for latest set of laptops and tablets on the showcase page. One contains Windows-only ARM/Intel machines and the other one contain open-for-all machine (unlocked, without OS). Now, I am not gonna comment on what percent of win-only machines would be sold (which is obviously some higher percentage and ofcourse im not betting on your money!). Just think about the other machines, how many percentage would get Windows installed in them even the end user have the leeway to install the OS of their choice… (be realistic; perhaps 1.1 : 92.8)??Anonymous
September 23, 2011
This does not address the real issue with Secure Boot, which is that bootloaders for virtual machines or other operating systems (including older versions of Windows) will not be able to run. Will OEMs include keys for all other possible legitimate bootloaders? Will they all really add a function to turn off Secure Boot, because we all know that OEMs don't always handle the BIOS very well? The other issue is that it's debatable whether this really adds a practical layer of security. Malware currently can be virtually irremovable even without touching the bootloader, just by embedding itself into Windows libraries. That's rootkit behaviour. Secure Boot will not prevent it. Who needs a modified bootloader when you can hide within the system's own DLLs and be almost undetectable, and certainly irremovable?Anonymous
September 23, 2011
UEFI based Windows8 would probably be tablets and next-gen touch PCs. For older desktops, BIOS is not refraining you to do dual boot. But imagine if you have an ARM, UEFI based tablet. Would you like to make it dual boot with other OSes? Wouldn't it be ugly to have 2 OS on tablet? A real PC running anything other than Windows is an ugly PC !!Anonymous
September 23, 2011
It's interesting that Microsoft have chosen to respond to the myriad of comments complaining that the Windows 8 boot loader (like the Win 7 boot leader before it) assumes that it has the right to overwrite any other boot loader that the user might have installed, without so much as a warning, or an accommodation to existing setups - with a post about UEFI Secure Boot. Let's be clear about something: UEFI Secure Boot is totally unrelated to the complaints about the Win 8 Boot Loader. @Steven_Sinofsky knows this, but has chosen to ignore the issue. I take exception to that. For example, if you have an existing dual-boot Win 7/Win XP machine, and install the Win 8 Preview, it will simply overwrite the existing boot loader. It will recognise the Win 7 installation, but will remove the Win XP install from the menu. That's totally unacceptable install behaviour. Note that this happens on Non-UEFI systems, so Microsoft can't use "UEFI Secure Boot" as an excuse for why the installer does this. If Microsoft simply accommodated users with dual-boot systems inside the Windows Boot loader, then users wouldn't have to install a GRUB loader between the BIOS and the Win Boot loader, would they? But that's never going to happen. I find this post disingenuous and unhelpful, frankly. It's irrelevant what a locked down OEM laptop single booting Win 8 is doing when complaints are being made about dual boot enterprise or "home professional" installation procedures.Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
Please look into this bug report, and press "I can too" if you think its critical: connect.microsoft.com/.../v8-benchmark-and-ie10 @Dev-Team, please improve the performance and incorporate swifter RegEx engine in IE10.Anonymous
September 23, 2011
Please address the performance issues pertaining to the test suites cited in these bug reports:
- connect.microsoft.com/.../v8-benchmark-and-ie10
- connect.microsoft.com/.../a-dom-manipulation-test-ie-performance
Anonymous
September 23, 2011
I see one of my posts seems to have got lost in Azures database, that shouldn't happen should it ;-)Anonymous
September 23, 2011
Microsoft should make sure that Windows-Certified systems have an ability to update certificate lists. All keys leak, and if Secure Boot boots system that uses a compromised certificate, it's worse than having no Secure Boot at all.Anonymous
September 23, 2011
Keys will leak 24 Sep 2011 5:21 AM
Microsoft should make sure that Windows-Certified systems have an ability to update certificate lists. All keys leak, and if Secure Boot boots system that uses a compromised certificate, it's worse than having no Secure Boot at all. That's another thing as the OEMs themselves need to have Security Measures to avoid that this happens and that their Employes that have todo with this Specific parts can't leak them to Criminal Groups they work together with for Profit Reasons, which would make this obsolete again, but im sure revoking is also part of the Specification in those cases but you first need to know that a key has leaked to react.
Anonymous
September 23, 2011
i defend part A & part C of suggestions of "Windows 8 suggestions" : blogs.msdn.com/.../protecting-the-pre-os-environment-with-uefi.aspxAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
@Saad Shamsaei, how about leave windows at once now and just start using linux? Also stop visiting and following up with windows development. Please don't embarrass yourself anymore.Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
anywho, what about Blu-Ray??? will playback be builtin, inclduing resizing the video for <1080 screens? will the rendering be handled by DWM? seems that's only used for the desktop, and not general rendering.. what about good ole DirectShow????? last i heard it was being dumped, fine please do, but are you going to include FLAC & ALAC codecs? (ALAC is really just an AC3 file in a MP4 container anyway.) anything else i forgot to ask about?Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
@David F. Skoll, AFAIK you were trolling against the company as a whole at some point in time?Anonymous
September 23, 2011
Dude, forget about these losers. You need to go back to facebook, your community, your people and most importantly where you belong! If you need to find anything within facebook, use the integrated Bing search in Facebook and enjoy the party. Adios.Anonymous
September 23, 2011
@Linux4junkies, Ok. i just defend part C of suggestions. Some Programs and all exe ebooks don't work when there are in a UTF-8 characters named folder, or file is named with UTF-8 characters (when run a explorer address that contain UTF-8 characters).Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
I really don't understand what the issue is. It is highly likely that vendors of major Linux distributions will get their stuff signed and have mechanisms for distributing keys. RedHat is no tiny little company with no market presence who needs government oversight to protect themselves from big bad Microsoft. Furthermore many pieces of perfectly nice hardware will ship with the ability for the user to manage keys and even enable or disable secure boot depending on their needs. Anyone who wants to install Linux (a small minority) will know enough when making purchase decisions to make this one of the buying criteria. Meanwhile, my grandmother who has trouble remembering how to send email some days will be protected when she plugs in the rootkit infested USB stick that she got from Evelyn at work and flips the power switch on her Win8 machine. I hate that Microsoft looking out for the average person can somehow be turned into a bad thing.Anonymous
September 23, 2011
@Drewfus: "Time for a fundamental update, don't you think?" Sure. But why this update? Doesn't buy anything.Anonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
The comment has been removedAnonymous
September 23, 2011
I would be really happy if IE10 for Windows 8 will put Sandboxing? Just like Chrome approach or even betterAnonymous
September 23, 2011
I would be really happy if IE10 for Windows 8 will put Sandboxing?Anonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
@David F. Skoll, then you better not buy win8 machine. Stick to Linux. Good Luck!Anonymous
September 24, 2011
@Jesse: I have never bought Windows and never will. I run a small company and no-one uses Windows. We all use Linux at work. I, my kids and my parents all use Linux at home, so I really don't care how Windows evolves. However, I don't want to be restricted in my choice of hardware, which is why I am worried by the whole secure boot thing. It doesn't protect against any common malware (as mentioned by others, almost no malware today is boot-sector malware) so I'm not sure what attack scenario Microsoft is trying to prevent, other than prevention of booting of "unauthorized" software AKA competing operating systems.Anonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
@David F. Skoll. You have kids? Lol I thought u r some stupid kid with no company. Coz usually that kind of abandoned and lonely people/junkies are addicted to Linux.. If you don't use anything belongs to Microsoft (which I highly doubt after seeing your keen presence on Channel9 and then here), why you are here? Ask yourself this question, stop embarrassing yourself any further and leave the house sir!Anonymous
September 24, 2011
@Jesse: Ad-hominem attacks (sorry for using hard words... go look it up assuming you know how to use a dictionary) are the sign of a small mind. I'm here not because I use Windows (I do not) but because Microsoft is trying to make it harder for me, a non-customer, to use the OS of my choice.Anonymous
September 24, 2011
@ David F. Skoll Linux is for loners and trolls like yourself. You must have your own version called Troll Edition especially made for trolling Microsoft blogs. Get out of here, no one wants your hear your anti rants.Anonymous
September 24, 2011
@David F. Skoll: I'm not here to defend Microsoft, as many of my earlier comments would suggest, but on the question of Windows general security, versus, lets see ... Linux, could we make the following comparisons?... Windows Integrity Mechanism msdn.microsoft.com/.../bb625963.aspx versus what in Linux? Protected Mode apps (IE9/10 and Adobe Reader X) msdn.microsoft.com/.../bb250462(v=VS.85).aspx versus what in Linux? Secure Boot (in ~12 months) versus what in Linux? "I really can't see how locking down which OS you are allowed to boot can help with any of these things." Allowed to boot? What does that mean? Please refer to Figure 5 in this post. Secure Boot is a firmware option. There is no conspiracy.Anonymous
September 24, 2011
@David F. Skoll: I'm not here to defend Microsoft, as many of my earlier comments would suggest, but on the question of Windows general security, versus, lets see ... Linux, could we make the following comparisons?... Windows Integrity Mechanism msdn.microsoft.com/.../bb625963.aspx versus what in Linux? Protected Mode apps (IE9/10 and Adobe Reader X) msdn.microsoft.com/.../bb250462(v=VS.85).aspx versus what in Linux? Secure Boot (in ~12 months) versus what in Linux? "I really can't see how locking down which OS you are allowed to boot can help with any of these things." Allowed to boot? What does that mean? Please refer to Figure 5 in this post. Secure Boot is a firmware option. There is no conspiracy.Anonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
I'm honestly surprised by the losers who fake posts under my name. We're just talking about technology here; don't get so personal. And yet some people feel the urge to write sophomoric posts and eschew technical discussion. Anyway, it's easy to tell which of my posts are real. They're the grammatically correct and correctly-spelled ones.Anonymous
September 24, 2011
you do't decide for release Windows XP Sp4. Windows XP is Simple and Best choice for Pro Users. WINDOWS 7 is Good only for Chess Gaming or Parade for Nice Desktop or Areo .Anonymous
September 24, 2011
@David F. Skoll Successfully running malware on Windows is becoming increasingly difficult and, with the inclusion of AV software in Windows 8 that will become even more true. One of the core areas of vulnerability however is the boot sequence. There is malware in the wild that exploits this and proof-of-concept attacks which use Hypervisor technology to launch malware that would be OS independent and nearly impossible to detect from within an OS and equally difficult to get rid of. Protecting the boot sequence before such malware becomes prevalent will be better for everyone. Whilst they may not be under extensive Antitrust monitoring any more it's unlikely Microsoft would take the steps you suggest, since it wouldn't be long before they were back in court.Anonymous
September 24, 2011
@AndyCadley: "Successfully running malware on Windows is becoming increasingly difficult" That is not my experience. I work in a field related to computer security (anti-spam, specifically) and we still see lots of successful Windows malware. (More and more, it's using social engineering that no amount of boot-time protection can prevent.)Anonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
The comment has been removedAnonymous
September 24, 2011
"Any OEM that won't let me turn this off or load my own certs won't get any business from me." Well said, the cynic in me thinks this has the major side-ploy to prevent people from running The Penguin (e.g. "Palladium II" or "Trusted" Computing II). I have switched to FOSS OS's about 6-7 years ago for better security and stability, no OEM giving me the choice to run them will not get my business.Anonymous
September 24, 2011
Also, I fully agree that -if- the OEMs don't let you load another OS that they shouldn't be purchased from, but I've yet to see any proof that that's going to happen. All I'm seeing is a bunch of people getting essentially toyed with by Redhat's spokespeople to think that it's going to happen.Anonymous
September 24, 2011
Comments temporarily unavailable.