Rôles et autorisations de gouvernance pour les Data Catalog classiques dans les types gratuits et compte d’entreprise
Importante
Cet article décrit les autorisations de gouvernance dans les versions gratuites et d’entreprise des solutions de gouvernance des données Microsoft Purview à l’aide de la Catalogue de données Microsoft Purview classique.
- Pour obtenir des autorisations à l’aide de la nouvelle Catalogue unifié Microsoft Purview, consultez l’article Autorisations de gouvernance des données.
- Pour obtenir des autorisations générales dans le nouveau portail Microsoft Purview , consultez autorisations dans le portail.
- Pour connaître les autorisations de conformité et de risque classiques, consultez les autorisations dans l’article portail de conformité Microsoft Purview.
- Pour obtenir des autorisations de gouvernance des données classiques, consultez les autorisations dans l’article sur le portail de gouvernance Microsoft Purview.
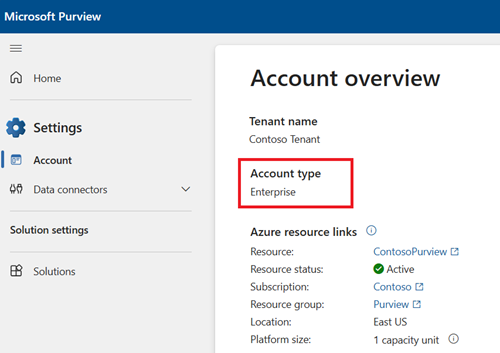
La gouvernance des données Microsoft Purview propose deux solutions dans le portail Microsoft Purview : Data Map et le catalogue. Ces solutions utilisent des autorisations au niveau du locataire/de l’organisation, des autorisations d’accès aux données existantes et des autorisations de domaine/collection pour fournir aux utilisateurs l’accès aux outils de gouvernance et aux ressources de données. Le type d’autorisations disponibles dépend de votre type de compte Microsoft Purview. Vous pouvez case activée votre type de compte dans le portail Microsoft Purviewsous paramètres carte et Compte.
| Type de compte | Autorisations de locataire/organisation | Autorisations d’accès aux données | Autorisations de domaine et de collection |
|---|---|---|---|
| Gratuit | x | x | |
| Enterprise | x | x | x |
Pour plus d’informations sur chaque type d’autorisation, consultez les guides suivants :
- Autorisations de locataire/organization : attribuées au niveau de l’organisation, elles fournissent des autorisations générales et administratives.
- Autorisations au niveau du domaine et de la collection : autorisations dans le Mappage de données Microsoft Purview qui accordent l’accès aux ressources de données dans Microsoft Purview.
- Autorisations d’accès aux données : autorisations dont disposent déjà les utilisateurs sur leurs sources de données Azure.
Pour plus d’informations sur les autorisations basées sur le type de compte, consultez les guides suivants :
Importante
Pour les utilisateurs nouvellement créés dans Microsoft Entra ID, la propagation des autorisations peut prendre un certain temps, même après l’application des autorisations correctes.
Groupes de rôles au niveau du locataire
Attribués au niveau de l’organisation, les groupes de rôles au niveau du locataire fournissent des autorisations générales et administratives pour les Data Catalog Mappage de données Microsoft Purview et classiques. Si vous gérez votre compte Microsoft Purview ou la stratégie de gouvernance des données de votre organization, vous avez probablement besoin d’un ou plusieurs de ces rôles.
Les groupes de rôles de niveau locataire de gouvernance actuellement disponibles sont les suivants :
| Groupe de rôles | Description | Disponibilité du type de compte |
|---|---|---|
| Administrateur Purview | Créez, modifiez et supprimez des domaines et effectuez des attributions de rôles. | Comptes gratuits et d’entreprise |
| Administrateurs de sources de données | Gérer les sources de données et les analyses de données dans le Mappage de données Microsoft Purview. | Comptes d’entreprise |
| conservateurs Data Catalog | Effectuez des actions de création, de lecture, de modification et de suppression sur des objets de données de catalogue et établissez des relations entre les objets dans le Data Catalog classique. | Comptes d’entreprise |
| Lecteurs Data Estate Insights | Fournit un accès en lecture seule à tous les rapports d’insights sur les plateformes et les fournisseurs dans le Data Catalog classique. | Comptes d’entreprise |
| Administrateurs Data Estate Insights | Fournit un accès administrateur à tous les rapports d’insights sur les plateformes et les fournisseurs dans le Data Catalog classique. | Comptes d’entreprise |
Pour obtenir la liste complète de tous les rôles et groupes de rôles disponibles, pas seulement pour la gouvernance des données, consultez rôles et groupes de rôles dans les portails Microsoft Defender XDR et Microsoft Purview.
Comment attribuer et gérer des groupes de rôles
Remarque
Les utilisateurs doivent avoir le rôle de gestion des rôles ou le rôle Administrateur général pour le organization afin d’attribuer des rôles.
Importante
Microsoft vous recommande d’utiliser des rôles disposant du moins d’autorisations. La réduction du nombre d’utilisateurs disposant du rôle Administrateur général permet d’améliorer la sécurité de vos organization. En savoir plus sur les rôles et autorisations Microsoft Purview.
Pour attribuer et gérer des rôles dans Microsoft Purview, suivez les autorisations dans le guide Microsoft Purview.
Autorisations pour rechercher dans le Data Catalog classique
Aucune autorisation spécifique n’est nécessaire dans le catalogue pour pouvoir le rechercher. Toutefois, la recherche dans le catalogue retourne uniquement les ressources de données pertinentes que vous avez les autorisations nécessaires pour afficher dans data map.
Les utilisateurs peuvent trouver une ressource de données dans le catalogue dans les cas suivants :
- L’utilisateur dispose au moins des autorisations de lecture sur une ressource Azure ou Microsoft Fabric disponible
- L’utilisateur dispose d’autorisations de lecteur de données sur un domaine ou une collection dans le Mappage de données Microsoft Purview où la ressource est stockée
Les autorisations sur ces ressources sont gérées au niveau de la ressource et au niveau du mappage de données.
Autorisations de domaine et de collection
Les domaines et les collections sont des outils que le Mappage de données Microsoft Purview utilise pour regrouper des ressources, des sources et d’autres artefacts dans une hiérarchie à des fins de détectabilité et de gestion du contrôle d’accès au sein du Mappage de données Microsoft Purview.
Rôles de domaine et de collection
Le Mappage de données Microsoft Purview utilise un ensemble de rôles prédéfinis pour contrôler qui peut accéder à ce qui se trouve dans le compte. Ces rôles sont actuellement les suivants :
- Administrateur de domaine (au niveau du domaine uniquement) : peut attribuer des autorisations au sein d’un domaine et gérer ses ressources.
- Administrateur de collection : rôle pour les utilisateurs qui devront attribuer des rôles à d’autres utilisateurs dans le portail de gouvernance Microsoft Purview ou gérer des regroupements. Les administrateurs de regroupements peuvent ajouter des utilisateurs à des rôles sur les regroupements où ils sont administrateurs. Ils peuvent également modifier des collections, leurs détails et ajouter des sous-collections. Un administrateur de collection sur la collection racine a également automatiquement l’autorisation d’accéder au portail de gouvernance Microsoft Purview. Si votre administrateur de collection racine doit être modifié, vous pouvez suivre les étapes décrites dans la section ci-dessous.
- Conservateurs de données : rôle qui permet d’accéder aux Catalogue unifié Microsoft Purview pour gérer les ressources, configurer des classifications personnalisées, créer et gérer des termes de glossaire et afficher des insights sur le patrimoine de données. Les conservateurs de données peuvent créer, lire, modifier, déplacer et supprimer des ressources. Ils peuvent également appliquer des annotations aux ressources.
- Lecteurs de données : rôle qui fournit un accès en lecture seule aux ressources de données, aux classifications, aux règles de classification, aux collections et aux termes du glossaire.
- Administrateur de source de données : rôle qui permet à un utilisateur de gérer les sources de données et les analyses. Si un utilisateur n’est accordé qu’au rôle d’administrateur de source de données sur une source de données donnée, il peut exécuter de nouvelles analyses à l’aide d’une règle d’analyse existante. Pour créer de nouvelles règles d’analyse, l’utilisateur doit également être accordé en tant que lecteur de données ou conservateur de données .
- Lecteur d’insights : rôle qui fournit un accès en lecture seule aux rapports d’insights pour les collections où le lecteur d’insights a également au moins le rôle Lecteur de données . Pour plus d’informations, consultez Autorisations d’insights.
- Auteur de stratégie : rôle qui permet à un utilisateur d’afficher, de mettre à jour et de supprimer des stratégies Microsoft Purview via l’application Stratégie de données dans Microsoft Purview.
- Administrateur de flux de travail : rôle qui permet à un utilisateur d’accéder à la page de création de flux de travail dans le portail de gouvernance Microsoft Purview et de publier des flux de travail sur des collections pour lesquelles il dispose d’autorisations d’accès. L’administrateur de flux de travail n’a accès qu’à la création et a donc besoin au moins de l’autorisation lecteur de données sur une collection pour pouvoir accéder au portail de gouvernance Purview.
Remarque
À l’heure actuelle, le rôle d’auteur de stratégie Microsoft Purview n’est pas suffisant pour créer des stratégies. Le rôle d’administrateur de source de données Microsoft Purview est également requis.
Importante
L’utilisateur qui a créé le compte se voit attribuer automatiquement un administrateur de domaine sur le domaine par défaut et l’administrateur de collection sur la collection racine.
Ajouter des attributions de rôles
Ouvrez le Mappage de données Microsoft Purview.
Sélectionnez le domaine ou la collection dans lequel vous souhaitez ajouter votre attribution de rôle.
Sélectionnez l’onglet Attributions de rôles pour afficher tous les rôles d’une collection ou d’un domaine. Seul un administrateur de collection ou un administrateur de domaine peut gérer les attributions de rôles.
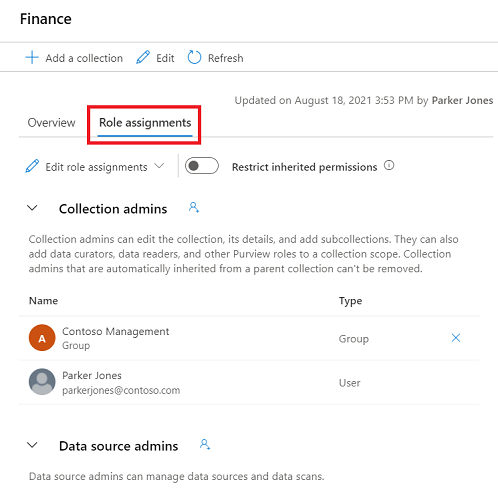
Sélectionnez Modifier les attributions de rôles ou l’icône de personne pour modifier chaque membre de rôle.
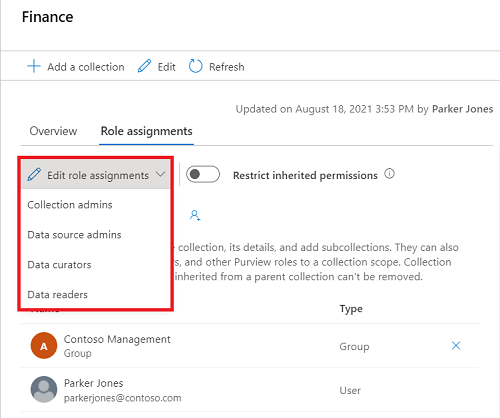
Tapez dans la zone de texte pour rechercher les utilisateurs que vous souhaitez ajouter au membre de rôle. Sélectionnez X pour supprimer les membres que vous ne souhaitez pas ajouter.
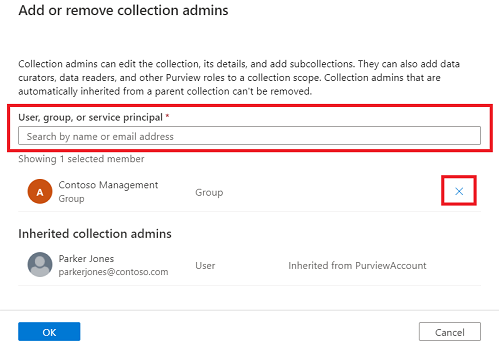
Sélectionnez OK pour enregistrer vos modifications, et vous verrez les nouveaux utilisateurs répercutés dans la liste des attributions de rôles.
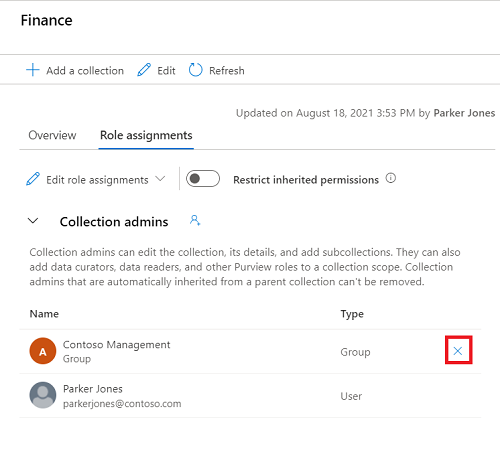
Supprimer les attributions de rôles
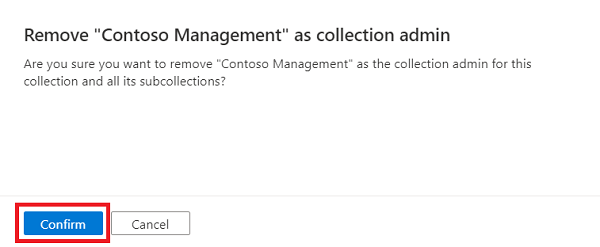
Sélectionnez le bouton X en regard du nom d’un utilisateur pour supprimer une attribution de rôle.
Sélectionnez Confirmer si vous êtes sûr de supprimer l’utilisateur.
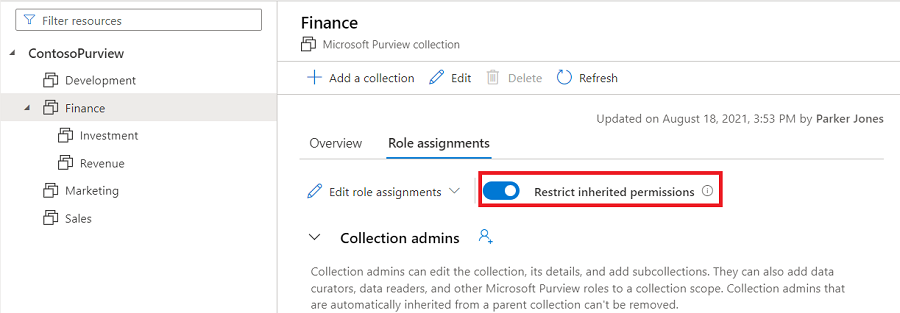
Restreindre l’héritage
Les autorisations de collection sont héritées automatiquement de la collection parente. Vous pouvez restreindre l’héritage d’une collection parente à tout moment, à l’aide de l’option Restreindre les autorisations héritées.
Remarque
Actuellement, les autorisations du domaine par défaut ne peuvent pas être restreintes. Toutes les autorisations affectées au domaine par défaut sont héritées par les sous-collections directes du domaine.
Une fois que vous avez restreint l’héritage, vous devez ajouter des utilisateurs directement à la collection restreinte pour leur accorder l’accès.
Accédez à la collection dans laquelle vous souhaitez restreindre l’héritage, puis sélectionnez l’onglet Attributions de rôles .
Sélectionnez Restreindre les autorisations héritées et sélectionnez Restreindre l’accès dans la boîte de dialogue contextuelle pour supprimer les autorisations héritées de cette collection et de toutes les sous-collections. Les autorisations d’administrateur de collection ne seront pas affectées.
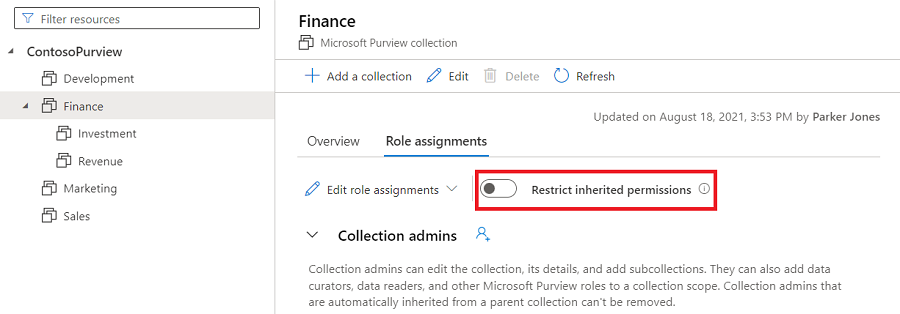
Après la restriction, les membres hérités sont supprimés des rôles attendus pour l’administrateur de collection.
Sélectionnez à nouveau le bouton bascule Restreindre les autorisations héritées pour revenir.
Conseil
Pour plus d’informations sur les rôles disponibles dans les regroupements, consultez la table des rôles qui doivent être affectés ou l’exemple de collections.
Autorisations d’accès aux données
Les autorisations d’accès aux données sont des autorisations dont disposent déjà les utilisateurs sur leurs sources de données Azure. Ces autorisations existantes accordent également l’autorisation d’accéder aux métadonnées de ces sources et de les gérer, en fonction du niveau d’autorisations :
Actuellement, ces fonctionnalités ne sont disponibles que pour certaines sources Azure :
| Source de données | Autorisation de lecteur |
|---|---|
| Base de données Azure SQL | Lecteur, ou ces actions. |
| Stockage Blob Azure | Lecteur, ou ces actions. |
| Azure Data Lake Storage Gen2 | Lecteur, ou ces actions. |
| Abonnement Azure | l’autorisation Lecture sur l’abonnement, ou ces actions. |
Le rôle lecteur contient suffisamment d’autorisations, mais si vous créez un rôle personnalisé, vos utilisateurs doivent avoir les actions suivantes :
| Source de données | Autorisation de lecteur |
|---|---|
| Base de données Azure SQL | « Microsoft.Sql/servers/read », « Microsoft.Sql/servers/databases/read », « Microsoft.Sql/servers/databases/schemas/read », « Microsoft.Sql/servers/databases/schemas/tables/read », « Microsoft.Sql/servers/databases/schemas/tables/columns/read » |
| Stockage Blob Azure | « Microsoft.Storage/storageAccounts/read », « Microsoft.Storage/storageAccounts/blobServices/read », « Microsoft.Storage/storageAccounts/blobServices/containers/read » |
| Azure Data Lake Storage Gen2 | « Microsoft.Storage/storageAccounts/read », « Microsoft.Storage/storageAccounts/blobServices/read », « Microsoft.Storage/storageAccounts/blobServices/containers/read » |
| Abonnement Azure | « Microsoft.Resources/subscriptions/resourceGroups/read » |
Autorisations de lecteur
Les utilisateurs qui ont au moins le rôle de lecteur sur les ressources Azure disponibles peuvent également accéder à ces métadonnées de ressources dans les types gratuit et compte d’entreprise.
Les utilisateurs peuvent rechercher et rechercher des ressources à partir de ces sources dans le Data Catalog classique et afficher leurs métadonnées.
Voici les autorisations nécessaires sur les ressources pour que les utilisateurs soient considérés comme des lecteurs :
| Source de données | Autorisation de lecteur |
|---|---|
| Base de données Azure SQL | Lecteur, ou ces actions. |
| Stockage Blob Azure | Lecteur, ou ces actions. |
| Azure Data Lake Storage Gen2 | Lecteur, ou ces actions. |
| Abonnement Azure | l’autorisation Lecture sur l’abonnement, ou ces actions. |
Autorisations de propriétaire
Les utilisateurs disposant du rôle de propriétaire ou des autorisations d’écriture sur les ressources Azure disponibles peuvent accéder aux métadonnées de ces ressources et les modifier dans des types gratuits et compte d’entreprise.
Les utilisateurs propriétaires peuvent rechercher et rechercher des ressources à partir de ces sources dans le catalogue et afficher les métadonnées. Les utilisateurs peuvent également mettre à jour et gérer les métadonnées de ces ressources. En savoir plus sur la conservation des métadonnées.
Voici les autorisations nécessaires sur les ressources pour que les utilisateurs soient considérés comme des propriétaires :
| Source de données | autorisation du propriétaire |
|---|---|
| Base de données Azure SQL | « Microsoft.Sql/servers/write », « Microsoft.Sql/servers/databases/write », « Microsoft.Authorization/roleAssignments/write » |
| Stockage Blob Azure | « Microsoft.Storage/storageAccounts/write », « Microsoft.Authorization/roleAssignments/write » |
| Azure Data Lake Storage Gen2 | « Microsoft.Storage/storageAccounts/write », « Microsoft.Authorization/roleAssignments/write » |
Autorisations dans la version gratuite
Tous les utilisateurs sont en mesure d’afficher les ressources de données pour les sources disponibles lorsqu’ils disposent déjà d’au moins des autorisations de lecture . Les utilisateurs propriétaires sont en mesure de gérer les métadonnées des ressources disponibles lorsqu’ils disposent déjà au moins des autorisations Propriétaire/Écriture . Pour plus d’informations, consultez la section Autorisations d’accès aux données.
Des autorisations supplémentaires peuvent également être attribuées à l’aide de groupes de rôles au niveau du locataire.
Importante
Pour les utilisateurs nouvellement créés dans Microsoft Entra ID, la propagation des autorisations peut prendre un certain temps, même après l’application des autorisations correctes.
Autorisations dans la version entreprise de Microsoft Purview
Tous les utilisateurs sont en mesure d’afficher les ressources de données pour les sources disponibles lorsqu’ils disposent déjà d’au moins des autorisations de lecture . Les utilisateurs propriétaires sont en mesure de gérer les métadonnées des ressources pour lesquelles ils disposent déjà au moins des autorisations Propriétaire/Écriture . Pour plus d’informations, consultez la section Autorisations d’accès aux données.
Des autorisations supplémentaires peuvent également être attribuées à l’aide de groupes de rôles au niveau du locataire.
Des autorisations peuvent également être attribuées dans le Mappage de données Microsoft Purview afin que les utilisateurs puissent parcourir les ressources dans data Map ou la recherche de Data Catalog classiques auxquelles ils n’ont pas encore accès aux données.