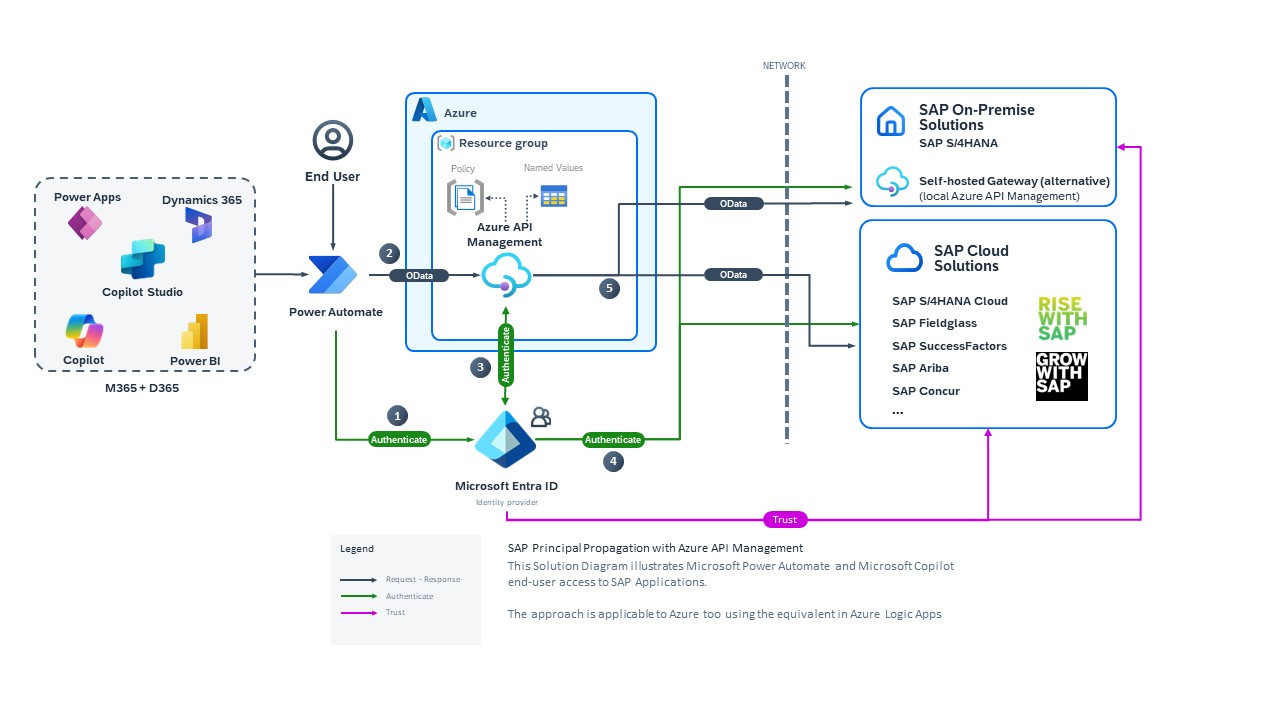
Configurer Microsoft Entra ID, Azure API Management et SAP pour l’authentification unique à partir du connecteur SAP OData
Vous pouvez configurer le connecteur SAP OData pour Power Platform pour utiliser les informations d’identification Microsoft Entra pour l’authentification unique (SSO) dans SAP. Cela permet à vos utilisateurs d’accéder aux données SAP dans les solutions Power Platform sans avoir à se connecter plusieurs fois à plusieurs services tout en respectant leurs autorisations et les rôles attribués dans SAP.
Cet article vous guide tout au long du processus, y compris l’établissement d’une relation de confiance entre SAP et Microsoft Entra ID et la configuration d’Azure API Management pour convertir le jeton OAuth de Microsoft Entra ID en jeton SAML qui est utilisé pour passer des appels OData à SAP.
Vous pouvez également obtenir des informations et un contexte supplémentaires sur le processus de configuration dans le billet de blog, Hourra ! Le connecteur SAP OData prend désormais en charge OAuth2 et la propagation du principal SAP.
Prérequis
- Instance SAP
- Ressource Azure API Management
Télécharger les métadonnées SAML du fournisseur local à partir de SAP
Pour établir une relation de confiance entre SAP et Microsoft Entra ID à l’aide de SAML 2.0, téléchargez d’abord le fichier xml de métadonnées à partir de SAP.
Effectuez ces étapes en tant qu’administrateur SAP Basis dans SAP GUI.
Dans SAP GUI, exécutez la transaction SAML2 pour ouvrir l’assistant dépendant du client SAP concerné et choisissez l’onglet Fournisseur local.
Sélectionnez Métadonnées, puis Télécharger les métadonnées. Vous téléchargerez les métadonnées SAP SAML dans Microsoft Entra ID à une étape ultérieure.
Notez le Nom du fournisseur conforme à l’URI.
Note
Microsoft Entra ID nécessite que cette valeur soit conforme à l’URI. Si le Nom du fournisseur est déjà défini et qu’il n’est pas compatible avec l’URI, ne le modifiez pas sans avoir préalablement consulté votre équipe SAP Basis. La modification du Nom du fournisseur peut interrompre les configurations SAML existantes. Les étapes pour le modifier dépassent le cadre de cet article. Renseignez-vous auprès de votre équipe SAML Basis pour obtenir des conseils.
Consultez la documentation officielle de SAP pour plus d’informations.
Importer des métadonnées SAP dans l’application d’entreprise Microsoft Entra ID
Effectuez ces étapes en tant qu’administrateur Microsoft Entra ID dans le portail Azure.
Sélectionnez Microsoft Entra ID>Applications d’entreprise.
Sélectionnez Nouvelle application.
Recherchez SAP Netweaver.
Attribuez un nom à l’application d’entreprise, puis sélectionnez Créer.
Accédez à Authentification unique et sélectionnez SAML.
Sélectionnez Charger le fichier de métadonnées, puis sélectionnez le fichier de métadonnées que vous avez téléchargé à partir de SAP.
Sélectionnez Ajouter.
Remplacez l’URL de réponse (URL Assertion Consumer Service) par le point de terminaison du jeton SAP OAuth. L’URL se présente au format
https://<SAP server>:<port>/sap/bc/sec/oauth2/token.Remplacez l’URL de connexion par une valeur conforme à l’URI. Ce paramètre n’est pas utilisé et peut être défini sur n’importe quelle valeur conforme à l’URI.
Sélectionnez Enregistrer.
Sous Attributs et revendications, sélectionnez Modifier.
Vérifiez que l’Identificateur utilisateur unique du nom de la revendication (ID de nom) est défini sur user.userprincipalname [nameid=format:emailAddress].
Sous Certificats SAML, sélectionnez Télécharger pour Certificat (Base64) et XML des métadonnées de fédération.
Configurer Microsoft Entra ID en tant que fournisseur d’identité de confiance pour OAuth 2.0 dans SAP
Suivez les étapes décrites dans la documentation sur Microsoft Entra ID pour SAP NetWeaver et OAuth2.
Revenez à cet article une fois le client OAuth2 créé dans SAP.
Consultez la documentation officielle de SAP sur SAP NETWEAVER pour plus de détails. Notez que vous devez être un administrateur SAP pour accéder à ces informations.
Créer une application Microsoft Entra ID qui représente la ressource Azure API Management
Configurez une application Microsoft Entra ID qui accorde l’accès au connecteur SAP OData Microsoft Power Platform. Cette application permet à une ressource Azure API Management de convertir des jetons OAuth en jetons SAML.
Effectuez ces étapes en tant qu’administrateur Microsoft Entra ID dans le portail Azure.
Sélectionnez Microsoft Entra ID>Enregistrements d’applications>Nouvel enregistrement.
Entrez un Nom, puis sélectionnez Enregistrer.
Sélectionnez Certificats et secrets>Nouvelle clé secrète client.
Entrez une Description, puis sélectionnez Ajouter.
Copiez et enregistrez ce secret dans un endroit sûr.
Cliquez sur Autorisations API>Ajouter une autorisation.
Sélectionnez Microsoft Graph>Autorisations déléguées.
Recherchez et sélectionnez openid.
Sélectionnez Ajouter des autorisations.
Sélectionnez Authentification>Ajouter une plateforme>Web.
Définissez URI de redirection sur
https://localhost:44326/signin-oidc.Sélectionnez Jetons d’accès et Jetons d’ID, puis sélectionnez Configurer.
Sélectionnez Exposer une API.
En regard de l’URI de l’ID d’application, sélectionnez Ajouter.
Acceptez la valeur par défaut et sélectionnez Enregistrer.
Sélectionnez Ajouter une étendue.
Définissez Nom de l’étendue sur user_impersonation.
Définissez Qui peut donner le consentement ? sur Administrateurs et utilisateurs.
Sélectionnez Ajouter une étendue.
Copiez l’ID de l’application (client).
Autoriser la ressource Azure API Management à accéder à SAP Netweaver à l’aide de l’application d’entreprise Microsoft Entra ID
Lorsqu’une application d’entreprise Microsoft Entra ID est créée, elle crée un enregistrement d’application correspondant. Recherchez l’Enregistrement d’application correspondant à l’application d’entreprise Microsoft Entra ID que vous avez créée pour SAP NetWeaver.
Sélectionnez Exposer une API>Ajouter une application cliente.
Collez l’ID d’application (client) de l’enregistrement d’application Microsoft Entra ID de votre instance Azure API Management dans ID client.
Sélectionnez l’étendue user_impersonation, puis sélectionnez Ajouter une application.
Autoriser le connecteur SAP OData Microsoft Power Platform à accéder aux API exposées par Azure API Management
Dans l’enregistrement d’application Microsoft Entra ID d’Azure API Management, sélectionnez Exposer une API> Ajouter l’ID client du connecteur SAP OData Power Platform
6bee4d13-fd19-43de-b82c-4b6401d174c3sous les applications clientes autorisées.Sélectionnez l’étendue user_impersonation, puis sélectionnez Enregistrer.
La configuration d’SAP.OAuth
Créez un client OAuth 2.0 dans SAP qui permet à Azure API Management d’obtenir des jetons pour le compte des utilisateurs.
Consultez la documentation officielle de SAP pour plus de détails.
Effectuez ces étapes en tant qu’administrateur SAP Basis dans SAP GUI.
Exécutez la transaction SOAUTH2.
Sélectionnez Créer.
Sur la page ID client :
- Pour ID Client OAuth 2.0, sélectionnez un utilisateur système SAP.
- Entrez une Description, puis sélectionnez Suivant.
Sur la page Authentification du client, sélectionnez Suivant.
Sur la page Paramètres du type d’autorisation :
- Pour IdP OAuth 2.0 approuvé, sélectionnez l’entrée Microsoft Entra ID.
- Sélectionnez Actualisation autorisée, puis sélectionnez Suivant.
Sur la page Attribution de l’étendue, sélectionnez Ajouter, sélectionnez les services OData utilisés par Azure API Management (par exemple, ZAPI_BUSINESS_PARTNER_0001), puis sélectionnez Suivant.
Cliquez sur Terminer.
Configurer Azure API Management
Importez les métadonnées XML SAP OData dans votre instance Azure API Management. Appliquez ensuite une stratégie Azure API Management pour convertir les jetons.
Ouvrez votre instance Azure API Management et suivez les étapes pour créer une API SAP OData.
Sous API, sélectionnez Valeurs nommées.
Ajoutez les paires clé/valeur suivantes :
| Touche | active |
|---|---|
| AADSAPResource | URI du fournisseur local SAP |
| AADTenantId | GUID de votre client |
| APIMAADRegisteredAppClientId | GUID de l’application Microsoft Entra ID |
| APIMAADRegisteredAppClientSecret | Clé secrète client de l’étape antérieure |
| SAPOAuthClientID | Utilisateur système SAP |
| SAPOAuthClientSecret | Mot de passe de l’utilisateur système SAP |
| SAPOAuthRefreshExpiry | Expiration de l’actualisation du jeton |
| SAPOAuthScope | Étendues OData choisies lors de la configuration SAP OAuth |
| SAPOAuthServerAddressForTokenEndpoint | Point de terminaison SAP pour Azure API Management à appeler pour effectuer l’acquisition du jeton |
Note
N’oubliez pas que les paramètres diffèrent légèrement pour SAP SuccessFactors. Pour plus d’informations, consultez la Stratégie Azure API Management pour SAP SuccessFactors.
Appliquer la stratégie de jeton Azure API Management
Utilisez les stratégies Azure API Management pour convertir un jeton émis par Microsoft Entra ID en un jeton accepté par SAP NetWeaver. Pour ce faire, utilisez le flux OAuth2SAMLBearer. Voir la documentation officielle de SAP pour obtenir plus d’informations.
Copiez la stratégie Azure API Management à partir de la page GitHub officielle de Microsoft.
Ouvrez le Portail Azure.
Accédez à votre ressource Azure API Management.
Sélectionnez API, puis sélectionnez l’API OData que vous avez créée.
Sélectionnez Toutes les opérations.
Sous Traitement entrant, sélectionnez Stratégies </>.
Supprimez la stratégie existante et collez la stratégie que vous avez copiée.
Sélectionnez Enregistrer.
Contenu associé
- Connecteur SAP OData
- Le connecteur SAP OData prend désormais en charge OAuth2 et la propagation du principal SAP | Blog de la communauté Power Automate
- Stratégie Azure API Management pour SAP SuccessFactors | GitHub
- Connecteur SAP OData pour SAP SuccessFactors | Blog de la communauté SAP
- Le SAP Business Accelerator Hub propose également du contenu lié à la stratégie de suite d’intégration SAP pour SuccessFactors et NetWeaver. Vous devez disposer d’un compte SAP pour accéder à ce contenu.