Évaluation de la sécurité : délégation Kerberos non sécurisée
Qu’est-ce que la délégation Kerberos ?
La délégation Kerberos est un paramètre de délégation qui permet aux applications de demander des informations d’identification d’accès à l’utilisateur final pour accéder aux ressources pour le compte de l’utilisateur d’origine.
Quel risque la délégation Kerberos non sécurisée représente-t-elle pour un organization ?
La délégation Kerberos non sécurisée permet à une entité d’emprunter l’identité de n’importe quel autre service choisi. Par exemple, imaginez que vous disposez d’un site web IIS et que le compte du pool d’applications est configuré avec une délégation sans contrainte. L’authentification Windows est également activée sur le site web IIS, ce qui autorise l’authentification Kerberos native, et le site utilise une SQL Server principale pour les données d’entreprise. Avec votre compte Domain Administration, vous accédez au site web IIS et vous vous authentifiez auprès de celui-ci. Le site web, qui utilise une délégation sans contrainte, peut obtenir un ticket de service d’un contrôleur de domaine vers le service SQL et le faire en votre nom.
Le main problème avec la délégation Kerberos est que vous devez faire confiance à l’application pour toujours faire la bonne chose. Les acteurs malveillants peuvent à la place forcer l’application à faire la mauvaise chose. Si vous êtes connecté en tant qu’administrateur de domaine, le site peut créer un ticket pour les autres services qu’il souhaite, agissant en tant qu’administrateur de domaine. Par exemple, le site peut choisir un contrôleur de domaine et apporter des modifications au groupe d’administrateurs d’entreprise . De même, le site pourrait acquérir le hachage du compte KRBTGT ou télécharger un fichier intéressant à partir de votre service des ressources humaines. Le risque est clair et les possibilités de délégation non sécurisée sont presque infinies.
Voici une description du risque posé par les différents types de délégation :
- Délégation sans contrainte : tout service peut être utilisé de manière abusive si l’une de ses entrées de délégation est sensible.
- Délégation contrainte : les entités contraintes peuvent être abusées si l’une de leurs entrées de délégation est sensible.
- Délégation contrainte basée sur les ressources (RBCD) : les entités contraintes basées sur les ressources peuvent être abusées si l’entité elle-même est sensible.
Comment faire utiliser cette évaluation de sécurité ?
Passez en revue l’action recommandée sur https://security.microsoft.com/securescore?viewid=actions pour découvrir quelles entités non-contrôleur de domaine sont configurées pour la délégation Kerberos non sécurisée.
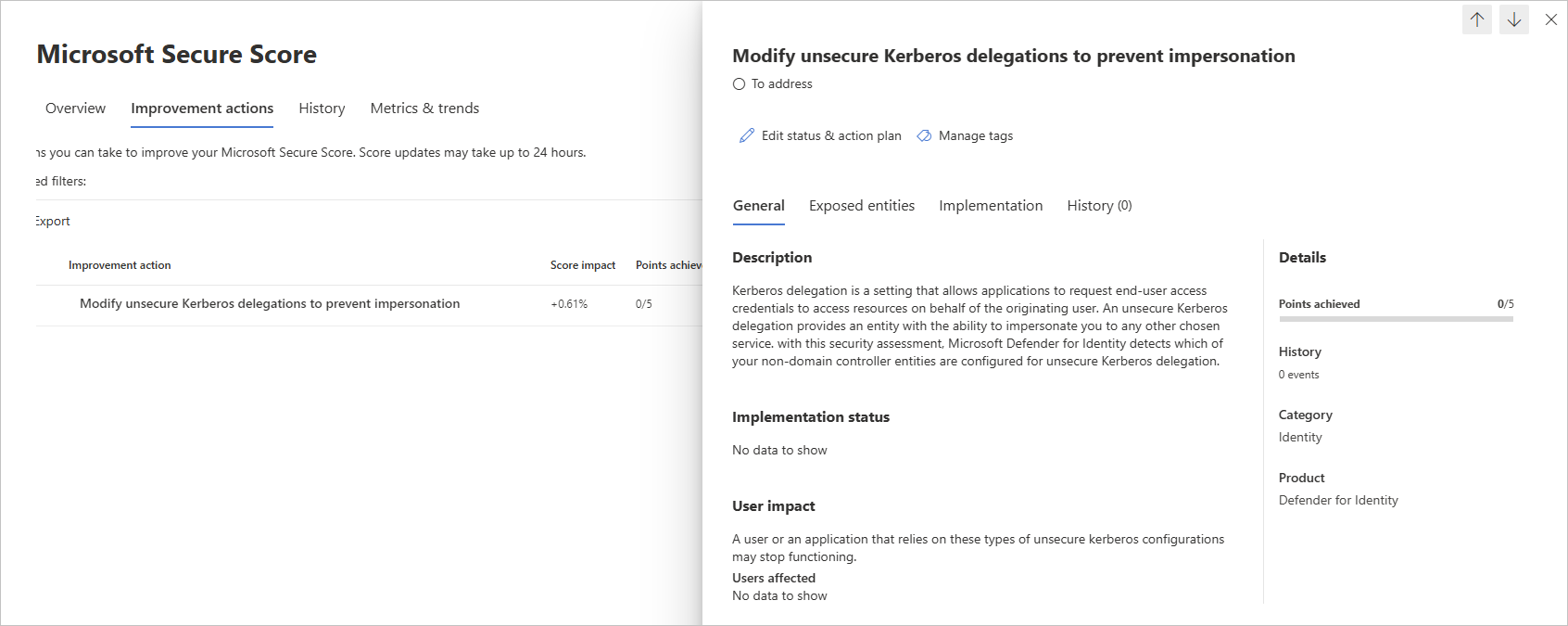
Prenez les mesures appropriées sur ces utilisateurs à risque, par exemple en supprimant leur attribut sans contrainte ou en le remplaçant par une délégation contrainte plus sécurisée.
Remarque
Bien que les évaluations soient mises à jour en quasi-temps réel, les scores et les états sont mis à jour toutes les 24 heures. Bien que la liste des entités concernées soit mise à jour quelques minutes après l’implémentation des recommandations, le status peut encore prendre du temps avant d’être marqué comme Terminé.
Remédiation
Utilisez la correction appropriée à votre type de délégation.
Délégation sans contrainte
Désactivez la délégation ou utilisez l’un des types de délégation Kerberos contrainte (KCD) suivants :
Délégation contrainte : Limite les services que ce compte peut emprunter l’identité.
Sélectionnez N’approuver cet ordinateur que pour la délégation aux services spécifiés.
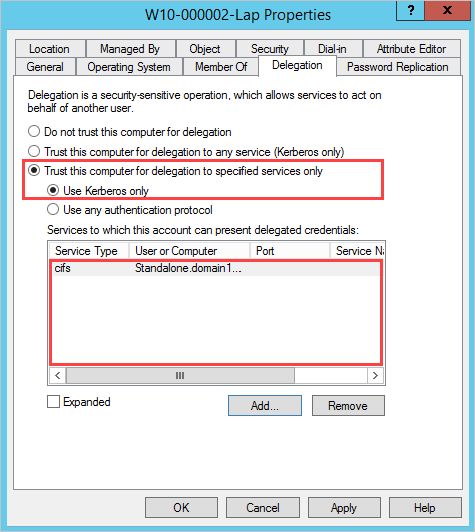
Spécifiez les services auxquels ce compte peut présenter des informations d’identification déléguées.
Délégation contrainte basée sur les ressources : Limite les entités qui peuvent emprunter l’identité de ce compte.
Le KCD basé sur les ressources est configuré à l’aide de PowerShell. Vous utilisez les applets de commande Set-ADComputer ou Set-ADUser , selon que le compte d’emprunt d’identité est un compte d’ordinateur ou un compte d’utilisateur/compte de service.
Délégation contrainte
Passez en revue les utilisateurs sensibles répertoriés dans les recommandations et supprimez-les des services auxquels le compte affecté peut présenter des informations d’identification déléguées.
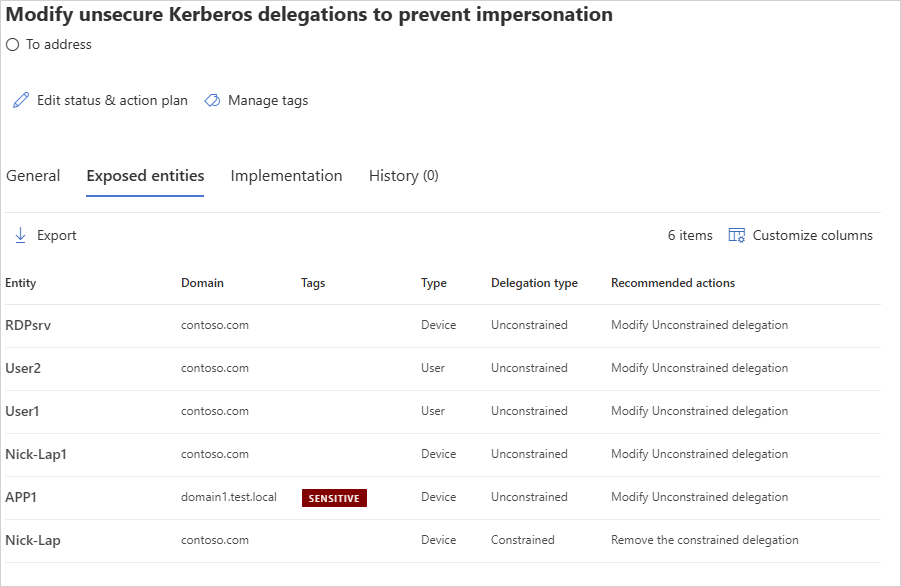
Délégation contrainte basée sur les ressources (RBCD)
Passez en revue les utilisateurs sensibles répertoriés dans les recommandations et supprimez-les de la ressource. Pour plus d’informations sur la configuration de RBCD, consultez Configurer la délégation Kerberos contrainte (KCD) dans Microsoft Entra Domain Services.