Examiner les alertes de sécurité Defender pour Identity dans Microsoft Defender XDR
Remarque
Defender pour Identity n’est pas conçu pour servir de solution d’audit ou de journalisation qui capture chaque opération ou activité sur les serveurs sur lesquels le capteur est installé. Il capture uniquement les données requises pour ses mécanismes de détection et de recommandation.
Cet article explique les principes de base de l’utilisation des alertes de sécurité Microsoft Defender pour Identity dans Microsoft Defender XDR.
Les alertes Defender pour Identity sont intégrées en mode natif à Microsoft Defender XDR avec un format de page d’alerte d’identité dédié.
La page Alerte d’identité offre aux clients Microsoft Defender pour Identity un meilleur enrichissement des signaux inter-domaines et de nouvelles fonctionnalités de réponse d’identité automatisées. Il garantit votre sécurité et contribue à améliorer l’efficacité de vos opérations de sécurité.
L’un des avantages de l’examen des alertes via Microsoft Defender XDR est que Microsoft Defender pour Identity alertes sont davantage corrélées avec les informations obtenues à partir de chacun des autres produits de la suite. Ces alertes améliorées sont cohérentes avec les autres formats d’alerte Microsoft Defender XDR provenant de Microsoft Defender pour Office 365 et Microsoft Defender pour point de terminaison. La nouvelle page élimine efficacement la nécessité d’accéder à un autre portail produit pour examiner les alertes associées à l’identité.
Les alertes provenant de Defender pour Identity peuvent désormais déclencher les fonctionnalités d’investigation et de réponse automatisées (AIR) Microsoft Defender XDR, y compris la correction automatique des alertes et l’atténuation des outils et des processus qui peuvent contribuer à l’activité suspecte.
Importante
Dans le cadre de la convergence avec Microsoft Defender XDR, certaines options et détails ont changé à partir de leur emplacement dans le portail Defender pour Identity. Lisez les détails ci-dessous pour découvrir où trouver les fonctionnalités familières et nouvelles.
Passer en revue les alertes de sécurité
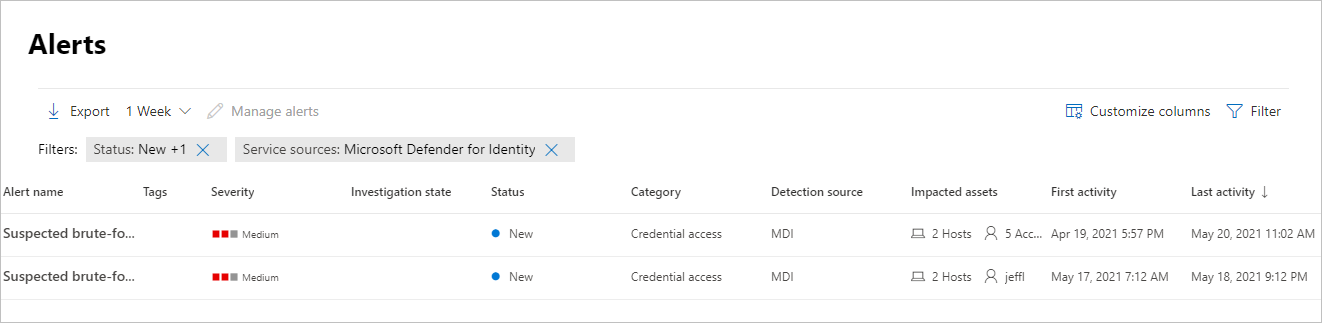
Les alertes sont accessibles à partir de plusieurs emplacements, notamment la page Alertes , la page Incidents , les pages des appareils individuels et la page Repérage avancé . Dans cet exemple, nous allons examiner la page Alertes.
Dans Microsoft Defender XDR, accédez à Incidents & alertes, puis à Alertes.
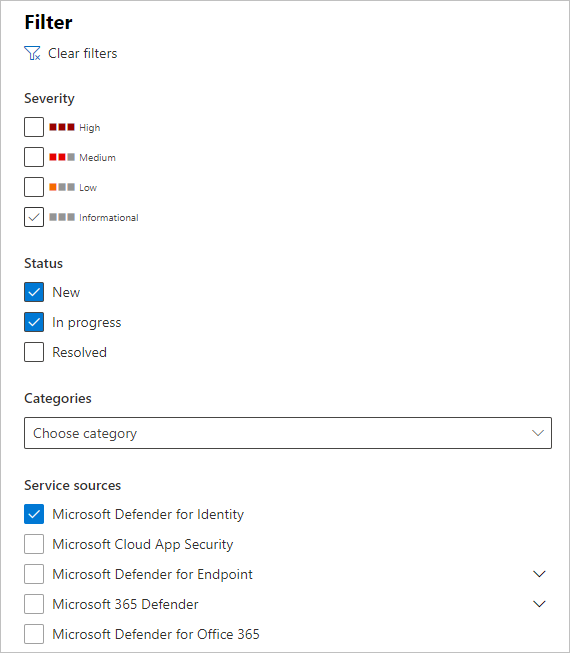
Pour afficher les alertes de Defender pour Identity, en haut à droite, sélectionnez Filtrer, puis sous Sources de service, sélectionnez Microsoft Defender pour Identity, puis Sélectionnez Appliquer :
Les alertes sont affichées avec des informations dans les colonnes suivantes : Nom de l’alerte, Étiquettes, Gravité, État de l’examen, État, Catégorie, Source de détection, Ressources impactées, Première activité et Dernière activité.
Catégories d’alertes de sécurité
Les alertes de sécurité Defender pour Identity sont divisées en catégories ou phases suivantes, comme les phases observées dans une chaîne de destruction de cyberattaque classique.
- Alertes de reconnaissance
- Alertes d’informations d’identification compromises
- Alertes de mouvement latéral
- Alertes de dominance de domaine
- Alertes d’exfiltration
Gérer des alertes
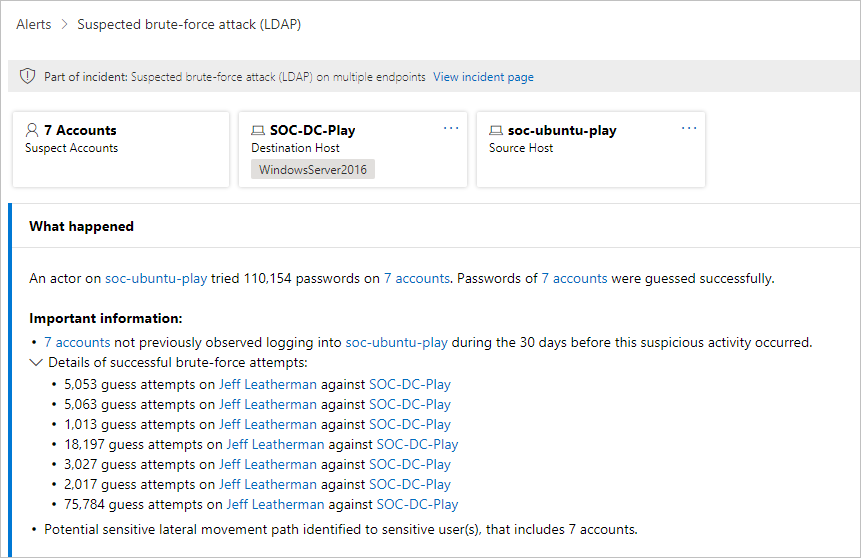
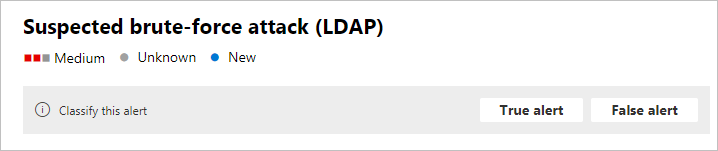
Si vous sélectionnez le nom de l’alerte pour l’une des alertes, vous accédez à la page avec des détails sur l’alerte. Dans le volet gauche, vous verrez un résumé de ce qui s’est passé :
Au-dessus de la zone Ce qui s’est passé se trouvent des boutons pour les comptes, l’hôte de destination et l’hôte source de l’alerte. Pour d’autres alertes, vous pouvez voir des boutons pour plus d’informations sur les hôtes, comptes, adresses IP, domaines et groupes de sécurité supplémentaires. Sélectionnez l’une d’entre elles pour obtenir plus de détails sur les entités impliquées.
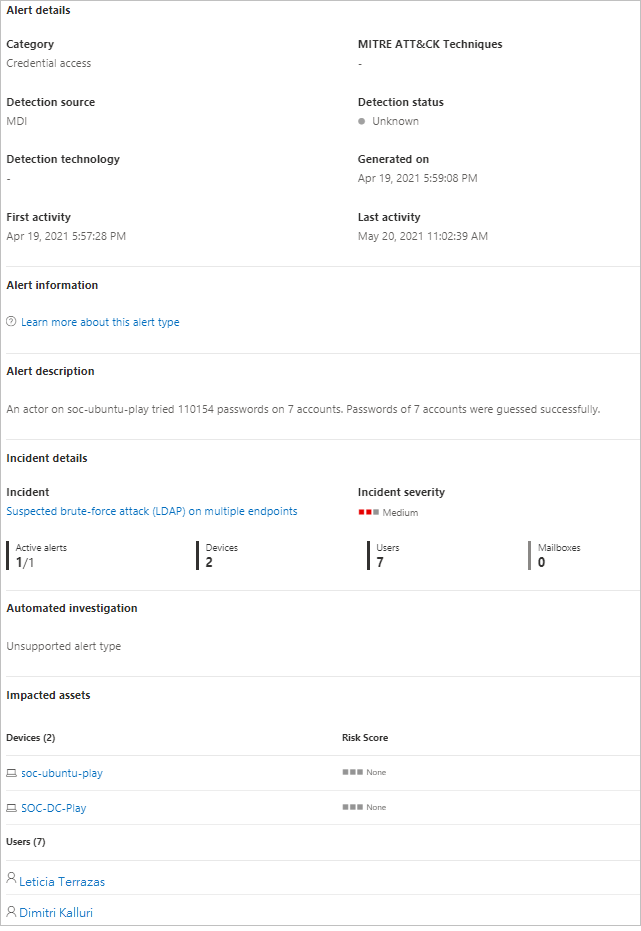
Dans le volet droit, vous verrez les détails de l’alerte. Ici, vous pouvez voir plus de détails et effectuer plusieurs tâches :
Classifier cette alerte : ici, vous pouvez désigner cette alerte en tant qu’alerte True ou False
État de l’alerte : dans Définir la classification, vous pouvez classifier l’alerte comme True ou False. Dans Affecté à, vous pouvez attribuer l’alerte à vous-même ou annuler son affectation.
Détails de l’alerte : sous Détails de l’alerte, vous pouvez trouver plus d’informations sur l’alerte spécifique, suivre un lien vers la documentation sur le type d’alerte, voir à quel incident l’alerte est associée, passer en revue toutes les investigations automatisées liées à ce type d’alerte et voir les appareils et les utilisateurs concernés.
Commentaires & l’historique : vous pouvez ici ajouter vos commentaires à l’alerte et voir l’historique de toutes les actions associées à l’alerte.
Gérer l’alerte : si vous sélectionnez Gérer l’alerte, vous accédez à un volet qui vous permettra de modifier :
État : vous pouvez choisir Nouveau, Résolu ou En cours.
Classification : vous pouvez choisir Alerte true ou False alert.
Commentaire : vous pouvez ajouter un commentaire sur l’alerte.
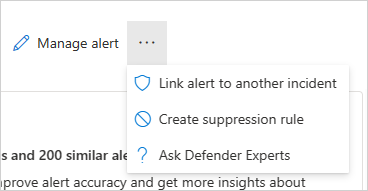
Si vous sélectionnez les trois points en regard de Gérer l’alerte, vous pouvez lier l’alerte à un autre incident, Créer une règle de suppression (disponible uniquement pour les clients en préversion) ou Demander aux experts Defender.
Vous pouvez également exporter l’alerte dans un fichier Excel. Pour ce faire, sélectionnez Exporter.
Remarque
Dans le fichier Excel, vous avez maintenant deux liens disponibles : Afficher dans Microsoft Defender pour Identity et Afficher dans Microsoft Defender XDR. Chaque lien vous amène au portail approprié et fournit des informations sur l’alerte.
Paramétrage des alertes
Paramétrez vos alertes pour les ajuster et les optimiser, ce qui réduit les faux positifs. Le réglage des alertes permet à vos équipes SOC de se concentrer sur les alertes de haute priorité et d’améliorer la couverture de la détection des menaces dans votre système. Dans Microsoft Defender XDR, créez des conditions de règle basées sur des types de preuves, puis appliquez votre règle à tout type de règle qui correspond à vos conditions.
Pour plus d’informations, consultez Régler une alerte.
Voir aussi
En savoir plus
- Essayez notre guide interactif : Détecter les activités suspectes et les attaques potentielles avec Microsoft Defender pour Identity