Tester la connectivité Microsoft Defender pour Identity
Le capteur Defender pour Identity nécessite une connectivité réseau au service Defender pour Identity, et la plupart des organisations contrôlent l’accès à Internet via un pare-feu ou des proxys. Par exemple, lorsque vous utilisez un proxy, vous pouvez autoriser l’accès au port 443 via une seule URL. Pour plus d’informations, consultez Ports requis.
Après avoir préparé le serveur que vous allez utiliser pour votre capteur Microsoft Defender pour Identity et configuré les paramètres de proxy en fonction des besoins, nous vous recommandons de tester la connectivité pour vous assurer que votre serveur peut accéder au service cloud Defender pour Identity. Utilisez les procédures décrites dans cet article même après le déploiement si votre serveur de capteur rencontre des problèmes de connectivité.
Pour plus d’informations, consultez Ports requis.
Remarque
Pour obtenir le nom et d’autres détails importants sur votre espace de travail Defender pour Identity, consultez la page À propos de dans le portail Microsoft Defender XDR.
Tester la connectivité à l’aide d’un navigateur
Ouvrez un navigateur. Si vous utilisez un proxy, vérifiez que votre navigateur utilise les mêmes paramètres de proxy que le capteur.
Par exemple, si les paramètres de proxy sont définis pour le système local, vous devez utiliser PSExec pour ouvrir une session en tant que système local et ouvrir le navigateur à partir de cette session.
Accédez à l’URL suivante :
https://<your_workspace_name>sensorapi.atp.azure.com/tri/sensor/api/ping. Remplacez par<your_workspace_name>le nom de votre espace de travail Defender pour Identity.Importante
Vous devez spécifier
HTTPS, et nonHTTP, pour tester correctement la connectivité.
Résultat : un message Ok doit s’afficher (HTTP status 200), qui indique que vous avez réussi à router vers le point de terminaison HTTPS Defender pour Identity. Il s’agit du résultat souhaité.
Pour certains espaces de travail plus anciens, le message retourné peut être Erreur 503 Le service n’est pas disponible. Il s’agit d’un état temporaire qui indique toujours la réussite. Par exemple :
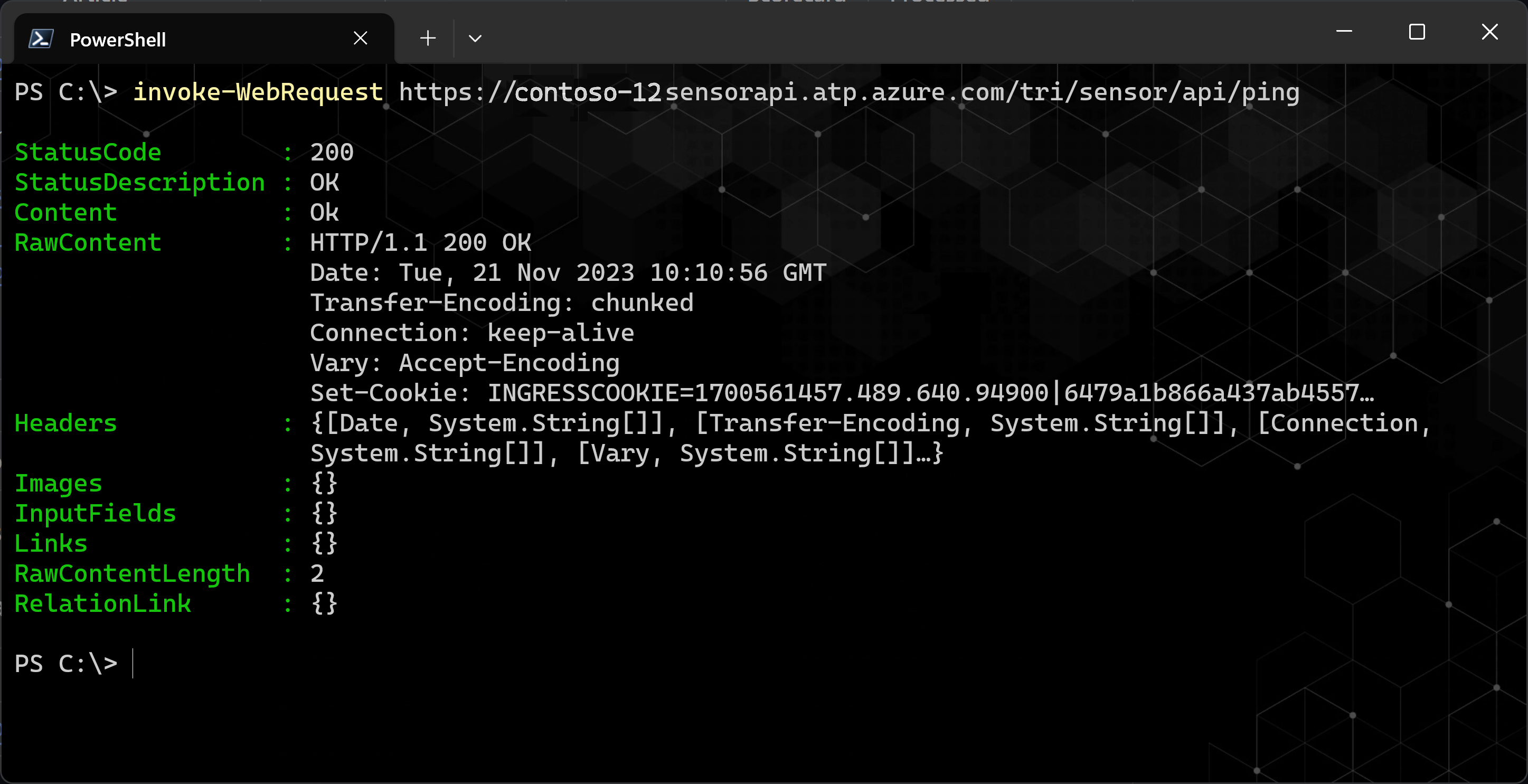
D’autres résultats peuvent inclure les scénarios suivants :
Si vous ne recevez pas le message Ok , vous pouvez rencontrer un problème avec la configuration de votre proxy. Vérifiez vos paramètres réseau et proxy.
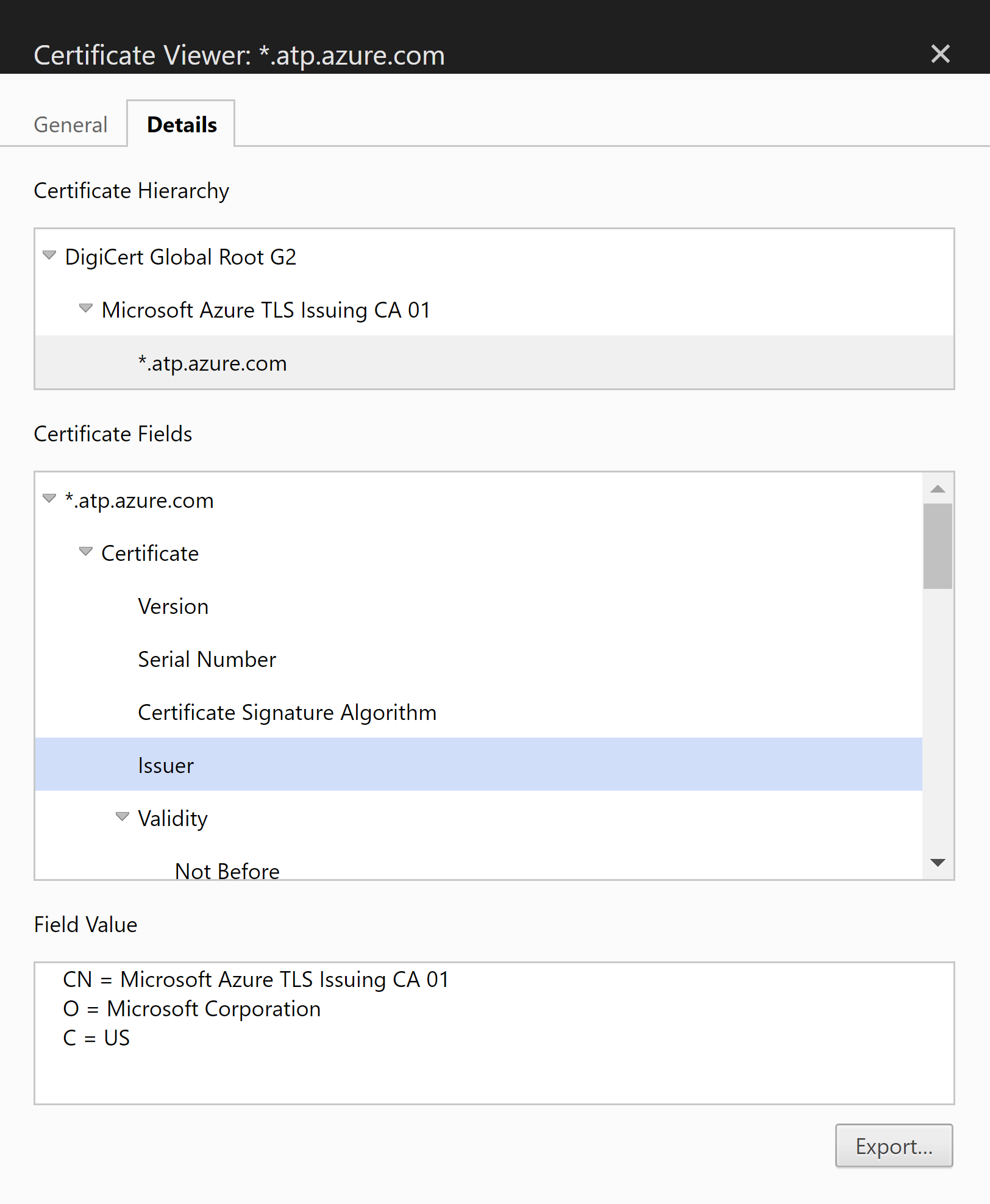
Si vous obtenez une erreur de certificat, vérifiez que les certificats racines approuvés requis sont installés avant de continuer. Pour plus d’informations, consultez Le problème d’authentification proxy se présente comme une erreur de connexion. Les détails du certificat doivent ressembler à ceci :
Tester la connectivité du service à l’aide de PowerShell
Prérequis : avant d’exécuter les commandes PowerShell Defender pour Identity, assurez-vous que vous avez téléchargé le module PowerShell Defender pour Identity.
Connectez-vous à votre serveur et exécutez l’une des commandes suivantes :
Pour utiliser les paramètres du serveur actuel, exécutez :
Test-MDISensorApiConnectionPour tester les paramètres que vous envisagez d’utiliser, mais qui ne sont pas actuellement configurés sur le serveur, exécutez la commande à l’aide de la syntaxe suivante :
Test-MDISensorApiConnection -BypassConfiguration -SensorApiUrl 'https://contososensorapi.atp.azure.com' -ProxyUrl 'https://myproxy.contoso.com:8080' -ProxyCredential $credentialOù :
-
https://contososensorapi.atp.azure.comest un exemple d’URL de votre capteur, où contososensor est le nom de votre espace de travail. -
https://myproxy.contoso.com:8080est un exemple d’URL de votre proxy
-
Pour plus d’informations, consultez la documentation MDI PowerShell.