Utiliser le tableau de bord ITDR de Defender pour Identity
La page Tableau de bord Microsoft Defender pour Identity affiche des données pour vous aider à mieux analyser votre posture de sécurité, à comprendre dans quelle mesure vous êtes protégé, à identifier les vulnérabilités et à effectuer les actions recommandées.
Utilisez la page Tableau de bord pour afficher des insights critiques et des données en temps réel sur la détection et la réponse aux menaces d’identité (ITDR). Affichez des graphiques et des widgets qui présentent des informations importantes relatives à l’accès non autorisé, à la compromission de compte, aux menaces internes et aux activités anormales, puis surveillez et gérez de manière proactive les risques potentiels liés à la sécurité liés à l’identité.
Configuration requise
Pour accéder à ce nouveau tableau de bord, vous avez besoin des éléments suivants :
Une licence Microsoft Defender pour Identity et une licence Entra ID Identity Protection
Un rôle d’utilisateur avec au moins les autorisations Lecteur de sécurité
Pour afficher une liste complète des recommandations et sélectionner tous les liens d’action recommandés, vous avez besoin du rôle Administrateur général .
Importante
Microsoft vous recommande d’utiliser des rôles disposant du moins d’autorisations. Cela contribue à renforcer la sécurité de votre organisation. Administrateur général est un rôle hautement privilégié qui doit être limité aux scénarios où vous ne pouvez pas utiliser un rôle existant.
Accéder au tableau de bord
Pour accéder au tableau de bord, connectez-vous à Microsoft 365 Defender et sélectionnez Tableau de bord identités>.
Par exemple :
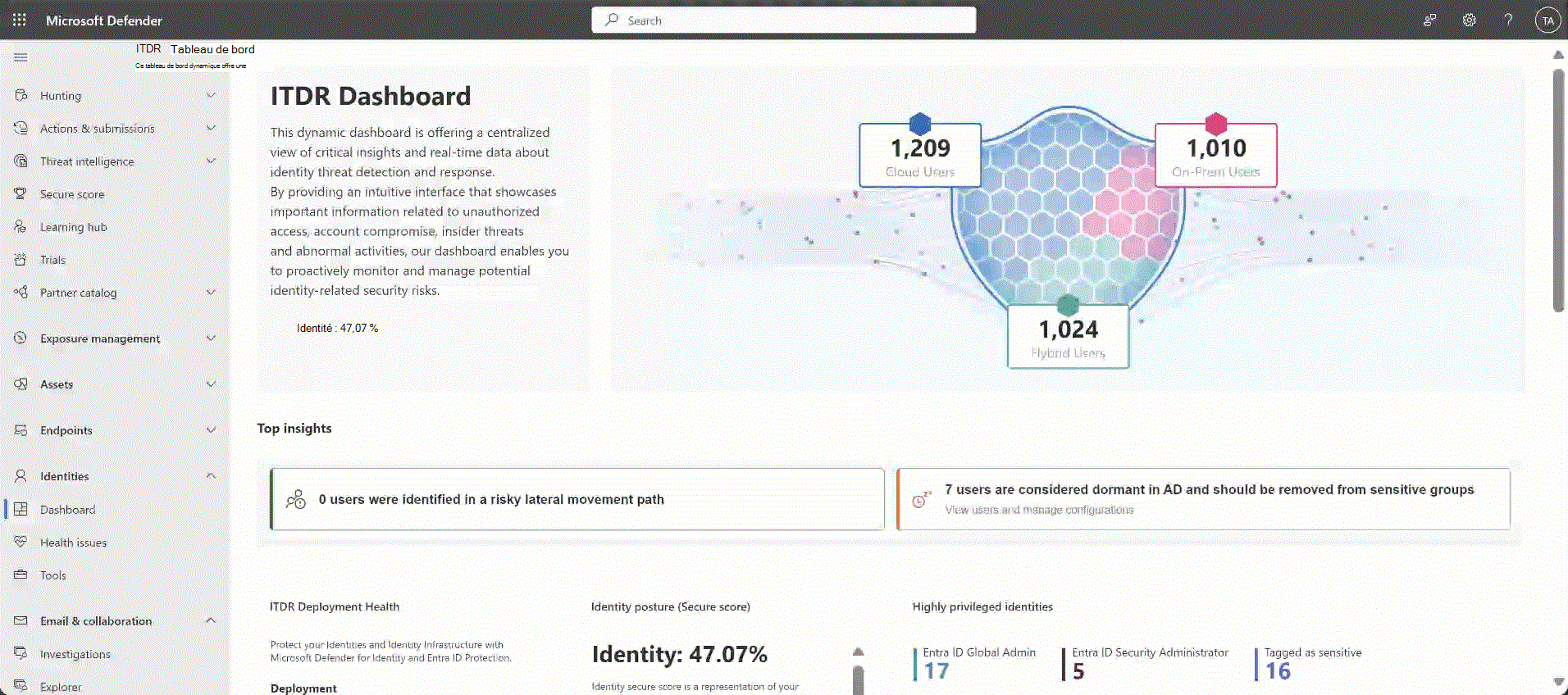
Informations de référence sur les widgets de tableau de bord
Cette section décrit les graphiques et widgets disponibles sur le tableau de bord ITDR.
Sélectionnez des liens dans les cartes pour accéder à plus de détails, tels que la documentation, les recommandations associées dans Microsoft Secure Score, etc.
| Nom | Description |
|---|---|
| Vue d’ensemble des identités (widget Sheild) | Fournit une vue d’ensemble rapide du nombre d’utilisateurs dans des environnements hybrides, cloud et locaux (AD et Microsoft Entra ID). Cette fonctionnalité inclut des liens directs vers la plateforme Advanced Hunting, offrant des informations détaillées sur les utilisateurs à portée de main. |
|
Principaux insights / Utilisateurs identifiés dans un chemin de mouvement latéral à risque |
Indique tous les comptes sensibles avec des chemins de mouvement latéral à risque, qui sont des fenêtres d’opportunité pour les attaquants et peuvent exposer des risques. Nous vous recommandons de prendre des mesures sur tous les comptes sensibles trouvés avec des chemins de mouvement latéral à risque pour réduire vos risques. Pour plus d’informations, consultez Comprendre et examiner les chemins de mouvement latéral (LPM) avec Microsoft Defender pour Identity. |
|
Principaux insights / Utilisateurs Active Directory dormants qui doivent être supprimés des groupes sensibles |
Listes comptes qui n’ont pas été utilisés pendant au moins 180 jours. Un chemin simple et silencieux dans votre organization consiste à passer par des comptes inactifs qui font partie de groupes sensibles. Par conséquent, nous vous recommandons de supprimer ces utilisateurs des groupes sensibles. Pour plus d’informations, consultez Évaluation de la sécurité : chemins de mouvement latéral les plus risqués (LMP). |
| Intégrité du déploiement ITDR | Listes la progression du déploiement du capteur, les alertes d’intégrité et la disponibilité des licences. |
| Posture de l’identité (degré de sécurisation) | Le score affiché représente la posture de sécurité de votre organization avec un focus sur le score d’identité, reflétant l’état de sécurité collective de vos identités. Le score est automatiquement mis à jour en temps réel pour refléter les données affichées dans les graphiques et les actions recommandées. Microsoft Secure Score est mis à jour quotidiennement avec les données système avec de nouveaux points pour chaque action recommandée. Pour plus d’informations, consultez Microsoft Secure Score. |
| Entités à privilèges élevés | Listes un résumé des comptes sensibles dans votre organization, y compris les administrateurs de sécurité de l’ID Entra et les utilisateurs administrateurs généraux. |
| Incidents liés à l’identité | Listes alertes de Defender pour Identity et de Protection Microsoft Entra ID, ainsi que tous les incidents pertinents correspondants des 30 derniers jours. |
| Domaines avec configuration non sécurisée | Listes domaines Active Directory qui ont des paramètres de configuration non sécurisés. Les domaines Active Directory contiennent de nombreuses configurations liées à la sécurité, qui, lorsqu’elles sont mal configurées, peuvent rendre les organisations plus vulnérables aux cyberattaques. Veillez à configurer vos domaines conformément aux bonnes pratiques de sécurité pour réduire la probabilité de compromission de l’identité. Pour plus d’informations, consultez Évaluation de la sécurité : configurations de domaine non sécurisé |
| Utilisateurs actifs de l’ID Entra à risque | Listes comptes d’utilisateur actifs qui peuvent être vulnérables aux menaces de sécurité, aux activités inhabituelles ou aux compromissions potentielles. L’identification et la gestion des utilisateurs à risque sont un aspect essentiel de la gestion d’un environnement informatique sécurisé. Pour plus d’informations, consultez Corriger les risques et débloquer les utilisateurs dans Protection Microsoft Entra ID. |
Étapes suivantes
Pour plus d’informations, consultez Microsoft Defender pour Identity dans Microsoft 365 Defender.