Ajouter la connexion avec le compte Microsoft Entra à une application web Spring
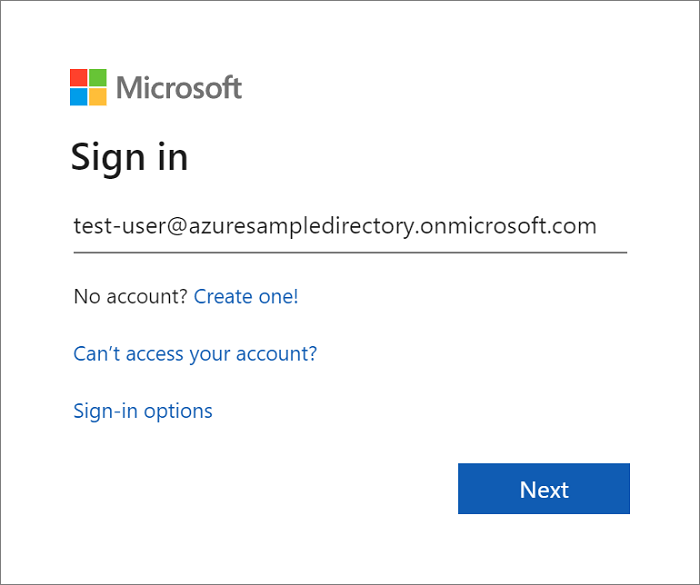
Cet article explique comment développer une application web Spring qui prend en charge la connexion par compte Microsoft Entra. Une fois toutes les étapes de cet article terminées, l’application web redirige vers la page de connexion Microsoft Entra lorsqu’elle est accessible anonymement. La capture d’écran suivante montre la page de connexion Microsoft Entra :
Conditions préalables
Les conditions préalables suivantes sont requises pour effectuer les étapes décrites dans cet article :
- Kit de développement Java (JDK) pris en charge. Pour plus d’informations sur les JDK disponibles lors du développement sur Azure, consultez prise en charge de Java sur Azure et Azure Stack.
- Apache Maven, version 3.0 ou ultérieure.
- Un abonnement Azure. Si vous n’avez pas d’abonnement Azure, créez un compte gratuit .
Important
Spring Boot version 2.5 ou ultérieure est nécessaire pour effectuer les étapes décrites dans cet article.
Créer une application à l’aide de Spring Initializr
Accédez à https://start.spring.io/.
Spécifiez que vous souhaitez générer un projet Maven avec Java, puis entrez les noms de Groupe et d’Artefact de votre application.
Ajoutez des dépendances pour Spring Web, Microsoft Entra IDet OAuth2 Client.
En bas de la page, sélectionnez le bouton GÉNÉRER.
Lorsque vous y êtes invité, téléchargez le projet dans un emplacement défini par un chemin d’accès sur votre ordinateur local.
Créer une instance Microsoft Entra
Créer l’instance Active Directory
Si vous êtes l’administrateur d’une instance existante, vous pouvez ignorer ce processus.
Connectez-vous à https://portal.azure.com.
Sélectionnez Tous les services, Identity, puis Microsoft Entra ID.
Entrez le nom de votre organisation et le nom de domaine initial . Copiez l’URL complète de votre répertoire. Vous utiliserez l’URL pour ajouter des comptes d’utilisateur plus loin dans ce didacticiel. (Par exemple :
azuresampledirectory.onmicrosoft.com.)Copiez l’URL complète de votre répertoire. Vous utiliserez l’URL pour ajouter des comptes d’utilisateur plus loin dans ce didacticiel. (Par exemple :
azuresampledirectory.onmicrosoft.com.).Lorsque vous avez terminé, sélectionnez Créer. La création de la ressource prend quelques minutes.
Lorsque vous avez terminé, sélectionnez le lien affiché pour accéder au nouveau répertoire.
Copiez l’ID de locataire . Vous utiliserez la valeur d’ID pour configurer votre fichier application.properties plus loin dans ce tutoriel.
Ajouter un enregistrement d'application pour votre application Spring Boot
Dans le menu du portail, sélectionnez enregistrements d’applications, puis Enregistrer une application.
Spécifiez votre application, puis sélectionnez Enregistrer.
Lorsque la page de l’inscription de votre application s’affiche, copiez votre ID d’application (client) et l’ID d’annuaire (locataire). Vous allez utiliser ces valeurs pour configurer votre fichier application.properties plus loin dans ce tutoriel.
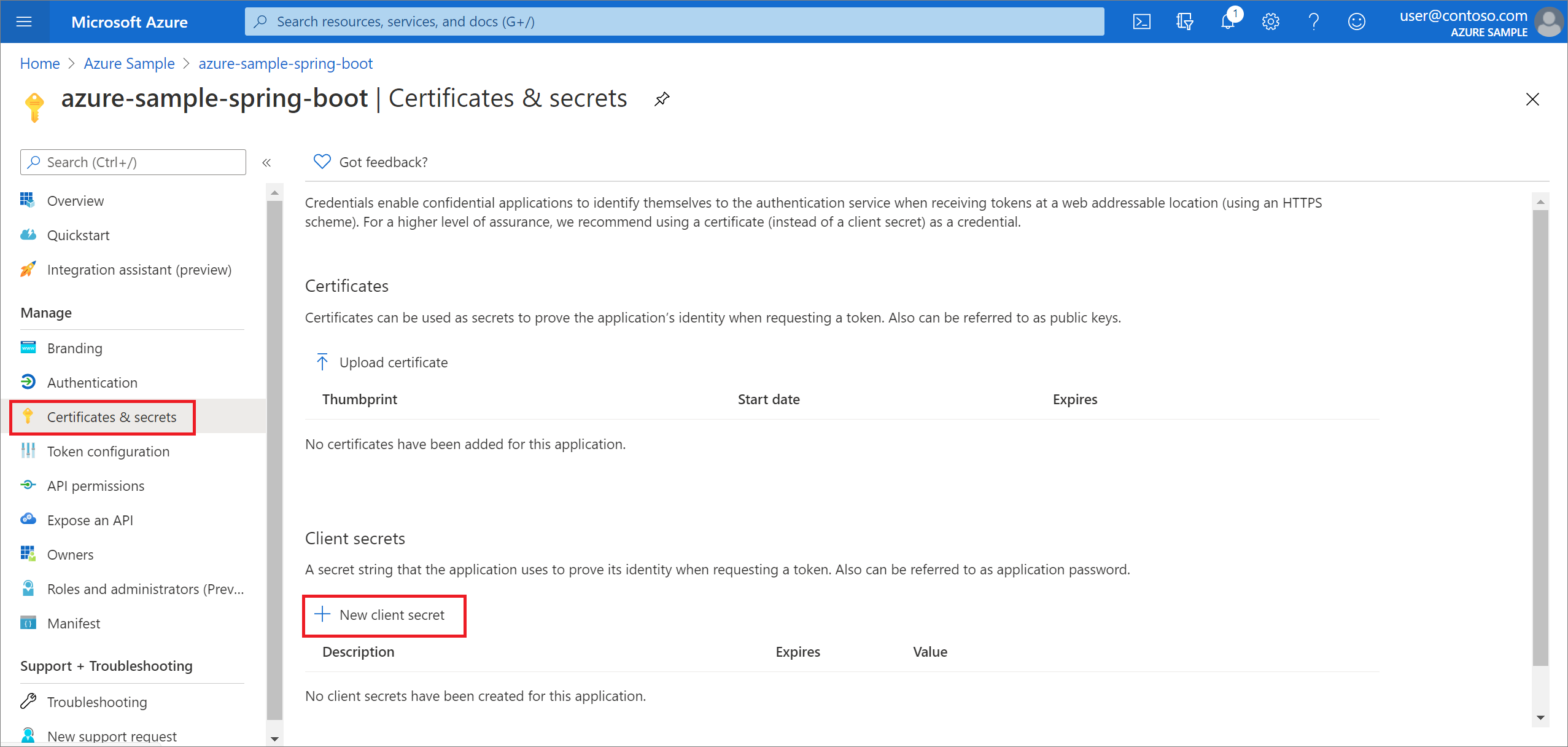
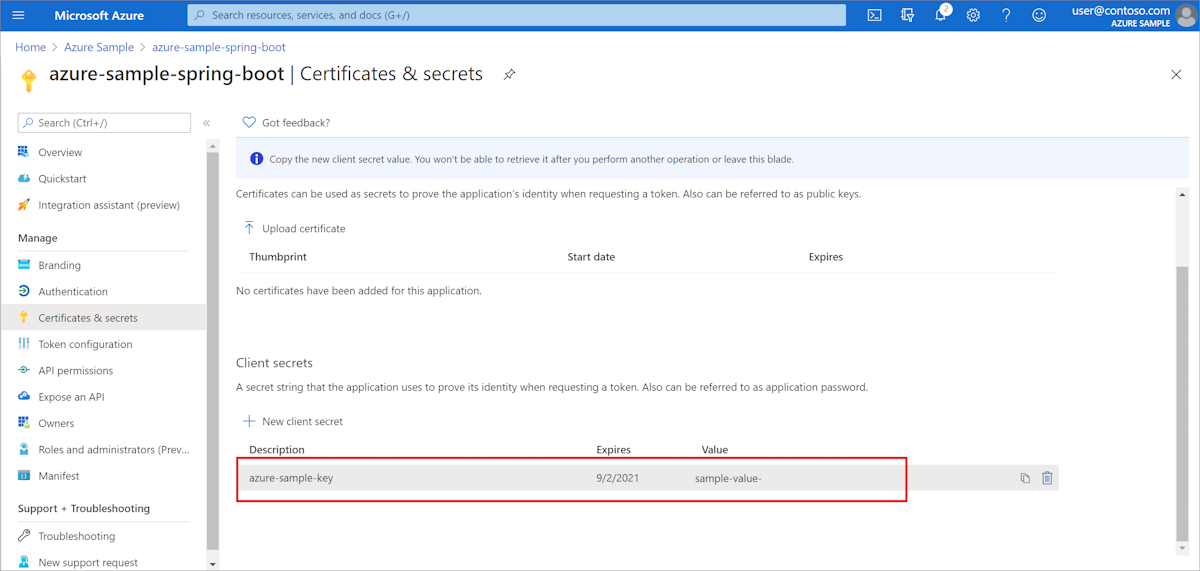
Dans le menu de navigation, sélectionnez Certificats et secrets. Sélectionnez ensuite nouveau secret client.
Ajoutez une description et sélectionnez une durée dans la liste Expire le. Sélectionnez Ajouter. La valeur de la clé est automatiquement renseignée.
Copiez et enregistrez la valeur de la clé secrète client pour configurer votre fichier application.properties plus loin dans ce tutoriel. (Vous ne pourrez pas récupérer cette valeur ultérieurement.)
Dans la page principale de l’inscription de votre application, sélectionnez Authentification, puis Ajouter une plateforme. Ensuite, sélectionnez Applications web.
Entrez
http://localhost:8080/login/oauth2/code/comme nouvel URI de redirection, puis sélectionnez Configurer.Si vous avez modifié le fichier pom.xml pour utiliser une version de démarrage de Microsoft Entra antérieure à 3.0.0 : sous Octroi implicite et flux hybrides, sélectionnez Jetons d’ID (utilisés pour les flux implicites et hybrides), puis Enregistrer.
Ajouter un compte d’utilisateur à votre annuaire et ajouter ce compte à un appRole
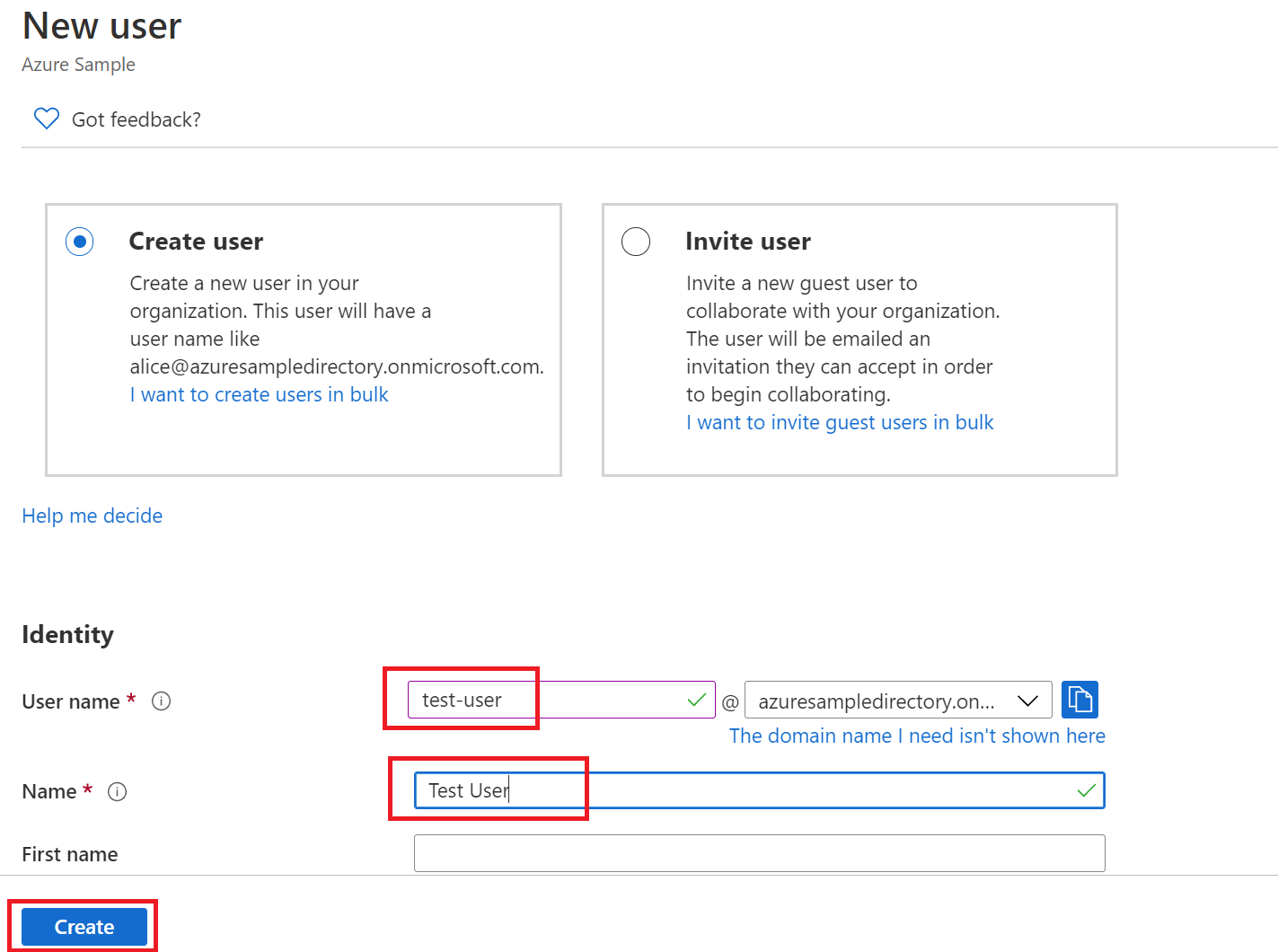
Dans la page Vue d’ensemble de votre annuaire Active Directory, sélectionnez Utilisateurs, puis Nouvel utilisateur.
Lorsque le panneau Utilisateur s’affiche, entrez le Nom d’utilisateur et le Nom. Sélectionnez ensuite Créer.
Remarque
Vous devez spécifier l’URL de votre répertoire précédemment dans ce didacticiel lorsque vous entrez le nom d’utilisateur. Par exemple:
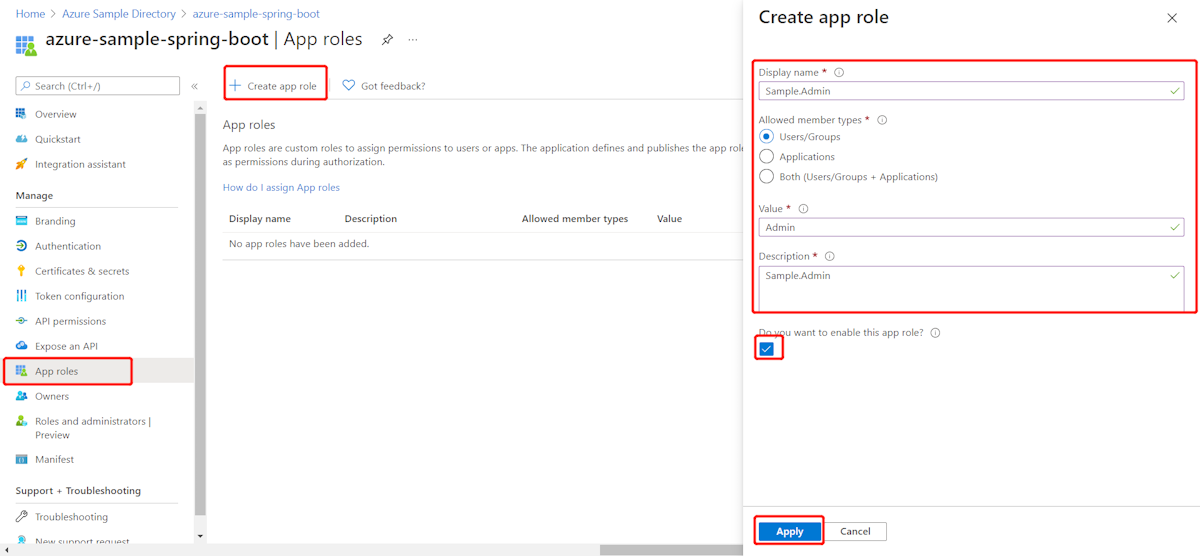
test-user@azuresampledirectory.onmicrosoft.comDans la page principale de l’inscription de votre application, sélectionnez rôles d’application, puis sélectionnez Créer un rôle d’application. Fournissez des valeurs pour les champs de formulaire, sélectionnez Voulez-vous activer ce rôle d’application ?, puis sélectionnez Appliquer.
À partir de la page Vue d’ensemble de votre annuaire Microsoft Entra, sélectionnez Applications d’entreprise.
Sélectionnez Toutes les applications, puis sélectionnez l’application à laquelle vous avez ajouté le rôle d’application à l’étape précédente.
Sélectionnez Utilisateurs et groupes, puis sélectionnez Ajouter unutilisateur/groupe.
Sous Utilisateurs, sélectionnez Aucun sélectionné. Sélectionnez l’utilisateur que vous avez créé précédemment, sélectionnez Ajouter, puis Attribuer. Si vous avez créé plusieurs rôles d’application précédemment, sélectionnez un rôle.
Revenez au panneau utilisateurs , sélectionnez votre utilisateur de test, puis sélectionnez Réinitialiser le mot de passe. Ensuite, copiez le mot de passe. Vous utiliserez le mot de passe lorsque vous vous connectez à votre application plus loin dans ce tutoriel.
Configurer et compiler votre application
Extrayez les fichiers de l’archive de projet que vous avez créée et téléchargée précédemment dans ce didacticiel dans un répertoire.
Accédez au dossier src/main/resources dans votre projet, puis ouvrez le fichier application.properties dans un éditeur de texte.
Spécifiez les paramètres de votre inscription d’application à l’aide des valeurs que vous avez créées précédemment. Par exemple:
# Enable related features. spring.cloud.azure.active-directory.enabled=true # Specifies your Active Directory ID: spring.cloud.azure.active-directory.profile.tenant-id=<tenant-ID> # Specifies your App Registration's Application ID: spring.cloud.azure.active-directory.credential.client-id=<client-ID> # Specifies your App Registration's secret key: spring.cloud.azure.active-directory.credential.client-secret=<client-secret>Où:
Paramètre Description spring.cloud.azure.active-directory.enabledActiver les fonctionnalités fournies par spring-cloud-azure-starter-active-directory spring.cloud.azure.active-directory.profile.tenant-idContient l’ID du répertoire d’Active Directory vu précédemment. spring.cloud.azure.active-directory.credential.client-idContient l’ID de l’application de votre inscription d’application exécutée précédemment. spring.cloud.azure.active-directory.credential.client-secretContient la Valeur de votre clé d’inscription d’application exécutée précédemment. Enregistrez et fermez le fichier application.properties.
Créez un dossier nommé contrôleur dans le dossier source Java de votre application. Par exemple : src/main/java/com/wingtiptoys/security/controller.
Créez un fichier Java nommé
HelloController.java dans le dossier du contrôleur deet ouvrez-le dans un éditeur de texte. Entrez le code suivant, puis enregistrez et fermez le fichier :
package com.wingtiptoys.security; import org.springframework.web.bind.annotation.GetMapping; import org.springframework.web.bind.annotation.ResponseBody; import org.springframework.web.bind.annotation.RestController; import org.springframework.security.access.prepost.PreAuthorize; @RestController public class HelloController { @GetMapping("Admin") @ResponseBody @PreAuthorize("hasAuthority('APPROLE_Admin')") public String Admin() { return "Admin message"; } }
Générer et tester votre application
Ouvrez une invite de commandes et remplacez le répertoire par le dossier où se trouve le fichier pom.xml de votre application.
Générez votre application Spring Boot avec Maven et exécutez-la. Par exemple:
mvn clean package mvn spring-boot:runUne fois votre application générée et démarrée par Maven, ouvrez
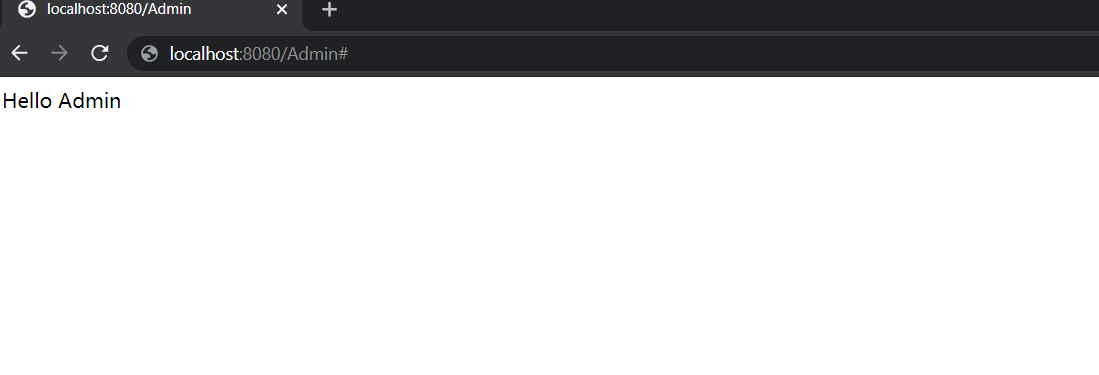
http://localhost:8080/Admindans un navigateur web. Vous devez être invité à entrer un nom d’utilisateur et un mot de passe.
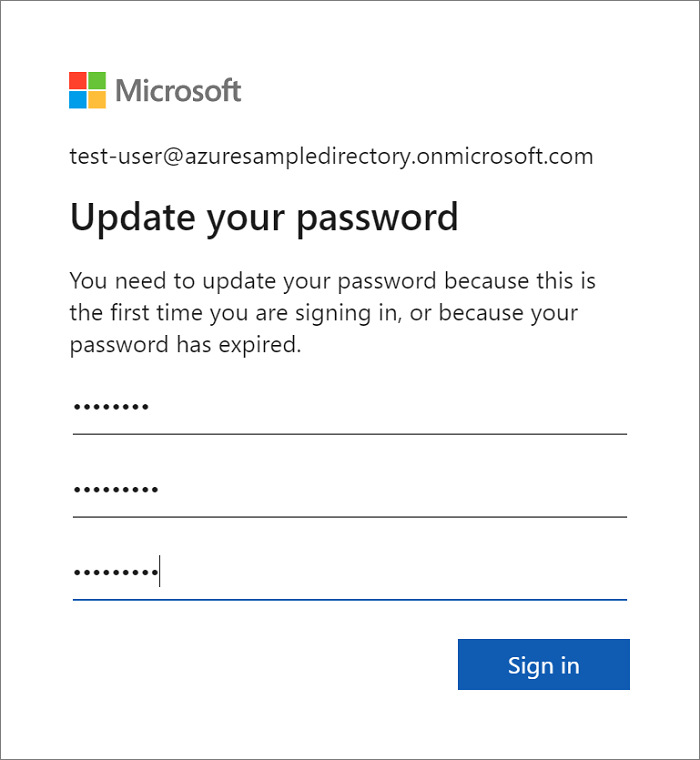
Remarque
Vous pouvez être invité à modifier votre mot de passe s’il s’agit de la première connexion d’un nouveau compte d’utilisateur.
Une fois connecté, vous devez voir l’exemple de texte « Message administrateur » du contrôleur.
Résumé
Dans ce tutoriel, vous avez créé une application web Java à l’aide du démarrage Microsoft Entra, configuré un nouveau locataire Microsoft Entra, inscrit une nouvelle application dans le locataire, puis configuré votre application pour utiliser les annotations et classes Spring pour protéger l’application web.
Voir aussi
- Pour plus d’informations sur les nouvelles options d’interface utilisateur, consultez Guide de formation sur l’inscription des applications du portail Azure
Étapes suivantes
Pour en savoir plus sur Spring et Azure, passez au centre de documentation Spring sur Azure.