Tutoriel : Migrer WebLogic Server vers Azure avec Elastic sur Azure comme solution de journalisation
Dans ce tutoriel, vous déployez WebLogic Server (WLS) sur des machines virtuelles Azure et intégrez Elastic Cloud (Elasticsearch). Vous configurez également les Elastic Custom Logs pour capturer les données de journal à partir de WLS. Enfin, vous utilisez Kibana pour rechercher et analyser les logs WLS. Bien que chaque composant soit documenté individuellement, ce tutoriel montre comment ils s’intègrent en toute transparence pour fournir une solution de gestion des journaux robuste pour WLS sur Azure.
Dans ce tutoriel, vous allez apprendre à :
- Créez une instance Elastic sur Azure.
- Déployez WLS sur Azure.
- Configurer Elastic Custom Logs pour intégrer les journaux de WLS.
- Effectuer des recherches dans les journaux de WebLogic Server à partir de Kibana.
Conditions préalables
- Un abonnement Azure actif. Si vous n’avez pas d’abonnement Azure, créer un compte gratuit.
- La possibilité de déployer l’une des applications Azure WLS sur des machines virtuelles répertoriées dans Quelles sont les solutions pour l’exécution d’Oracle WebLogic Server sur des machines virtuelles Azure ?
- Terminal pour l’accès SSH aux machines virtuelles.
Déployer WLS sur Azure
Provisionnez WebLogic Server en suivant les étapes décrites dans Quelles sont les solutions pour l’exécution d’Oracle WebLogic Server sur des machines virtuelles Azure ? « Déployer Oracle WebLogic Server avec le serveur d’administration sur un nœud unique » et « Déployer un cluster Oracle WebLogic Server sur Microsoft Azure IaaS » sont compatibles avec Elastic sur Azure. Ce didacticiel utilise WebLogic sur la machine virtuelle comme exemple.
Remarque
La taille de machine virtuelle par défaut peut ne pas avoir suffisamment de mémoire pour l’agent élastique. Vérifiez que la taille de machine virtuelle sélectionnée a au moins 2,5 Go de mémoire. Standard_A2_v2 est la taille minimale suffisante
Après avoir renseigné les informations requises, sélectionnez Créer pour lancer le déploiement WLS sur Azure. Le déploiement prend généralement environ 30 minutes. Après le déploiement, accédez à Sorties et enregistrez la valeur de adminConsoleURL, qui est l’URL d’accès à la console d’administration.
Comprendre les logs WebLogic
Les sous-systèmes WebLogic Server utilisent des services de journalisation pour suivre les événements tels que le déploiement d’applications et les défaillances du sous-système. Ces journaux permettent aux instances de serveur de communiquer leur état et de répondre à des événements spécifiques, fournissant des informations détaillées qui peuvent vous aider à résoudre les problèmes et à surveiller. Les services de journalisation de WebLogic vous permettent de signaler des erreurs, d’écouter les messages de journalisation à partir de sous-systèmes particuliers et de capturer les mises à jour de l’état du système. Pour plus d’informations sur les services de journalisation WebLogic, consultez Understanding WebLogic Logging Services.
Ce tutoriel se concentre sur la configuration des journaux WebLogic clés suivants :
Fichiers journaux du serveur : généralement trouvés dans le répertoire de journaux à la racine de l’instance de serveur. Le chemin d’accès est généralement DOMAIN_NAME/servers/SERVER_NAME/logs/SERVER_NAME.log.
Fichiers journaux de domaine : ces journaux fournissent une vue d’ensemble de l’état du domaine et sont stockés dans le répertoire des journaux du serveur d’administration. Le chemin d’accès par défaut est DOMAIN_NAME/servers/ADMIN_SERVER_NAME/logs/DOMAIN_NAME.log.
Journaux d’accès HTTP : par défaut, les journaux d’accès HTTP partagent le répertoire et la stratégie de rotation du journal du serveur. Le chemin d’accès par défaut est DOMAIN_NAME/servers/SERVER_NAME/logs/1access.log.
Vous pouvez configurer et gérer ces journaux pour faciliter l’intégration à des outils de surveillance tels qu’Elastic sur Azure, ce qui permet d’analyser et d’alerter les journaux centralisés sur les instances WebLogic Server.
Pendant le déploiement de l'offre, vous pouvez passer directement aux étapes de la section Créer une instance Elasticsearch on Azure. Revenez ici lorsque le déploiement de l'offre est terminé.
Se connecter à la machine WLS
Pour accéder à la machine virtuelle exécutant WebLogic Server (WLS), suivez les étapes décrites dans Se connecter à la machine virtuelle. Dans ce tutoriel, vous vous connectez à l’ordinateur qui héberge le serveur d’administration WebLogic, nommé adminVM.
Créer une instance Elasticsearch sur Azure
Elastic Cloud (Elasticsearch) pour Azure est un azure Native ISV Services que vous pouvez obtenir à partir de la Place de marché Azure et déployer avec le portail Azure. Azure Native ISV Services vous permet de provisionner, de gérer et d’intégrer facilement des logiciels et des services indépendants de fournisseur de logiciels (ISV) sur Azure. Elastic Cloud - Azure Native ISV Service est développé et géré par Microsoft et Elastic. Vous créez, approvisionnez et gérez des ressources élastiques via le portail Azure. Elastic possède et exécute l’application SaaS, y compris les comptes élastiques créés. Pour obtenir une vue d’ensemble de Elastic Cloud (Elasticsearch) consultez Qu’est-ce que Elastic Cloud (Elasticsearch) - Un service ISV natif Azure ?
Créer Elastic sur Azure
Pour créer une application Élastique, suivez les étapes décrites dans Démarrage rapide : Prise en main d’Elastic.
Dans la première étape de la section Créer une ressource, procédez comme suit pour les substitutions :
Dans le volet Informations de base, sous Détails du plan, procédez comme suit :
- Pour groupe de ressources, renseignez un nom de groupe de ressources unique. Ce didacticiel utilise
elkrg1030. - Pour nom de ressource, renseignez un nom unique pour votre instance Elastic. Vous pouvez utiliser la même valeur que celle utilisée pour groupe de ressources.
- Pour région, sélectionnez votre région souhaitée.
- Conservez les valeurs par défaut pour d’autres champs.
- Pour groupe de ressources, renseignez un nom de groupe de ressources unique. Ce didacticiel utilise
Dans le volet de mesure des& journaux d'activité, sélectionnez Envoyer les journaux d'activité des abonnements et Envoyer les journaux des ressources Azure pour toutes les ressources définies afin de surveiller les ressources Azure. Toutefois, ce didacticiel se concentre uniquement sur les journaux WLS et ne couvre pas les journaux d’infrastructure.
Vous pouvez sauter les sections Configuration d'Azure OpenAI et Balises.
Suivez les étapes restantes de l’article.
Une fois le déploiement réussi, passez à la section suivante de cet article.
Lancer Kibana
Une fois Elastic déployé sur Azure, ouvrez la ressource Élastique à partir du portail Azure. Recherchez l’URL Kibana, à côté de l’étiquette URL de déploiement, comme illustré dans la capture d’écran suivante :
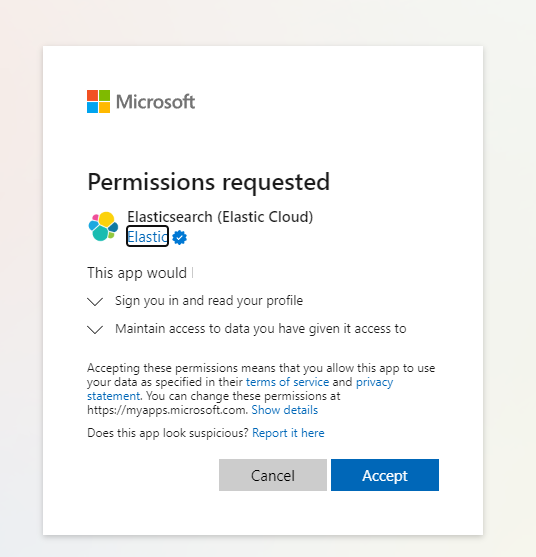
Lorsque vous lancez Kibana, vous êtes invité à vous connecter en sélectionnant un compte Azure. Choisissez le compte Azure utilisé pour créer le déploiement Élastique, puis passez en revue et acceptez les autorisations Elasticsearch demandées.
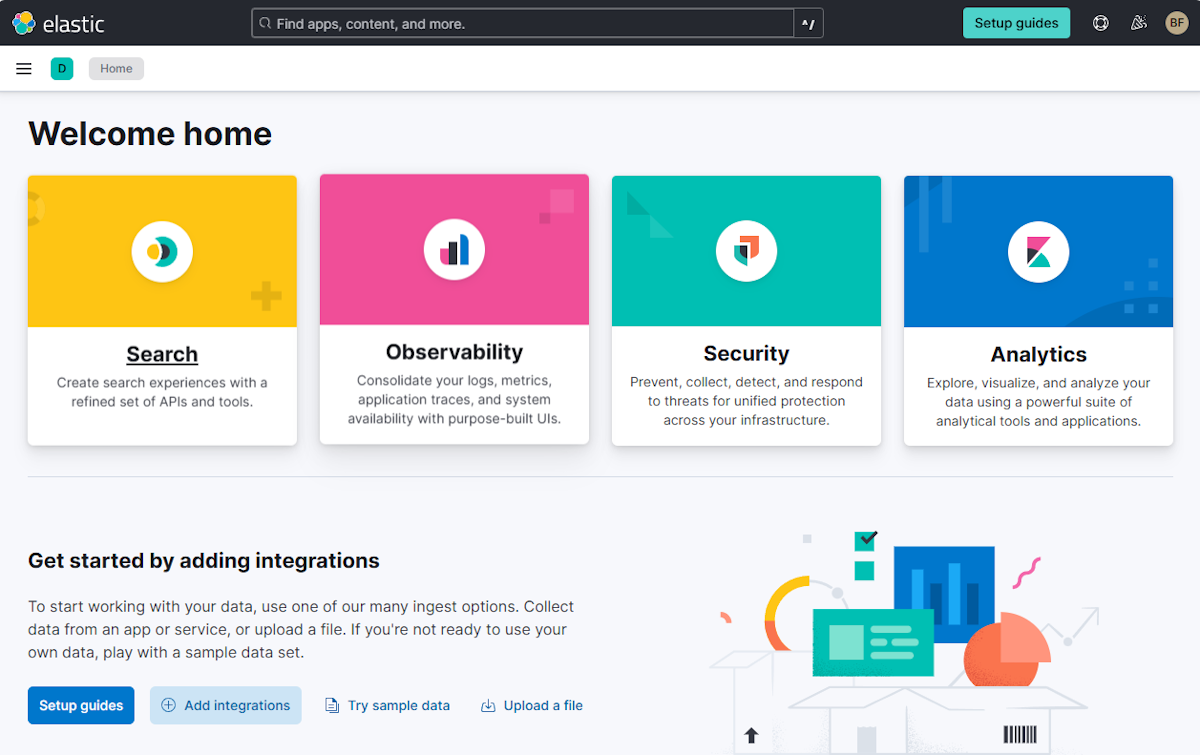
Une fois connecté, le navigateur accède à la page d’accueil de Kibana, comme illustré dans la capture d’écran suivante :
Configurer des journaux personnalisés élastiques et intégrer des journaux WLS
Suivez les étapes suivantes pour configurer l'intégration des journaux personnalisés pour WebLogic Server sur Kibana :
Pour accéder à la configuration de l’intégration de Kibana, procédez comme suit :
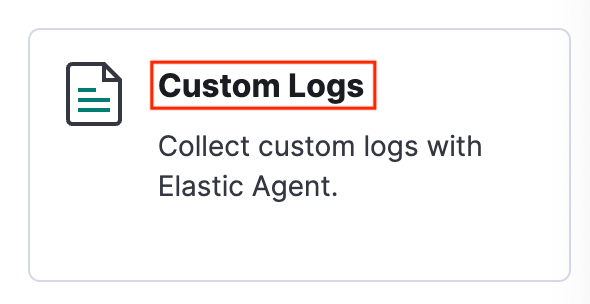
Dans la page d’accueil Kibana, recherchez Commencer en ajoutant des intégrations, puis sélectionnez Ajouter des intégrations.
Recherchez les journaux personnalisés et sélectionnez-les.
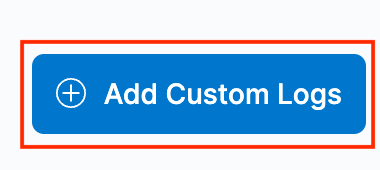
Sélectionnez Ajouter des journaux personnalisés pour afficher les instructions d’installation de l’agent élastique et l’ajout d’intégrations.
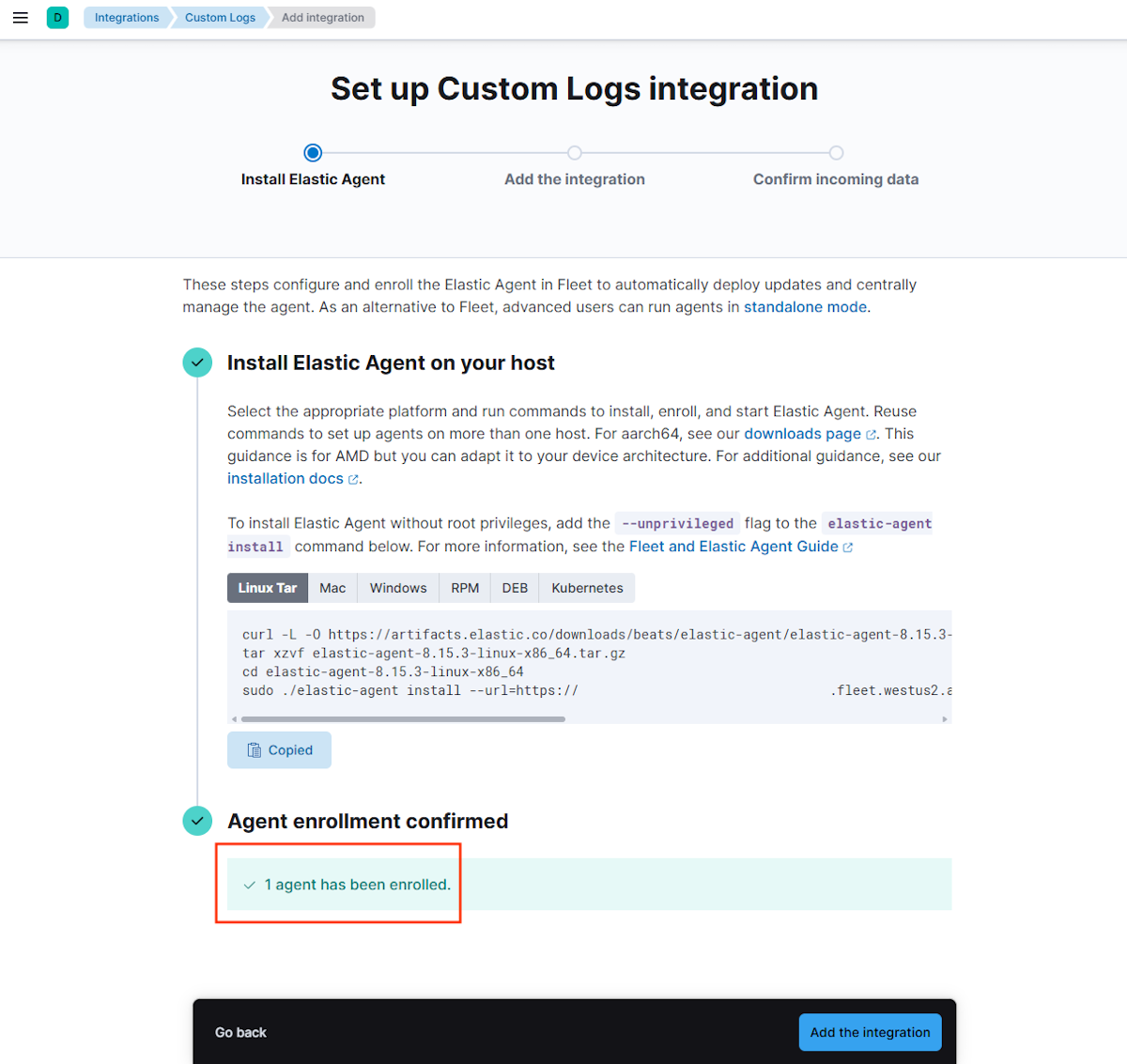
Procédez comme suit pour installer l’agent élastique :
Sélectionnez Installer l’agent élastique, ce qui affiche les étapes d’installation.
Connectez-vous à la machine WLS, puis basculez vers les privilèges racines à l’aide de la commande suivante :
sudo su -À partir de Kibana, copiez la commande Linux Tar de la section Installez Elastic Agent sur votre machine hôte et exécutez-la sur la machine WLS.
Dans le terminal de l’ordinateur, confirmez l’installation en entrant y lorsque vous y êtes invité, comme illustré dans l’exemple suivant :
Elastic Agent will be installed at /opt/Elastic/Agent and will run as a service. Do you want to continue? [Y/n]:yRecherchez le texte
Elastic Agent has been successfully installed.Ce texte indique une installation réussie. Si vous ne voyez pas ce texte, dépannez et résolvez le problème avant de continuer.
Vérifiez l’inscription de l’agent. Dans Kibana, confirmez l'inscription de l'agent sous Confirmation de l'inscription de l'agent.
Suivez les étapes ci-dessous pour ajouter l'intégration pour les journaux de domaine WLS :
Sélectionnez Ajouter l'intégration.
Sous fichier journal personnalisé, définissez les propriétés suivantes :
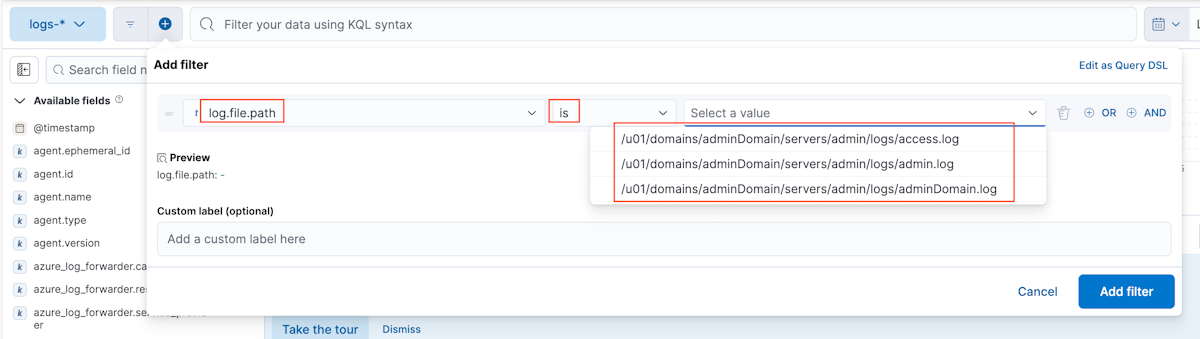
- Pour le chemin du fichier journal, utilisez /u01/domaines/adminDomain/servers/admin/logs/adminDomain.log.
- Pour le nom de l'ensemble de données, utilisez le nom générique.
Développer Options avancées. Pour les configurations personnalisées , définissez les propriétés suivantes :
- Pour multiligne.type , utilisez le modèle .
- Pour multiline.pattern, utilisez '^####' .
- Pour multiline.negate, utilisez true.
- Pour cmultiline.match, utilisez after.
Développez les options avancées . Pour le nom de l'intégration, remplissez log-weblogic-domain-log.
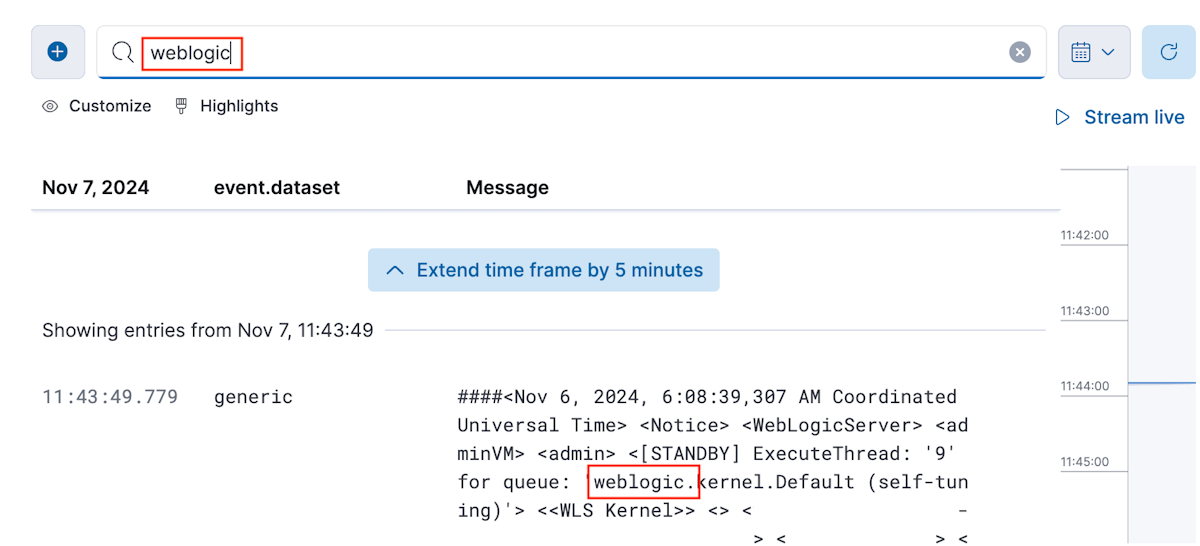
Sélectionnez Confirmer les données entrantes pour prévisualiser les journaux. Ensuite, sélectionnez Voir les ressources ->Ressources ->Points de vue ->Logs pour afficher les journaux du domaine dans Kibana.
Dans la zone de texte contenant le texte Rechercher les messages du journal, saisissez la chaîne weblogic et appuyez sur Entrée. Vous devriez voir des messages de journal contenant la chaîne de caractères weblogic.
Procédez comme suit pour ajouter des intégrations pour les journaux d’activité du serveur et les journaux d’accès HTTP :
Dans Kibana, recherchez Integrations et sélectionnez-le.
Sélectionnez Intégrations installées>Journaux personnalisé>sAjouter des journaux personnalisés.
Entrez les configurations appropriées dans les listes suivantes pour chaque type de journal - serveur et journaux d’accès HTTP. Après avoir renseigné tous les champs de configuration, sélectionnez Enregistrer et continuer puis Enregistrer et déployer les modifications.
Pour le journal du serveur, utilisez les valeurs suivantes :
Pour les paramètres d'intégration> Nom de l'intégration, utilisez log-weblogic-server-log.
Pour le fichier journal personnalisé> Chemin du fichier journal, utilisez /u01/domaines/adminDomain/servers/admin/logs/admin.log.
Pour fichier journal personnalisé > options avancées > configurations personnalisées, utilisez les valeurs suivantes :
- Pour le type de multiligne , utilisez le modèle .
- Pour multiline.pattern, utilisez '^####'.
- Pour multiline.negate, utilisez true.
- Pour cmultiline.match, utilisez after.
Pour Où ajouter cette intégration ? Pour les hôtes> existants, utilisez la stratégie Mon premier agent.
Pour les journaux d'accès HTTP, utilisez les valeurs suivantes :
- Pour les paramètres d'intégration> Nom de l'intégration, utilisez log-http-access-log.
- Pour le fichier journal personnalisé> Chemin du fichier journal, utilisez /u01/domaines/adminDomain/servers/admin/logs/access.log.
- Pour fichier journal personnalisé > options avancées > configurations personnalisées, aucune configuration n’est fournie.
- Pour Où ajouter cette intégration ? Pour les hôtes> existants, utilisez la stratégie Mon premier agent.
Rechercher les logs WLS dans Kibana
Après l'intégration, utilisez les étapes suivantes pour commencer à analyser les journaux dans Kibana :
Pour accéder à la page Découvrir, ouvrez le menu hamburger . Ensuite, sous Analytique, sélectionnez Découvrir.
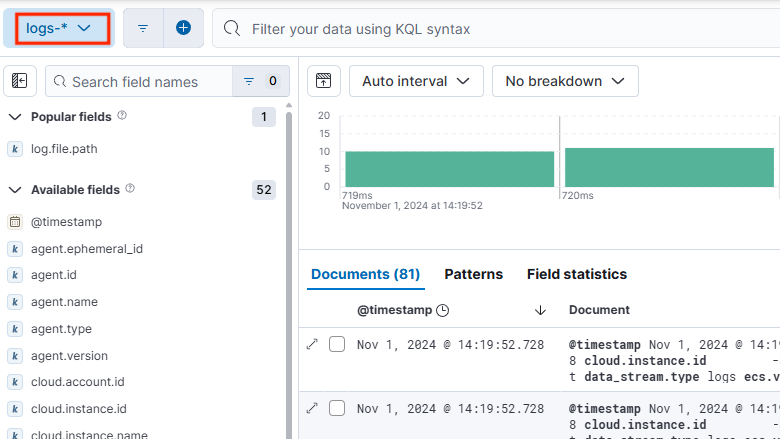
Pour sélectionner l'index des journaux, dans la page Découvrir, sélectionnez journaux-*.
Rechercher et filtrer les journaux de WLS. Pour plus d’informations sur l’utilisation de Découvrir, consultez Découvrir dans la documentation Kibana.
Remarque
Si vous exécutez un cluster WLS, vous devez installer l’agent élastique sur chaque machine virtuelle et configurer des journaux personnalisés sur les hôtes correspondants.
Nettoyer les ressources
Si vous n’utilisez plus la pile WLS ou Elastic, vous pouvez les nettoyer en suivant les étapes décrites dans cette section.
Nettoyer le WLS
Procédez comme suit pour nettoyer WLS :
Dans la page d’accueil du portail Azure, sélectionnez groupes de ressources.
Dans le champ de texte Filtrer un champ..., entrez le nom du groupe de ressources dans lequel vous avez créé le déploiement de WLS.
Lorsque la liste affiche votre groupe de ressources, sélectionnez-le.
Dans la vue d’ensemble du groupe de ressources , sélectionnez Supprimer le groupe de ressources.
Dans la section Êtes-vous sûr de vouloir supprimer section, tapez le nom du groupe de ressources, puis sélectionnez Supprimer. Vous pouvez continuer à utiliser le portail Azure pendant que le groupe de ressources et son contenu sont supprimés.
Nettoyer Elastic sur Azure
Suivez les mêmes étapes que dans la section précédente pour supprimer Elastic sur Azure, mais utilisez le nom de groupe de ressources du déploiement Elastic sur Azure en tant que groupe de ressources à supprimer.
Étape suivante
Poursuivez votre parcours de migration en explorant WebLogic Server vers des machines virtuelles Azure.