Catch the security flaw #2
Consider a fictional web site that lets you create new accounts (as shown below).
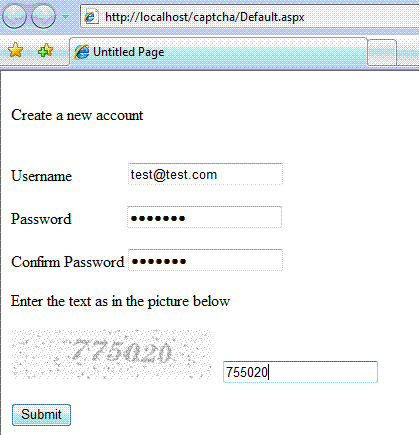
This site implements CAPTCHA to prevent a malicious user from creating large number of false accounts by running an automated script.
The following code is used to implement the CAPTCHA. What do you think is the flaw here?
public partial class _Default : System.Web.UI.Page
{
protected void Page_Load(object sender, EventArgs e)
{
if (!IsPostBack)
{
int randomValue = GetRandomCaptchaValue();
imgCaptcha.ImageUrl = GenerateImage(randomValue);
// hdnCaptchaValue is a hidden variable.
// <asp:HiddenField ID="hdnCaptchaValue" runat="server" />
hdnCaptchaValue.Value = GenerateHash(randomValue.ToString());
}
}
protected void btnSubmit_Click(object sender, EventArgs e)
{
if (GenerateHash(txtImageValue.Text).CompareTo(hdnCaptchaValue.Value) == 0)
{
// Code to create the account
}
else
{
lblCaptcha.Text = "The value entered is not correct.";
}
}
public static string GenerateHash(string text)
{
string hash = string.Empty;
System.Text.UnicodeEncoding uEncode = new System.Text.UnicodeEncoding();
System.Security.Cryptography.SHA512Managed sha = new System.Security.Cryptography.SHA512Managed();
Byte[] hashBuffer = sha.ComputeHash(uEncode.GetBytes(text));
return Convert.ToBase64String(hashBuffer);
}
private int GetRandomCaptchaValue()
{
Random random = new System.Random();
return random.Next(100001, 999999);
}
/// <summary>
/// This method generates an image using Bitmap class and then saves it in webroot.
/// It returns the URL of the image.
/// </summary>
/// <param name="captchaValue">URL of the image</param>
/// <returns></returns>
private string GenerateImage(int captchaValue)…
Comments
Anonymous
March 31, 2008
Looking through the script the flaw appears to be that any attacker can continue to try the same captcha image until they are correct. You need to generate a different captcha image each time the submit button is pressed to avoid this.Anonymous
March 31, 2008
The random function will generate a value between 100001 and 999999. There are 899998 such values possible. Since the value remains same across post backs, if the attacker automates the script to increment the value with each post, we can assume the attacker will find it after an average of 449999 posts. Assuming each post takes 3 seconds, this will take approx 15 days. That is a lot of time to create one false account! Look closer, there is a more serious flaw!Anonymous
March 31, 2008
The url of the image contains the captcha value?Anonymous
March 31, 2008
The comment has been removedAnonymous
March 31, 2008
The comment has been removedAnonymous
April 25, 2008
Make use of this flaw - (!IsPostBack) first time.. he runs & there on... he runs automated scripts with postback requests with the same valuesAnonymous
June 15, 2008
In my previous “Catch the Security Flaw” post I wrote about a flawed CAPTCHA implementation. In this