It’s That Time of Year, For the December 2012 Bulletin Release
Happy holidays! I hope everyone is enjoying the festive season. I like to get my holiday shopping done early, and this year was no exception. In the middle of my holiday shopping last week, as I passed my cash from one store to the next, I was reminded of “Pass-the-Hash.” (My mind does tend to wander a bit as I shop.) For those not familiar, Pass-the-Hash (PtH) is a technique in which an attacker captures account logon credentials on one computer and then uses those captured credentials to authenticate to other computers over the network. Various folks have discussed this technique in the past, and we have seen it used in attacks as well. Today, TwC released a whitepaper that lays out ways to help prevent these types of attacks. Please take a few minutes to read about the Pass-the-Hash technique on the TwC team blog or download the whitepaper to read on the way over the river and through to woods to Grandma’s house. You won’t be disappointed.
Now, on to the news of the day; today we’re releasing seven bulletins, five Critical-class and two Important-class, addressing 12 vulnerabilities in Microsoft Windows, Internet Explorer (IE), Word and Windows Server. For those who need to prioritize deployment, we recommend focusing on the following two critical updates first:
MS12-077 (Internet Explorer)
This security update addresses three Critical-class Internet Explorer issues that could result in remote code execution. These issues exist in all versions of IE, but there is no evidence that they are known publically or under exploit in the wild. You’ll notice there is no severity rating for IE versions prior to IE 9. On these versions, the update is a defense-in-depth change only. Although there are no known attack vectors for these versions, we still recommend that our customers using these versions apply the update.
MS12-079 (Microsoft Word)
This security update resolves one issue in Microsoft Word. This bulletin has a Critical severity rating and can result in remote code execution. An attacker could run code in the context of the logged-on user if they were to open a specially crafted Rich Text Format (RTF) file, or preview or open a specially-crafted RTF email message in Outlook while using Microsoft Word as the email viewer. This issue was privately disclosed and we’re not aware of any attacks or customer impact.
Security Advisory 2755801
With this month’s release, we are also revising Security Advisory 2755801 to address issues in Adobe Flash Player in IE 10. This is a cumulative update, which means customers do not need to install previous updates as a prerequisite for installing the current update. We remain committed to working closely with Adobe to deliver quality protections that are aligned with Adobe’s update process.
Please watch the bulletin overview video below for more information.
As always, we recommend that our customers deploy all security updates as soon as possible. Our deployment priority guidance is below to further assist in deployment planning (click for larger view).
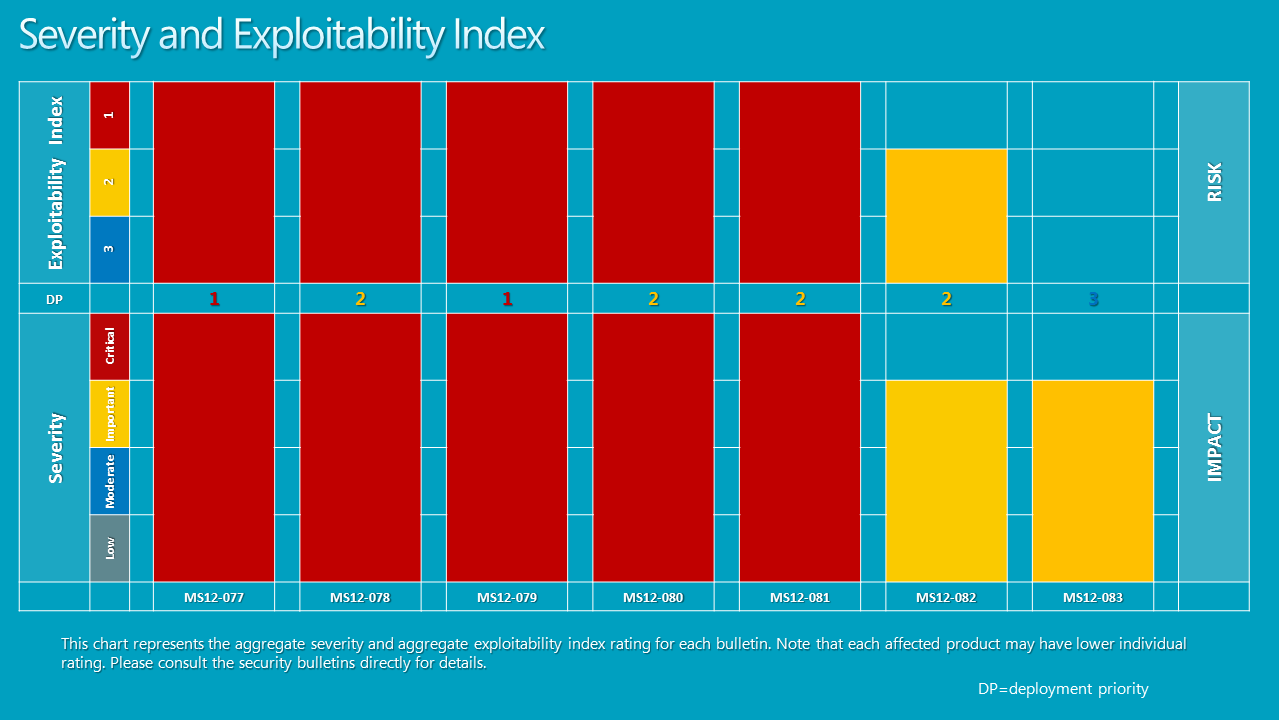
Our risk and impact graph shows an aggregate view of this month's severity and exploitability index (click for larger view).
For more information about this month's security updates, visit the Microsoft Security Bulletin summary web page.
Per our usual process, Jonathan Ness and I will host the monthly technical webcast on Wednesday. I invite you to tune in and learn more about the December security bulletins and advisories. We’ve scheduled the webcast for Wednesday, Dec. 12, 2012 at 11 a.m. PST, and you can register here.
For all the latest information, you can also follow the MSRC team on Twitter at @MSFTSecResponse.
I hope everyone has a wonderful holiday season, safe travels and I look forward to hearing your questions during the webcast.
Dustin Childs
Group Manager
Trustworthy Computing