Discover SMB1 in your environment with DSCEA
So, SMB1. Hopefully by now you have already heard and heeded the advice Ned Pyle provided in the link below, and you are no longer using SMB1 in your environment. https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1
Let’s say though that for some reason, you have not followed Ned’s advice yet and you still have some Windows systems in your environment that are using the SMB1 protocol. The same nearly 30 year old SMB1 protocol that Ned explains isn’t safe, isn’t modern or efficient, isn’t usually necessary, and isn’t hard to remove. And let’s say you would like to remove this unsafe, legacy, inefficient and usually unnecessary protocol from the systems in your environment. Ned explains some great methods to remove the SMB1 feature starting in Windows 8.1 and Windows Server 2012 R2, and the steps to disable SMB1 on legacy operating systems including Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, and Windows Server 2012.
Wouldn’t it be nice if there was a way for you to run a scan against your environment and determine if any systems had SMB1 installed or enabled?
I’m happy you asked 🙂
About two weeks ago we introduced DSCEA, a new PowerShell module that allows you to author a desired configuration state in PowerShell DSC and then scan your environment to determine if systems are compliant with the configuration you defined.
DSCEA requires that your systems are running at least PowerShell version 5.0, and has some additional requirements listed here.
Let’s take a look at one example of how we can use DSCEA to scan a Windows Server 2012 R2 environment to see if any of the systems have SMB1 installed. We’ll start by authoring a DSC configuration file that defines the desired state of our systems, which is that the Windows Feature for SMB1 should not be installed.
Next, we will perform a DSCEA scan of a group of systems to see if they are configured to our desired state, or if they have the SMB1 Windows Feature installed (The default setting in Windows Server 2012 R2) .
PS C:\> C:\Users\username\Documents\DSCEA> Start-DSCEAscan -MofFile .\localhost.mof -ComputerName dsctest-1, dsctest-2, dsctest-3
More information on performing a scan with DSCEA can be found at the DSCEA documentation site: https://microsoft.github.io/DSCEA
Now that we have scanned they systems in the environment to see how they match up, we need to generate some reports. DSCEA has multiple options when it comes to reporting. You can generate HTML reports, export result data as CSV, and also take an exported CSV file and bring it into Microsoft PowerBI for deeper insights and enhanced visuals in your report.
Let’s start by taking the XML raw data output we received from our scan and generate some HTML reports to get a quick, tactical view of how the systems are looking.
PS C:\> C:\Users\username\Documents\DSCEA> Get-DSCEAreport -Overall -InFile 'C:\Users\username\Documents\DSCEA\results.20170406-2309-05.xml' -OutPath 'C:\Users\username\Documents\DSCEA'
PS C:\> C:\Users\username\Documents\DSCEA> Get-DSCEAreport -Detailed -InFile 'C:\Users\username\Documents\DSCEA\results.20170406-2309-05.xml' -OutPath 'C:\Users\username\Documents\DSCEA'
Running the commands above generated some HTML reports, shown below.
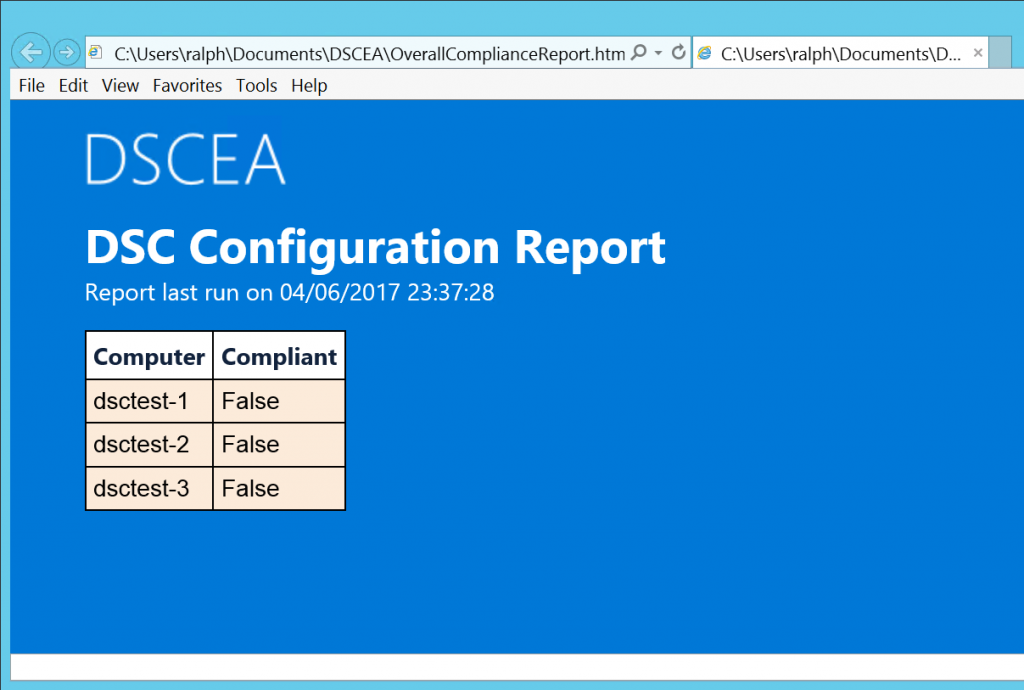
The first report is an overall report, which displays if systems match the desired configuration. In this case, all 3 systems failed our scan, indicating that they all have SMB1 installed.
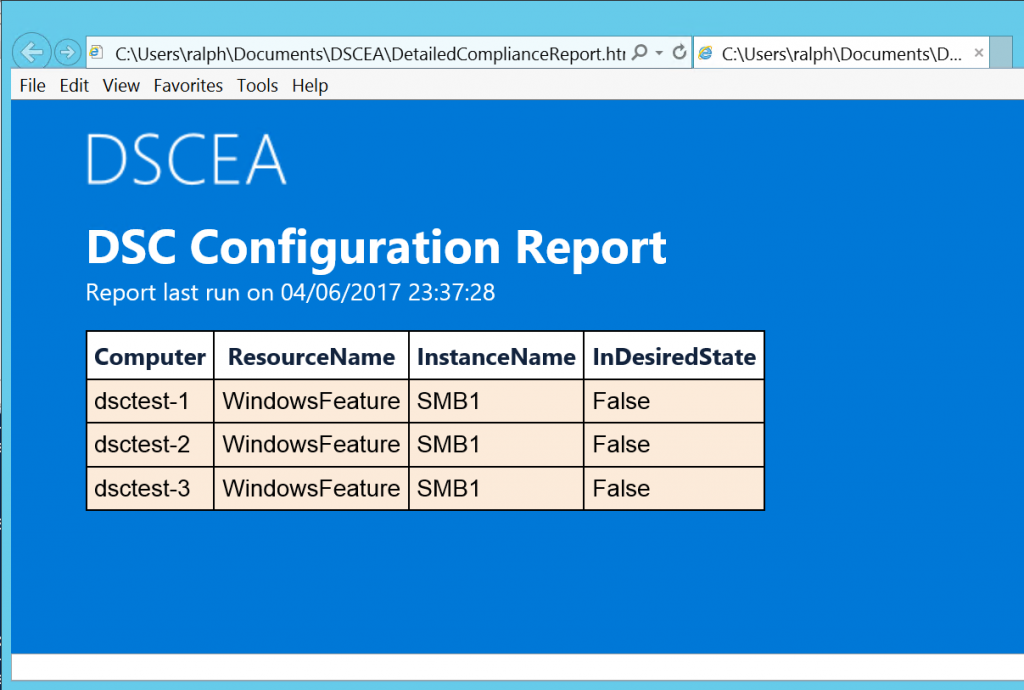
The second report is a detailed report, showing the items in the DSC configuration that were found as non-compliant. In this case, we only scanned for the SMB1 feature, so all 3 systems indicate that as the reason they failed to meet the compliancy requirements.
Armed now with this knowledge, we know which systems require attention and need to have SMB1 removed.
For legacy operating systems, the same guidance applies except you'll need a different DSC configuration file that targets settings in the registry as defined here: https://support.microsoft.com/en-us/help/2696547/how-to-enable-and-disable-smbv1,-smbv2,-and-smbv3-in-windows-vista,-windows-server-2008,-windows-7,-windows-server-2008-r2,-windows-8,-and-windows-server-2012
Example using registry key setting:
So, what are you waiting for? Download DSCEA, scan the systems in your environment and STOP USING SMB1!
Comments
- Anonymous
April 16, 2017
And how do you create the localhost.mof file you reference in your cmd above?- Anonymous
April 16, 2017
The comment has been removed
- Anonymous
- Anonymous
May 11, 2017
Writing this config with a Script resource seems a little easier, because it will work across all systems. And then you don't need two configs. here is the Configuration code: https://gist.github.com/dotps1/19377fc6e872173c5f4b1118745a0a23- Anonymous
May 13, 2017
The comment has been removed
- Anonymous