Enabling password rules for Office 2010
Hi, my name is Alan Myrvold, and I am a security tester on the Office Trustworthy Computing Team (TWC). This post introduces the new password rules feature in Office 2010.
Word, Excel, and PowerPoint have been able to password protect documents for several versions by setting the “password to open”. What we felt could be improved was the ability to enforce password strength rules, similar to what may be required when logging into your computer at work.
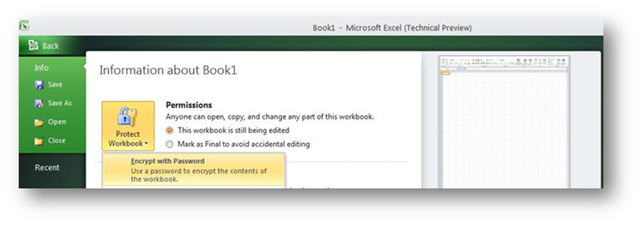
In Office 2010, the encryption password can be set using the Office Backstage View:
This password can also be set on the General Options dialog from the Save As dialog, as the “Password to open”, just like in previous versions of Office.
Password encryption is just one way to protect sensitive information. Depending on your business needs and risks, using IRM or BitLocker might be better choices.
Why is password complexity important?
Although historically Word and Excel used 40-bit RC4 encryption, faster computers mean that 40-bit keys are now considered weak. The Office Open XML format (*.docx, *.xlsx, *.pptx) introduced in Office 2007 provided an opportunity for us to improve our mechanism and algorithms used for password based encryption of documents. The Office Open XML format uses 128-bit AES encryption. We also use a slower key derivation algorithm to make brute force password cracking slower. RC4 is still used when saving in Office 97-2003 binary formats. For encrypted Office Open XML documents, the password is the weakest link. A short or commonly used password makes the document less secure, since it is easier for an attacker to guess it.
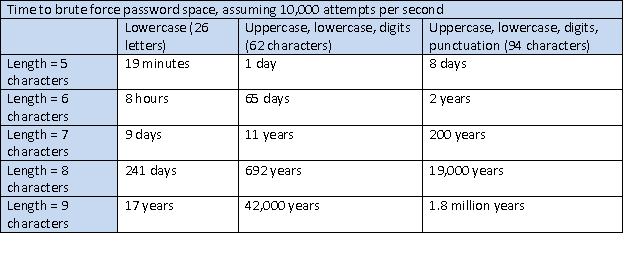
If an attacker needed to try all possible passwords of 5 lowercase letters from a-z, there are only 265, or about 11 million total passwords to guess during a brute force search. Searching dictionary words might even more quickly find the password. An 8 character password, chosen from lowercase and uppercase a-z, plus digits 0-9 is a much larger space of passwords to guess by brute force, 628 or about 200 trillion, and is more difficult to find with dictionary attacks too. These are all worst case efforts, and NIST estimates far less entropy in user chosen passwords. Having less entropy means that attackers can use heuristics to search the password space more intelligently than brute force.
Attackers can also harness the parallel processing power of graphics cards to help with their attack.
But, for brute force attacks, assuming 10,000 password attempts per second, the length and character set of the passwords can make a big difference.
Enforcing a minimum password length and character set complexity requirements can make passwords more difficult for attackers to guess.
How do I enable password complexity?
By default, complexity settings are not enforced, and registry settings are used to control this feature. Although I am describing the registry keys here, the Office Customization Tool (OCT) will be the easiest mechanism to deploy these policies within an organization, but these settings aren’t present in the OCT yet.
There are 2 registry settings to control this, PolicyLevel and MinLength.
HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\Security\PasswordComplexity
HKEY_CURRENT_USER\Software\Policies\Microsoft\Office\14.0\Common\Security\PasswordComplexity
- Value name: PolicyLevel
- Value type: DWORD
- Value data: [ 0 | 1 | 2 | 3 ]
- Use 0 to for no complexity (default), 1 for minimum length, 2 for minimum length plus requiring 3 of 4 character groups, and 3 for all these checks plus enforcing Windows domain password rules.
- Value name: MinLength
- Value type: DWORD
- Specifies the minimum length of password required.
When the policy level is 2 or 3, then the password must contain characters from at least three of four character sets, lowercase a-z, uppercase A-Z, digits 0-9, or non-alphabetic character. When this complexity is enforced, the minimum password length needs to be at least 6, but can be more depending on the MinLength.
Why not just use the Windows domain password policy?
When the policy level setting is 3, then Office will use the Windows domain policy as well as all the settings at level 2. This allows a custom password filter that is installed for Windows passwords to be used. If you are offline or a domain controller cannot be contacted, then the Windows password settings aren’t used, and only the level 2 settings are used. If you don’t have a custom password filter, then using level 2 saves a trip across the network, and would be the best choice.
What if my password doesn’t meet the complexity requirements?
Depending on whether the password is too short, or not complex enough, an error dialog will appear
and then you can re-enter the password.
What if I forget my password? Or the user leaves the company?
Oh dear. We’ve designed the Office Open XML password encryption to be strong and difficult for attackers to crack, which makes password recovery slow. There is no back door, no key escrow, and the 128-bit AES key makes guessing the password the best option.
Unfortunately Microsoft support cannot assist you, as described in KB article 189126.
Microsoft support engineers cannot help you retrieve passwords of files and features in Microsoft products that are lost or forgotten.
Because a forgotten password might result in the loss of critical business information, it is possible to disable setting new passwords in Word, Excel, and PowerPoint, using the DisablePasswordUI setting.
HKEY_CURRENT_USER \Software\Microsoft\Office\14.0\Common\Security
HKEY_CURRENT_USER \Software\Policies\Microsoft\Office\14.0\Common\Security
- Value name: DisablePasswordUI
- Value type: DWORD
- Value data: [ 0 | 1 ]
- Use 0 to enable the password UI, or 1 to disable the password UI.
This setting only prevents new passwords from being set. Existing password protected documents can still be opened. The DisablePasswordUI setting, along with the password complexity settings are designed to help balance the need to secure information with the risk of information loss.
The password rules feature is just one security enhancement in Office 2010, and future blog posts will cover more improvements we’ve made.
Thanks.
Alan Myrvold
Security Tester, Office Trustworthy Computing
Comments
Anonymous
January 01, 2003
Hi If we save with "maintain compatibility with previous versions" do we revert to 40 bit encryption or does it stay at 128 AES level. ps. It is always useful to try and give examples for the less technical users out there. bw MarkAnonymous
October 16, 2009
Do you really think that your core assumption of "10,000 password attempts per second" will have even the slightest validity 1.8 millions years into the future? how about 18 years into the future? no? then please stop misleading your users.Anonymous
October 16, 2009
Great post! Very informative. Thanks.Anonymous
October 16, 2009
@Rob - I think the point of this article was to lead users towards using complex passwords. If this chart had modeled an attack where the brute force key rate was increasing over time instead of remaining constant at 10,000/sec, wouldn't that only be a more persuasive argument to use complex passwords?Anonymous
October 16, 2009
The comment has been removedAnonymous
October 17, 2009
The comment has been removedAnonymous
October 18, 2009
Hi, what I miss from the screenshot you've posted above is the "Read only recommended" checkbox. Besides the password protection I love that feature even more (up to Office 2007) and really miss it a.) in Powerpoint (also up to 2007) and b.) in your screenshot. So my question is: Is this feature still available in Office 2010 - and is ist in addition extended to all Office applications (including Powerpoint)? Background of my question is that in an corporate environment you often send around links to documents - but not for editing but for just viewing them. And for several reasons user stay to long in these files in editing mode - and with the read only recommended feature you can dramatically reduce that unintended file-lock by others (and you can avoid un-intended changes). Any information on that? Regards - JoergAnonymous
October 20, 2009
Joerg - does the "Mark as Final" in the above screenshot accomplish your goal of discouraging editing? The "Mark as Final" feature is in Office 2007 in Word, Excel, and PowerPoint.Anonymous
October 22, 2009
The comment has been removedAnonymous
November 09, 2009
no entendi nada, ponganlo en espanish pleaseAnonymous
November 27, 2009
clé du produit de microsoft office 2010 BetaAnonymous
December 15, 2009
More characters seems desirable for ease of use. A 10 character password or an encryption phrase may be easier to remember than 6 random characters. A random character password is really a combination lock, not a password, and difficult to use. I think passwords are history in the future. We could use combination of a short personal password and a Provider ID Card for instance, which would be more secure. You could have multiple passwords associated with the card...etc...After all, in the future with fastr machines how many random characters do you want to have to remember?Anonymous
December 22, 2009
oi!!!!!!!!Anonymous
December 28, 2009
The comment has been removedAnonymous
January 04, 2010
رائع جدا ... اوفيس 2010 ثورة كبيرة ... انها اجمل ميزة في النسخة الجديدة fantastic >>> thank you vm :)Anonymous
June 23, 2010
Search Office 2007 Password Recovery at Google or Yahoo. Office Password Recovery 5.0 can help! It recovers Password to Open and removes both the Password to Open and Password to Modify for Microsoft Word, Excel, Access and PowerPoint of versions through 97 to 2007. source(s): www.recoverlostpassword.com/.../officepasswordrecovery.html