Gathering Windows AutoPilot hardware details from existing machines
As discussed in the documentation at https://docs.microsoft.com/en-us/windows/deployment/windows-10-auto-pilot, you can harvest the hardware details from existing Windows 10 devices, then upload those to AutoPilot via the Microsoft Store for Business, the Partner Center, or Intune (coming soon). I published a PowerShell script called Get-WindowsAutoPilotInfo to the PowerShell Gallery that helps with gathering that info and formatting it into a CSV-style file that can be uploaded.
In order to gather the hardware details, the device must be running Windows 10 1703 or later and the script needs to be run with admin rights (elevated when running locally). It can’t run on earlier versions of Windows, nor will it run in Windows PE.
It is possible to gather hardware details remotely, accessing WMI over the network, but the remote machine still needs to be running Windows 10 1703 or later. With the most recent script update published last week, you can optionally provide credentials for connecting to the remote machine (not supported for the local machine); just add the “-Credential” parameter (along with the -ComputerName parameter) and specify either a PSCredential object or a user ID (which would result in prompting for the password).
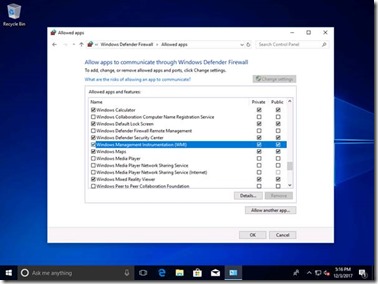
If you are trying to gather the hardware details remotely, you will need to make sure that the Windows Firewall enables access to WMI. To do that, open the “Windows Defender Firewall” control panel and click on “Allow an app or feature through Windows Defender Firewall.” Find “Windows Management Instrumentation (WMI)” in the list and enable for both Private and Public, then click OK:
Or you can do the same thing via Group Policy – nothing special about what the script is doing, it just needs remote WMI access to the classes that contain the details. The script should also accept a piped-in list of computer names, so you could grab them from AD or ConfigMgr and do a whole batch at once.
Some have also asked if it’s possible to have ConfigMgr inventory these details. Due to the length of the hardware hash (4KB), that doesn’t work. You could use ConfigMgr to run the PowerShell script on each machine, then collect the resulting CSV files.
Comments
- Anonymous
December 13, 2017
The comment has been removed- Anonymous
December 13, 2017
The comment has been removed- Anonymous
December 13, 2017
The comment has been removed- Anonymous
December 13, 2017
The comment has been removed- Anonymous
December 13, 2017
Ok, got it.Would it be an future option to let the machine re-register itself using the MDM client after a MB swap ? (without wiping the harddrive) - Anonymous
December 13, 2017
We've talked about ways that we might be able to do something, but nothing committed at this point.
- Anonymous
- Anonymous
- Anonymous
- Anonymous