High Availability Team Foundation Server (TFS) in Azure
A few months ago, I published a template for Deploying Team Foundation Server (TFS) in Azure. Since that approach has particular relevance for Azure Government users, the topic was also picked up by the AzureGov blog. The previous template shows you how to get off the ground pretty quick with TFS in Azure, but some organizations are very sensitive to down time and would want a high-availability (HA) deployment of TFS. I recently showed how to deploy SQL Server (2016/2017) Always On in Azure. A natural extension of this effort is, of course, to demonstrate an HA deployment of TFS in Azure using the SQL Server Always On template and multiple, load balanced, application layer TFS instances.
I have assembled a couple of templates that do just that. They can be found on GitHub. First a TFS HA template for deploying the TFS application with multiple VM instances and a load balancer. Secondly an HA DevOps template that combines all the components (network, domain controllers, SQL Always On, and TFS). The end result looks like this:
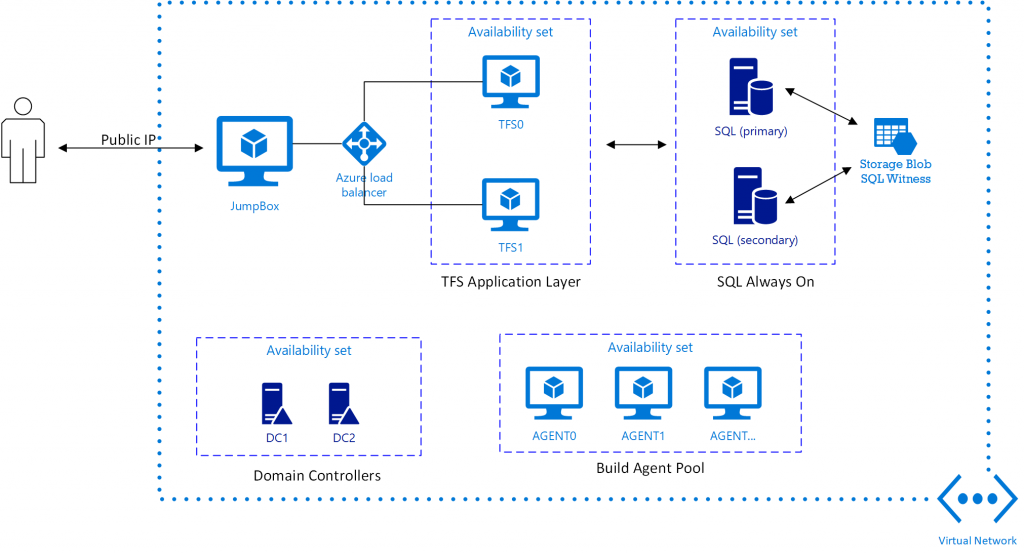
There is obviously quite a bit of stuff in this deployment and you should be aware that it will take on the order of 2-3 hours for a complete deployment.
You should be able to deploy using the usual "Deploy to Azure" buttons, but since TFS establishes a Web front-end, it is recommended that you provide an SSL certificate for that. Moreover, domain credentials are needed throughout the deployment to join VMs, etc. and it is good practice to store these credentials in Azure Key Vault. To help with that process, I have included a convenience script which you can use to set up the Key Vault and store all the details in it. The script will then create a template parameter json file that you can use for deployment. To use this script, you could call it with:
[ps]
.\PrepareDevnetTfsDeployment.ps1 -DomainName contoso.us `
-AdminUsername EnterpriseAdmin `
-KeyVaultResourceGroupName mykvgrp `
-KeyVaultName uniquekvname `
-CertificatePath '<PATH TO PFX FILE>' -Location usgovvirginia
[/ps]
You will then be prompted for two passwords, one if the domain admin password and the other is the certificate password. After running the script, a Key Vault will have been created and the parameters stored in a json file that will look something like:
[js]
{
"adminPassword": {
"reference": {
"keyvault": {
"id": "/subscriptions/XXXXXXXXXXXXX/resourceGroups/keyvault15/providers/Microsoft.KeyVault/vaults/mihansenkv15"
},
"secretName": "DomainAdminPassword"
}
},
"secrets": {
"value": [
{
"vaultCertificates": [
{
"certificateUrl": "https://XXXXXXX.vault.usgovcloudapi.net:443/secrets/SslCert/XXXXXXXXXXXXXXX",
"certificateStore": "My"
}
],
"sourceVault": {
"id": "/subscriptions/XXXXXXXXXX/resourceGroups/keyvault15/providers/Microsoft.KeyVault/vaults/XXXXXXXXXX"
}
}
]
},
"adminUsername": {
"value": "EnterpriseAdmin"
},
"sslThumbPrint": {
"value": "07XXXXXXXXXXXXXXXXXXXXFE9DB79"
},
"domainName": {
"value": "contoso.us"
}
}
[/js]
You can either use this file directly with the New-AzureRmResourceGroupDeployment command or simply copy and paste the parameters into the portal if you deploy that way. You can of course use your other tools of choice to upload the secrets. The script is just meant as help and documentation for assembling the required information.
The main purpose of this template deployment is to make it easier to get started with TFS in Azure. You will probably need to make some adjustments for your specific deployment, but it can be a place to start. The Powershell DSC scripts used in the deployment also provide a way of documenting the needed installation steps. Do feel free to use pieces of the code in your projects and please contribute back (with pull requests on GitHub) if you find bugs/problems or see a chance for improvement.
Let me know if you have questions/comments.
Comments
- Anonymous
January 02, 2018
It will be nice if you can have all the scripts running on-premise with Hyper-V.- Anonymous
January 03, 2018
I don't see why you couldn't run the DSC scripts on-prem to configure SQL and TFS. Haven't tried though. Feel free to give it a go and let us know how it goes.
- Anonymous