Physical Data Center Security
I don't spend a lot of time talking to customers about physical data center security.
As a developer using mostly PaaS or IaaS compute platforms, I just assumed that that cloud provider had taken care of it. Helping customers with Data Security (Data at Rest, Data in Transit, Secure Compute), and Application Code security takes up most of my time.
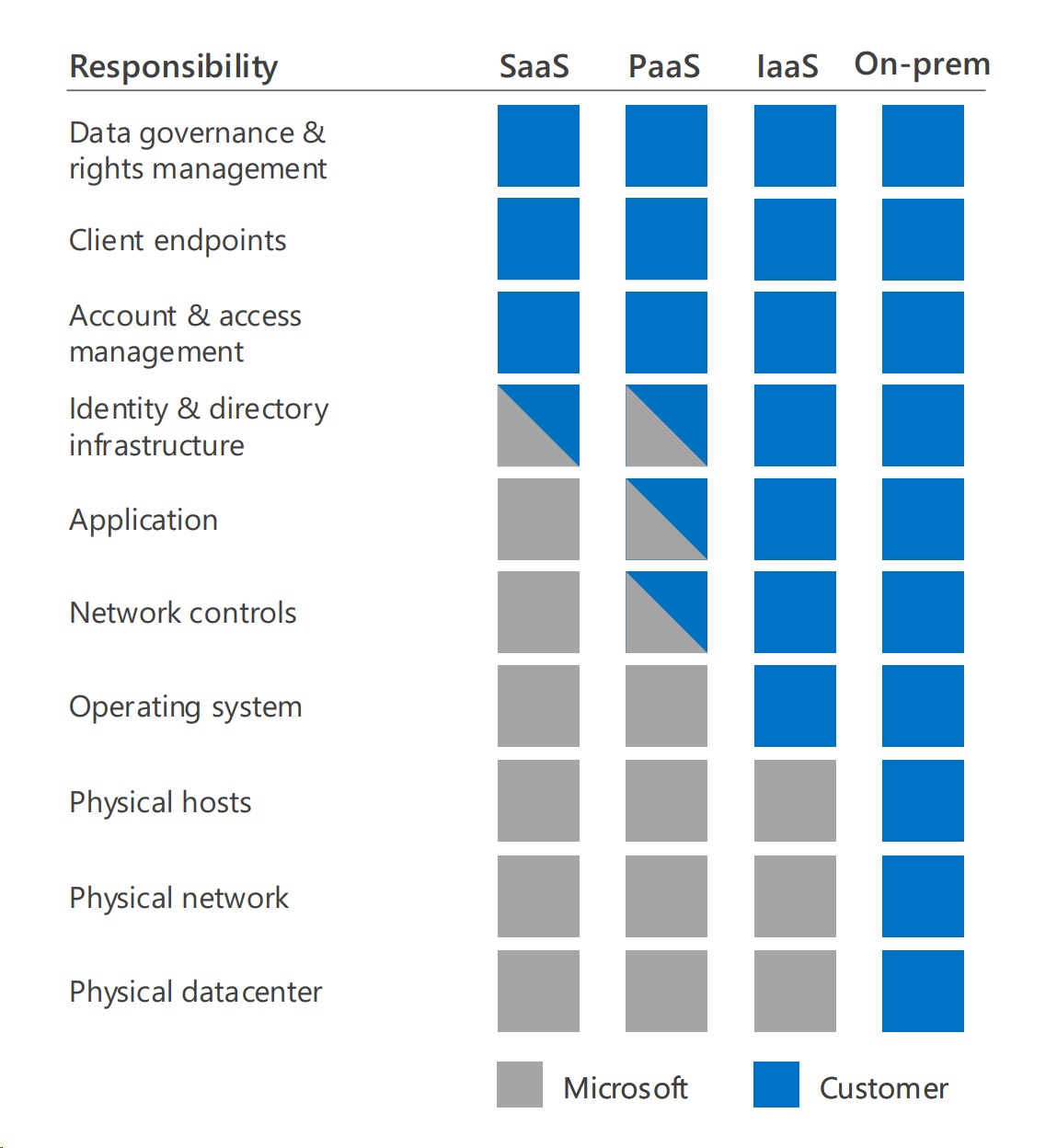
In this post, I wanted to step back a bit and look at the bigger picture. Lets toss out the above assumptions and look at the entire stack where we run our applications. With the proliferation of cloud platforms, you now have a wide choice of IT infrastructure to meet your business needs. A typical IT infrastructure today can encompass a mixture of SaaS, PaaS, IaaS and On-prem solutions.
With On-prem infrastructure, an IT Manager is responsible for the core capabilities and tenets below to make sure they have a secure infrastructure. As you move left in the diagram below, you notice that responsibilities for those core capabilities start to shift towards your cloud provider (in this case Microsoft).
The first shift accountability that a cloud provider takes on is hosting the physical infrastructure and providing Compute\Storage as a Service (i.e. typical IaaS scenarios). Along with hosting the physical hardware and making sure that it is operational, the cloud provider also takes on the responsibility of making sure that the physical hardware is secure.
Obviously, you don't want someone walking into a data center and walking out with a disk containing your data. So what does it take to physically secure a data center?
- Restrict Access to white-listed authorized users with prior time boxed approvals
- Fences, Gates to prevent unauthorized entry
- 24/7 Security to monitor internal and external environments
- Multi Factor Authentication to establish visitor access
- Security Searches of Personnel\Bags on entry and exit to make sure nothing unauthorized enters or leaves the building.
- Etc.
The above is not meant to be an exhaustive list but to help you get started thinking about Physical Datacenter Security. Layering in multiple levels of access controls and measures helps protect against an adversary who may defeat a particular layer.
How does Microsoft do it? Here is a link to a detailed post by Ryan describing the efforts of his team to make sure that Microsoft Data centers are physically secure. It is a great behind the scenes look at how Microsoft physically secures our global data centers. Microsoft has invested over a billion dollars into making sure that Azure is the most secure it can be so that we can earn our customers trust. Without that trust, customers would never be comfortable in handing over their data and infrastructure. Here are some more resources if you would like to dig deeper.
Microsoft Trust Center - Design and Operational Security Microsoft Azure Security, Privacy and Compliance Whitepaper
Do all customers need to physically secure their data centers to the same level as Microsoft? Well...it depends. What is the business impact and cost of a security incident to your business? Does that justify in implementing some or all of the measures above to protect your infrastructure? Hopefully the resources in this article help you understand how to better protect your infrastructure. If you would like to learn how Microsoft Services helps our customers secure their infrastructure, here is a great overview by our Secure Infrastructure team.
Microsoft Cloud Security for Enterprise Architects Whitepaper