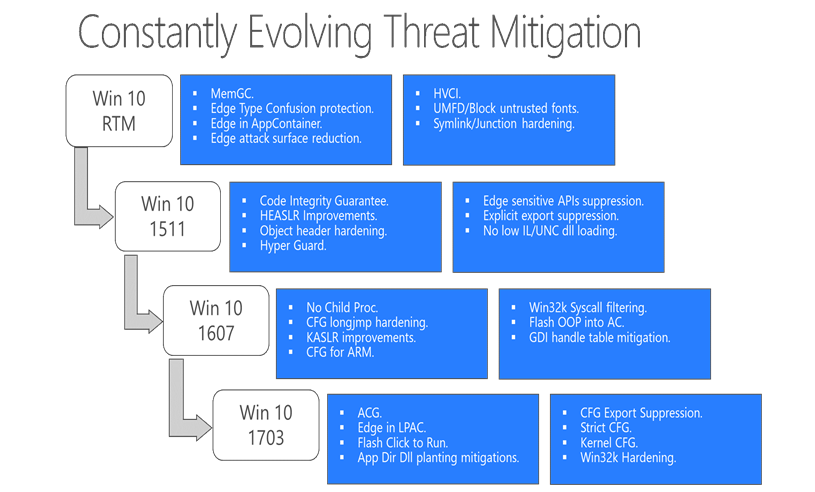
Threat Mitigations in Windows 10
Traditionally Operating system releases from Microsoft used to happen once in few years and the time between releases, a lot of these exploitation techniques used to get developed. Most of these new exploitation techniques were used to carry out attacks on Windows platform which didn't have any mitigations and future release with the fix was few years apart.
Some of the exploitation that exists today didn't even existed a decade before.
Exploitations a decade before:
- Stack overrun
- Return Address Corruption
- Shell Code
Exploitation techniques today :
- ARW
- Sandbox bypass
- Heapspray
- Memory Corrupt
- CFG Bypass
- ASLR Bypass
- DEP Bypass
- ROP Shellcode
Given the kind of threats have increased multifold, waiting for couple of years to mitigate a particular exploitation technique is far from ideal and leaves our consumers and commercial users/organizations vulnerable. With Windows 10 as a Service where we keep releasing new features and capabilities every 6 months has reduced the shelf live of these techniques.
Today we’ll go through these security mitigations enabled in Windows 10 and is enabled by default to all of our user irrespective of the Windows 10 editions you are using. 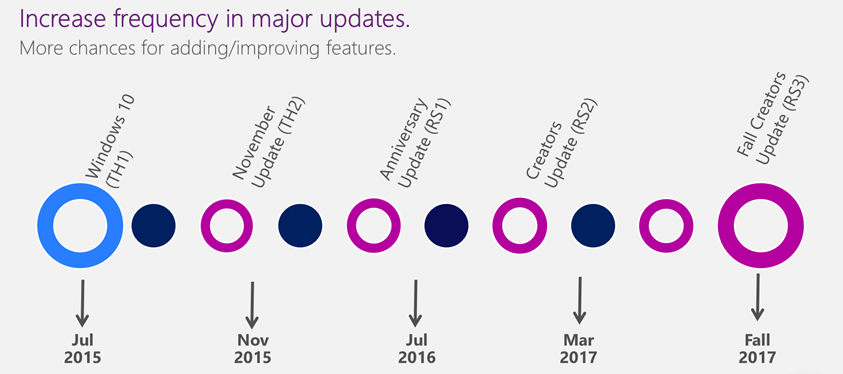
Threat Mitigations in Windows 10 is set of features which helps to disrupt exploitation techniques and vulnerability classes harder or impossible to use.
Lets go through some of these important mitigations
1. User Mode Font Driver ( UMFD ) :
User mode font driver mitigation was added in initial version of Windows 10. This is towards isolating or containing the vulnerabilities.
Font process was done in kernel mode, and these memory corruption could be hit remotely using untrusted fonts. The font processing code is very legacy code and it is also from different contributors as well.
With UMFD the font processing is now moved into an App Container in user mode. This actually makes any of the vulnerabilities in font processing kind of use less.
So, the EOPs or typically the sandbox escapes that were being targeted using vulnerabilities are no longer possible.
All the processes gets benefitted from this mitigation.
While we have moved the font processing to user mode to contain the vulnerability, it is also possible to disable processing of untrusted remote fonts for a process via the ProcessFontDisablePolicy process mitigation option.
2. Win32k Syscall Filtering :
We all know that Win32k subsystem is the No.1 targeted component for achieving Sandbox escapes. It is a gigantic component because of its functionality, what ever you see is all mostly Win32k. It has a very huge attack surface, about 1200 APIs compared to about 400 NT APIs.
With Syscall filtering Microsoft Edge tries to maintains a list of Win32k APIs that it needs and allows only those from the content process thus reduces the surface area.
This mitigation removes a good set of Win32k APIs that can be targeted for any possible memory corruption.
3. Less Privileged App Container (LPAC):
App Container has access to resources protected with ALL APPLICATION PACKAGES SID: This SID has read permission on all folders by default. LPAC is a more restricted version of the App Container. it denies access by default for everything. One can access only the secured objects that are granted explicitly to LPAC.
4. Structured Exception Handling Overwrite Protection (SEHOP) : this feature is designed to block exploits that use the Structured Exception Handler (SEH) overwrite technique. Because this protection mechanism is provided at run-time, it helps protect applications regardless of whether they have been compiled with the latest improvements.
5. Address Space Layout Randomization (ASLR) : ASLR loads DLLs into random memory addresses at boot time. This mitigates against malware designed to attack specific memory locations where specific DLLs are expected to be loaded.
6. Heap protections : Windows 10 includes protections for the heap, such as Heap metadata hardening for internal data structures that the heap uses, it also uses Heap allocation randomization, that is, the use of randomized locations and sizes for heap memory allocations, which makes it more difficult for an attacker to predict the location of critical memory to overwrite. Also Heap guard pages before and after blocks of memory, which work as tripwires. If an attacker attempts to write past a block of memory (a common technique known as a buffer overflow), the attacker will have to overwrite a guard page. Any attempt to modify a guard page is considered a memory corruption, and Windows 10 responds by instantly terminating the app.
7. Kernel pool protections,
Windows 10 includes protections like Kernel DEP and Kernel ASLR for the pool of memory used by the kernel. For example, safe unlinking protects against pool overruns that are combined with unlinking operations to create an attack.
8. Control Flow Guard :
Control Flow Guard (CFG) is a mitigation that requires no configuration within the operating system, but instead can be built into software when it’s compiled. It is built into Microsoft Edge, IE11, and other features in Windows 10. It can also be built into applications when they’re compiled. For example, it can be built into applications written in C or C++, or applications compiled using Visual Studio 2015.
For such an application, CFG can detect an attacker’s attempt to change the intended flow of code. If this occurs, CFG terminates the application. Administrators can request software vendors to deliver Windows applications compiled with CFG enabled
9. Protected Processes : With the Protected Processes feature, Windows 10 prevents untrusted processes from interacting or tampering with those that have been specially signed. Protected Processes defines levels of trust for processes. Less trusted processes are prevented from interacting with and therefore attacking more trusted processes. Windows 10 uses Protected Processes more broadly across the operating system, and for the first time, you can put antimalware solutions into the protected process space, which helps make the system and antimalware solutions less susceptible to tampering by malware that does manage to get on the system.
10. Universal Windows apps protections: When users download Universal Windows apps or even Windows Classic applications (Win32) from the Windows Store, it’s highly unlikely that they will encounter malware, because all apps go through a careful screening process before being made available in the store. Apps that organizations build and distribute through Sideloading processes will need to be reviewed internally to ensure that they meet organizational security requirements
11. No Child Proc : Attackers can trick a sandbox to create a child process to bypass mitigations. this feature prevents code execution via launching a child process.
Here is the release cycles of various threat mitigation capabilities in every Windows 10 feature updates :
The main objectives of implementing these threat mitigation capabilities in Windows 10 are :
- Reducing the attack surface of Windows Platform
- Takes soft target out of the picture
- Eliminates existing exploitation techniques so that new techniques need to be found.
- Reducing impact of vulnerability by isolation.
- Make overall exploitation harder and expensive
These are all the more reasons to move to Windows 10 as quickly as possible to remain protected against modern cyber threats.
Hope you liked the article, look forward to more later.
Cheers.
Comments
- Anonymous
August 29, 2017
Great.Please translate this note to Japanese, for target a lot of IT pro, Dev, Business owners for sharing updating windows 10 with schedule.This note share different era of security from Windows 7 era.and IT pro, Dev, Business owners prepare this era.Regards,Yoshihiro Kawabata- Anonymous
September 05, 2017
Hi Yoshihiro, I added Bing Translator which will help you to read this in your own language :)Cheers
- Anonymous