SharePoint permissions based on SAP Roles may not be honored
Issue:
I just worked with a customer that had Duet Enterprise configured and they were setting permissions in SharePoint based on their SAP Roles as described in Using SAP roles to access SharePoint objects . Everything looked good, but users with the SAP Roles defined were not able to access the SharePoint sites that were permissioned with the SAP Roles.
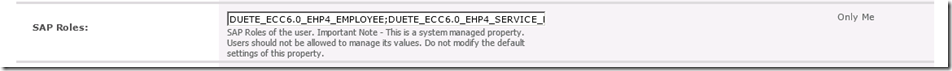
The first thing we did was confirm that the SAP Roles were actually on the user profiles. To do this we went to Central Administration selected Manage Service Applications and then clicked on our User Profile Service Application. Under People we chose Manage User Profiles and then searched for one of our users. Once found we selected the user and chose Edit My Profile and we could see in the list that the SAP Roles property existed and that it was populated as expected:
The next step was to verify that the user's Claims token on SharePoint actually contained the Roles. I didn't find a simple way to do this so I used the Windows Debugger (windbg.exe) to dump out the Claims and could see that the SAP Roles were not included. Instead of using windbg you could create a simple web part to dump out claims based on the sample on MSDN.
So at this point I knew that the User Profiles had the SAP Roles populated, but the user's Claims were not being augmented with the SAP Roles. I debugged the Security Token Service and found that the Duet claims provider successfully retrieved the User Profile but the SAP Roles property (actually named OBACore-SAP-Roles) was empty so the Duet claims provider didn't have any roles to add.
We then realized that the issue was related to the permissions on the User Profile Application. The SAP Roles property that gets added by Duet Enterprise is added with the Default Privacy Setting set to Only Me which is visible in the image above . The problem was that the customer had configured a new identity for the SecurityTokenServiceApplicationPool but this identity didn't have any special rights on the User Profile Application. So when the Duet claims provider code running in the SecurityTokenService retrieved the user profile, it was running as the identity of the SecurityTokenServiceApplicationPool and therefore could not see any fields that had the privacy setting configured to Only Me.
Resolution:
To fix this we went to Central Administration selected Manage Service Applications and then clicked next to the User Profile Service Application to select it without opening. On the menu we clicked on Administrators and then we added the identity from the SecurityTokenServiceApplicationPool and gave it the Manage Profiles permission.
Another solution would be to use Manage User Properties in the User Profile Service Application to change the Default Privacy Setting on the SAP Roles property to be Everyone instead of Only Me.