WCF: Transport Layer Security - with client certificates
WCF-Transport Layer Security - with client certificates
Requiremnt:
- HTTPS/SSL Channel
- Authentication mode
- Certificate
- Windows / NTLM
WCF HOST:
- IIS
Certificates Authentication on Transport Layer - IIS
Requirement:
- SSL Channel (using Server/SSL certificate)
- Adding a Https binding on IIS and assigning the required SSL certificate.
- Client to have private key of client certificate
- Server to have TRUST for client certificate
Trust:
- Peer Trust
- Chain Trust
PeerTrust (Forces a public key of the client certificate to be present in the 'Trusted People' certificate store on the service side)
ChainTrust (Certificate must validate according to the complete certificate chain)
Architecture:
Passing client certificate:
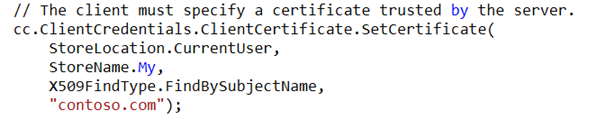
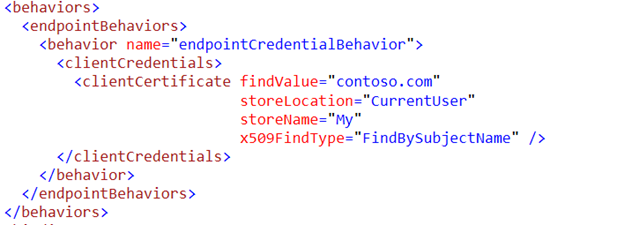
- Via Code
2. Via Config
Handling Certificate Authentication (IIS)
When we say we want to handle authentication @ transport layer, it would be the responsibility of our host (IIS) to help us authenticate the incoming request over a client certificate.
We call this process as Client Mapping.
Client Mapping
- One to one mapping
- Many to one mapping
Mapping is a process of assigning an identity to the incoming request.
Now when we use client credential type as certificate, the incoming request has only identity as “client certificate”, but on IIS how will I come to know who is the client ?
Because to access the resource or service on IIS machine, the incoming request should have an valid identity who is allowed to access that resource.
This valid identity could be a local account, domain account or service account.
Reference to learn one to one and many to one mapping:
Based on the mapping done and rules set, incoming client certificate will be mapped to the selected identity and will be authorized based on that only.
Once it is authorized the request will reach to service.
Addition:
Important thing to remember when we use Transport Security with Client cert as authentication type... we have to always configure IIS for Anonymous authentication.
Drawback: If the client cert mapping rule fails and a BAD CLIENT CERT (which we do not want to use) is issued,
the request fall back to Anonymous and request is eventually served by IIS (unless we add another check by using X509CertificateValadator in WCF API).
Workaround:
Configure IIS to have an AUTHORIZATION RULE, to KICK OUT the Anonymous users.
Mapping:
Authorization rule:
Note:
URL AUHORIZATION RULE only works in Classic mode.
Note (be careful for nested IIS applications):
Client cert mapping should always be set on web site level and the parent web application as applicable.
Directly adding the mapping at the child level will not be read..
Wrong way ...
Right way ...
Observing the SSL handshake for Client certificate over Transport layer.
The certificate handshake document will present the complete process involved for the key exchange between server and client.
They both starts talking over the SSL channel once the handshake is successful.
blogs.msdn.com/b/saurabs/archive/2012/04/27/monitor-certificate-ssl-handshake.aspx
Hope the document helps understanding the role of IIS and SSL channel for adding Transport layer security.
Comments
- Anonymous
June 07, 2015
I built a REST service, instead of SOAP, and wanted to secure it with Certificates. It seemed like all the methods for doing this at the Application level required SOAP (my methods were set up for POST using WebInvoke) so we resorted to setting up 2-way SSL in IIS configuration. However, I still wonder, is there a way to configured 2-way SSL in web.config if the WCF service is REST and not SOAP?