IIS: How to Reduce Multiple Authentication or Multiple 401 while using Kerberos for authentication
Problem:
While using Kerberos protocol for authentication on IIS; for every single request that comes to the service; in fiddler we can see that that there is a 401 followed by 200 response from the server.
Even though it might not be a problem in most of the cases however in the scenarios where there is huge network congestion this kind of response may raise concern.
Cause:
When we use windows authentication by default it uses Kerberos and Kerberos is request based authentication i.e. it authenticates each and every requests that comes in.
Whenever a request arrives at IIS it has to go through authorization mechanism if we are using Windows authentication.
Repro and Resolution:
I created a WCF service and hosted it on IIS with Windows Authentication and a sample client application that makes multiple calls to the service hosted on IIS.
The code for the client application looks like this:
So here we have created a proxy for the service and we are making a call to GetData method of this service 3 times in a loop.
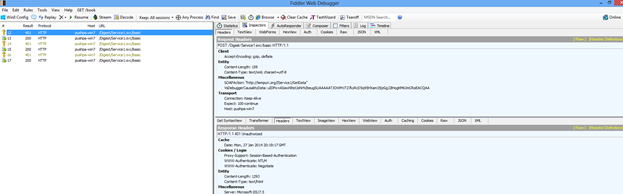
Now let’s monitor the traffic with the help of fiddler:
So the fiddler traces shows that every request to the service is first authenticated (as observed through the result code 401) and then responded.
This is the default nature of Kerberos protocol since it is made more secure.
Before Kerberos NTLM was being used which is a connection oriented protocol i.e. once a user is authenticated we can reuse the same connection again and again unless the session is being tear off.
Although the new protocol authentication mechanism enhances the security structure it increases the traffic flow between client and server as well; so can we reduce this traffic somehow?
Yes we can!!!!!
We have an option available with us on IIS for the website that enables IIS to use TCP session to identify the client. This particular property is called AuthPersistNonNTLM.
By default this property is false to enable session based authentication we can set it to true.
How to set AuthPersistNonNTLM=true ?
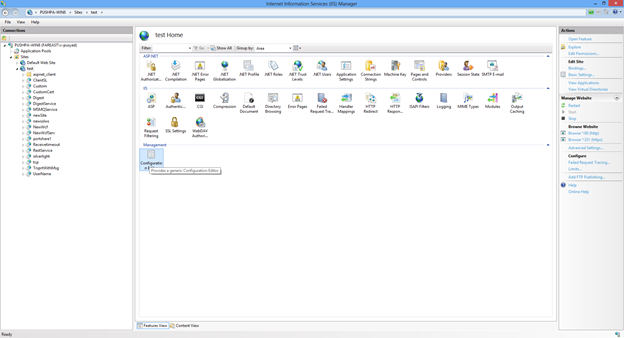
Navigate to the site on IIS that is hosting your service and open up the configuration editor and select applicationhost.config file
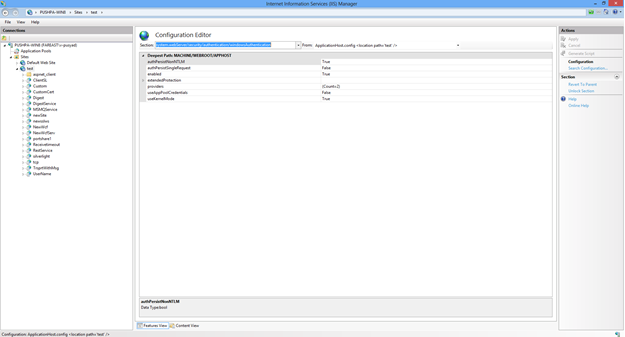
Go to Security->Authentication->WindowsAuthentication. Here we see the property set authPersistNonNTLM=true
Refresh the site once and let’s monitor the requests from the WCF client application to the service once again and this is how the traffic looks like now:
Story under the hood:
By default Kerberos is connection less protocol that results in each and every request being asked for authentication however when we set authPersistNonNTLM=true in the applicationhost.config file the Kerberos protocol works as connection oriented protocol over a TCP session and doesn’t ask for authorization again and again till the TCP session ends.
Hope this info helps !
Created by
Pushpa yadav