Using Google OAuth 2.0 authorization server in Azure API Management
While trying out API Management's in-preview SOAP to REST capabilities against Google's AdWords API, I needed to enable Google's OAuth 2.0 authorization in APIM to connect to the API. While each separately has good documentations and samples, I didn't find the intersect of someone putting together to two. So here it is, how to use Google OAuth 2.0 as authorization server in Azure API Management.
- Pre-requisites:
As prerequisite you will need to have an API Management instance in Azure and an account in Google's services.
- Start OAuth server addition
In Azure API Management you may create the Authorization Server either in the OAuth preview blade in the Azure Portal, or in the API Management Publisher Portal.
With the Publisher Portal go under the Security section of the left hand side menu, then the OAuth 2.0 tab on the horizontal menu. The settings you need to use will look like this:
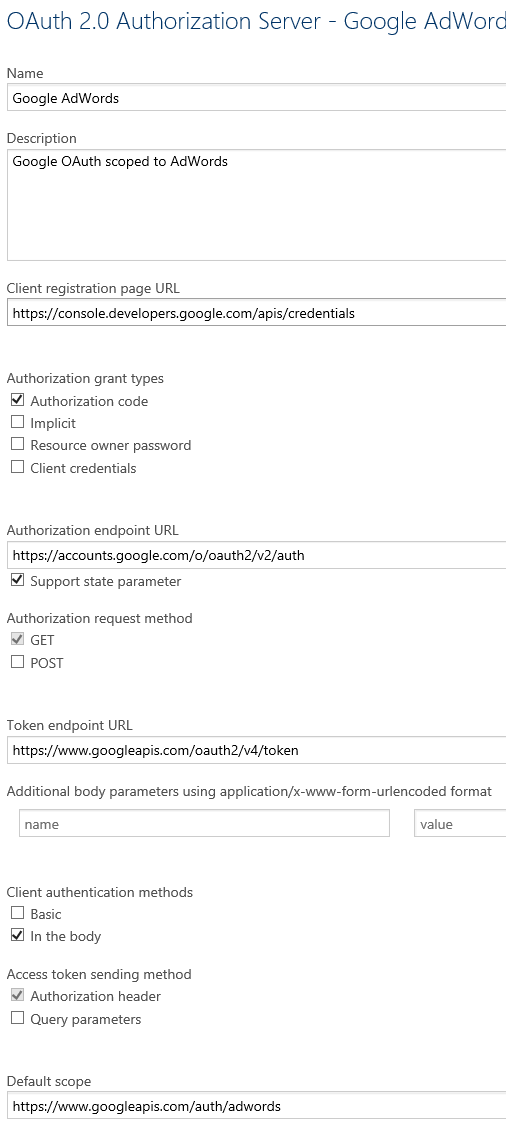
For your convenience, here are the field values as text so you may copy-paste them:
- Google AdWords (replace AdWords with the Google service scope of your choice)
- Google OAuth scoped to AdWords
- https://console.developers.google.com/apis/credentials
- https://accounts.google.com/o/oauth2/v2/auth
- https://www.googleapis.com/oauth2/v4/token
- https://www.googleapis.com/auth/adwords (replace the suffix of this URL with the specific Google service you seek to enable; here is the AdWords suffix. Google drive, Google mail for instance will have a different suffix. It should be possible to specify multiple scopes but I am not aware of the syntax for that.)
- Get client credentials from Google
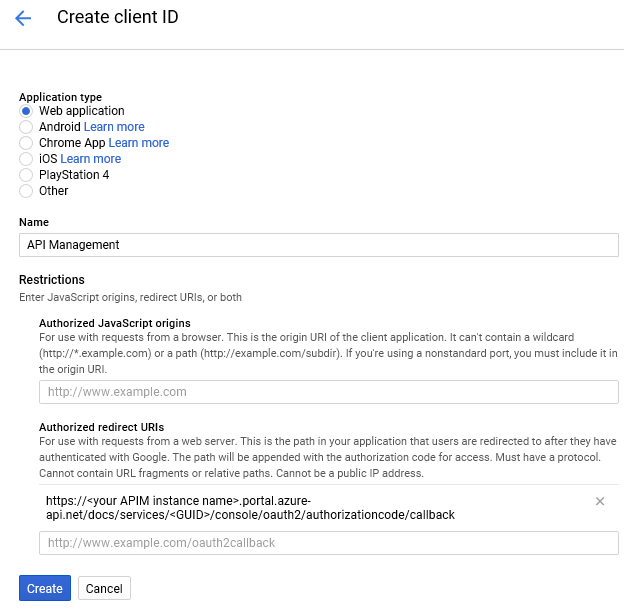
Then come the client credentials. However to get the client credentials value you need to create them on the Google account, which in turn will need the redirect URI to restrict the allowed callers. The APIM page will give you this under "This is what the redirect_uri for authorization code grant type looks like:"
i.e. https://<your APIM instance name>.portal.azure-api.net/docs/services/<GUID>/console/oauth2/authorizationcode/callback
You will need to copy the actual value from your instance of APIM as you can't have the placeholder <> values I put above.
The client credentials can be create in Google's developers console under the Credentials tab. Under Credentials, choose Create credentials then OAuth client ID
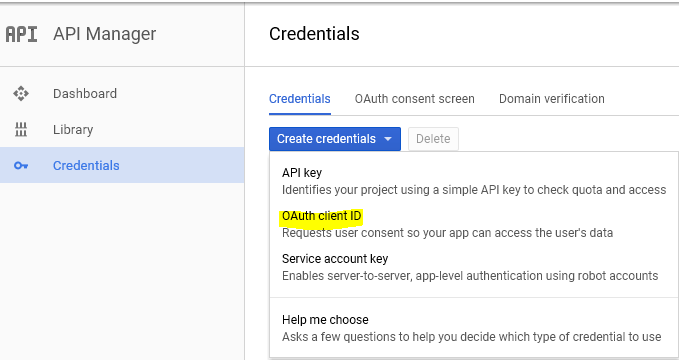
Select Web application as type.
I use "API Management" as name.
Then copy the redirect URI from APIM.
Finally hit "Create". A prompt will give you the client ID and client secret. If you discard the prompt by accident you can see these values again by opening the client entry again in the list of credentials. You can also correct the redirect URI or add more URIs if needed.
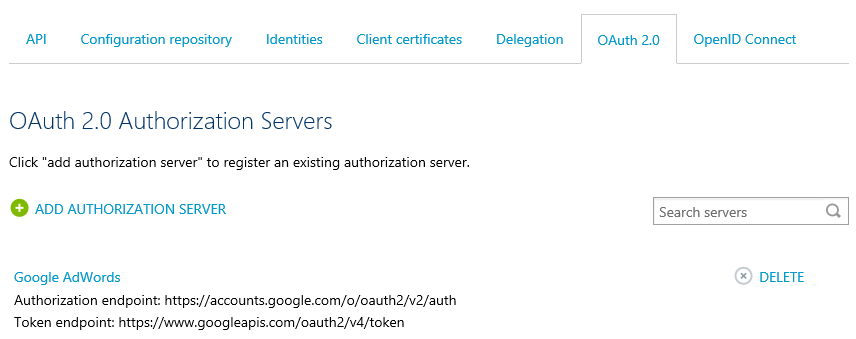
- Back to APIM to complete the authorization server addition
You can now fill the Client ID and Client secret fields of the API authorization server addition. Hit Save at the bottom of the page to complete the addition. You should now see the new entry in the list of authorization servers:
- Start using the authorization server for the Google APIs
Under the APIs section of API Management, after selecting a specific API such as the AdWords Campaign Service (you can import this in APIM for SOAP with the WSDL at https://adwords.google.com/api/adwords/cm/v201705/CampaignService?wsdl ), change the User authorization from None to OAuth 2.0 and select the Authorization server you just added such as here "Google AdWords":
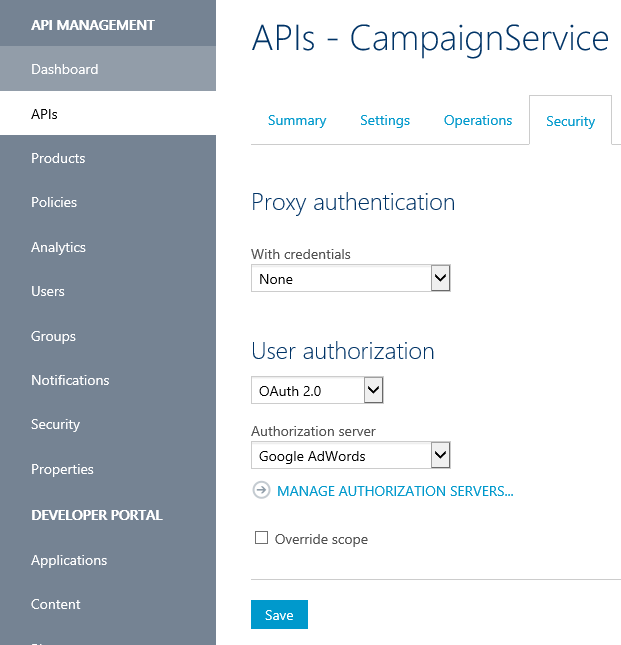
- Send a test request
For that you will need to switch to the API Developer Portal. Navigate to APIS, pick the Google API you would have associated with OAuth, select a specific operation and click "Try it". Under Authorization change from No auth to Authorization code. You will be redirected to Google's consent server
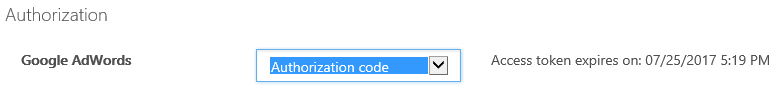
Assuming you have good values in the body for this request you should be able to hit "Send" to make an actual call with OAuth tokens to the Google API.
Comments
- Anonymous
June 20, 2019
This blog has been moved off the MSDN platform. Find further content and update at https://www.linkedin.com/today/author/daviburgComments are locked as part of the blog migration, so please reach out to your customer support contact for assistance with Microsoft products and services.