Restrict iOS/Android E-mail to Outlook using Conditional Access for MAM
One of the most common discussions I have with customers is how does an IT Pro ensure that corporate data is only being accessed by approved, managed email applications.
Intune Mobile Application Management (MAM) provides a rich set of Data Loss Prevention (DLP) features that ensures no corporate data is leaked outside of the corporately managed apps. The Outlook app for iOS and Android is by far the most popular MAM enabled app, as it provides the most secure and user-friendly experience for accessing Exchange Online.
But how does an organization restrict access to their Exchange Online data to only the Outlook protected app?
Traditionally, we’ve had some very complex solutions utilizing Exchange Allow/Block/Quarantine (ABQ) rules and ADFS claim rules to ensure users can only use the Outlook app. ABQ rules to restrict the client, and ADFS claims to restrict the authentication method, for example.
This month, we released a new feature which will simplify this ask a whole lot – Conditional Access for MAM.
CA for MAM will allow an IT Pro to restrict Exchange Online to only the MAM enabled apps for iOS and Android. All other third party clients (for example, the native e-mail apps on iOS/Android) will not be able to connect to Exchange Online.
The feature is available for MAM Without enrollment (MAMWE), meaning your devices don’t even need to be enrolled to enable this functionality.
In the new Intune Portal, you’ll see a new blade called Conditional Access 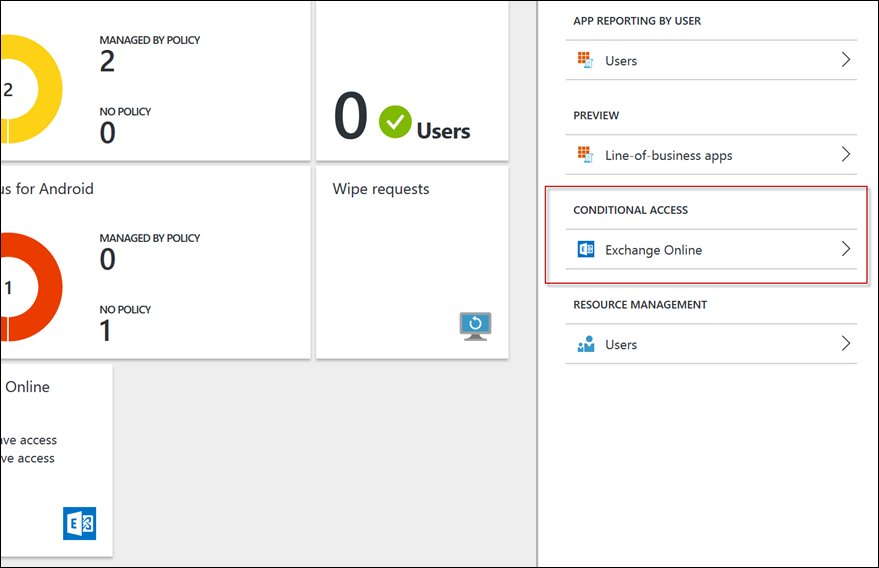
Select the Exchange Online option to expand out the options.
Here you can set up which apps can access the data, and which users are/aren’t targeted by the policy.
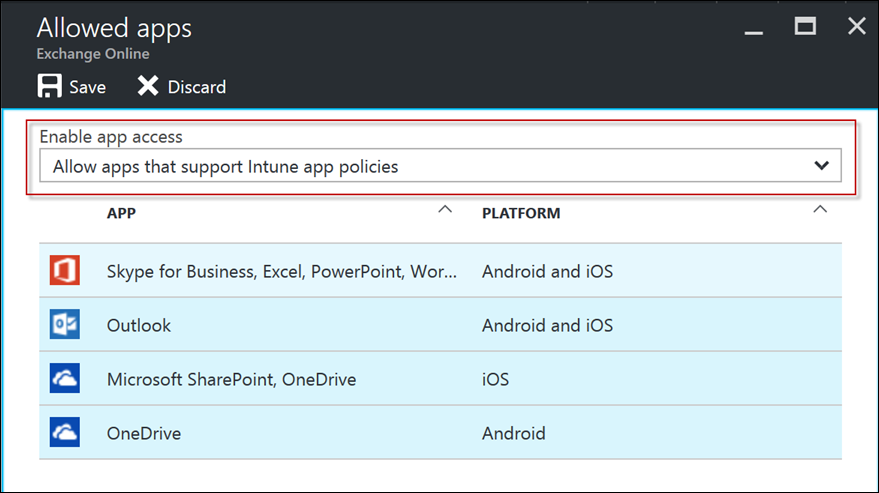
Select Allowed apps to configure the policy setting.
Select Allow apps that support Intune app policies and press Save
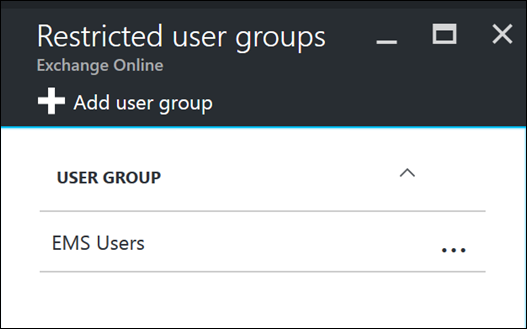
Then target the Restricted user groups with your desired AAD group
And you’re done! The users in the targeted AAD group will now be required to install the Outlook app to access their Office 365 e-mail.
There are some minor prerequisites you should be aware of. For the MAM CA to work, iOS users must have the Microsoft Authenticator app installed and logged in and Android users must have the Company Portal app installed and logged in. If the users do not have these apps installed, they will be prompted to install them before e-mail access is granted.
Edit 5/22/17: Users do not have to login to the Authenticator or Company Portal app for MAM CA to work. Just the presence of the app should be enough.
Also note that for Device CA targeted users (traditional CA), if a user is targeted for both policies the compliance is determined in a logical OR.
For example, if the device is managed by Intune and CA compliant the device will have full e-mail access, including the native EAS mail apps. OR, if the device is not managed but has the Outlook app it will have full access via the Outlook app only. This is really a very good experience for BYO vs COD scenarios, where we’d enroll a corporate owned device, but require Outlook and MAM for a personally owned device.
Edit 8/9/17: With the introduction of Azure AD in the Azure Portal, using MAM CA and AAD CA in Azure will allow a logical AND.
For example, if you want to enforce device enrollment AND the use of the Outlook app for Exchange Online, configure both the AAD CA in Azure policy AND the MAM CA policy in Intune. This is a great experience for organizations that want to manage devices, but ensure MAM DLP is applied to their corp data. This should also avoid the need for ADFS claims rules/ABQ's/etc to enforce the Outlook app! For more info on AAD CA see here.
Edit 16/10/17: In September the functionality to allow customers to select the AND/OR operator as desired was shipped!
To configure the OR operator:
- Login to portal.azure.com
- Browse to the Azure Active Directory Node, and select Conditional Access
- Find your Conditional Access policy and edit it
- Under Access controls > Grant you'll find a new option "Require approved client app (preview)"
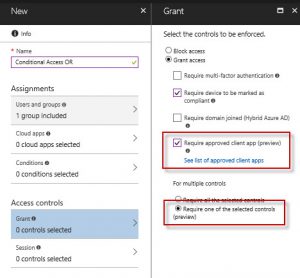
- Select this option and the Require one of the selected controls and save your policy.
This effectively enables Conditional Access to require an Intune compliant device OR an approved app such as Microsoft Outlook, OneDrive, etc. If you want to set the operator to AND (ie, enrolled device AND Outlook app), select the "Require all the selected controls" . For more detail, visit the following link
/en-us/azure/active-directory/active-directory-conditional-access-technical-reference
Matt Shadbolt
Senior Program Manager
Enterprise Client and Mobility – Intune
Comments
- Anonymous
November 02, 2016
He Matt,This would be very nice if this will become available for LOB apps published via the Azure Application Proxy.To be sure only that specific protected app can connect to the backend system.- Anonymous
November 02, 2016
Hey Nils. I noticed you added a Uservoice item for this request, that's the best path for getting the request actioned. For those reading this, feel free to up-vote Nils Uservoice item.https://microsoftintune.uservoice.com/forums/291681-ideas/suggestions/16918564-application-conditional-access-for-lob-appsMatt
- Anonymous
- Anonymous
November 10, 2016
I simply can't get this working as described for Exchange Online. If a user is a member of the group defined in "restricted user group" (EMS users in the example above), they receive the "You can't get there from here" warning stating "access rules set by restrict applications that can be used to open this resource". There is a MAM policy applied to Outlook for Android App which applies to this same group (kept simple for testing and just requires PIN). I am using the latest Outlook for Android client. The behaviour is the same regardless of whether the setting is set to "Allow apps that support Intune app policies" or "Allow All Apps".- Anonymous
November 20, 2016
Are you still having this problem Dae?
- Anonymous
- Anonymous
December 02, 2016
I am having a hard time piecing this all together. I have a set of users that I want to force to use Outlook mobile to access exchange online. They all have Intune and Azure AD licenses and some of them are enrolling devices with Intune and some of them are not. I have configured Intune compliance policies, Intune Exchange CA, Azure MAM and Azure Exchange CA - none of which seem to enforce the use of Outlook. The only way I have gotten this to work is if I specifically configure Exchange Active Sync rules to allow Outlook clients and block everything else. In the Azure portal I do see applications reporting but there really isn't any information of what policy is actually applying. Having multiple consoles and locations to configure policy is so typical Microsoft - can't believe how overly complex this is. Please help! - Anonymous
December 02, 2016
What the logical OR if I have devices enrolled with InTune, do not use InTune CA and then use Azure CA? Will that force only specific users to use Outlook per the Azure CA policy?- Anonymous
December 04, 2016
Hi JB. I'm assuming you posted previously as Jeff Bailey as the question is similar! The logical OR is most likely causing your confussion. If you have MAM CA AND Exchange CA (Device CA/Traditional CA) the logical OR kicks in. So, if user x is targeted with both a MAM CA policy AND a Device CA policy, they can use either. For example, if x user opens the native mail app and enrolls their device they'll be able to get access to email. OR, if x user just opens the Outlook app and doesn't enroll their device, they'll be able to get access to email. So if you want to ensure your users are enrolling their devices AND force them to use Outlook over other EAS mail clients, you'll still have to use a combination of EAS ABQ rules and ADFS Claims. Hope that helps.- Anonymous
December 05, 2016
Yes, I posted both - thought my first post got lost.Thanks, this makes more sense. I don't have ADFS and have been using Exchange device access rules to force outlook on enrolled devices. So it seems I am doing all that I can to catch both enrolled and unenrolled device.
- Anonymous
- Anonymous
- Anonymous
December 22, 2016
Would this work for a scenario of wanting Outlook to work on personal Windows 10 devices when the app is managed only? (And prevent access via OWA or standard personal non-MAM Outlook)- Anonymous
December 29, 2016
Hi @SB_UK - we dont have any 'MAM' policies available for Windows 10 devices. You'll need to use WIP to provide DLP to Windows devices. Matt
- Anonymous
- Anonymous
January 24, 2017
Hi MattWill this work for Intune/ConfigMgr integrated scenario?- Anonymous
February 21, 2017
Hi legionx. Yes, these features will work for hyrbid configurations. Matt- Anonymous
December 18, 2017
How is this actually done in Intune Hybrid environment? Anybody have docs/instructions?- Anonymous
January 08, 2018
Hi Emmi. This is performed exactly the same way for Hybrid or Standalone, as the feature is configured in Azure AD and not Intune. Thanks! Matt
- Anonymous
- Anonymous
- Anonymous
- Anonymous
February 13, 2017
Our tenant does not have the new portal yet ... can this be done with the old/classic portal?- Anonymous
February 21, 2017
Hi James. The MAM CA features are in a seperate Azure Blade called "Intune App Protection", and doesn't require any migration to the new portal. Every customer should aready have access to these features. Matt
- Anonymous
- Anonymous
March 13, 2017
Why outlook groups app is not listed. I tried that but then the outlook groups mobile app on my iphone stop working. This is a big show stopper.- Anonymous
March 13, 2017
Hi Ammr. Outlook Groups is currently not supported. It is by design to block access as the app is not managed. Matt- Anonymous
March 14, 2017
Outlook Groups is not supported and not managed? So Imagine this.. Office 365 product team are selling office groups everywhere. Now we are selling office groups and its mobile app everywhere to busienss people.Now we want to do this conditional access to enforce outlook, and now we cannot do this because what o365 team is promoting (office groups) is not managed.So now we are back in square one. I want you to take a moment and put yourself at my place. You want to restrict access to EXO by app to comply with intune MAM policies, but you cannot because this will block outlook groups app. Now Microsoft is saying this is by design :) so is by design means putting my in a place where i cannot use two different services from Microsoft (Intune MAM by restricting apps accessing EXO, and the use of Office Groups) ?Further more, Microsoft Teams is getting MAM support and it is managed while it is new app. Office groups app is there from long time and is not yet managed. How come?- Anonymous
March 14, 2017
Understand the frustration Ammar. The team is working on solutions, but no details are available as yet. I suggest you make your feelings known via UserVoice (https://microsoftintune.uservoice.com)- Anonymous
April 07, 2017
this is really sad, it's also a problem for the teams app.- Anonymous
April 10, 2017
Hi JohanVjr. The Teams apps for iOS and Android support MAM policies and will support Conditional Access in the future. As the app does not support it yet, we don't allow the data access as a security precaution.
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
March 30, 2017
I've run through a trial with both Android and iPhones. I wouldn't say this is ready for production. One only has to look at the reviews for the Company Portal and Microsoft Authenticator apps to see there are consistent authentication issues which kills ActiveSync. There's no warning either. Your emails just stop syncing and you won't know until you open the app to check. After this happens, MAYBE an update to the apps, an android system file update, or an account repair will fix it. Usually, you must remove everything, reinstall, and "re-register" the device. "Contact support and provide us the logs from the device", isn't acceptable for a company of any significant size of staff.In addition, to state it's without enrollment is a bit deceptive. The requirement to install and register your device with the above mentioned apps is a form of enrollment. Enrollment and registration are synonyms.Finally, if your end users use OneNote, Teams, or anything other mobile Office app besides OneDrive, Outlook, Skype, or Sharepoint. MAMWE will put an end to it.I really like the mobile Office suite. I don't like Intune, MAMWE, Company Portal/Authenticator, or Microsoft's decision to shut 3rd party MDM/EMM providers out of the ecosystem.Maybe it will be ready in the months ahead. At this point, everyone using it is a beta tester.- Anonymous
April 10, 2017
Sorry to hear your having such a bad experience, Chris. If your using Office 365 & Ourlook for iOS/Android, you shoudn't be getting ActiveSync auth errors as Outlook doesn't use EAS (it uses REST), so I'm not sure why you'd be having EAS auth issues. Are you trying to use Exchange on-prem or Exchange Online? I'm also surprised you're having to "re-register" the device in a MAMWE scenario. Once the device is 'registered', policy should hit the app directly in iOS or via the Company Portal in Android. There should be no need to "re-register" ever. As for the difference between "Without Enrollment" and "With Enrollment"; it's the control we have over the device, and the user/device impact. With enrollment scenarios mean we need full admin of the device, and can do full wipes, push apps/etc. Without enrollment means we dont use the MDM channel, and really have no control over the device other than delivering policies to the apps we manage. So while there still is a device registration (AAD registration), it's only so that the apps can receive the appropriate policy, rather than Intune manage the device. Without some kind of registration, you wouldn't be able to remote selete wipe certain devices ;) Anyway, sorry your having such a hard time. Please feel free to reach out to our support teams if you'd like any dedicated help. Matt
- Anonymous
- Anonymous
April 12, 2017
When I enable Exchange Online CA ( MAM only ), what impact, if any, it has on Windows 10 Computers trying to use the built in Mail App to connect to exchange?I have it current enabled targeting a large pilot group and recently was told that a few users complained that the Mail app stopped sync on their home Windows 10 computers.Could it be related?Also,I add to the list of frustrations.Being able to block exchange via CA is a great feature but it takes away from the MAM only that I was trying to sell the users on.As soon as you enable Exchange Online CA, users are prompted to Register their devices which at that point, why not just use Intune.Also, my pilot group has been complaining about sync issues and crashes on their apps.Any information would be great. thank you.- Anonymous
April 14, 2017
Hey Patrick. If you enable MAM only, it should only affect iOS and Android devices. Since the Windows 10 'Mail' app can use EAS, it might be that. I suggest reconfiguring the mail profiles & they should use modern auth & connect successfully. RE the Exchange CA question, when you enable MAM CA users should not be required to enroll their device and they'll be required to use the Outlook app. If you enable BOTH MAM CA and Device CA, the users will be able to do either; not enroll and use the Outlook app OR enroll and use the native mail apps. So in your situation where you dont want them to enroll, just use MAM CA and force your users to use Outlook with MAM. For sync issues, in most circumstances Intune doesn't proxy any data so shouldn't cause sync issues. If there are crashes, we can normally diagnose those fairly easily using the Intune logs. Feel free to log a support case and provide the crash dumps. Hope that helps. Matt
- Anonymous
- Anonymous
June 06, 2017
To all the administrators thinking of enabling this please put some thought behind it regards to security vs convenience. We have enabled it and only allow the Outlook app.We recently did a poll and 2/3 of users hate this setup as the Outlook app simply isn't that great and lacks functionality users have become dependent on. Some users even went that far to stop using mail on their phones. Also what the heck is up with the one-way contact sync. Seriously...- Anonymous
June 14, 2017
Agree Josh. There are certainly some differences in functionality, but there are areas in which Outlook does a much better job too. RE the contact sync, Outlook shipped an update last week that allowed contact edits/additions.- Anonymous
June 21, 2017
Here is the contact sync by the way. https://blogs.office.com/2017/06/05/improving-people-in-outlook-for-ios-and-android/
- Anonymous
- Anonymous
- Anonymous
June 14, 2017
Is there a way to inform the user to download the Outlook client if they try to access this via a native app?- Anonymous
June 14, 2017
There isn't, but that's a good idea. Suggest you raising this via UserVoice https://microsoftintune.uservoice.com
- Anonymous
- Anonymous
June 30, 2017
Hi Matt,Is MAM without Enrollment works for exchange on-prem users, since our organization is a hybrid mode.Nissan.- Anonymous
June 30, 2017
Hi Nissan. No, MAM is currently not supported for on-prem users. Matt
- Anonymous
- Anonymous
July 11, 2017
Hi Matt,My vendor told me that in order to get this conditional access feature, it is necessary for us to subscribe to Microsoft Enterprise Mobility+Security E3. Only subscribe to Intune is not enough. Do you know is above statement correct or not?- Anonymous
August 24, 2017
Hi Martin, you could just get a license for Azure AD Premium in addition to the Intune license, but getting the EMS license is generally more cost effective. See licensing section here: https://docs.microsoft.com/en-us/intune-classic/deploy-use/restrict-access-to-email-and-o365-services-with-microsoft-intune
- Anonymous
- Anonymous
August 10, 2017
"Also note that for Device CA targeted users (traditional CA), if a user is targeted for both policies the compliance is determined in a logical OR.For example, if the device is managed by Intune and CA compliant the device will have full e-mail access, including the native EAS mail apps. OR, if the device is not managed but has the Outlook app it will have full access via the Outlook app only. This is really a very good experience for BYO vs COD scenarios, where we’d enroll a corporate owned device, but require Outlook and MAM for a personally owned device."I can't get this working as described. When a user is targeted for both policies, they are notified to download the Outlook app via a message in their inbox, even though their devices in Intune enrolled and marked as compliant in the portal. Has something changed?- Anonymous
August 15, 2017
Be sure your not using the new Intune/AAD Conditional Access (found in the Azure console), otherwise you'll get a logical AND. Matt- Anonymous
August 16, 2017
So the logical OR condition can no longer be used in the new Azure Portal? How this needs to be done in the new portal?- Anonymous
August 24, 2017
Hey Thomas. Correct, today there is no way to do the OR inside the Azure Portal. Happy to say in the next few weeks an option will be available though, so please check back soon! Matt
- Anonymous
- Anonymous
August 24, 2017
Is there anyway to configure MAM CA and AAD CA to use a logical OR rather than AND, as per the old method? This is because we want to allow users to either use their personal device with Outlook or enrol their corporate device to access email.- Anonymous
August 24, 2017
Hey Rob. Today there isn't, but in the next few weeks there will be an option appear!- Anonymous
August 29, 2017
Great news, thanks Matt!
- Anonymous
- Anonymous
- Anonymous
August 24, 2017
Hmm, i thought using the new Intune console was required? Is there no way to achieve this using the new console?- Anonymous
August 24, 2017
Hey Josh. No way today, but an option is shipping in a few weeks. Matt- Anonymous
September 28, 2017
Any update on this? Few weeks have come and gone, i've got LOADS of clients waiting for this! Thanks!- Anonymous
October 16, 2017
Hey Chris, thanks for the nudge. I've made the update! Matt
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
- Anonymous
August 18, 2017
Is there a way to disallow the OneDrive, Skype for Business and Microsoft SharePoint and only allow users to use Outlook? We have compliance issues which make those apps problematic.- Anonymous
August 24, 2017
Hey Abraham, because all of the apps touch data across each other, there is no way to isolate these. One solution that's been used in the past is to not license users for the apps you want to block. Ie, don't license users for OneDrive and they wont have access at all. Matt
- Anonymous
- Anonymous
October 17, 2017
We had tested this and it fails.Sharing the info received from Microsoft.Intune CA Policy only works on EAS and OWA protocol. 3rd party email apps like Bluemail or Type App, works on EWS protocol which cannot be managed via Intune. Hence the users are able to access mails. Currently there is no ETA to when the EWS protocol will be supported by the Intune CA Policy- Anonymous
October 18, 2017
Hi Clawscorp. What fails? You're correct about EWS. We suggest blocking EWS via Exchange Online or ADFS. There's plenty of guides online on how to do this.
- Anonymous
- Anonymous
November 10, 2017
Great Article!I seem to be having the same problem as a few other people in that I cannot get this to work in the way that is described here.After reading the post, I assumed the below was possible:All un-enrolled iOS/Android devices can use MAM Conditional Access policies to restrict email to the outlook app only.All enrolled iOS/Android devices can use the Outlook app AND the native email applications on their devices via the AAD Conditional Access policy (PIN access for outlook no longer applies as the device PIN is managed)Is this correct?I followed the steps under the 16/10/17 edit while still having the MAM-CA settings in effect but my enrolled devices still cannot use the native email apps (iOS and Android test phones). I used the same user group for the MAM Conditional Access and Azure Conditional Access policies or is this incorrect?It would be great to get this working so any pointers / help would be appreciated!- Anonymous
November 10, 2017
Hey Matt. So here is the scenario you're looking to achieve.1. Un-enrolled devices - users must use Outlook Mobile with MAM2. Enrolled devices - users can use either native mail apps or Outlook Mobile with MAMTo achieve this, all you need to do is disable the MAM-CA functionality in the Intune App Protection blade! This will give you the logical OR you are after. IE - An approved app (Outlook) OR a compliant device (enrolled & compliant in Intune)Please report back on how you go with this, as it is indeed a very popular scenario!Matt- Anonymous
November 13, 2017
Thanks for the info! I changed the MAM-CA functionality back to allow all apps (and no group restrictions) as you suggested. I then found that email was working on native and the outlook apps without registering. Seeing that, I went back to the AAD-CA policy and instead of having 0 cloud apps selected (as per your screenshot) I added Office 365 Exchange Online. That triggered the below behaviour: On the iOS device, I've tried adding the email account to the outlook app and this happens:Outlook app prompts me to log inIt notifies that the devices needs to be registered and I need to install the authenticator appI follow the link, download the Authenticator appAuthenticator App prompts me to login againOops, something went wrong message.I am unable to register and use the outlook app. This error message seems to be pretty common from what I have seen google wise.The Android device was able to add the account and send emails from it's native email app without registering. When I used the gmail app it then prompted and successfully registered the device. I am using a pretty basic android device though, so maybe it's just an incompatibility / unsupported feature? Android 5.0.2 with KNOX 2.3 SM-G360FI've also found that when devices are enrolled in Intune and I remove it from the company portal app, it also deletes the Authenticator app. Shouldn't it delete the company data only? I use Authenticator for my personal accounts and it deleted the app and all data instead of just the company info.- Anonymous
November 20, 2017
Hi Matt. You should ensure the device you're testing with isn't MDM enrolled, or previously MDM enrolled with the Corp account still present in the Authenticator app. I see the "Oops" error generally when there is already a Corp account in the Authenticator app, as Outlook has trouble associating itself with the Auth broker (authenticator) if the corp creds were created elsewhere (ie, via MDM enrollment, etc). RE the Android device, this scenario should work for all Android devices as it's basically blocking the EAS protocol. I'd suggest ensuring everything is setup correctly and if it still doesn't work, raising an AAD support ticket (Conditional Access is actually an AAD feature, not an Intune feature). Matt
- Anonymous
- Anonymous
November 23, 2017
Hi Matt,using the old portal with the logical OR, I was able to set it so that un-enrolled devices would use Outlook + MFA, and Enrolled devices wouldn't require MFA.This was achieved with a CA rule that said Intune OR MFA.Is there any way to recreate that scenario now?Thanks!- Anonymous
December 07, 2017
Hey Martin. The MFA function is a function of Azure AD, so you'll need to take a look at your AAD MFA configuration. It's not something I've done before so I'm unable to help unfortunately.
- Anonymous
- Anonymous
- Anonymous