SSL Troubleshooting-TROUBLESHOOTING STEPS FOR SERVER SIDE SSL PROBLEMS
I would suggest to go through the below article which talks about SSL handshake before going through the Troubleshooting part.
https://blogs.msdn.com/b/kaushal/archive/2013/08/03/ssl-handshake-and-https-bindings-on-iis.aspx
Scenario 1: Page cannot be displayed error while browsing over https. it works over http.
Troubleshooting Steps:
Step1: Do an iisreset, browse the page and again do iisreset . Go through the Event Logs and filter by Schannel
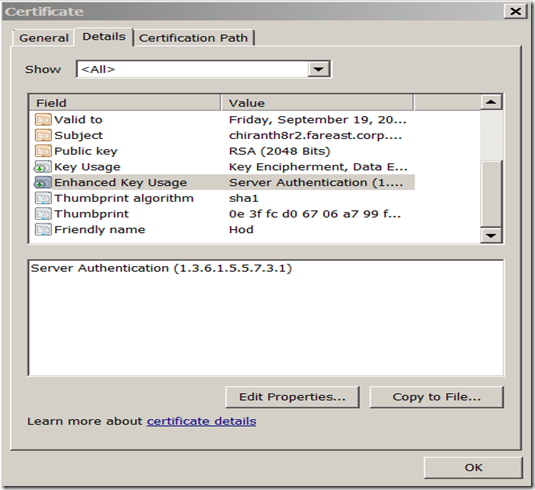
Step2: Check if the certificate has a primary key. You can check this by opening a certificate. If it doesn’t have a private key then run this command.
Certutil –repairstore my “thumbprint of the certificate”.
This command will rebind the private key to the certificate.
You can also run the certutil command with –verify switch to check if there is any problems with the certificate.
Step 3: If the command fails we might need to get a new certificate with a private key(new .pfx file with private key).
Step 4: Check permissions on Machine keys C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys in windows 2008 machines and c:\documents and setting\all users\Microsoft\Crypto\rsa\machine keys in windows 2003 machines. check if administrators and system have permissions on the folder. if not take ownership of the folder and add the accounts and for testing you can give control to everyone, replace the permissions on the child objects with the parents permissions and try to check if you are able to access the site.
Step 5: If the command succeeds but if the issue has not yet been resolved create a self-signed certificate and try to browse by adding a binding with the self-signed certificate.
Step 6: If self-signed certificate works the problem is with the cx certificate. Ask him to get a new certificate (.pfx file).
Step 7: If you are not able to create a self-signed certificate ( get an error), you might not have proper permissions for the machine key folder.( C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys). For info on default permissions on the machine key folder go through the following KB https://support.microsoft.com/kb/278381 .
Step 8: After setting the appropriate permissions for the machine key folder, delete the cx certificate (make sure he has a back-up) and reimport the cx certificate using mmc console. Now add a binding with the cx certificate and try to browse.
Step 9: if you see that you have all the proper permissions and certificate also looks good, check if the problem is with specific clients or all clients. Browse locally and see if it works. it might be possible that issue might be with some of the machines only. for this you need to check which versions of SSL is your server supporting. to check the versions being supported you can follow Step 10
Step 10: check the registry keys to see if the protocols are enabled (SSL/TLS). The path for the registry keys is
| [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\Schannel\Protocols]. |
By default u won’t the entries. Check if the entries are there and if it’s disabled. If disabled try to enable that.
Step 11: Also on the client check which version of SSL is your IE supporting. you can see that in advanced setting of IE.
Step 12: You can also take a network trace and check which version is sent by the client to the server, if the server doesn’t sipport any of the versions sent by the client the handshake will fail and you might end up seeing page cannot be displayed error. below is how you can see that in a network trace.
In the below example you can see that client is sending TLS 1.0 as the protocol supported.
403 9:07:37 PM 2/18/2014 8.9950582 iexplore.exe 10.171.66.34 any.edge.bing.com TLS TLS:TLS Rec Layer-1 HandShake: Client Hello. {TLS:157, SSLVersionSelector:156, TCP:153, IPv4:152} |
Frame Details
Frame: Number = 403, Captured Frame Length = 175, MediaType = ETHERNET + Ethernet: Etype = Internet IP (IPv4),DestinationAddress:[10-BD-18-E5-44-00],SourceAddress:[64-31-50-21-9D-DD] + Ipv4: Src = 10.171.66.34, Dest = 204.79.197.200, Next Protocol = TCP, Packet ID = 28447, Total IP Length = 161 + Tcp: Flags=...AP..., SrcPort=55735, DstPort=HTTPS(443), PayloadLen=121, Seq=538415128 - 538415249, Ack=685721231, Win=33120 (scale factor 0x2) = 132480 TLSSSLData: Transport Layer Security (TLS) Payload Data - TLS: TLS Rec Layer-1 HandShake: Client Hello. - TlsRecordLayer: TLS Rec Layer-1 HandShake: ContentType: HandShake: - Version: TLS 1.0 Major: 3 (0x3) Minor: 1 (0x1) Length: 116 (0x74) - SSLHandshake: SSL HandShake ClientHello(0x01) HandShakeType: ClientHello(0x01) Length: 112 (0x70) - ClientHello: TLS 1.0 + Version: TLS 1.0 + RandomBytes: SessionIDLength: 0 (0x0) CipherSuitesLength: 24 + TLSCipherSuites: TLS_RSA_WITH_AES_128_CBC_SHA { 0x00, 0x2F } + TLSCipherSuites: TLS_RSA_WITH_AES_256_CBC_SHA { 0x00, 0x35 } + TLSCipherSuites: TLS_RSA_WITH_RC4_128_SHA { 0x00,0x05 } + TLSCipherSuites: TLS_RSA_WITH_3DES_EDE_CBC_SHA { 0x00,0x0A } + TLSCipherSuites: TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA { 0xC0,0x13 } + TLSCipherSuites: TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA { 0xC0,0x14 } + TLSCipherSuites: TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA { 0xC0,0x09 } + TLSCipherSuites: TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA { 0xC0,0x0A } + TLSCipherSuites: TLS_DHE_DSS_WITH_AES_128_CBC_SHA { 0x00, 0x32 } + TLSCipherSuites: TLS_DHE_DSS_WITH_AES_256_CBC_SHA { 0x00, 0x38 } + TLSCipherSuites: TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA { 0x00,0x13 } + TLSCipherSuites: TLS_RSA_WITH_RC4_128_MD5 { 0x00,0x04 } CompressionMethodsLength: 1 (0x1) CompressionMethods: 0 (0x0) ExtensionsLength: 47 (0x2F) - ClientHelloExtension: Renegotiation Info(0xFF01) ExtensionType: Renegotiation Info(0xFF01) ExtensionLength: 1 (0x1) Data: Binary Large Object (1 Bytes) - ClientHelloExtension: Server Name(0x0000) ExtensionType: Server Name(0x0000) ExtensionLength: 13 (0xD) NameListLength: 11 (0xB) NameType: Host Name (0) NameLength: 8 (0x8) ServerName: bing.com - ClientHelloExtension: Status Request(0x0005) ExtensionType: Status Request(0x0005) ExtensionLength: 5 (0x5) Data: Binary Large Object (5 Bytes) - ClientHelloExtension: Elliptic Curves(0x000A) ExtensionType: Elliptic Curves(0x000A) ExtensionLength: 6 (0x6) CurvesLength: 4 (0x4) NamedCurve: secp256r1(0x0017) NamedCurve: secp384r1(0x0018) - ClientHelloExtension: EC Point Formats(0x000B) ExtensionType: EC Point Formats(0x000B) ExtensionLength: 2 (0x2) ECPointLength: 1 (0x1) ECPointFormat: uncompressed(0x00) |
Note:
Step 13: so check for Listen only list in the registry to check if the application is listening to only a specific ip address and u might have your https website name getting resolved into a different ip. By default this key won’t be present. The path of the registry key is as below.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters\ListenOnlyList |
Step 14: If still the problem persists take a network trace using netmon or wireshark. And after getting the trace apply the filter for “SSL OR TLS” . If the network trace contains server hello and client hello then there is no problem from IIS side.
Step 15: You can also follow some advanced steps like enabling S-channel or Capi2 logging. You can verify the SSL Handshake using S-channel logging. To enable S-channel logging the steps are given below
1. Start Registry Editor. To do this, click Start, click Run, type regedt32, and then click OK.
2. Locate the following key in the registry:
| HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL |
3. On the Edit menu, click Add Value, and then add the following registry value:
| Value Name: EventLogging Data Type: REG_DWORD |
Note After you add this property, you must give it a value. See the table in the "Logging options" section to obtain the appropriate value for the kind of events that you want to log.
4. Exit Registry Editor.
5. Click Start, click Shut Down, click to select Restart, and then click OK to restart the computer. (Logging does not take effect until after you restart the computer).
The value of the REG_DWORD can be any of the below.
0x0000 |
Do not log |
0x0001 |
Log error messages |
0x0002 |
Log warnings |
0x0003 |
Log warnings + error messages |
0x0004 |
Log informational and success events |
0x0007 |
Log warnings + error+ informational and success events |
After enabling the S-channel logging before browsing the page run the command
net stop http /y
if after running this command system hangs then u will have to restart the system to enable the logging.
To enable CAPI2 Logging go to event viewer and traverse to the path given below and right click and enable logging.
Applications and Services Logs\Microsoft\CAPI2\operational
Scenario 2: A specific logon session error while adding a SSL binding.
Troubleshooting
Step 1: Check if we are using a server certificate or client certificate or a dual purpose certificate(it should be either server or dual purpose certificate).
Step 2: How have we imported the certificate through IIS or MMC console.
Step 3: If we have imported the certificate using IIS, did we uncheck the box Allow certificate to be exported. ( it’s a know limitation in IIS UI and we do not recommend the users to import and certificates through iis certificates console and strongly recommend it to be done in MMC console).So if we have imported using IIS, delete that certificate and import that certificate using MMC console and check now if while again binding it throws an error.
Hope the article was helpful ![]()
Technorati Tags: SSL,certificate,page cannot be displayed,troubleshooting,certificates,tls
Comments
- Anonymous
February 28, 2015
Nice article, is there a method of enabling CAPI logging via GPO ore Registry settings? - Anonymous
March 02, 2015
Hi Jeff,That's an interesting question. I haven't seen any articles that talks abt the registry changes to enable CAPI2 logging. so I took some traces on my machine to see what happens when I enable capi2 logging from event logs. I see that a DWORD called Enable is created in HKLMSystemCurrentControlSetserviceseventlogMicrosoft-Windows-CAPI2/Operational and the value is 1. I haven't tested it though. but this should achieve the purpose and we will get to know more by testing with these registry keys - Anonymous
March 02, 2015
The comment has been removed