Have you ever wondered what web service URLs are used by the Lync client? STrace is your tool.
Hi Everyone
I recently stumbled onto a handy little tool called STrace, from Microsoft, which can be used to interrogate a targeted executable's web service calls.
In the world of Lync, especially when your environment has multiple pools and maybe even a director pool, it can be tricky understanding what web service URLs are being used by the Lync client. STrace can be used to attach to your Lync client, or rather run your Lync client and then capture to a log file all of the web service URLs that are called during a particular activity. Now there are other ways of achieving this, i.e firing up Netmon and watching a network trace, but STrace is the easiest tool I have seen for achieving this goal.
What is STrace?
According to the STrace website the tool is used for:
STRACE is a socket/SSL tracer that is based on the "detours" utility. The tool has been specifically designed to generate a LOG for Internet Explorer but it can be used with many other applications. (Including Lync :) )
Using STRACE with Internet Explorer is equivalent to use a (non full) debug build of WININET.DLL to generate a WININET LOG. The STRACE LOG contains clear text HTTP traffic (with socket information) and encrypted/decrypted SSL data.
From the STRACE LOG, you can "replay" a full navigation scenario using the HTTPREPLAY tool. This can be useful to reproduce a problem or browse web sites offline...
Using STrace
So how do we use it? First of all you will need to download STrace from the Microsoft website. You can get the tool here https://www.microsoft.com/en-us/download/details.aspx?displaylang=en&id=7643.
The STrace download is a .MSI so you'll need to install the MSI on the machine you wish to interrogate. The STrace utility by default installs to the C:\Program Files (x86)\STRACE\ directory on your machine.
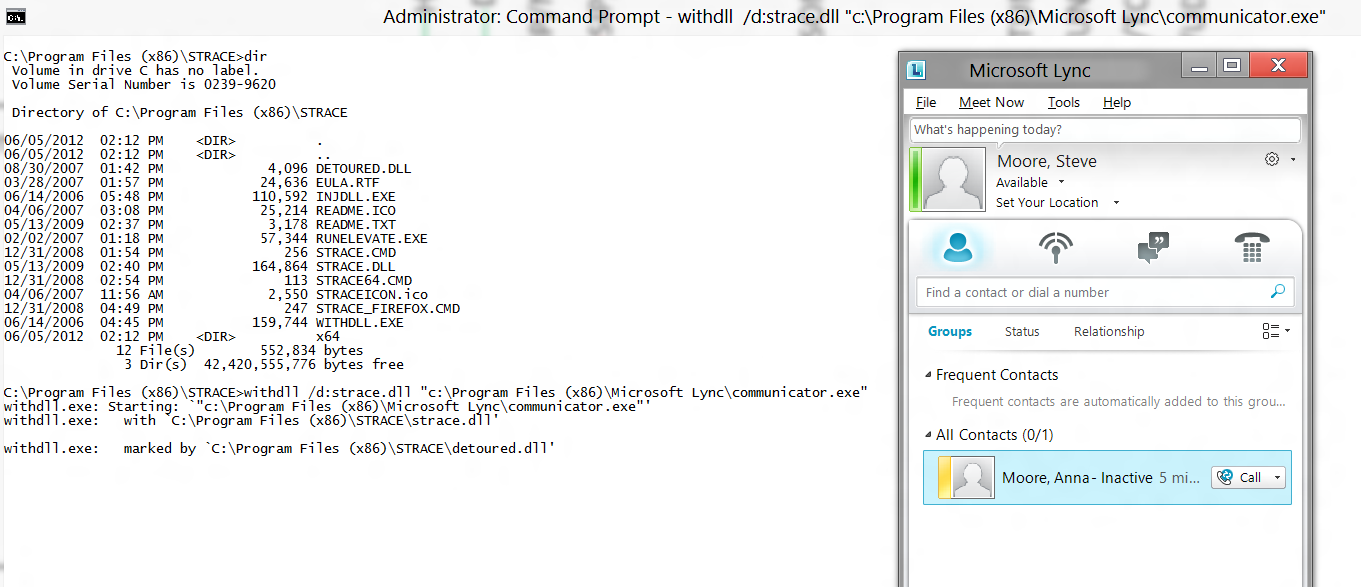
Once you have installed STrace fire up a Command Prompt as an administrator and navigate to the STrace installation directory (remember real men don't click so don't use the GUI) . If you elected to not use the default installation directory navigate to the directory where you installed the tool. Perform a "Dir" in the installation directory and see what is installed as part of the STrace .msi.
As you can see from the directory listing above, the STrace tool is actually a .DLL, that is used in conjunction with the WITHDLL.exe utility. Looks like there is even a Strace_Firefox.cmd there, interesting, not sure why you would even need to use that.
Starting the Communicator Client with STrace
So let's get stuck into it. Before you start, make sure you exit from your trusty instance of the Lync client (I am hoping you are running the Lync client cumulative update from March 2012 :)). Next, from your Command Prompt in the STrace installation directory, run the following command:
withdll /d:strace.dll "c:\Program Files (x86)\Microsoft Lync\communicator.exe"
The Lync client will start up and you'll see that the WithDLL.exe is sitting continuing to run in your Command Prompt window watching all that the Lync client is doing. Don't Ctrl-C on that Command Prompt as that will terminate the WithDLL.exe process and stop the whole capturing process. Although it's a little hard to see in this low res pic, the WithDLL.exe is sitting there running, and will continue to run as long as my Lync client is running.
Generate some Web Traffic and create the STrace Log
Now that you have your marvelous Lync client up and running, kick off an IM session (with powerpoint slide) with one of your Pals or start a application sharing instance with the boss. Maybe share your instance of the Command Prompt running WithDLL.exe I am sure that will definitely impress them. As well as the Lync client sign in process, while executing some of the above suggested Lync functions you will have made some Lync web service calls. The WithDLL.exe will have caught these calls and will when you exit the Lync client create a log file with all of your activity on the desktop of the person you are running the Lync client as.
Once you have generated some activity in your Lync client you can exit from the client. Don't just sign out, use the File Menu and Exit out from the client altogether. Once you have done that the WithDLL.exe will also terminate. While terminating the WithDLL.exe will create a log file on your desktop (STRACE_COMMUNICATOR_XXXX_DDMMYYY.....log). You can see from the diagram below that I have kicked off a few traces hence the 4 or so logs. Next step is to find the most recently created log file, as we are going to use this file to perform some analysis.
Analysing the Log File
Now that you have a log of all the web service calls the Communicator client made, we need to analyse the log file. This is performed using the HTTPReplay tool which is also downloadable from Microsoft. You can download HTTPReplay here https://www.microsoft.com/downloads/details.aspx?familyid=d25ba362-c17b-4d80-a677-1faff862e629&displaylang=en&tm.
As per TechNet, the HTTPReplay is used to:
HTTPREPLAY is a SOCKTRC plugin allowing to analyze and replay HTTP traffic from STRACE or WININET log. You can use this tool to "replay a web server" without needing to setup IIS. The main goal of this tool is to help building a repro scenario when customer can't provide one.
So download HTTPReplay and install the tool. It like STrace is a .MSI. The HTTPReplay tool installs in the C:\Program Files (x86)\HTTPREPLAY\ directory. In a Command Prompt, navigate to the HTTPReplay installation directory, making note of the STrace log file we created in the previous stage.
Once in the HTTPReplay directory execute the following command to have HTTPReplay analyse the log file generated by STrace.
HTTPREPLAY.CMD C:\STRACE_COMMUNICATOR_PID_5780_31052012_014441.LOG /showfullresponse
The HTTPReplay then goes off and analyses the STrace log with the assistance of SockTrc (a part of the HTTPReplay MSI), and generates a nice HTML report. In the Lync session that I observed with Strace I performed only a few minor actions, and you can see that even in that small session a number of web service calls were made:
Web Services Results
I've attached the actual HTML report (at the bottom of the blog), as the image above is a little hard to view clearly (sorry I can only use picture files that are up to a particular size). You can see that my Lync client has gone to the following Web Services:
- https://se01.contoso.org/CertProv/CertProvisioningService.svc/mex
- https://se01.contoso.org/WebTicket/WebTicketService.svc/mex
- https://se01.contoso.org/CertProv/CertProvisioningService.svc/WebTicket_Proof_SHA1
- https://se01.contoso.org/locationinformation/liservice.svc/mex
- https://se01.contoso.org/RgsClients/AgentService.svc/mex
- https://se01.contoso.org/groupexpansion/service.svc/WebTicket_Bearer
As you can see there is some handy information in the report about what is happening under the hood and the report makes it pretty clear what URLs are being used by the Communicator client (for that session). In more complex environments (and Lync client usages) you are going to see a lot more interesting traffic.
One thing to note too is that you can use STrace and HTTPReplay for more than just the Lync client, you may also want to have a look at what the Outlook client does or other applications that are of interest to you.
Happy Lync'ing
Steve
Comments
- Anonymous
February 04, 2016
This is slightly confusing naming, as there is a well known Unix/Linux utility called strace which traces system calls.