Removable Storage, Group Policy and Windows Server 2008 and Windows Vista
“I don’t want my users copying data to removable drives. How can I prevent this?”
Mike here again to answer this common question asked to our team. Removable drives are widespread. Current mobile devices can now store up to 8 GB of data on a micro-SD card, which is no bigger than your thumb nail. Eight gigabytes is a huge amount of data and it could be your company’s Intellectual Property (IP) going out the door. There is a need to protect your company’s sensitive information from being transferred to removable storage devices; Group Policy in Windows Server 2008 and Windows Vista can help you.
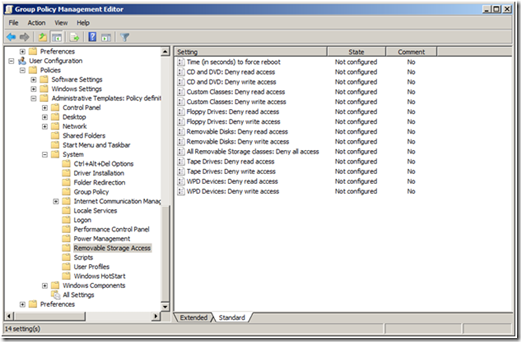
You can control access to six removable storage categories (actually seven but the seventh category controls access to ALL removable storage devices). These categories include CD and DVD, Floppy Drives, Removable Disks, Tape Drives, and WPD devices.
Figure 1 Removable Storage Policy Settings
Today’s computers usually do not included a floppy drives because the amount of data that fits on a floppy disk seems trivial in the age of one terabyte drives—regardless, you can restrict access to floppy drives, which includes USB floppy drives. Removable drives included classic USB thumb drives. WPD devices include media players, cell phones, CE devices, and some auxiliary displays. There is a custom category that allows you to identify the unique identifier of a device and control access of that device based on the unique ID.
Each device category provides two types of access control—deny read and deny write. These policy settings apply to Windows Vista or later (to included Windows Server 2008) and can co-exist in GPOs applying to clients earlier than Windows Vista; however these older operating systems ignore the policy settings.
You can find these policies under the Removable Storage Access category, under User or Computer Configuration\Policies\System\Removable Storage Access
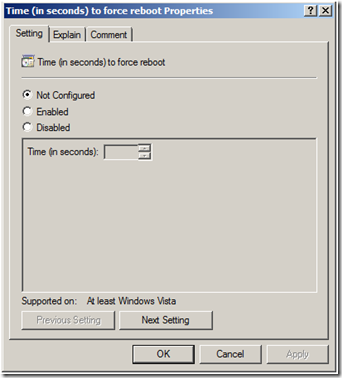
These policy settings change the security descriptor on the removable objects. Changing the security descriptor requires a computer reboot. Window's does not reboot the computer when the policy changes these security descriptors. However, Removable Storage provides a policy setting to which you can enable to force a reboot. Enable the Time (in seconds) to force reboot policy setting and provided value (in seconds) for which Windows waits before rebooting the computer to apply the new security descriptors for removal drives.
Figure 2 Removable Storage Reboot Policy
So, keep your Intellectual Property secure by controlling access to removable storage devices. Delegate write permissions to a limited user set, or limit removable storage write access to a single workstation. You can do your part to keep your company's sensitive data where it belongs.
- Mike Stephens
Comments
- Anonymous
August 25, 2008
PingBack from http://windows2008security.com/security-policy/removable-storage-group-policy-and-windows-server-2008-and/