Migrated Users Get Prompted To Change Password at First Logon Even After Migrating Their Password with the PES
Hello all, Jason (J4) here again. I recently experienced an issue with ADMT and the Password Export Service (PES) tool that I wanted to quickly bring to everyone’s attention. The new revision of the ‘ADMT v3.2 Migration Guide’ will include an update to the documentation, but wanting to post here as it’s also something relevant to both ADMT versions 3.0 and 3.1 - which won’t get updated.
When one uses ADMT and the PES service to migrate passwords of user accounts, the migrated user accounts get the option “User must change password at next logon” enabled by default. Hence, when the user logs onto the new target domain they are required to change their migrated password at first logon.
After some investigating and discussion with ADMT Program Managers and Developers, this is by-design type of behavior to prevent what is considered a security risk. ADMT and the PES service has no way of determining if the users migrated password is compatible with the target domains password policy; specifically the more sensitive password complexity settings.
Here are a couple of options in maintaining the end users passwords that they were using in the source domain and commonly the end-goal/desire when using the PES service to migrate users passwords from the very beginning:
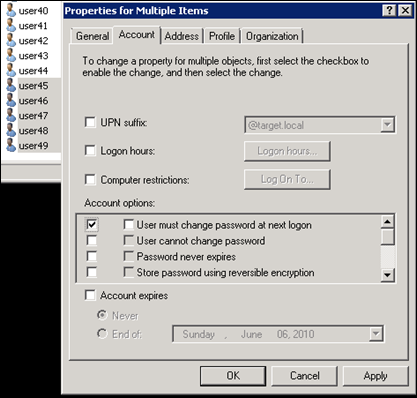
1.) The obvious – manually toggle the “User must change password…” check box within the ‘Active Directory Users and Computers’ snap-in for the user account’s properties and prior to the end user logging into the target domain for the very first time. As represented here with the screen shot, this can also be done by multi-selecting the migrated accounts to check the far-left checkbox and remove the check for “User must change password at next logon”:
2.) Use the free, excellent, and unsupported ADModify.NET tool:
3.) Create a VBScript that toggles the pwdLastSet attribute of the migrated user accounts from the default of ‘0’ to ‘-1’. There are a number of samples here:
4.) Scripting option with DSQUERY and DSMOD USER commands:
DSQuery user “ou=foo,dc=contoso,dc=com” –scope subtree -limit 0 | DSMod User –mustchpwd no
5.) And finally, AD PowerShell in Windows 2008 R2/Windows7 RSAT tools:
Get–aduser –filter {pwdlastset –eq 0} –searchbase “dc=contoso,dc=com” –searchscope subtree | set-aduser –changepasswordatlogon $false
Thanks,
-Jason (J4) Fournerat