Who Disabled A Smartcard For Logon?
Does your environment utilize Smartcard/CAC for logging in the network? Do they know who is disabling the smartcards and if they are doing it for other people? This monitor will alert on the security events and reports when someone disables smartcard(s) logon. It will report who did it, and whos account was it applied to. The monitor will auto close once the smartcard logon is re-enabled allowing you to track when and how often this is happening.
Requirements for making this happen:
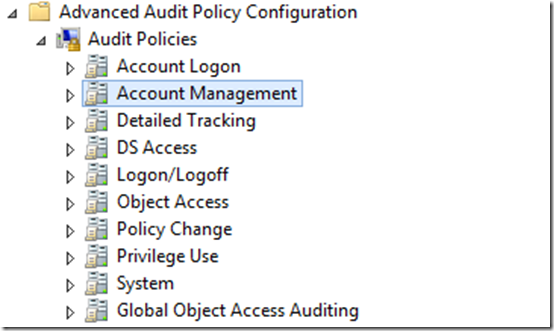
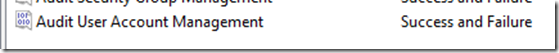
A GPO setting needs to be capturing success and failure. Advance Audit Policy Configuration > Account Management > Audit User Account Management
Make sure that “Success” and “Failure” are checked; both are needed for this type of monitoring.
Informational: User Account Management
This policy setting allows you to audit changes to user accounts. Events include the following:
A user account is created, changed, deleted; renamed, disabled, enabled, locked out, or unlocked.
A user account’s password is set or changed.
A security identifier (SID) is added to the SID History of a user account.
The Directory Services Restore Mode password is configured.
Permissions on administrative user accounts are changed.
Credential Manager credentials are backed up or restored.
If you configure this policy setting, an audit event is generated when an attempt to change a user account is made. Success audits record successful attempts and Failure audits record unsuccessful attempts. If you do not configure this policy setting, no audit event is generated when a user account changes.
Volume: Low.
Default: Success.
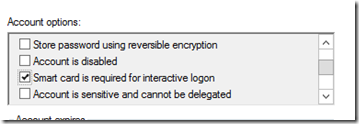
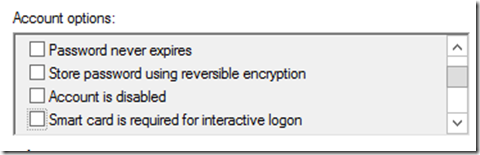
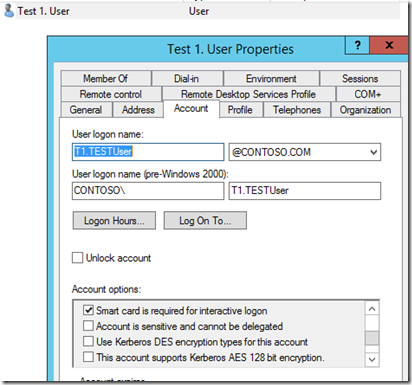
Next I have a test account with the “Smart card is required for interactive logon” checked in “Active Directory Computer and Users”.
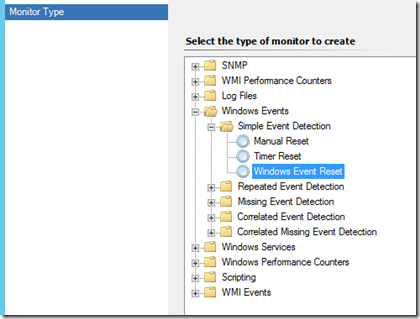
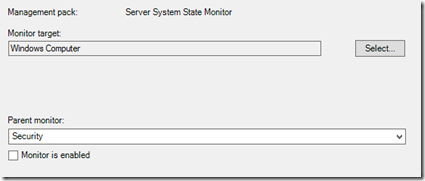
Building the monitor, a “Windows Event” > “Simple Event Detection” > “Windows Event Reset”
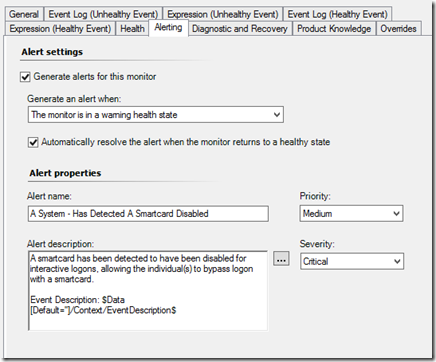
Target “Windows Computer”, ensured that the monitor is disabled. Name the alert what ever you like.
For me I like everything to be uniformed; I use: “A System – Has Detected A Smartcard Disabled”.
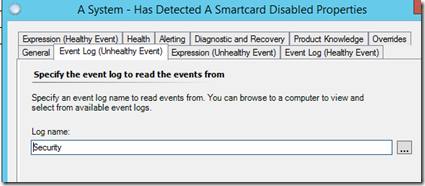
Targeting the “Security” Event Log for the “Unhealthy Event”
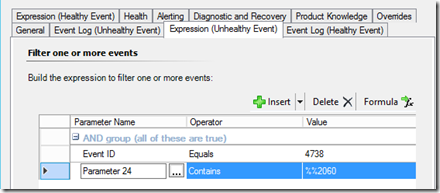
Alerting off an Event ID 4738 “A user account was changed” and the 24th Parameter of the alert description. “User Account Control: %%2060” = unchecked/disabled
More Information: How to use the UserAccountControl flags to manipulate user account properties: https://support.microsoft.com/en-us/kb/305144
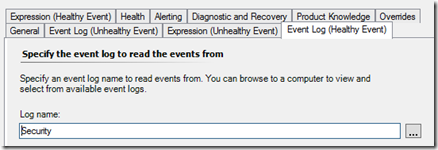
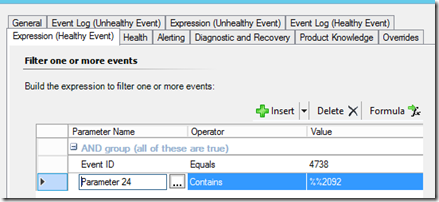
The “Healthy Event” will also be targeting the “Security” Event Log.
Alerting off an Event ID 4738 again “A user account was changed” and the 24th Parameter of the alert description. “User Account Control: %%2092” = checked/enabled
The Alerting, I’ve added some information about the alert in the “Alert description” and I am also pulling the who event description as well.
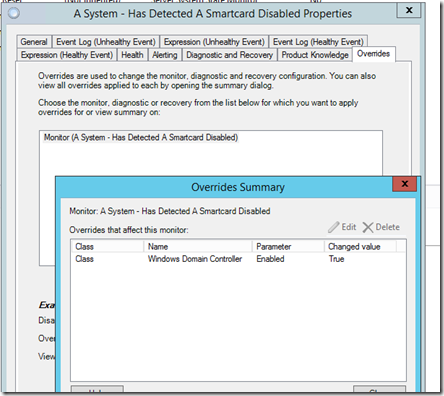
Next, turn it on to start capturing the events by overriding the monitor and target “Windows Domain Controller”.
Enable the monitor like this and apply it.
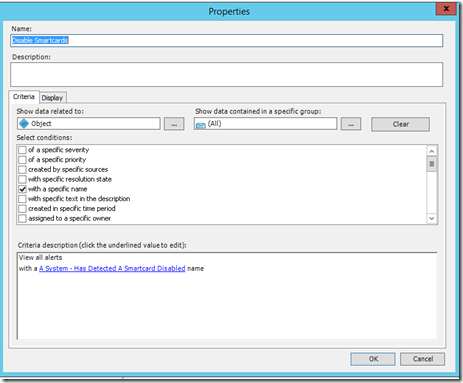
Optional: Next, an alert view might be in order. Here is a screenshot of how I configured the one I am using.
Now that the view has been created, hopefully enough time has gone by for all the domain controllers to have picked up this monitor. If not allow time before you test.
Let’s test it; open “Active Directory Users and Computers” find a test subject. Uncheck the “Smart card is required for interactive logon” and click apply.
Warning: Do not apply to your account if you are testing. When you uncheck the account, your password may need to be reset or you will not be able to log back on.
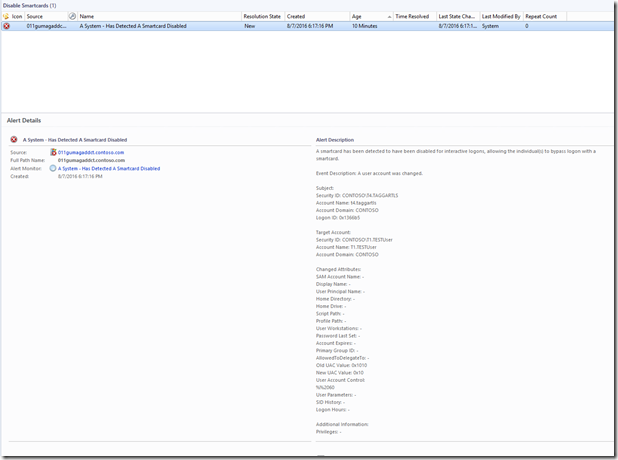
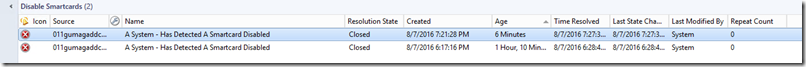
There should be a new alert in the view that was created or in the “Active Alert” view.
Informational: The “Alert Description” tells you who made the change and who’s account was it applied to. Depending on the customer, you could send notifications on this since it could be a security risk.
To close the event, re-check the “Smart card is required for interactive logon” and applied, you should see an alert now closed in the console.
Simple as that.
Comments
- Anonymous
September 04, 2016
Good one Lynne....