Describe Microsoft Defender for Office 365
Microsoft Defender for Office 365 is a seamless integration into your Office 365 subscription that provides protection against threats, like phishing and malware that arrive in email links (URLs), attachments, or collaboration tools like SharePoint, Teams, and Outlook. Defender for Office 365 provides real-time views of threats. It also provides investigation, hunting, and remediation capabilities to help security teams identify, prioritize, investigate, and respond to threats.
Microsoft Defender for Office 365, which is available in two plans Microsoft Defender for Office 365 Plan 1 and Plan 2, safeguards organizations against malicious threats by providing admins and security operations (sec ops) teams a wide range of capabilities.
These capabilities can be categorized into the following security emphases:
- Preventing and detecting threats
- Investigating threats
- Responding to threats
Prevent and detect
Some of the features of Microsoft Defender for Office 365 that help organizations prevent and detect email and collaboration based threats include:
- Policies for anti-malware, anti-spam, and anti-phishing
- Outbound spam filtering
- Connection filtering to help identify good or bad source email servers by IP addresses.
- Quarantine policies to define the user experience for quarantined messages
- Submit messages, URLs, and attachments to Microsoft for analysis.
- Safe attachments that provide an additional layer of protection against malware. After files are scanned by the common virus detection engine in Microsoft 365, Safe Attachments opens files in a virtual environment to see what happens (a process known as detonation).
- Email and collaboration alerts
- Attack simulation training, which allows admins to run realistic attack scenarios in your organization. These simulated attacks help identify and train vulnerable users before a real attack impacts your bottom line.
- Security information and event management (SIEM) integration for alerts.
Investigate
Some of the features of Microsoft Defender for Office 365 that help organizations detect email and collaboration based threats include:
- Audit log search by users with appropriate permissions such as admins, insider risk teams, compliance and legal investigators, to provide visibility into the activities of the organization.
- Message trace capabilities. Message trace follows email messages as they travel through your Microsoft 365 organization. You can determine if a message was received, rejected, deferred, or delivered by the service. It also shows what actions were taken on the message before it reached its final status.
- Reports to help you see how email security features are protecting your organization.
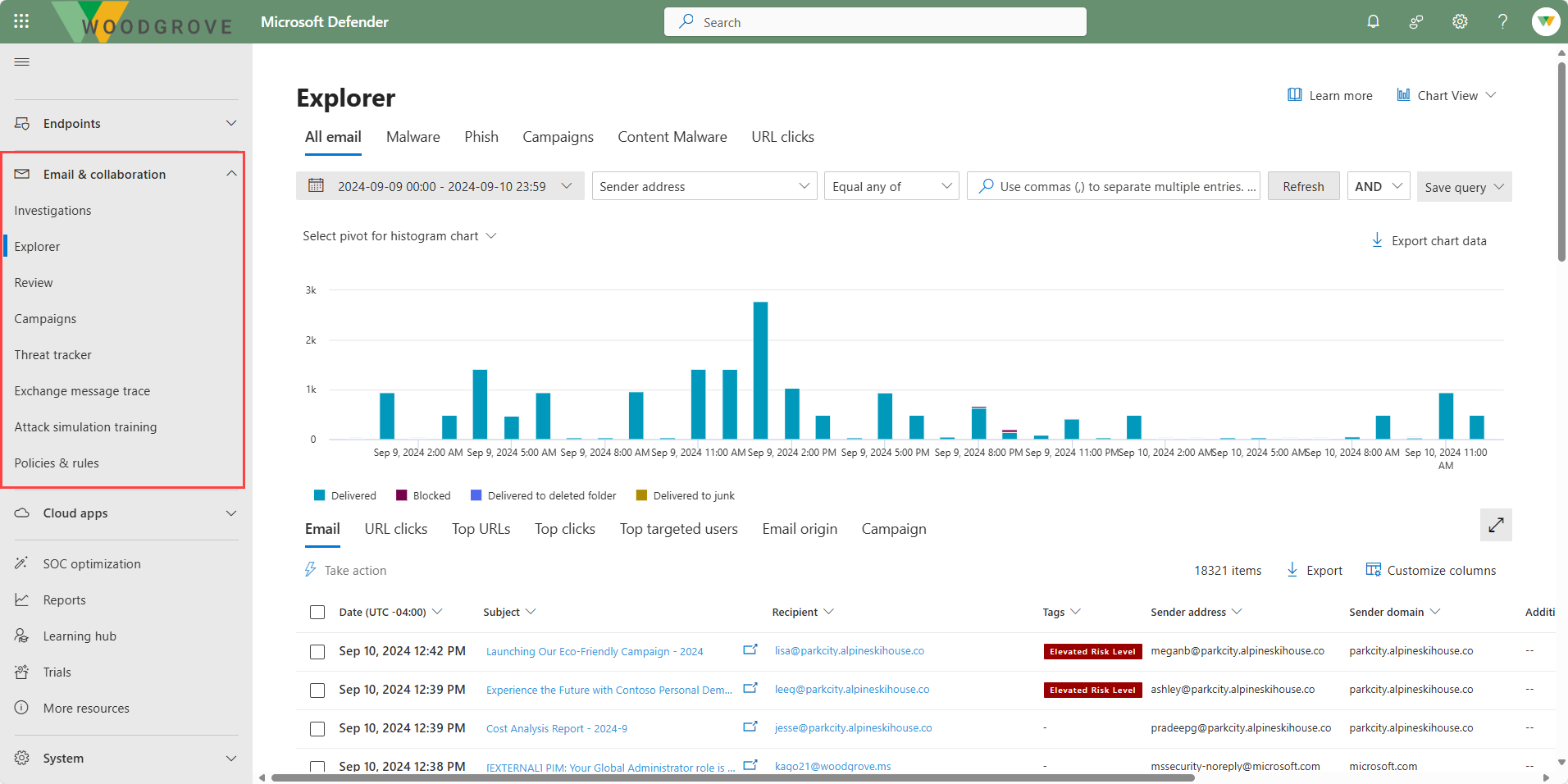
- Explorer (also known as Threat Explorer) or Real-time detections that are near real-time tools to help Security Operations (SecOps) teams investigate and respond to threats. Explorer allows admins to see malware detected by Microsoft 365 security features, start an automated investigation and response process, Investigate malicious email, and more.
- Security information and event management (SIEM) integration for detections.
- URL trace that allows admins to investigate a domain to see if the devices and servers in your enterprise network have been communicating with a known malicious domain.
- Threat trackers that are queries that you create and save to automatically or manually discover cybersecurity threats in your organization.
- The campaigns feature that identifies and categorizes coordinated phishing and malware email attacks. The campaigns feature lets you see the overall picture of an email attack faster and more completely than any human.
Respond
Some of the features of Microsoft Defender for Office 365 that help organizations detect email and collaboration based threats include:
- Zero-hour auto purge (ZAP) that retroactively detects and neutralizes malicious phishing, spam, or malware messages that have already been delivered to Exchange Online mailboxes.
- Automated investigation and response (AIR) capabilities that include automated investigation processes in response to well-known threats that exist today.
- Security information and event management (SIEM) integration for automated responses.
For a complete listing of the features in each plan, see the Microsoft Defender for Office 365 security product overview document that is linked in summary and resources unit of this module.
Microsoft Defender for Office 365 in the Microsoft Defender portal
Microsoft Defender for Office 365 is experienced through the Microsoft Defender portal. The Defender portal is the home for monitoring and managing security across your Microsoft identities, data, devices, apps, and infrastructure, allowing security admins to perform their security tasks, in one location.
Microsoft Defender for Office 365 functionality can be found under the Email & collaboration node on the left navigation panel of the Microsoft Defender portal.
- Investigations - View, manage, and remediate threats using automated investigation and response.
- Explorer - Investigate, hunt for, and remediate threats in emails and documents.
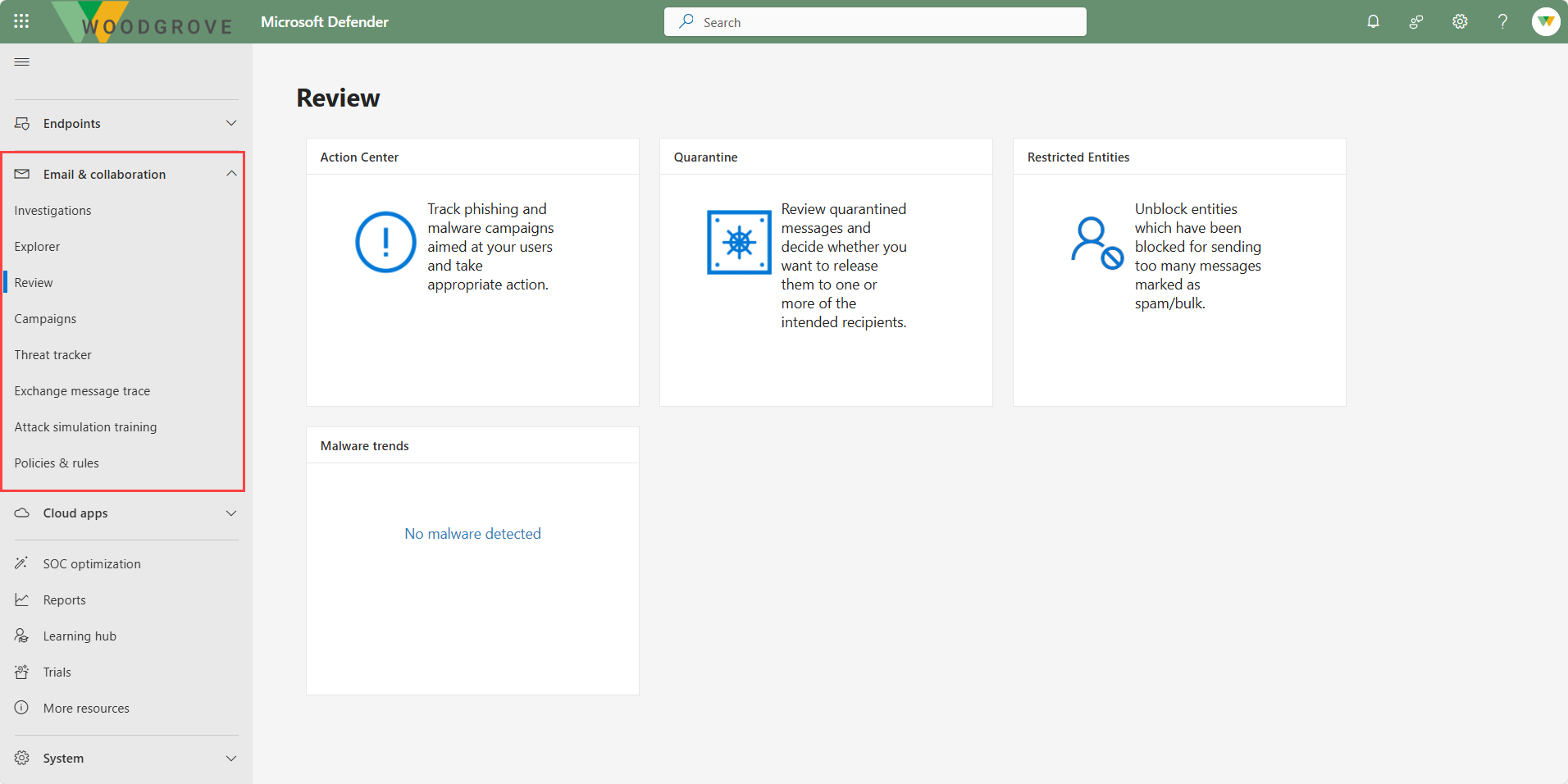
- Review - Manage quarantined items and restricted senders.
- Campaigns - Analyze coordinated attacks against your environment.
- Threat tracker - Monitor threat trends using widgets and custom searches.
- Exchange message trace - Analyze message flow in the Exchange admin center.
- Attack simulation training - Access and build user resilience using simulated attacks and training.
- Policies & rules - Configure security policies for email and other Microsoft 365 workspaces.
Settings, permissions, incidents and alerts, reports and other features are also available through the Microsoft Defender portal. More information is covered in the unit, "Describe the Microsoft Defender portal," included in this module.