Conditional access policy for SharePoint sites and OneDrive
 Some features in this article require Microsoft SharePoint Premium - SharePoint Advanced Management
Some features in this article require Microsoft SharePoint Premium - SharePoint Advanced Management
With Microsoft Entra authentication context, you can enforce more stringent access conditions when users access SharePoint sites.
You can use authentication contexts to connect an Microsoft Entra Conditional Access policy to a SharePoint site. Policies can be applied directly to the site or via a sensitivity label.
This capability can't be applied to the root site in SharePoint (for example, https://contoso.sharepoint.com).
Requirements
Using authentication context with SharePoint sites requires one of the following licenses:
- Microsoft SharePoint Premium - SharePoint Advanced Management
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5 Compliance
- Microsoft 365 E5 Information Protection and Governance
- Office 365 E5/A5/G5
Limitations
Some apps don't work with authentication contexts. We recommend testing apps on a site with authentication context enabled before broadly deploying this feature.
The following apps and scenarios don't work with authentication contexts:
- Older version of Office apps (see the list of supported versions)
- Viva Engage
- OneNote app can't be added to channel if the associated SharePoint site has an authentication context.
- Teams channel meeting recording upload fails on sites with an authentication context.
- SharePoint folder renaming in Teams fails if the site has an authentication context.
- Teams webinar scheduling fails if OneDrive has an authentication context.
- The OneDrive sync app won't sync sites with an authentication context.
- Associating an authentication context to the enterprise application catalog site collection isn't supported.
- The “Visualize SharePoint List in Power BI” feature doesn't currently support authentication context.
- Outlook on Windows, Mac, Android, and iOS don't support communication with SharePoint sites protected by an Authentication Context.
- The multiple-file download feature currently doesn't function when both the authentication context and 'Use Conditional Access App Control' in session control are enabled in the conditional access policy.
- The file copy and move feature between different regions (cross-geo) currently doesn’t function when an authentication context is applied to the destination site.
- Exporting to Excel as an Excel Web Query (IQY) doesn't currently support authentication context.
Setting up an authentication context
Setting up an authentication context for labeled sites requires these basic steps:
Add an authentication context in Microsoft Entra ID.
Create a conditional access policy that applies to that authentication context and has the conditions and access controls that you want to use.
Do one of the following:
- Set a sensitivity label to apply the authentication context to labeled sites.
- Apply the authentication context directly to a site
In this article, we look at the example of requiring guests to agree to a terms of use before gaining access to a sensitive SharePoint site. You can also use any of the other conditional access conditions and access controls that you might need for your organization.
Add an authentication context
First, add an authentication context in Microsoft Entra ID.
To add an authentication context:
In Microsoft Entra Conditional Access, under Manage, select Authentication context.
Select New authentication context.
Type a name and description and select the Publish to apps check box.
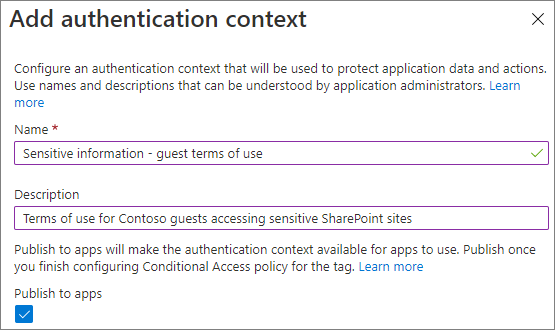
Select Save.
Create a conditional access policy
Next, create a conditional access policy that applies to that authentication context and that requires guests to agree to terms of use as a condition of access.
To create a conditional access policy:
In Microsoft Entra Conditional Access, select New policy.
Type a name for the policy.
On the Users and groups tab, choose the Select users and groups option, and then select the Guest or external users check box.
Choose B2B collaboration guest users from the dropdown.
On the Cloud apps or actions tab, under Select what this policy applies to, choose Authentication context, and select the check box for the authentication context that you created.
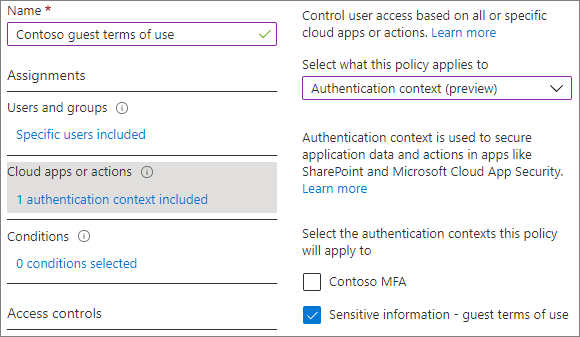
On the Grant tab, select the check box for the terms of use that you want to use, and then select Select.
Choose if you want to enable the policy, and then select Create.
Apply the authentication context directly to a site
You can directly apply an authentication context to a SharePoint site by using the Set-SPOSite PowerShell cmdlet.
Note
This capability requires a Microsoft 365 E5 or Microsoft SharePoint Premium - SharePoint Advanced Management license.
In the following example, we apply the authentication context we created above to a site called "research."
Set-SPOSite -Identity https://contoso.sharepoint.com/sites/research -ConditionalAccessPolicy AuthenticationContext -AuthenticationContextName "Sensitive information - guest terms of use"
Set a sensitivity label to apply the authentication context to labeled sites
If you want to use a sensitivity label to apply the authentication context, update a sensitivity label (or create a new one) to use the authentication context.
Note
Sensitivity labels require Microsoft 365 E5 or Microsoft 365 E3 plus the Advanced Compliance license.
To update a sensitivity label
In the Microsoft Purview compliance portal, on the Information protection tab, select the label that you want to update and then select Edit label.
Select Next until you are on the Define protection settings for groups and sites page.
Ensure that the External sharing and Conditional Access settings check box is selected, and then select Next.
On the Define external sharing and device access settings page, select the Use Microsoft Entra Conditional Access to protect labeled SharePoint sites check box.
Select the Choose an existing authentication context option.
In the dropdown list, choose the authentication context that you want to use.
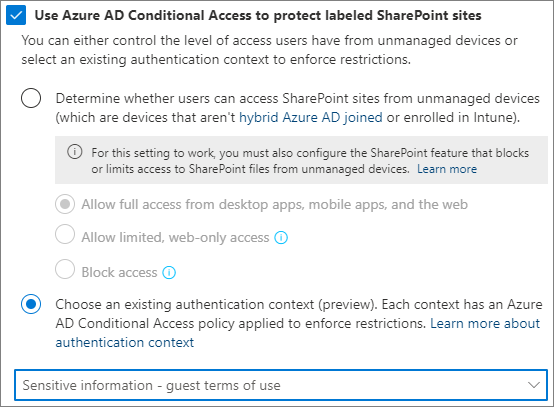
Select Next until you are on the Review your settings and finish page, and then select Save label.
Once the label has been updated, guests accessing a SharePoint site (or the Files tab in a team) with that label will be required to agree to the terms of use before gaining access to that site.
Blocking background apps
If authentication context is set on a site, admins can choose to prevent background apps from accessing that site for the apps assigned with that authentication context in a conditional access policy. You can configure a conditional access policy such that a specific authentication context can be assigned to chosen application principles (non-Microsoft applications). You need to explicitly turn on this feature via the following cmdlet. You should have at least one conditional access policy with an application principle configured.
Set-SPOTenant -BlockAppAccessWithAuthenticationContext $false/$true (default false)
Third party app integration
Third party apps using sites with authentication context attached will need to be able to handle claims challenge. If you have third party apps then we recommend test the apps and you read guidance here.
See also
Conditional Access: Cloud apps, actions, and authentication context