Integrate with Zero Trust solutions
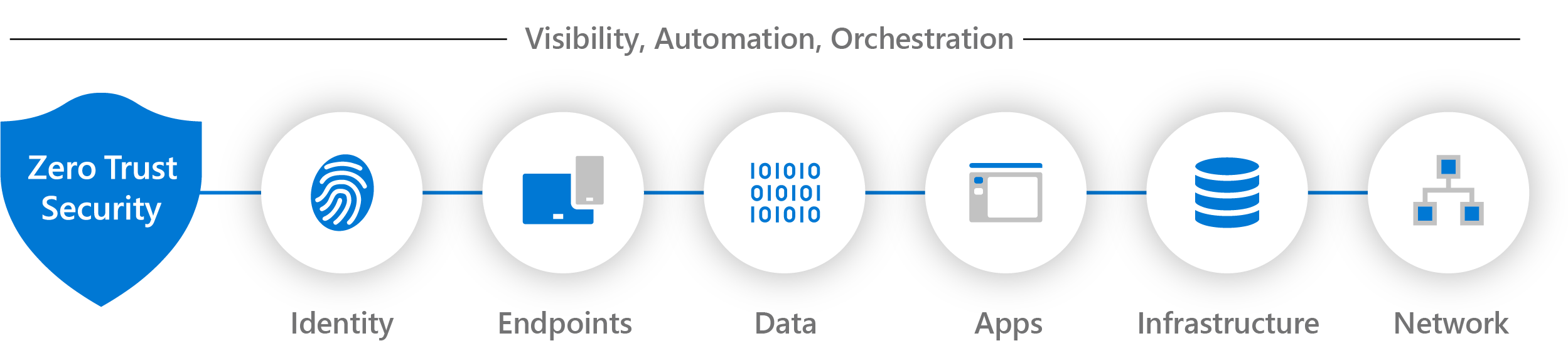
Zero Trust is an approach to security that adapts to the complexity of the modern environment, embraces the mobile workforce, and protects people, devices, applications, and data wherever they are located.
The journey to implementing Zero Trust will be distinct for every organization depending on their needs and existing infrastructure. For this reason, we support technology partner integrations that help meet our customers' unique needs.
The integration guidance in this section is organized by Zero Trust technology areas. This guidance is for software providers and technology partners who want to enhance their security solutions and reach new customers by integrating with Microsoft products.
Additional Zero Trust documentation
Use additional Zero Trust content based on a documentation set or the roles in your organization.
Documentation set
Follow this table for the best Zero Trust documentation sets for your needs.
| Documentation set | Helps you... | Roles |
|---|---|---|
| Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. | Security architects, IT teams, and project managers |
| Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. | IT teams and security staff |
| Zero Trust for small businesses | Apply Zero Trust principles to small business customers. | Customers and partners working with Microsoft 365 for business |
| Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. | Security architects and IT implementers |
| Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance | Apply Zero Trust protections to your Microsoft 365 tenant. | IT teams and security staff |
| Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. | IT teams and security staff |
| Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. | IT teams and security staff |
| Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. | Application developers |
Your role
Follow this table for the best documentation sets for your role in your organization.
| Role | Documentation set | Helps you... |
|---|---|---|
| Security architect IT project manager IT implementer |
Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. |
| Member of an IT or security team | Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. |
| Customer or partner for Microsoft 365 for business | Zero Trust for small businesses | Apply Zero Trust principles to small business customers. |
| Security architect IT implementer |
Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. |
| Member of an IT or security team for Microsoft 365 | Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance for Microsoft 365 | Apply Zero Trust protections to your Microsoft 365 tenant. |
| Member of an IT or security team for Microsoft Copilots | Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. |
| Member of an IT or security team for Azure services | Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. |
| Application developer | Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. |