Securing identity with Zero Trust
![]()
Before most organizations start a Zero Trust journey, their approach to identity might be fragmented with various identity providers, a lack of single sign-on (SSO) between cloud and on-premises apps, and limited visibility into identity risk.
Cloud applications and mobile workers require a new way of thinking when it comes to security. Many employees bring their own devices and work in a hybrid manner. Data is regularly accessed outside the traditional corporate network perimeter and shared with external collaborators like partners and vendors. Traditional corporate applications and data are moving from on-premises to hybrid and cloud environments.
Traditional network controls for security aren't enough anymore.
Identities represent the people, services, or devices, across networks, endpoints, and applications. In the Zero Trust security model, they function as a powerful, flexible, and granular means to control access to resources.
Before an identity attempts to access a resource, organizations must:
- Verify the identity with strong authentication.
- Ensure access is compliant and typical for that identity.
- Follow least privilege access principles.
Once the identity is verified, we can control access to resources based on organization policies, ongoing risk analysis, and other tools.
Identity Zero Trust deployment objectives
When implementing an end-to-end Zero Trust framework for identity, we recommend you focus first on these initial deployment objectives:
- Cloud identity federates with on-premises identity systems.
- Conditional Access policies gate access and provide remediation activities.
- Analytics improve visibility.
After the previous areas are addressed, focus on these deployment objectives:
- Identities and access privileges are managed with identity governance.
- User, device, location, and behavior is analyzed in real time.
- Integrate threat signals from other security solutions.
I. Cloud identity federates with on-premises identity systems
Microsoft Entra ID enables strong authentication, a point of integration for endpoint security, and the core of your user-centric policies to guarantee least-privileged access. Microsoft Entra Conditional Access is the policy engine used to make decisions for access to resources based on user identity, environment, device health, and risk verified explicitly at the time of access. You can implement a Zero Trust identity strategy with Microsoft Entra ID.

Connect all of your users to Microsoft Entra ID and federate with on-premises identity systems
Maintaining a healthy pipeline of your employees' identities and the necessary security artifacts including groups for authorization and endpoints for access policy controls puts you in the best place to use consistent identities and controls in the cloud.
Follow these steps:
- Choose an authentication option. Microsoft Entra ID provides you the best brute force, DDoS, and password spray protection, but make the decision that's right for your organization and your compliance needs.
- Only bring the identities you absolutely need. Use going to the cloud as an opportunity to leave behind service accounts that only make sense on-premises. Leave on-premises privileged roles on-premises.
- Ensure you meet the hardware requirements for Microsoft Entra Connect Sync based on your organization's size.
Establish your Identity Foundation with Microsoft Entra ID
A Zero Trust strategy requires verifying explicitly, using least-privileged access principles, and assuming breach. Microsoft Entra ID can act as the policy decision point to enforce your access policies based on insights on the user, endpoint, target resource, and environment.
Put Microsoft Entra ID in the path of every access request. This process connects every user, app, and resource through a common identity control plane and provides Microsoft Entra ID with the signals to make the best possible decisions about the authentication/authorization risk. In addition, single sign-on (SSO) and consistent policy guardrails provide a better user experience and contribute to productivity gains.
Integrate all your applications with Microsoft Entra ID
Single sign-on prevents users from leaving copies of their credentials in various apps and helps avoid phishing attacks or MFA fatigue due to excessive prompting.
Make sure you don't have multiple identity and access management (IAM) solutions in your environment. This duplication diminishes signals that Microsoft Entra ID sees, allows bad actors to live in the shadows between the two IAM engines, and leads to poor user experience. This complexity might lead to your business partners becoming doubters of your Zero Trust strategy.
Follow these steps:
- Integrate modern enterprise applications that speak OAuth2.0 or SAML.
- For Kerberos and form-based auth applications, integrate them using the Microsoft Entra application proxy.
- If you publish your legacy applications using application delivery networks/controllers, use Microsoft Entra ID to integrate with most of the major ones (such as Citrix, Akamai, and F5).
- To help discover and migrate your apps off of ADFS and existing/older IAM engines, review Resources for migrating applications to Microsoft Entra ID.
- Automate user provisioning.
Verify explicitly with strong authentication
Follow these steps:
- Roll out Microsoft Entra multifactor authentication. This effort is a foundational piece of reducing user session risk. As users appear on new devices and from new locations, being able to respond to an MFA challenge is one of the most direct ways that your users can teach us that these are familiar devices/locations as they move around the world (without having administrators parse individual signals).
- Block legacy authentication. One of the most common attack vectors for malicious actors is to use stolen/replayed credentials against legacy protocols, such as SMTP, that can't do modern security challenges.
II. Conditional Access policies gate access and provide remediation activities
Microsoft Entra Conditional Access analyzes signals such as user, device, and location to automate decisions and enforce organizational access policies for resource. You can use Conditional Access policies to apply access controls like multifactor authentication (MFA). Conditional Access policies allow you to prompt users for MFA when needed for security and stay out of users' way when not needed.
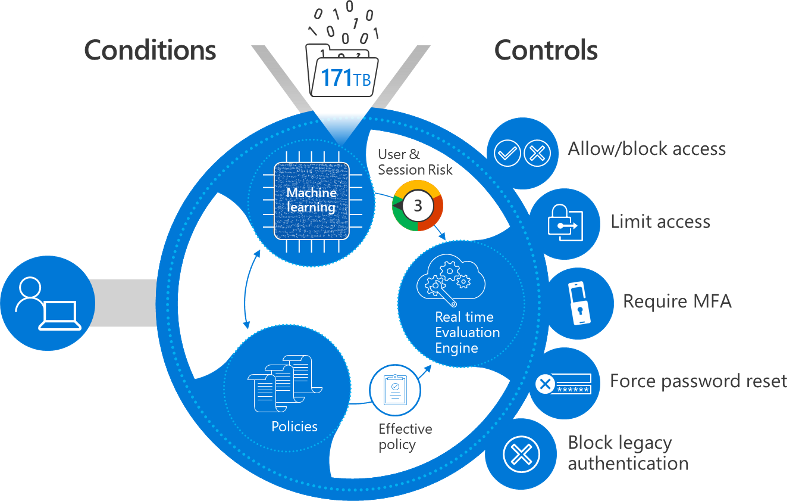
Microsoft provides standard conditional policies called security defaults that ensure a basic level of security. However, your organization might need more flexibility than security defaults offer. You can use Conditional Access to customize security defaults with more granularity and to configure new policies that meet your requirements.
Planning your Conditional Access policies in advance and having a set of active and fallback policies is a foundational pillar of your Access Policy enforcement in a Zero Trust deployment. Take the time to configure known network locations in your environment. Even if you don't use these network locations in a Conditional Access policy, configuring these IPs informs the risk of Microsoft Entra ID Protection.
Take this step:
- Check out our deployment guidance and best practices for resilient Conditional Access policies.
Register devices with Microsoft Entra ID to restrict access from vulnerable and compromised devices
Follow these steps:
- Enable Microsoft Entra hybrid join or Microsoft Entra join. If you're managing the user's laptop/computer, bring that information into Microsoft Entra ID and use it to help make better decisions. For example, allowing rich clients, that have offline copies on the computer, access to data if you know the user is coming from a machine that your organization controls and manages.
- Enable the Intune service within Microsoft Endpoint Manager (EMS) for managing your users' mobile devices and enroll devices. The same can be said about user mobile devices as about laptops: The more you know about them (patch level, jailbroken, rooted, etc.), the more you can provide a rationale for why you block/allow access.
III. Analytics improve visibility
As you build your estate in Microsoft Entra ID with authentication, authorization, and provisioning, it's important to have strong operational insights into what is happening in the directory.
Configure logging and reporting to improve visibility
Take this step:
- Plan a Microsoft Entra reporting and monitoring deployment to be able to persist and analyze logs from Microsoft Entra ID, either in Azure or using a SIEM system of choice.
IV. Identities and access privileges are managed with identity governance
Once you accomplish your initial objectives, focus on other objectives such as more robust identity governance.
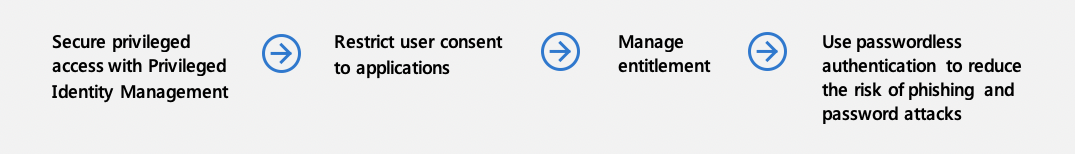
Secure privileged access with Privileged Identity Management
Control the endpoints, conditions, and credentials that users use to access privileged operations/roles.
Follow these steps:
- Take control of your privileged identities. Privileged access isn't only administrative access, but also application or developer access that can change the way your mission-critical apps run and handle data.
- Use Privileged Identity Management to secure privileged identities.
Restrict user consent to applications
User consent to applications is a common way for modern applications to get access to organizational resources, but there are some best practices to keep in mind.
Follow these steps:
- Restrict user consent and manage consent requests to ensure that no unnecessary exposure occurs of your organization's data to apps.
- Review prior/existing consent in your organization for any excessive or malicious consent.
For more on tools to protect against tactics to access sensitive information, see "Strengthen protection against cyber threats and rogue apps" in our guide to implementing an identity Zero Trust strategy.
Manage entitlement
With applications centrally authenticating and driven from Microsoft Entra ID, you can streamline your access request, approval, and recertification process to make sure that the right people have the right access and that you have a trail of why users in your organization have the access they have.
Follow these steps:
- Use Entitlement Management to create access packages that users can request as they join different teams/projects and that assigns them access to the associated resources (such as applications, SharePoint sites, group memberships).
- If deploying Entitlement Management isn't possible for your organization at this time, at least enable self-service paradigms in your organization by deploying self-service group management and self-service application access.
Use passwordless authentication to reduce the risk of phishing and password attacks
With Microsoft Entra ID supporting FIDO 2.0 and passwordless phone sign-in, you can move the needle on the credentials that your users (especially sensitive/privileged users) are employing day-to-day. These credentials are strong authentication factors that can mitigate risk as well.
Take this step:
- Start rolling out passwordless credentials in your organization.
V. User, device, location, and behavior are analyzed in real time to determine risk and deliver ongoing protection
Real-time analysis is critical for determining risk and protection.
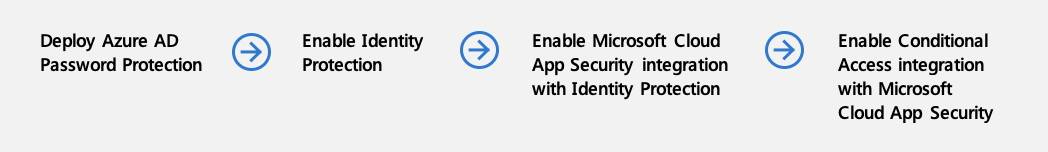
Deploy Microsoft Entra Password Protection
While enabling other methods to verify users explicitly, don't ignore weak passwords, password spray, and breach replay attacks. And classic complex password policies don't prevent the most prevalent password attacks.
Take this step:
- Enable Microsoft Entra Password Protection for your users in the cloud and on-premises.
Enable Microsoft Entra ID Protection
Get more granular session/user risk signal with Microsoft Entra ID Protection. You can enable risk investigation and remediation options based on your organization's evolving security needs.
Take this step:
Enable Microsoft Defender for Cloud Apps integration with Microsoft Entra ID Protection
Microsoft Defender for Cloud Apps monitors user behavior inside SaaS and modern applications. This signal informs Microsoft Entra ID about what happened to the user after they authenticated and received a token. If the user pattern starts to look suspicious, then a signal can feed to Microsoft Entra ID Protection and Conditional Access notifying it that the user seems to be compromised or high risk. On the next access request from this user, Microsoft Entra ID can correctly take action to verify the user or block them.
Take this step:
- Enable Defender for Cloud Apps monitoring to enrich the Microsoft Entra ID Protection signal.
Enable Conditional Access integration with Microsoft Defender for Cloud Apps
Using signals emitted after authentication and with Defender for Cloud Apps proxying requests to applications, you'll be able to monitor sessions going to SaaS applications and enforce restrictions.
Follow these steps:
Enable restricted session for use in access decisions
When a user's risk is low, but they're signing in from an unknown endpoint, you might want to allow access to resources, but not allow them to do things that expose your organization to risky actions. You can configure Exchange Online and SharePoint Online to offer the user a restricted session that allows them to read emails or view files, but not download them and save them on an untrusted device.
Take this step:
- Enable limited access to SharePoint Online and Exchange Online.
VI. Integrate threat signals from other security solutions to improve detection, protection, and response
Finally, other security solutions can be integrated for greater effectiveness.
Integrate Microsoft Defender for Identity with Microsoft Defender for Cloud Apps
Integration with Microsoft Defender for Identity enables Microsoft Entra ID to know that a user is indulging in risky behavior while accessing on-premises, nonmodern resources (like file shares). This signal can be factored into overall risk, possibly blocking further access in the cloud.
Follow these steps:
- Enable Microsoft Defender for Identity with Microsoft Defender for Cloud Apps to bring on-premises signals into the risk signal we know about the user.
- Check the combined Investigation Priority score for each user at risk to give a holistic view of which ones your SOC should focus on.
Enable Microsoft Defender for Endpoint
Microsoft Defender for Endpoint allows you to attest to the health of Windows machines and determine whether they're undergoing a compromise. You can then feed that information into mitigating risk at runtime. Whereas Domain Join gives you a sense of control, Defender for Endpoint allows you to react to a malware attack at near real time by detecting patterns where multiple user devices are hitting untrustworthy sites, and to react by raising their device/user risk at runtime.
Take this step:
Securing Identity in accordance with Executive Order 14028 on Cybersecurity & OMB Memorandum 22-09
The Executive Order 14028 on Improving the Nations Cyber Security & OMB Memorandum 22-09 includes specific actions on Zero Trust. Identity actions include employing centralized identity management systems, use of strong phishing-resistant MFA, and incorporating at least one device-level signal in authorization decisions. For detailed guidance on implementing these actions with Microsoft Entra ID, see Meet identity requirements of memorandum 22-09 with Microsoft Entra ID.
Products covered in this guide
- Microsoft Entra ID
- Microsoft Defender for Identity
- Microsoft Endpoint Manager (includes Microsoft Intune)
- Microsoft Defender for Endpoint
- SharePoint Online
- Exchange Online
Conclusion
Identity is central to a successful Zero Trust strategy. For further information or help with implementation, contact your Customer Success team or continue to read through the other chapters of this guide, which span all Zero Trust pillars.
The Zero Trust deployment guide series