Set up a lab to teach ethical hacking class by using Azure Lab Services
Important
Azure Lab Services will be retired on June 28, 2027. For more information, see the retirement guide.
This article shows you how to set up a class that focuses on the forensics side of ethical hacking with Azure Lab Services. In an ethical hacking class, students can learn modern techniques for defending against vulnerabilities. Penetration testing, a practice that the ethical hacking community uses, occurs when someone attempts to gain access to the system or network to demonstrate vulnerabilities that a malicious attacker might exploit.
Each student gets a Windows host virtual machine (VM) that has two nested virtual machines: one VM with Metasploitable3 image and another VM with the Kali Linux image. Use the Metasploitable VM to try exploitation tasks. The Kali VM provides access to the tools you need to run forensic tasks.
Prerequisites
- To set up this lab, you need access to an Azure subscription. Discuss with your organization's administrator to see if you can get access to an existing Azure subscription. If you don't have an Azure subscription, create a free account before you begin.
- After you have an Azure subscription, you can create a lab plan in Azure Lab Services. For more information about creating a new lab plan, see Quickstart: Set up resources to create labs. You can also use an existing lab plan.
Configure your lab
For instructions on how to create a lab, see Tutorial: Set up a lab. Use the following settings when creating the lab.
| Lab settings | Value |
|---|---|
| Virtual machine (VM) size | Medium (Nested Virtualization) |
| VM image | Windows 11 |
Note
This article references features available in lab plans, which replaced lab accounts.
Configure your template
After you create a lab, create a template VM that is based on the virtual machine size and image you choose. Configure the template VM with everything you want to provide to your students for this class. For more information, see Create and manage a template in Azure Lab Services.
To configure the template VM, complete the following tasks:
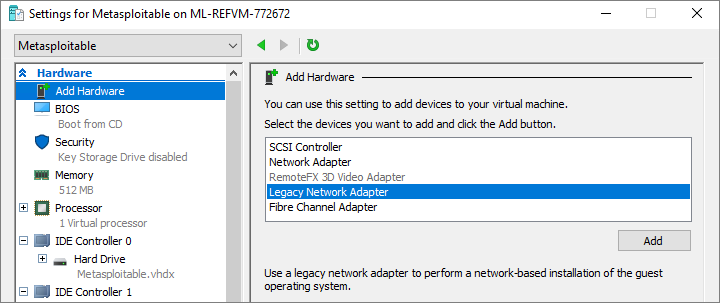
- Set up the machine for nested virtualization. Enable all the appropriate windows features, like Hyper-V.
- Set up the Kali Linux image. Kali is a Linux distribution that includes tools for penetration testing and security auditing.
- Set up the Metasploitable image. For this example, use the Metasploitable3 image. This image is created to purposely have security vulnerabilities.
Important
Azure Lab Services will be retired on June 28, 2027. For more information, see the retirement guide.
Prepare template machine for nested virtualization
Launch PowerShell in Administrator mode. Run these commands.
Invoke-WebRequest 'https://aka.ms/azlabs/scripts/hyperV-powershell' -Outfile SetupForNestedVirtualization.ps1 .\SetupForNestedVirtualization.ps1
Note
The script might require the machine to restart. Follow instructions from the script and re-run the script until you see Script completed in the output.
Set up nested virtual machine images
Kali is a Linux distribution that includes tools for penetration testing and security auditing.
The Rapid7 Metasploitable image is an image purposely configured with security vulnerabilities. Use this image to test and find issues. The following instructions show you how to set up a particular Metasploitable image. If you need a newer version of the Metasploitable, see https://github.com/rapid7/metasploitable3.
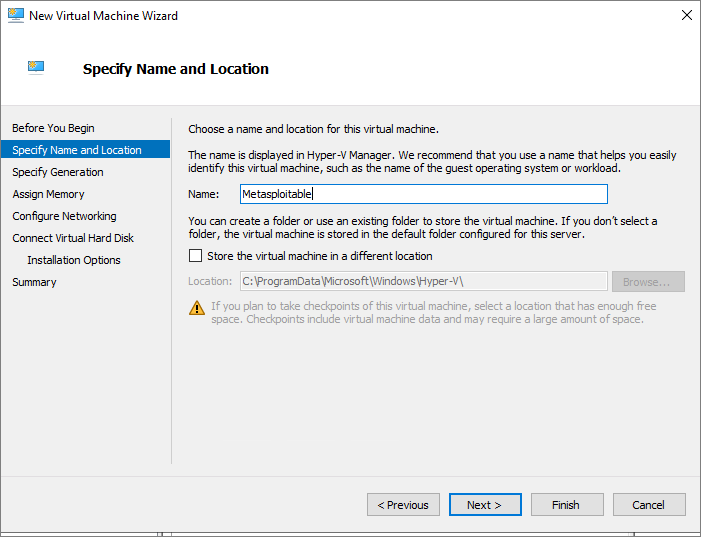
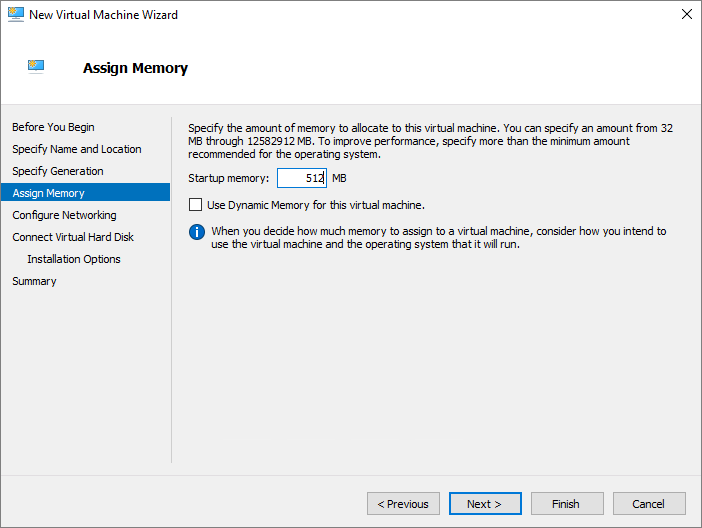
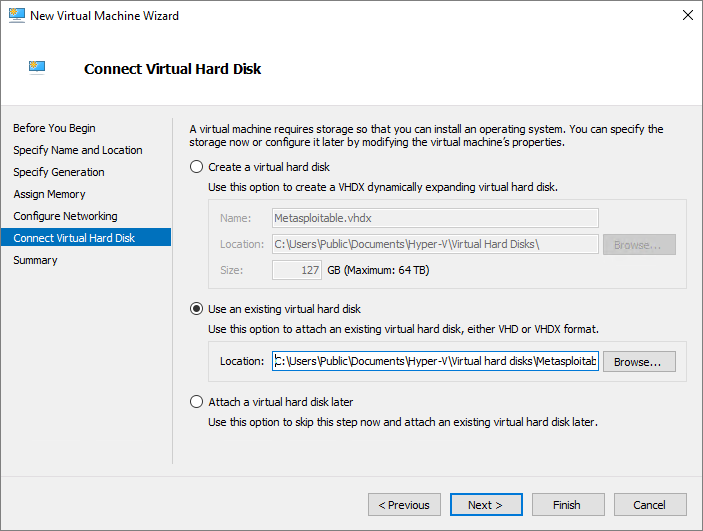
To install Kali Linux and Metasploitable on the template VM, run the following command:
Invoke-WebRequest ' https://aka.ms/azlabs/scripts/EthicalHacking-powershell' -Outfile Setup-EthicalHacking.ps1 .\Setup-EthicalHacking.ps1 -SwitchName 'Default Switch'
The template is now updated and has the nested VM images needed for an ethical hacking penetration testing class: an image with tools to do the penetration testing, and another image with security vulnerabilities to discover. You can now publish the template VM to the class.
Related content
In this article, you went through the steps to create a lab for ethical hacking class. The lab VM contains two nested virtual machines to practice penetrating testing.
The template image can now be published to the lab. For more information, see Publish the template VM.
As you set up your lab, see the following articles: