Microsoft Identity Manager 2016 reporting with Azure Monitor
Azure Monitor is a monitoring solution for collecting, analyzing, and responding to monitoring data from your cloud and on-premises environments. MIM Synchronization Service writes to the event log for key events, and the MIM Service can be configured to add records to a Windows event log for requests it receives. These event logs are transported by Azure Arc to Azure Monitor, and can be retained in an Azure Monitor workspace alongside the Microsoft Entra audit log, and logs from other data sources. You can then use Azure Monitor workbooks to format the MIM events in a report, and alerts to monitor for specific events in MIM Service. This approach replaces the earlier MIM hybrid reporting.
Setting up Azure Monitor with your MIM server consists of the following steps:
- Join MIM servers to Azure with Azure Arc
- Install the Azure Monitor extensions
- Create a workspace
- Create a Data Collection Rule (DCR)
- Verify the MIM data
The following sections describe each of the individual steps.
Prerequisites
You should make sure that you meet the Azure Arc and Azure Monitor prerequisites before attempting the steps outlined below.
Also, a resource group in Azure is required before joining the server with Azure Arc. If you do not have a resource group, you can create one before generating the Azure Arc installation script.
Join MIM server to Azure with Azure Arc
You'll likely have one or more Windows Server machines that run MIM Sync or MIM Service in your environment, potentially located on-premises. To join any non-Azure hosted Windows Server to Azure, you generate a script and run it locally on each of those servers. This provides a consistent management experience across native Azure virtual machines and servers anywhere. When a non-Azure machine is Arc-enabled, it becomes a connected machine and is treated as a resource in Azure, with its own resource Id and projection in Azure.
To join your MIM server, you generate a script and run it locally on the MIM server. Follow the prompts in the portal to create the script. Download the script and run it on the MIM server. After the script completes, the MIM server should appear under Azure Arc in the portal.
For more information, see Connect Windows Server machines to Azure through Azure Arc Setup.
Install the Azure Monitor extensions
After you've joined the Windows Server machines, which have MIM Sync or MIM Service installed, to Azure, you can use the Azure Monitor agent on those servers to begin collecting Windows Event logs. Azure Arc-enabled servers support the Azure VM extension framework, which provides post-deployment configuration and automation tasks, enabling you to simplify management of your hybrid machines like you can with Azure VMs.
After you have MIM joined to Azure, you can the Azure Monitor agent on the MIM server to beginning collecting Windows Event data. To install the Azure Monitor extensions you can use the following PowerShell script. Be sure to replace the variables with your information.
## Install the Azure Monitor Agent
Install-Module -Name Az.ConnectedMachine
$subscriptionID = "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
$tenantID = "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
$resourcegroup = "MIM-resource-group"
$MIMServer = "MIM"
$location = eastus
Connect-AzAccount -Tenant $tenantID -SubscriptionId $subscriptionID
New-AzConnectedMachineExtension -Name AzureMonitorWindowsAgent -ExtensionType AzureMonitorWindowsAgent -Publisher Microsoft.Azure.Monitor -ResourceGroupName $resourcegroup -MachineName $MIMServer -Location $location -EnableAutomaticUpgrade
For more information, see Deployment options for Azure Monitor agent on Azure Arc-enabled servers
Create a workspace
A Log Analytics workspace is a data store into which you can collect any type of log data from all of your Azure and non-Azure resources and applications.
Before we create a data collection rule that collects the Windows Event log information, we need somewhere to send this information. Follow the steps outline in Create a workspace to create a Log Analytics workspace.
Create a Data Collection Rule
Data collection rules (DCRs) are part of an Extract, Transform, and Load (ETL) data collection process that improves on legacy data collection methods for Azure Monitor. This process uses a common data ingestion pipeline, the Azure Monitor pipeline, for all data sources and a standard method of configuration that's more manageable and scalable than other methods.
To create the data collection rule for the MIM server, use the following steps.
- On the Monitor home screen in the Azure portal, select Settings and Data Collection Rules.
- At the top, click Create.
- Give your rule a name, associate it with your resource group, and the region your resource group is located in.
- Click Next.
- On the resources tab, click Add resources and under your resource group, add the MIM server. Click Next.
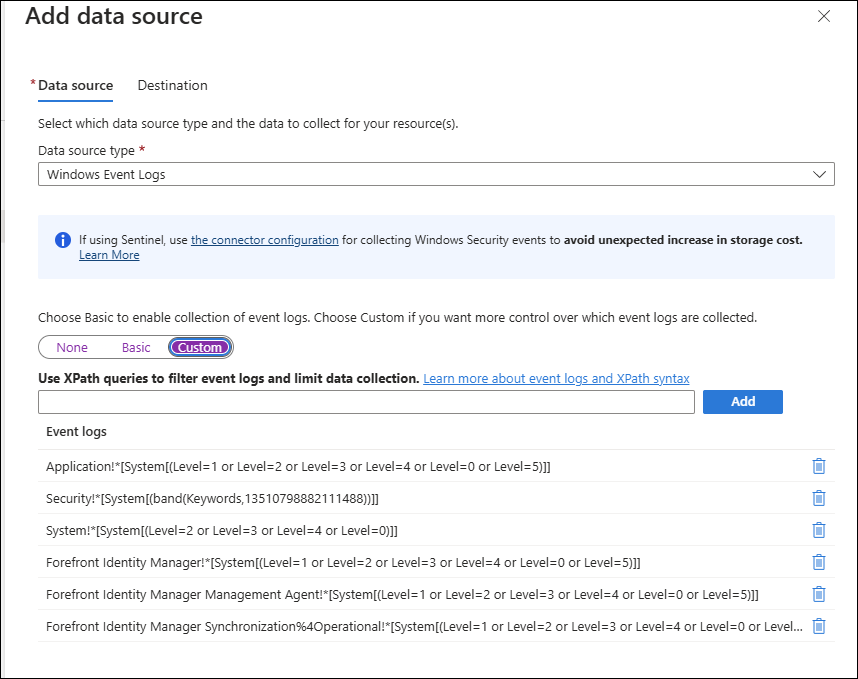
- On Collect and deliver and the Windows Event Logs as the data source.
- On Basic you can add the basic Windows Event logs, System, Security, and Application.
- Click on Custom.
- Enter the following in the box under Use XPath queries to filter event logs and limit data collection:
| Xpath query | Description |
|---|---|
Forefront Identity Manager!*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]] |
The MIM service log |
Forefront Identity Manager Management Agent!*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]] |
The MIM management agent log |
Forefront Identity Manager Synchronization%4Operational!*[System[(Level=1 or Level=2 or Level=3 or Level=4 or Level=0 or Level=5)]] |
The operations log for the MIM synchronization engine |
- Click Next Destination and click Add Destination.
- Enter the following:
- Destination Type: Azure Monitor Logs
- Subscription: Your subscription
- Destination Details: Your workgroup
- Click Add data source.
- Click Review and Create.
- Click Create.
Once the DCR is created and deployed, event log information begins to flow from the MIM server.
Windows events generated by MIM Service
Events that are generated by Microsoft Identity Manager are stored in Windows Event Log. You can view the events corresponding to MIM Service requests in the Event Viewer by selecting Application and Services logs > Identity Manager Request Log. Each MIM Service request is exported as an event in Windows Event Log in the JSON structure.
| Event type | ID | Event details |
|---|---|---|
| Information | 4121 | The Identity Manager event data that includes all the request data. |
| Information | 4137 | The Identity Manager event 4121 extension, if there is too much data for a single event. The header in this event is displayed in the following format: "Request: <GUID> , message <xxx> out of <xxx>. |
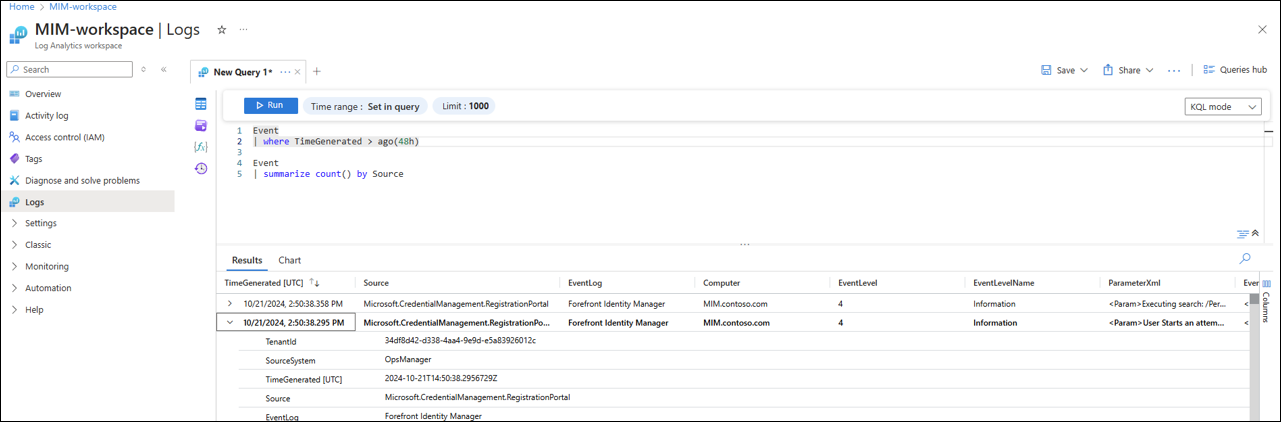
Verify data
To verify that you are collecting data, you can go to your workspace and run the following query.
- On your workspace, select logs
- Enter the following query:
Event | where TimeGenerated > ago(48h) - You should see your MIM data.
Create a workbook for your data
Workbooks provide a flexible canvas for data analysis and the creation of rich visual reports within the Azure portal. Now that the MIM data is in the portal, you can use workbooks. Workbooks let you combine multiple kinds of visualizations and analyses, making them great for freeform exploration.
For more information, see Create or edit an Azure Workbook.