Create a device-based Conditional Access policy
Microsoft Intune device compliance policies can evaluate the status of managed devices to ensure they meet your requirements before you grant them access to your organization's apps and services. The status results from your device compliance policies can be used by Microsoft Entra Conditional Access policies to enforce security and compliance standards. This combination is referred to as device-based Conditional Access.
Tip
In addition to device-based Conditional Access policies, you can use App-based Conditional Access with Intune.
From within the Intune admin center, you can access the Conditional Access policy UI as found in Microsoft Entra ID. This access includes all of the Conditional Access options you would have if you were to configure the policy from within the Azure portal. The policies you create can specify the apps or services you want to protect, the conditions under which the apps or services can be accessed, and the users that the policy applies to.
To Create a device-based Conditional Access policy your account must have one of the following permissions in Microsoft Entra:
- Security administrator
- Conditional Access administrator
To take advantage of device compliance status, configure Conditional Access policies to Require device to be marked as compliant. This option is set while configuring Grant access during step 6 of the following procedure.
Important
Before you set up Conditional Access, you'll need to set up Intune device compliance policies to evaluate devices based on whether they meet specific requirements. See Get started with device compliance policies in Intune.
Create the Conditional Access policy
Sign in to the Microsoft Intune admin center.
Select Endpoint security > Conditional Access > Create new policy.
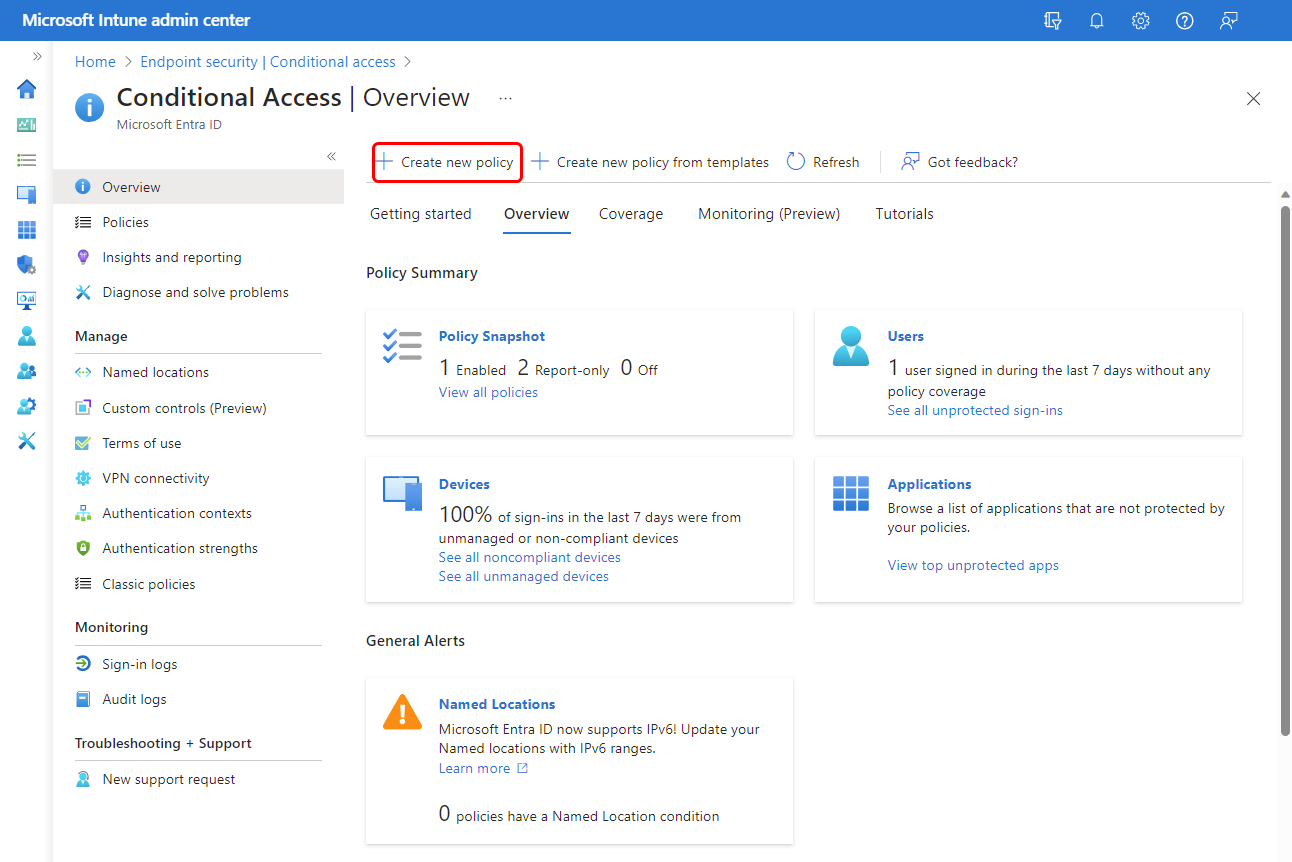
The New pane opens, which is the configuration pane from Microsoft Entra. The policy you’re creating is a Microsoft Entra policy for Conditional Access. To learn more about this pane and Conditional Access policies, see Conditional Access policy components in the Microsoft Entra content.
Under Assignments, configure Users to select the Identities in the directory that the policy applies to. To learn more, see Users and groups in the Microsoft Entra documentation.
- On the Include tab, configure the user and groups you want to include.
- Use the Exclude tab if there are any users, roles, or groups you want to exclude from this policy.
Tip
Test the policy against a smaller group of users to make sure it works as expected before deploying it to larger groups.
Next configure Target resources, which is also under Assignments. Use the drop-down for Select what this policy applies to to select Cloud apps.
On the Include tab, use available options to identify the apps and services that you want to protect with this Conditional Access policy.
If you choose Select apps, use the available UI to select apps and services to protect with this policy.
Caution
Don't lock yourself out. If you choose All cloud apps, be sure to review the warning, and then Exclude from this policy your user account or other relevant users and groups that should retain access to use the Azure portal or Microsoft Intune admin center after this policy takes effect.
Use the Exclude tab if there are any apps or services you want to exclude from this policy.
For more information, see Cloud apps or actions in the Microsoft Entra documentation.
Next, configure Conditions. Select the signals you want to use as conditions for this policy. Options include:
- User risk
- Sign-in risk
- Device platforms
- Locations
- Client apps
- Filter for devices
For information about these options, see Conditions in the Microsoft Entra documentation.
Tip
If you want to protect both Modern authentication clients and Exchange ActiveSync clients, create two separate Conditional Access policies, one for each client type. Although Exchange ActiveSync supports modern authentication, the only condition that is supported by Exchange ActiveSync is platform. Other conditions, including multi-factor authentication, are not supported. To effectively protect access to Exchange Online from Exchange ActiveSync, create a Conditional Access policy that specifies the cloud app Microsoft 365 Exchange Online and the client app Exchange ActiveSync with Apply policy only to supported platforms selected.
Under Access controls, configure Grant to select one or more requirements. To learn about the options for Grant, see Grant in the Microsoft Entra Documentation.
Important
To have this policy use device compliance status, for Grant access you must select Require device to be marked as compliant.
Block access: The users specified in this policy are denied access to the apps or services under the conditions you've specified.
Grant access: The users specified in this policy are granted access, but you can require any of the following further actions:
- Require multi-factor authentication
- Require authentication strength
- Require device to be marked as compliant - This option is required for the policy to use device compliance status.
- Require Microsoft Entra hybrid joined device
- Require approved client app
- Require app protection policy
- Require password change
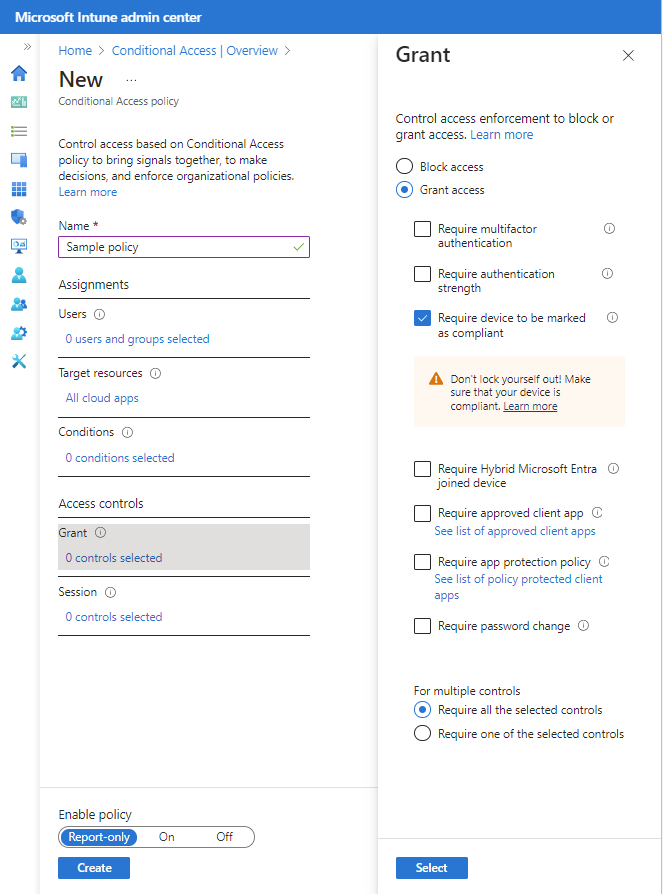
Under Enable policy, select On. By default, the policy is set to Report-only.
Select Create.