Microsoft Entra Permissions Management integration with Microsoft Defender for Cloud
Cloud Infrastructure Entitlement Management (CIEM) is a security model that helps organizations manage and control user access and entitlements in their cloud infrastructure. CIEM is a critical component of a Cloud Native Application Protection Platform (CNAPP) solution providing visibility into who has access to what resources and ensuring access rights align with the principle of least privilege (PoLP), where users have the minimum levels of access necessary to perform their tasks.
Microsoft delivers both CNAPP and CIEM solutions with Microsoft Defender for Cloud (CNAPP) and Microsoft Entra Permissions Management (CIEM). While both Defender for Cloud and Permissions Management help secure customers’ cloud environments, they're two distinct security solutions that address different aspects of cloud security. Permissions Management focuses on managing and enforcing fine-grained access controls, permissions, and entitlements for identities across multicloud infrastructures. Defender for Cloud focuses on securing cloud-native applications such as containers, microservices, and serverless applications through visibility into application behavior and security posture.
How Permissions Management works with Defender for Cloud
Permissions Management capabilities are available to integrate into the Defender for Cloud CSPM plan. Adding the capabilities of Permissions Management to Defender for Cloud strengthens the prevention of security breaches that might occur due to excessive permissions or misconfigurations in the cloud environment. By continuously monitoring and managing cloud entitlements, Permissions Management helps to reduce the attack surface, detect potential threats, and maintain compliance with regulatory standards. These added features make Permissions Management an essential tool to integrate into the capabilities of Defender for Cloud for securing cloud-native applications and protecting sensitive data in the cloud.
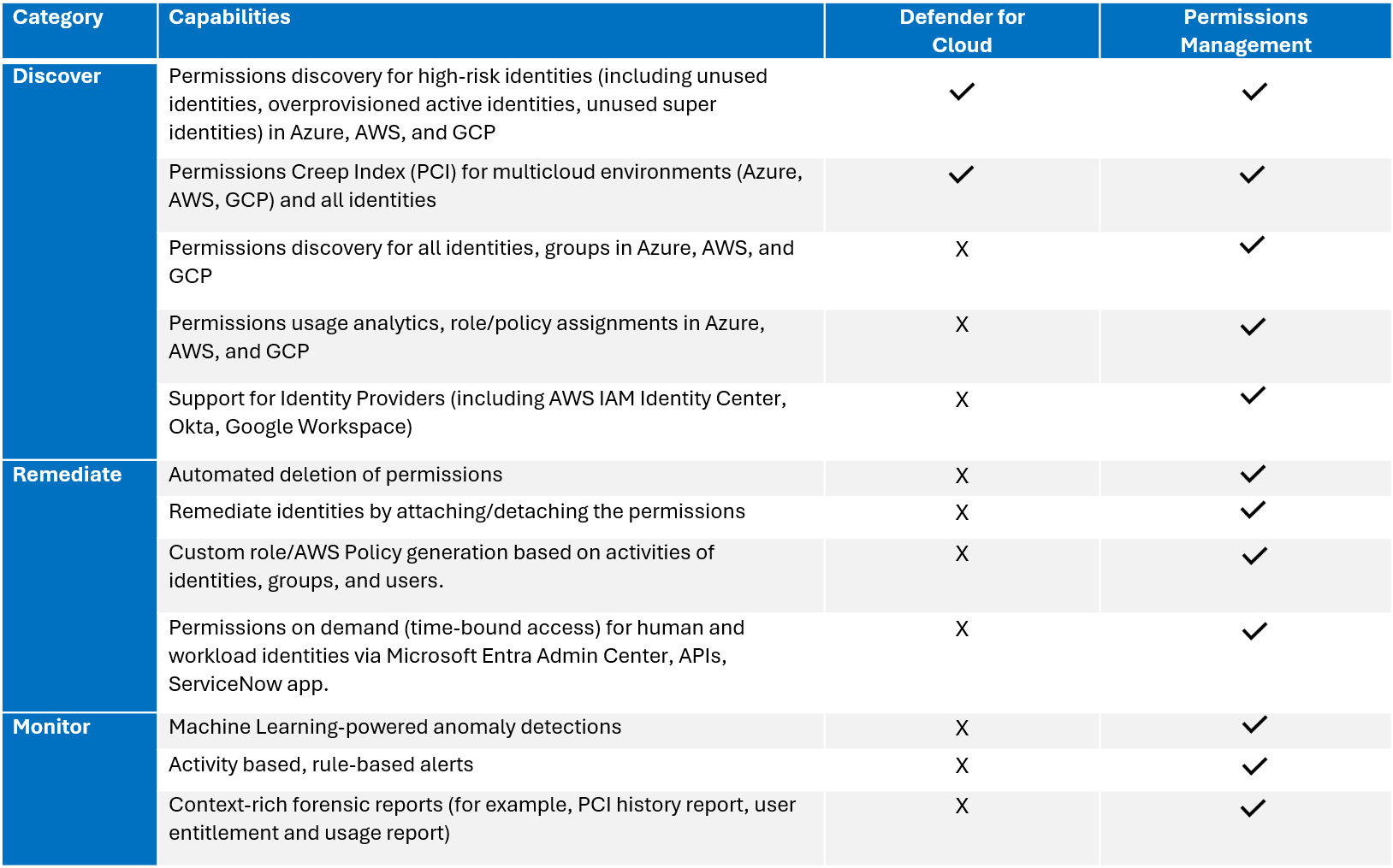
Permissions Management and Defender for Cloud capabilities
Common use cases and scenarios
With the added capabilities of Permissions Management, you can track permissions analytics, unused permissions for active identities, and over-permissioned identities then act to mitigate them to support the best practice of least privilege in Defender for Cloud.
Next steps
- For instructions on how to enable Permissions Management in your Defender for Cloud environment, see Enable Permissions Management in Microsoft Defender for Cloud.